- Published on
HTB Beep
- Authors

- Name
- collinhacks
- @collinhacks
Beep
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-22 18:31 EDT
Nmap scan report for 10.10.10.7
Host is up (0.034s latency).
Not shown: 65519 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
111/tcp open rpcbind
143/tcp open imap
443/tcp open https
878/tcp open unknown
993/tcp open imaps
995/tcp open pop3s
3306/tcp open mysql
4190/tcp open sieve
4445/tcp open upnotifyp
4559/tcp open hylafax
5038/tcp open unknown
10000/tcp open snet-sensor-mgmt
Nmap done: 1 IP address (1 host up) scanned in 8.19 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap check UDP
sudo nmap -sU --top-ports 1000 -v $IP -o udp.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
└─$ nmap -p 22,25,80,110,111,143,443,878,993,995,3306,4190,4445,4559,5038,10000 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-22 18:34 EDT
Nmap scan report for 10.10.10.7
Host is up (0.029s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN
80/tcp open http Apache httpd 2.2.3
| http-headers:
| Date: Fri, 22 Sep 2023 22:36:45 GMT
| Server: Apache/2.2.3 (CentOS)
| Location: https://10.10.10.7/
| Content-Length: 278
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
|
|_ (Request type: GET)
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: APOP RESP-CODES STLS IMPLEMENTATION(Cyrus POP3 server v2) EXPIRE(NEVER) AUTH-RESP-CODE USER LOGIN-DELAY(0) UIDL TOP PIPELINING
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 875/udp status
|_ 100024 1 878/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: STARTTLS RIGHTS=kxte ACL LIST-SUBSCRIBED IMAP4rev1 SORT UNSELECT BINARY IDLE OK RENAME LITERAL+ THREAD=REFERENCES X-NETSCAPE NAMESPACE ID CONDSTORE CATENATE ANNOTATEMORE CHILDREN SORT=MODSEQ IMAP4 ATOMIC MULTIAPPEND THREAD=ORDEREDSUBJECT UIDPLUS URLAUTHA0001 Completed MAILBOX-REFERRALS NO LISTEXT QUOTA
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
|_ssl-date: 2023-09-22T22:37:26+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
| http-headers:
| Date: Fri, 22 Sep 2023 22:36:46 GMT
| Server: Apache/2.2.3 (CentOS)
| X-Powered-By: PHP/5.1.6
| Set-Cookie: elastixSession=bfmubccpc0u98oom59j5o6ruh2; path=/
| Expires: Thu, 19 Nov 1981 08:52:00 GMT
| Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
| Pragma: no-cache
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: HEAD)
|_http-title: Elastix - Login page
|_http-server-header: Apache/2.2.3 (CentOS)
| http-robots.txt: 1 disallowed entry
|_/
878/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4190/tcp open sieve Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)
4445/tcp open upnotifyp?
4559/tcp open hylafax HylaFAX 4.3.10
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-server-header: MiniServ/1.570
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
| http-headers:
| Server: MiniServ/1.570
| Date: Fri, 22 Sep 2023 22:36:45 GMT
| Content-type: text/html; Charset=iso-8859-1
| Connection: close
|
|_ (Request type: GET)
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com, localhost; OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 384.91 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
└─$ nmap -p 22,25,80,110,111,143,443,878,993,995,3306,4190,4445,4559,5038,10000 --script vuln $IP -o vuln.nmap 130 ⨯
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-22 18:42 EDT
Nmap scan report for 10.10.10.7
Host is up (0.031s latency).
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
80/tcp open http
|_http-trace: TRACE is enabled
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-vuln-cve2013-7091: ERROR: Script execution failed (use -d to debug)
| http-enum:
|_ /icons/: Potentially interesting directory w/ listing on 'apache/2.2.3 (centos)'
|_http-passwd: ERROR: Script execution failed (use -d to debug)
110/tcp open pop3
111/tcp open rpcbind
143/tcp open imap
443/tcp open https
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-fileupload-exploiter:
|
|_ Couldn't find a file-type field.
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| http://www.openssl.org/news/secadv_20140605.txt
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
|_ http://www.cvedetails.com/cve/2014-0224
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: BID:70574 CVE:CVE-2014-3566
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.securityfocus.com/bid/70574
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.imperialviolet.org/2014/10/14/poodle.html
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-trace: TRACE is enabled
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: mod_ssl 2.2.x/1024-bit MODP group with safe prime modulus
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
878/tcp open unknown
993/tcp open imaps
|_ssl-ccs-injection: No reply from server (TIMEOUT)
995/tcp open pop3s
|_ssl-ccs-injection: No reply from server (TIMEOUT)
3306/tcp open mysql
4190/tcp open sieve
4445/tcp open upnotifyp
4559/tcp open hylafax
5038/tcp open unknown
10000/tcp open snet-sensor-mgmt
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: BID:70574 CVE:CVE-2014-3566
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.securityfocus.com/bid/70574
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.imperialviolet.org/2014/10/14/poodle.html
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
|_sslv2-drown: ERROR: Script execution failed (use -d to debug)
| http-vuln-cve2006-3392:
| VULNERABLE:
| Webmin File Disclosure
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2006-3392
| Webmin before 1.290 and Usermin before 1.220 calls the simplify_path function before decoding HTML.
| This allows arbitrary files to be read, without requiring authentication, using "..%01" sequences
| to bypass the removal of "../" directory traversal sequences.
|
| Disclosure date: 2006-06-29
| References:
| http://www.exploit-db.com/exploits/1997/
| http://www.rapid7.com/db/modules/auxiliary/admin/webmin/file_disclosure
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-3392
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| http://www.openssl.org/news/secadv_20140605.txt
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
|_ http://www.cvedetails.com/cve/2014-0224
Nmap done: 1 IP address (1 host up) scanned in 515.75 seconds
Port Enumeration
**Port 10000 catches my attention
**************Port 443
curl -v https://10.10.10.7
Seems to be using TLS 1.0 and gives an error when we visit the site:
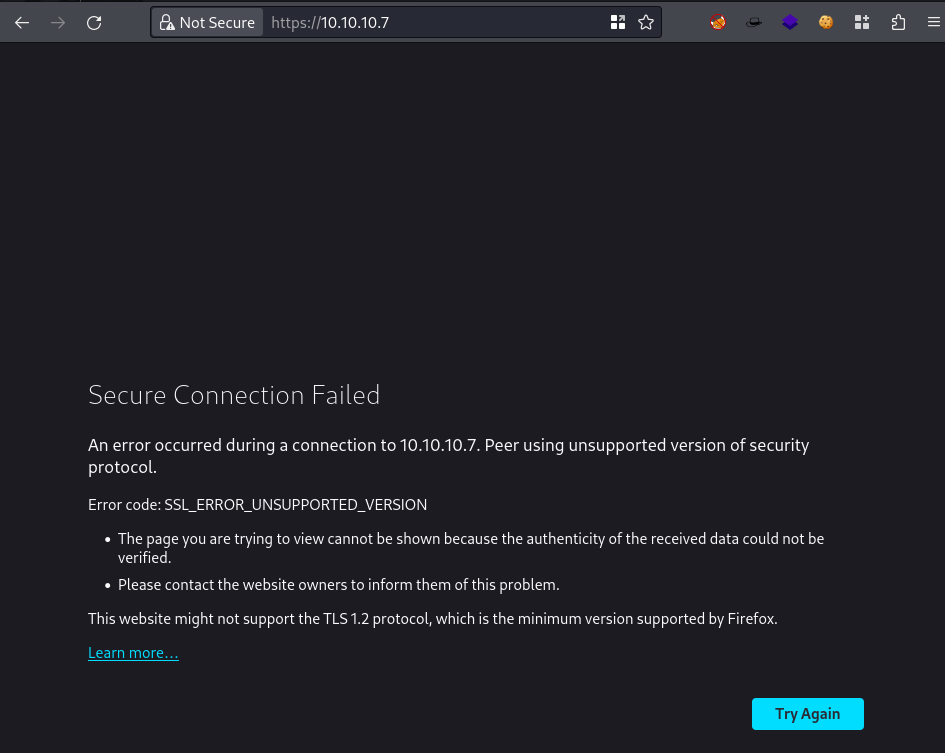
Change firefox’s about:config to be able to load TLS 1.0
about:configsecurity.tls.version.min=1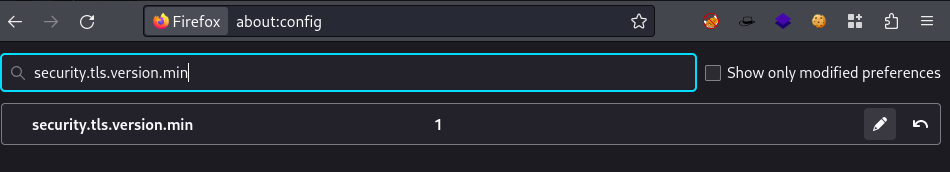
Now we can load the site
elastix

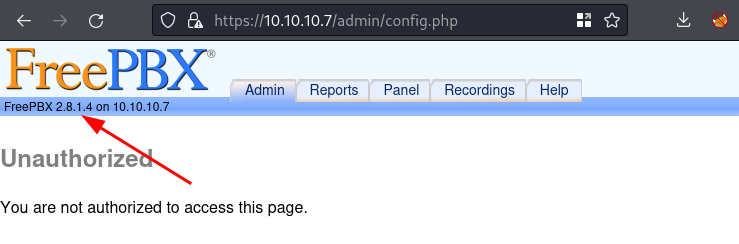
- Tried
/adminand didn’t know creds but it shows this
Onto Foothold
Exploitation
**********Port 443
Foothold
Usually elastix is old af and vulnerable to we
searchsploit elastix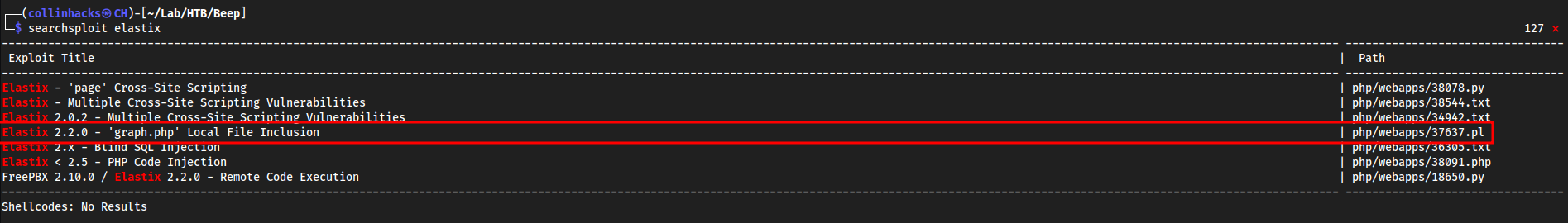
Seems to be vulnerable to LFI possibly - This perl script wouldn’t work so I did some googling and read the source code on https://www.exploit-db.com/exploits/37637
yes I could’ve just
cat'd it but I didn’t realize it at first lol
Going to this directory we do get some kind of LFI but I need to figure out how to change it to be more specific to get a shell
We see user
asteriskorasteriskuserwith passamp109- Also
jEhdIekWmdjEpassword is listed here a lot
- Also
Pivoting to a login
We can browse to https://10.10.10.7:10000/ now that we downgraded our TLS version
Tried a bunch of users,
root:jEhdIekWmdjElogs me in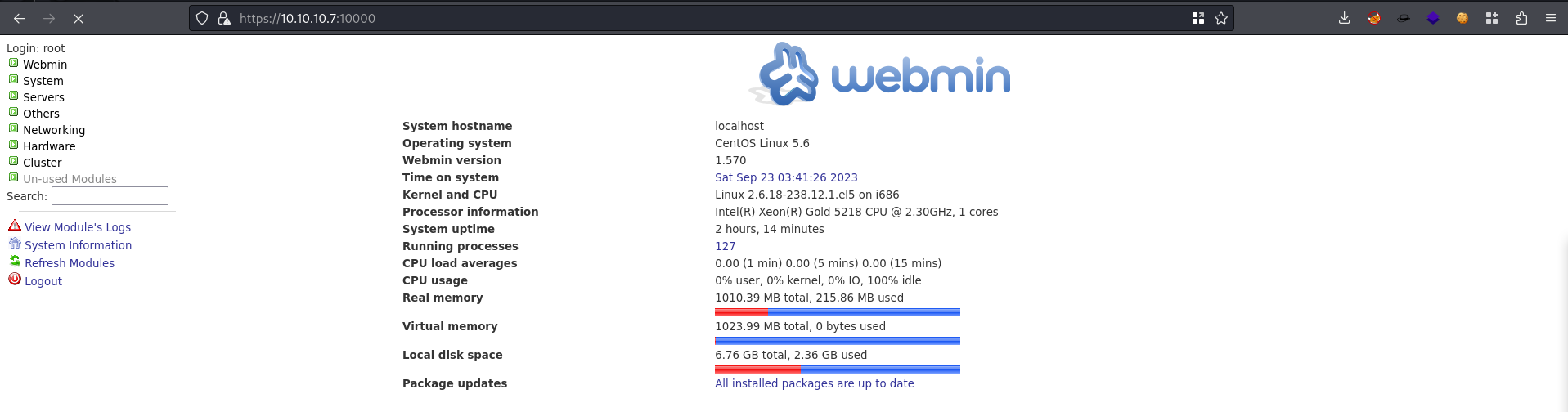
Root
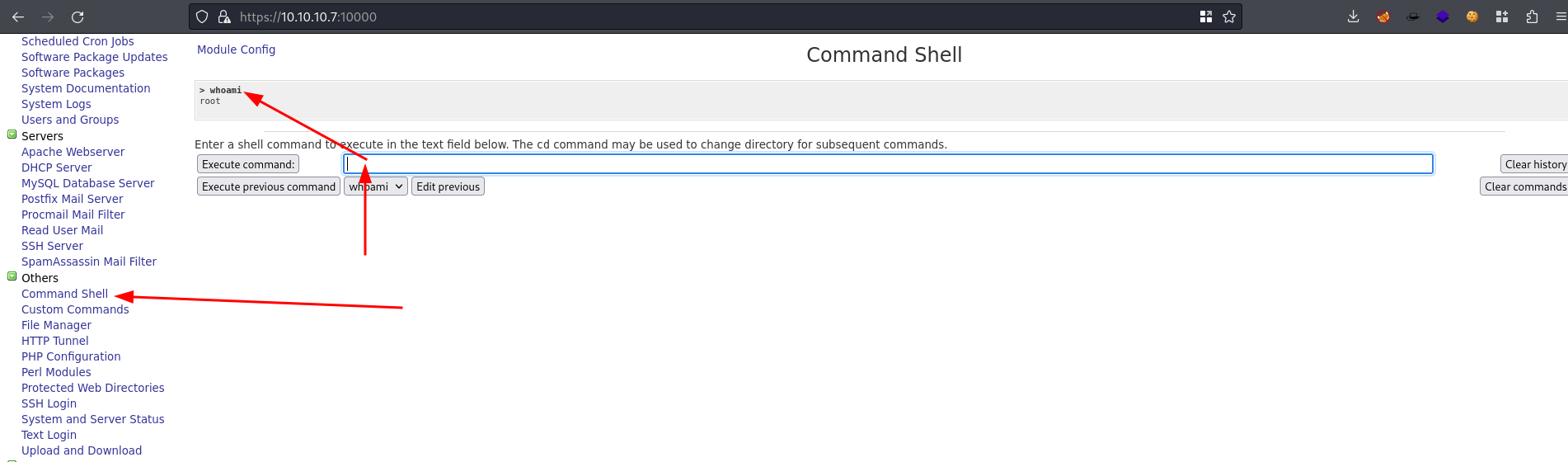
- Found a “
Command Shell" under the “Others" tab which lets me execute commands and it seems we are root