- Published on
HTB Mirai
- Authors

- Name
- collinhacks
- @collinhacks
Mirai
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-27 13:58 EDT
Nmap scan report for 10.10.10.48
Host is up (0.032s latency).
Not shown: 65529 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
1806/tcp open musiconline
32400/tcp open plex
32469/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 14.67 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap check UDP
sudo nmap -sU --top-ports 1000 -v $IP -o udp.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
nmap -p 22,53,80,1806,32400,32469 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-27 14:00 EDT
Nmap scan report for 10.10.10.48
Host is up (0.045s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aa:ef:5c:e0:8e:86:97:82:47:ff:4a:e5:40:18:90:c5 (DSA)
| 2048 e8:c1:9d:c5:43:ab:fe:61:23:3b:d7:e4:af:9b:74:18 (RSA)
| 256 b6:a0:78:38:d0:c8:10:94:8b:44:b2:ea:a0:17:42:2b (ECDSA)
|_ 256 4d:68:40:f7:20:c4:e5:52:80:7a:44:38:b8:a2:a7:52 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
| http-headers:
| X-Pi-hole: A black hole for Internet advertisements.
| Content-type: text/html; charset=UTF-8
| Content-Length: 0
| Connection: close
| Date: Fri, 27 Oct 2023 18:00:52 GMT
| Server: lighttpd/1.4.35
|
|_ (Request type: GET)
|_http-server-header: lighttpd/1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
1806/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
32400/tcp open http Plex Media Server httpd
| http-headers:
| Content-Length: 193
| Content-Type: text/html
| X-Plex-Protocol: 1.0
| Cache-Control: no-cache
| Date: Fri, 27 Oct 2023 18:00:53 GMT
|
|_ (Request type: GET)
|_http-title: Unauthorized
|_http-cors: HEAD GET POST PUT DELETE OPTIONS
|_http-favicon: Plex
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Server returned status 401 but no WWW-Authenticate header.
32469/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.20 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
0
Port Enumeration
**Port 32400
http://10.10.10.48:32400/web/index.html

adminexists
collinhacks:Password1!http://10.10.10.48:32400/web/index.html#!/settings
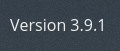
- Version 3.9.1
Doesn’t really seem to be anything here that I could create a shell off of, trying to brute force admin is an idea also considering I cannot find anything on the version being vulnerable
Rabbit hole
Port 80
Went to the IP by default on accident and noticed it was a blank endpoint, a white screen. So I fuzzed it and found
/admin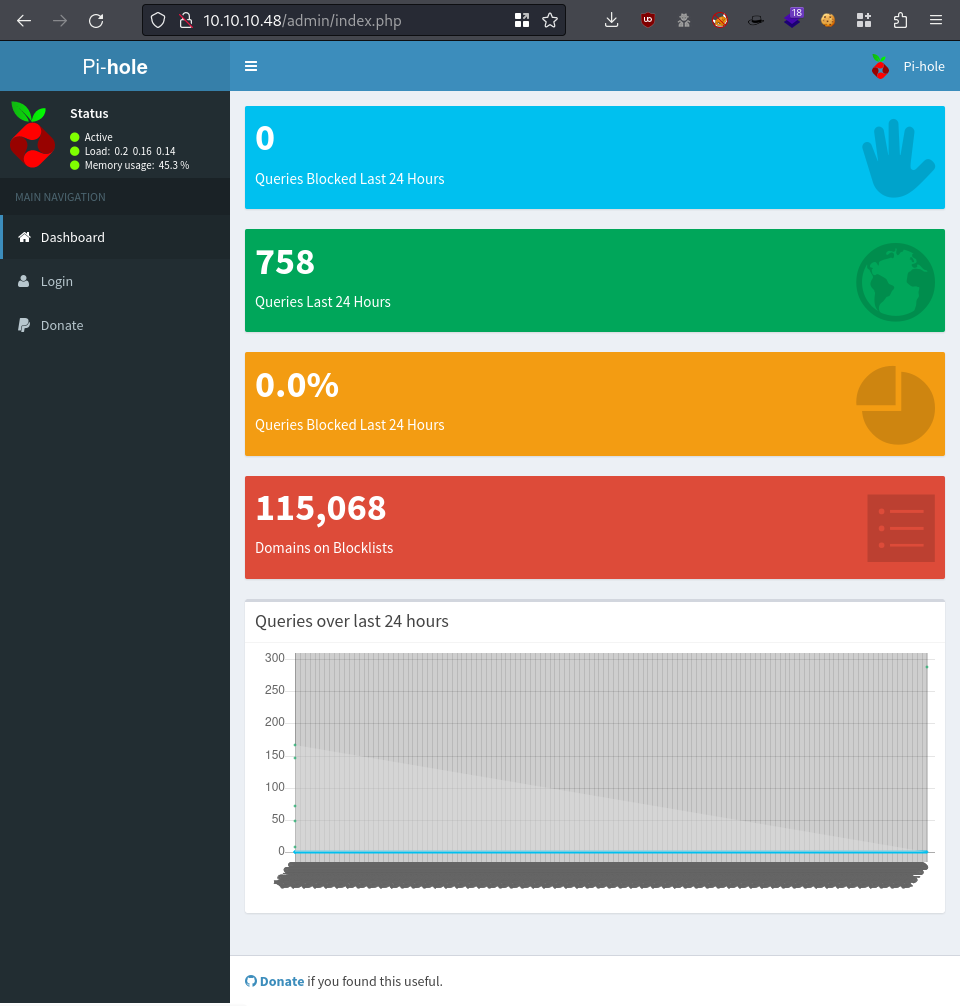
Seems to be some sort of PiHole instance
PiHole
- Couldn’t find any default credentials to work here, pihole documentation was saying it’s
pi-hole:raspberry
Port 22
ssh pi@10.10.10.48raspberrry
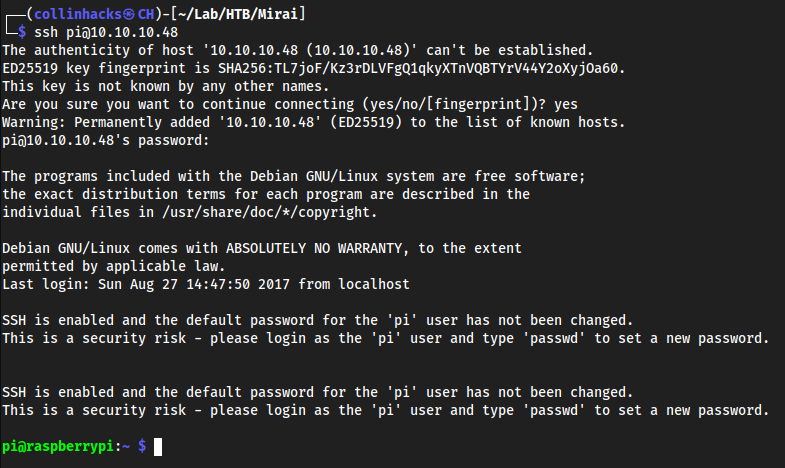
Exploitation
**********Port 22
Foothold
We have gained foothold from finding that it is a PiHole instance, found default credentials, and then pivoted those credentials to points where we can use them.
ssh pi@10.10.10.48raspberrry
Root
sudo -l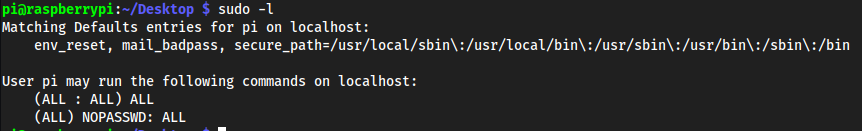
- bruh
sudo su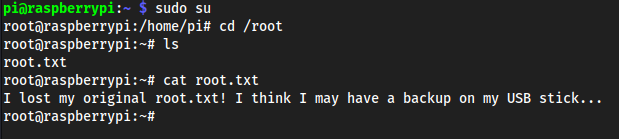
Went to
/mediato find if any USB sticks are attached, and we do see/media/usbstick;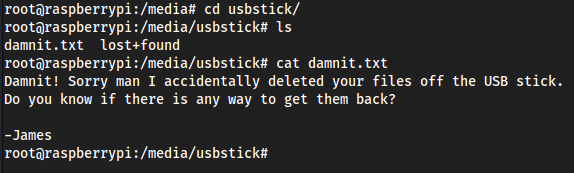
cat /dev/sdb
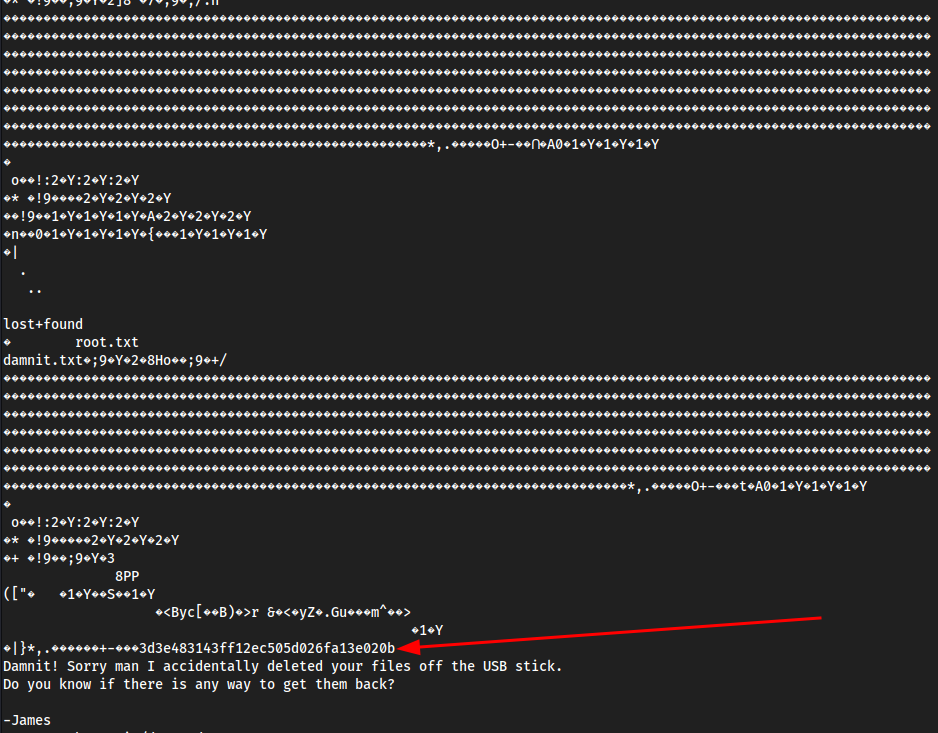
Root file found in this file, which is apparently where
/dev/sdbseems to be where files are stored either temporarily or something similar. It seems to be a cache of the SCSI disk, which issd, and takes the/dev/*information of things likesda, etc. That’s why we see the note from James, and the root flag right after. James deleted the root flag, then made his message.
Useful resource links
Lessons Learned
- Learned to pivot default credentials. It’s a good thing to realize that the box I’m on is rather specific so one piece of information can be utilized in other areas. We see that it’s pi hole, ok I try default creds there, doesn’t work. I tried it on the plex site, didn’t work, but admin existed. Then remembered ssh exists and thats how you would theoretically communicate with a pihole, and credentials worked.
- Learned where USB sticks are located on Linux machines, and how to kind of recover lost information if it is in plaintext.